Zeus_attack_module_5
This page aims to help you remove Zeus_attack_module_5 virus. These kinds of Zeus_attack_module_5 malicious software a termination guide run for each variant of Windows.
The logic why we have accumulated the report underneath is a Trojan horse titled Zeus_attack_module_5. If we can define it in fleeting, we have to tell that it is badly sly, for the most part as nobody can say for certain what its particular aim hugely is. Due to this in a dubious way, we will attempt to enlist all the potential sources, results and approaches of behaving in the text beneath. Hopefully, we will aid you to successfully defy the malware, provoked by this tedious cyber malicious software. In the succeeding section you will understand all the information you need to keep in mind in regards to these types of parasite. You are in addition going to get some profitable blockage recommendation and some effective elimination instructions.
Download Removal Toolto remove Zeus_attack_module_5
The Zeus_attack_module_5 malware
The Zeus_attack_module_5 malware could really be very creative when it comes to the potential distribution methods it may use. The Zeus_attack_module_5 infections may have just as tons of multiple usages and goals.
The most frequent trait that they share, which earns them a utility classification, is whatever they do after they have infiltrated your computer is for the most part subtle and carried out in a stealthy way. Actually, in nearly all of the instances the not clean people have little idea their computers have been infected. Indeed, if you have read about the notorious Trojan war, you will see that this is what the at the beginning Trojan horse from the story actually did. It stealthily sneaked into the city of Troy hidden as a innocuous calm suggestion gift and the gullible Trojans had no indication it was complete of Greek soldiers and their defeat was connected to to start. The alias of this malicious software classification comes from this well-known ancient tale primarily due to the way those infections commonly infect a machine and function after that.
What Zeus_attack_module_5 contamination may be employed for
It is accurate that such a malicious software could be used with different intentions in mind. The a majority of bad and well-scatter of them have been added to the classification underneath:
- The cyber crooks may just believe the want to ruin something without any rational argument for doing so. Unfortunately, the oriented thing could be your os. Also, some of your information can be destroyed/ deleted/ polluted or enchiphered. Your computer system may fall victim to so greatly wreck that an whole fresh setup might be required.
