Trojan.W97M.CVE202230190.A
Trojan infections like Trojan.W97M.CVE202230190.A are well-known for their stealthy capabilities and a load of probable employs. Our aim throughout the next report is to familiarize our readers along with the details of the insidious Trojan.W97M.CVE202230190.A malicious software, and to aid them to eliminate this infection from their pcs.
Working on a Trojan threat for example this one is not a simple mission, and you shall ought all the assistance you can obtain so to eradicate it. Fortunately that together with the guidelines posted at the bottom of this site, and the elimination tool we have encouraged in it, you need to be capable of cleaning