- The deceptive users behind Zeus_attack_module_5 may merely require your profits or your identity for quite some reasoning. That’s why Trojans may generally be employed for illegally monitoring and copying account credentials, which may after that let the crooks use your bank accounts or hijack your complete identity, based on the internet. Some categories of crimes should also be dedicated on your behalf, which might be terribly puzzling and nerve-racking for you, because you can get convicted afterwards without being to blame in any way.
- Such malicious software can be used just for incorporating other viruses onto your pc. What such a tool may slip into your device are other terribly corrupt infections such as Ransomware. If you haven’t heard of it, Ransomware is a variation of malicious viruses adept at enciphering details and urging a fine in return for retaking them. However, no assure is exhibited for the actual restoration of the encoded files no issue whether the victim user consents or disagrees to pay the requested fine.
- The cyber crooks behind Zeus_attack_module_5 can also are likely to be physically abusive. Such users might use such parasite to infect your device and monitor every stage of yours, no issue whether it’s performed on the internet or in the valid world. All your collecting os elements for instance cameras and mics may be turned on remotely and accustomed for tailing you all the time.
How to successfully block and/ or uninstall Zeus_attack_module_5
So to keep away from a Trojan, you shall call for to see which its prime sources are. Bypassing them shall equal bypassing this severe infection. The typical among plenty of feasible signifies of spreading Zeus_attack_module_5 are:
- Malvertising (the process of spreading pop-up ads leading to malware-containing web pages or containing malicious scripts);
- Weird emails, detected both in your Spam Folder and your Inbox Directory. Not only can letters on their own be compromised, but all the links into them, as well as all their attachments could be infected;
- Social media web links – perhaps you have observed some spam circulated across the social media in the shape of videos, gifs, images and ties. Do not press on any of them. They are possibly bad;
- Torrents, shareware, video-streaming webpages – such on the internet locations are for the most part illicit and may contain malicious as well.
For the get rid of of Zeus_attack_module_5, please turn to the deletion instructions straightaway underneath the qualities chart. Maybe it will be valuable ample and the phases there will aid you handle your matter.
Learn how to remove Zeus_attack_module_5 from your computer
Step 1. Zeus_attack_module_5 Removal from Windows
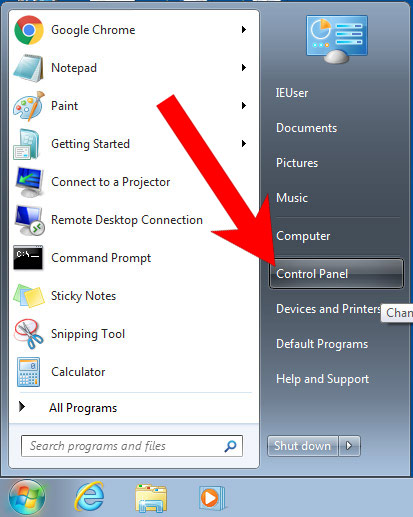
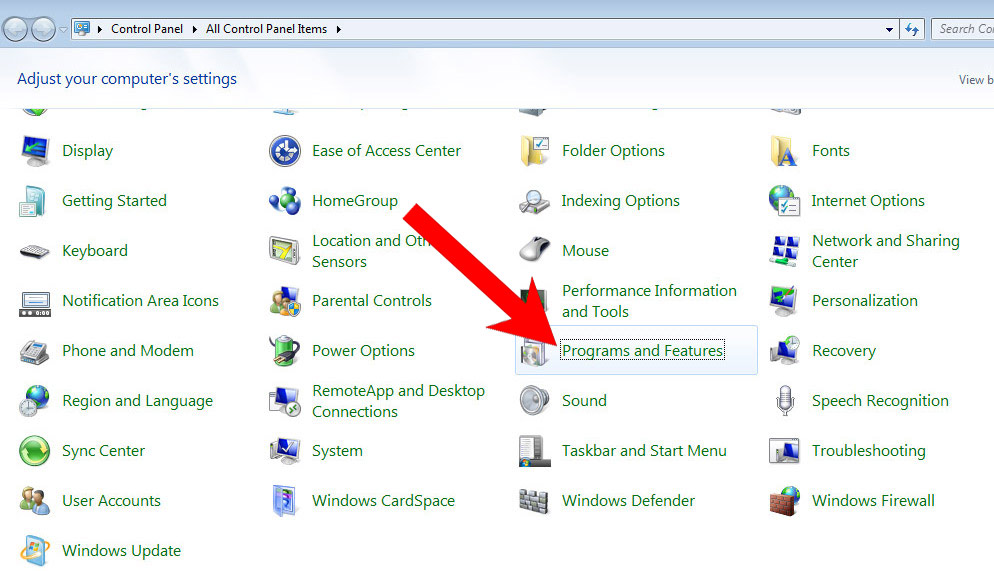
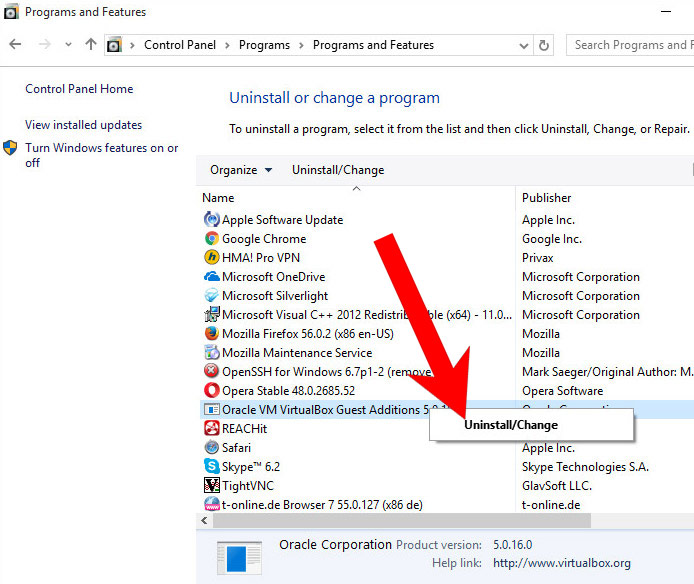
a) Windows 7/XP
- Press on the Start icon.

- Control Panel → Programs and Features.

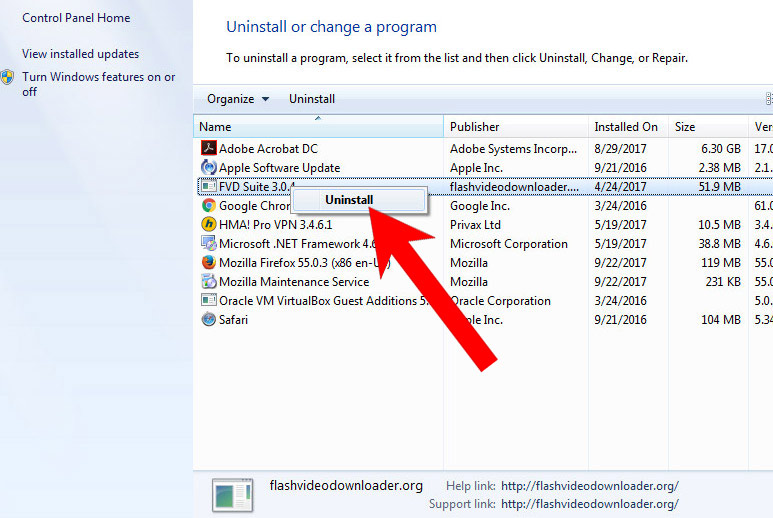
- Find the program you want to delete and press Uninstall.

b) Windows 8
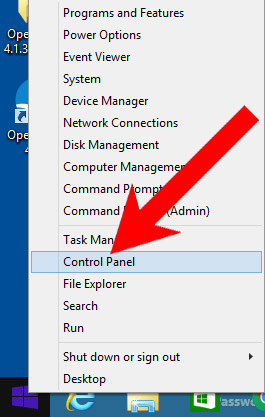
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

c) Windows 10
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

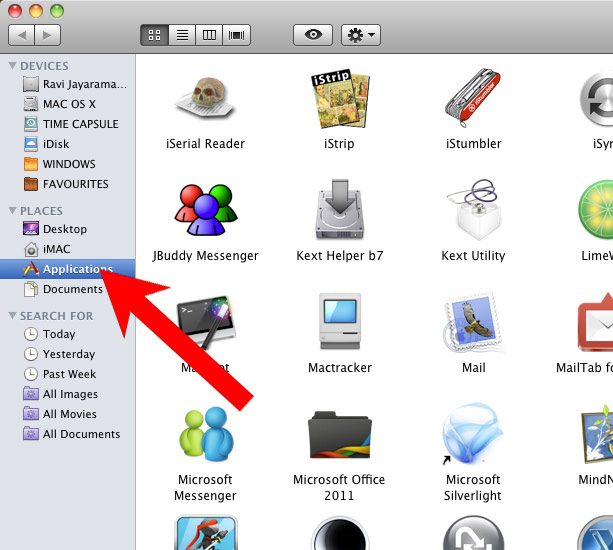
d) Mac OS X
- Open Finder and press Applications.

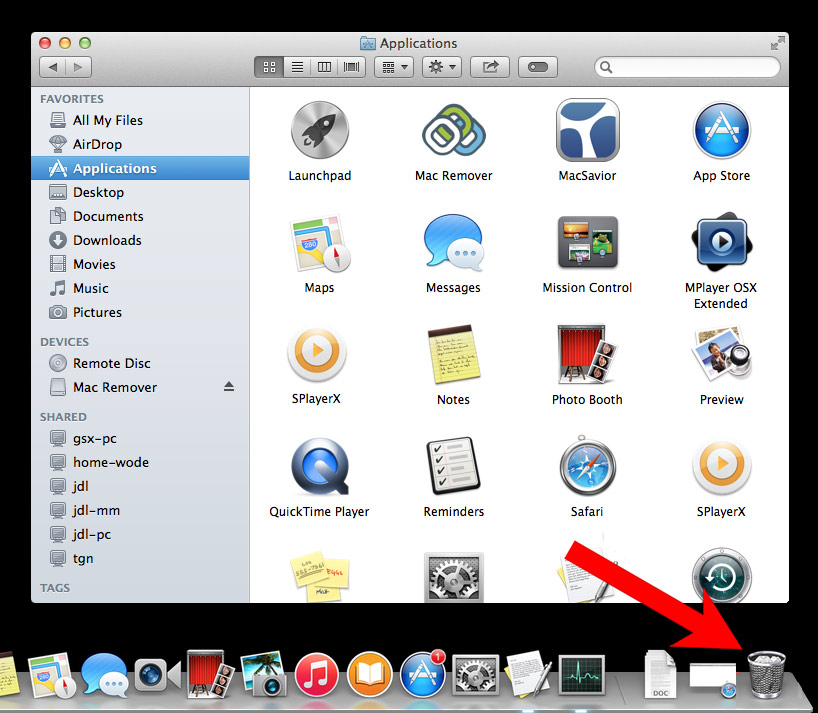
- Check all suspicious programs you want to get rid of.
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete Zeus_attack_module_5 from browsers
a) Remove Zeus_attack_module_5 from Microsoft Edge
Reset Microsoft Edge (Method 1)
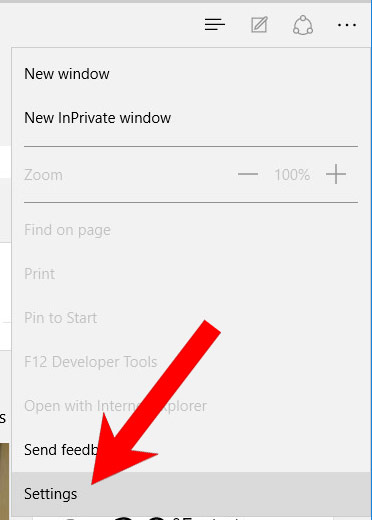
- Open Microsoft Edge.
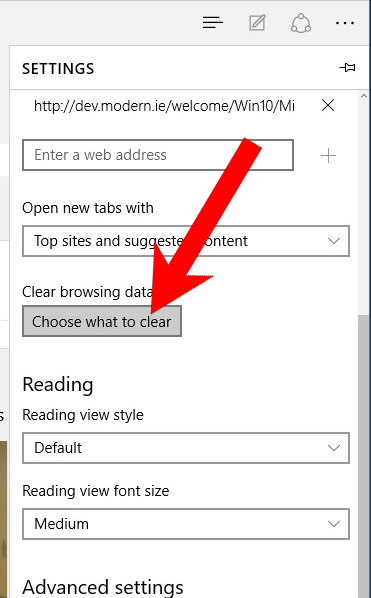
- Press More located at the top right corner of the screen (the three dots).

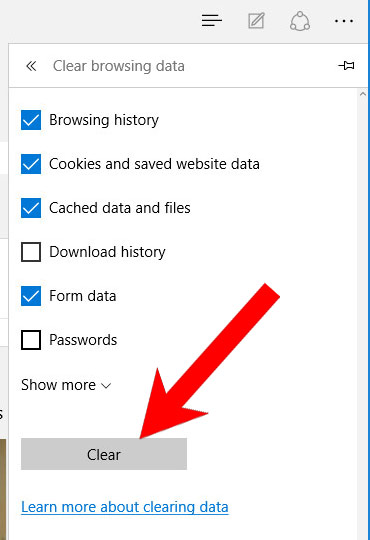
- Settings → Choose what to clear.

- Check the boxes of the items you want removed, and press Clear.

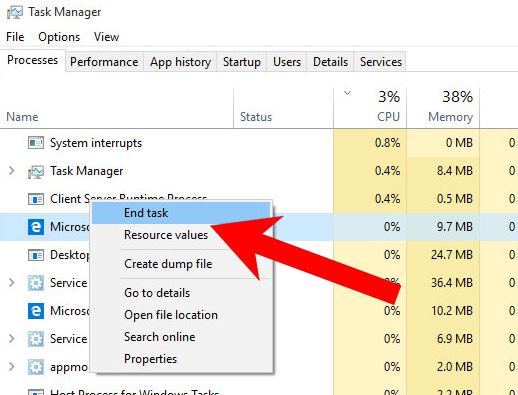
- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
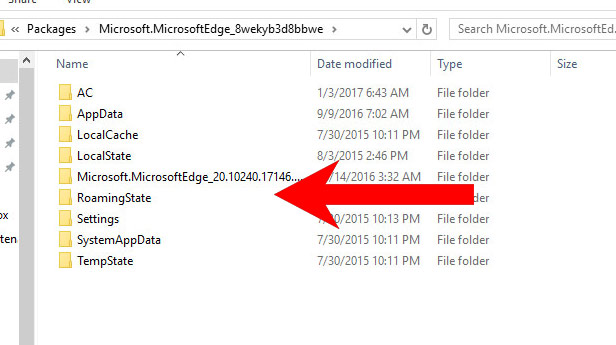
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

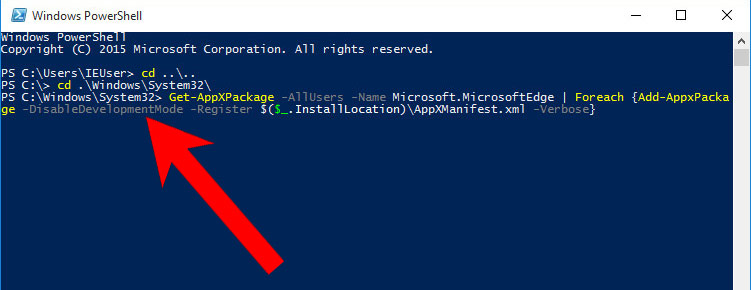
- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
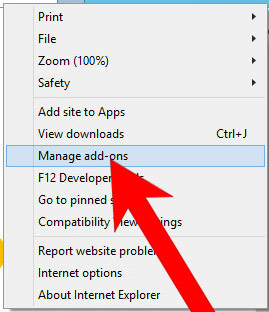
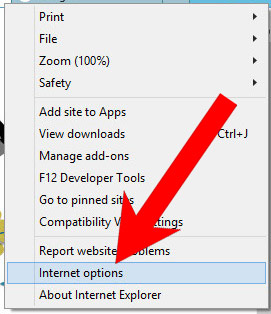
b) Remove Zeus_attack_module_5 from Internet Explorer
- Open Internet Explorer and press on the Gear icon.

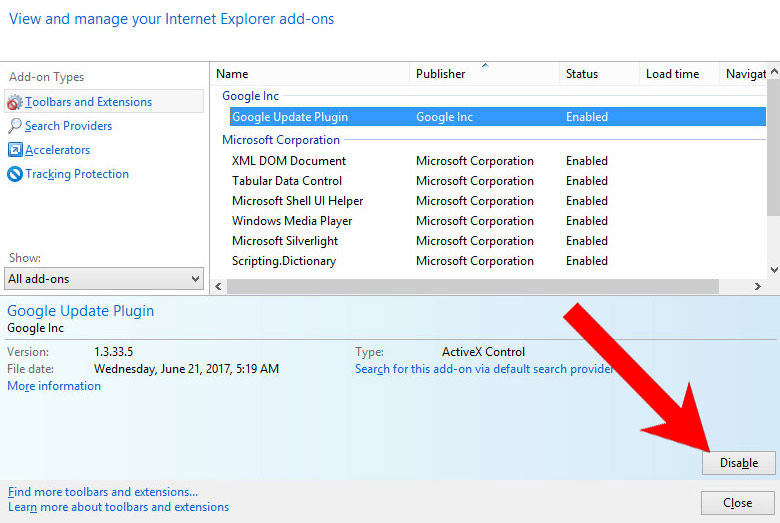
- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
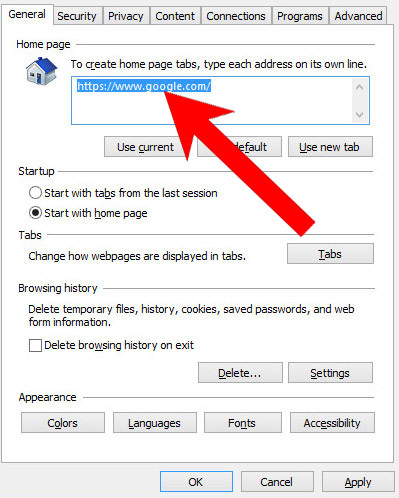
c) Restore your homepage on Internet Explorer
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
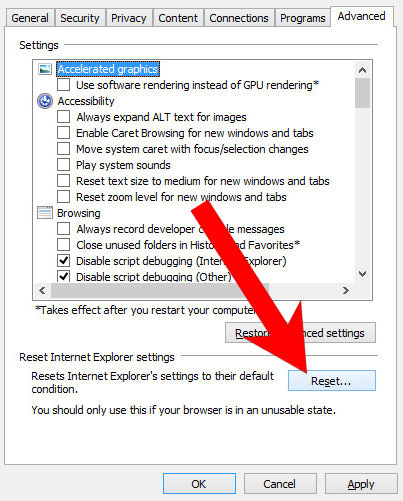
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

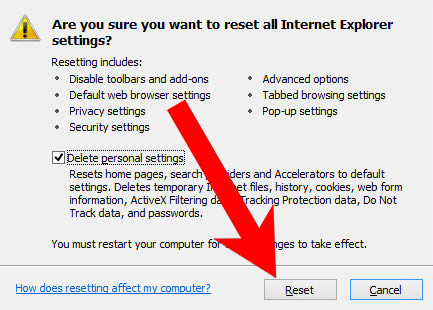
- At the bottom, you will see a Reset button. Press that.
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
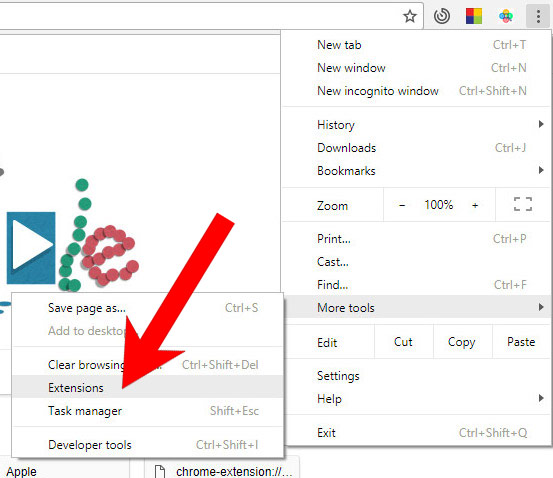
e) Remove Zeus_attack_module_5 from Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
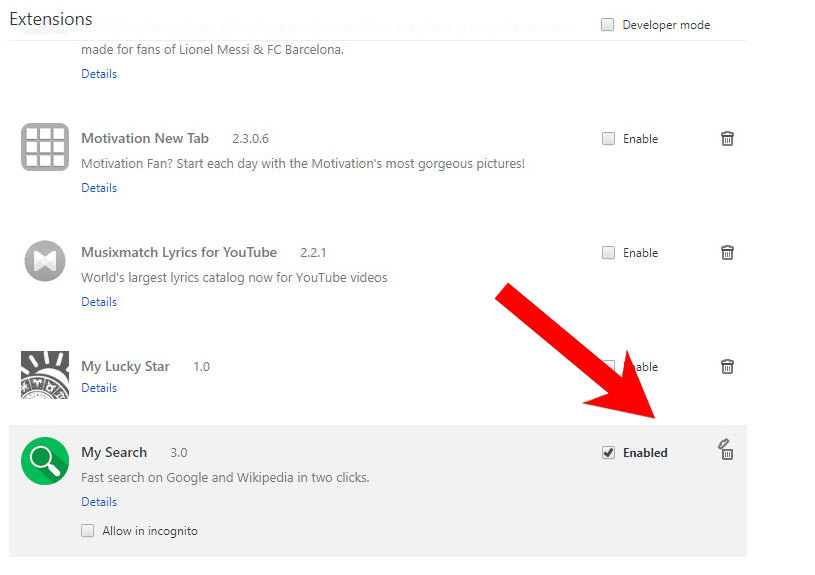
- Choose More tools and Extensions.

- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
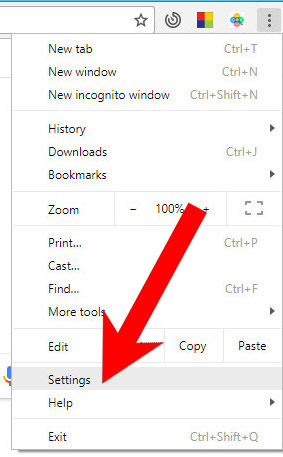
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

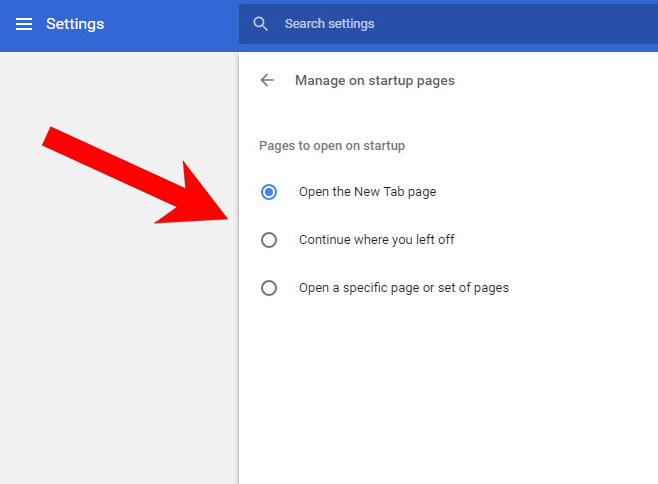
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

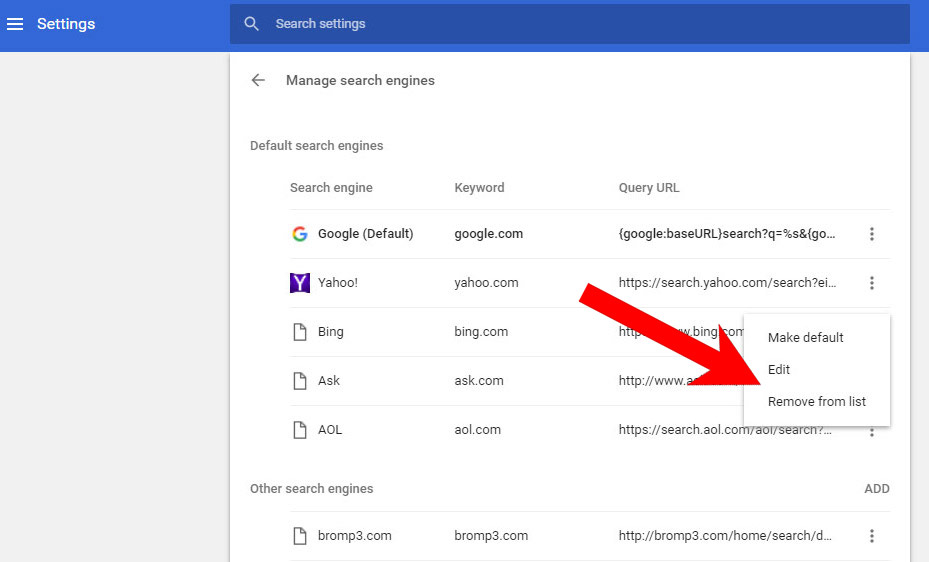
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
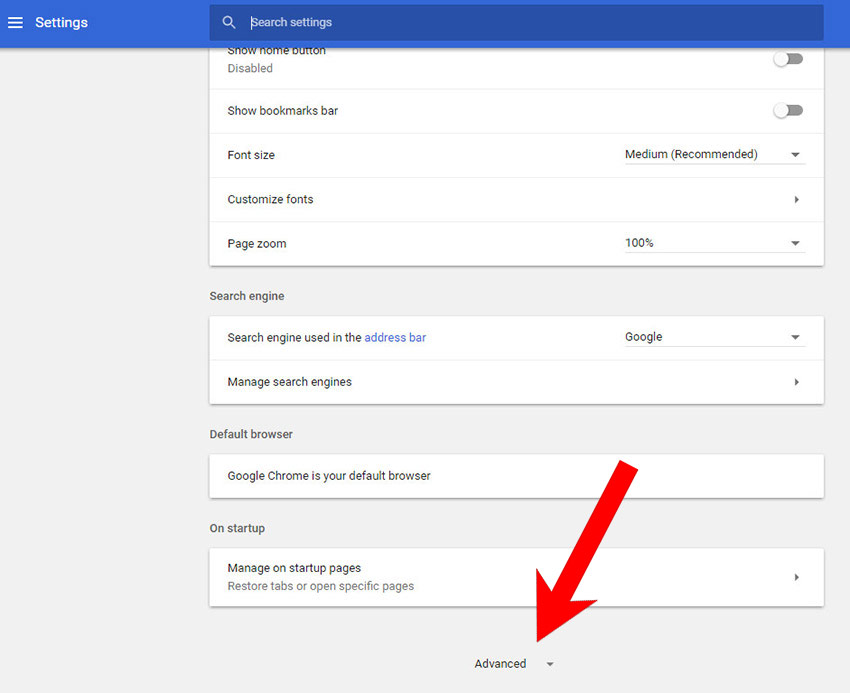
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

- Scroll down and press on Show advanced settings.

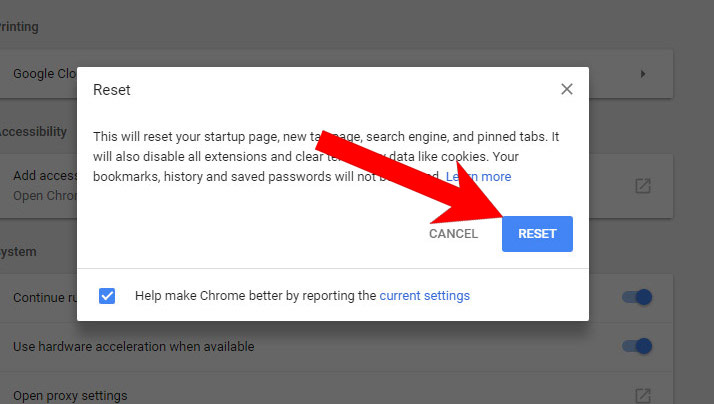
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
h) Remove Zeus_attack_module_5 from Mozilla Firefox
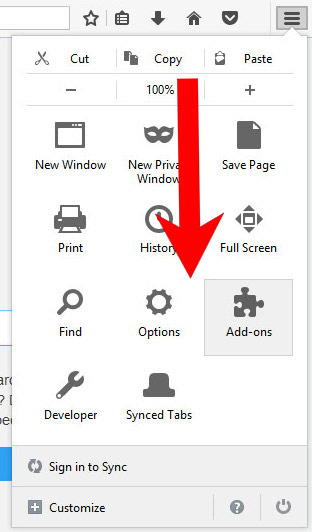
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Select Add-ons.

- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
i) Restore your homepage on Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
- Select Options.

- In General, click Restore to Default below the Home Page field.

j) Reset Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

- Select the Refresh Firefox option.

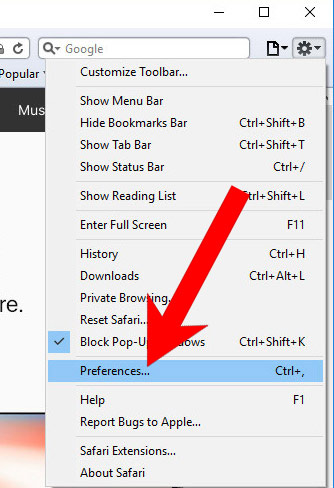
k) Remove Zeus_attack_module_5 from Safari (for Mac)
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

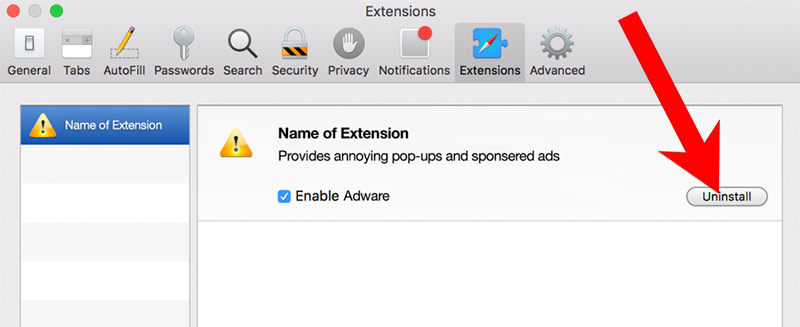
- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
l) Reset Safari
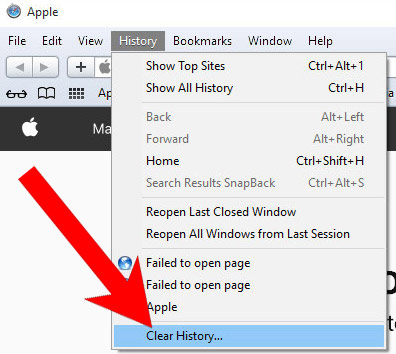
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
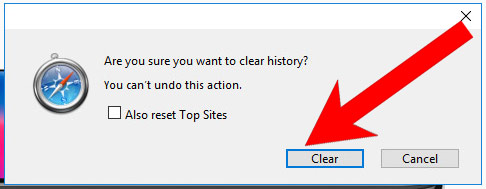
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

- Press on Safari at the top of the screen and select Preferences.

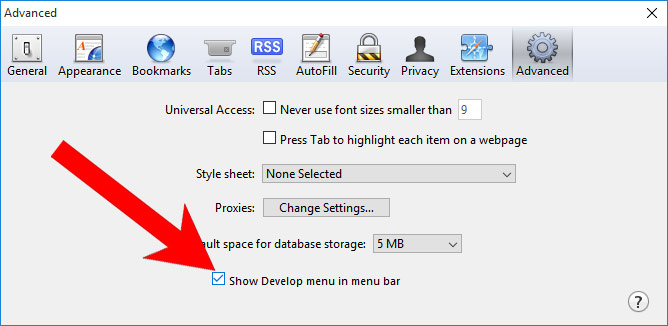
- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
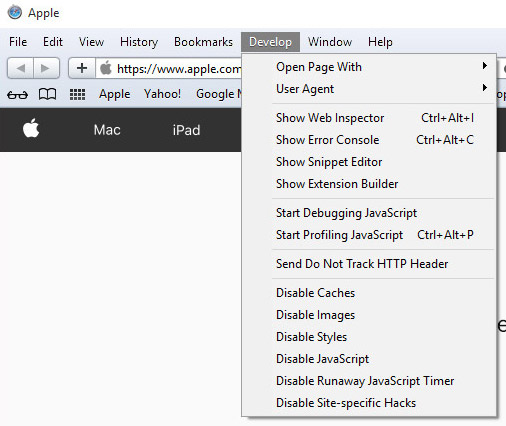
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.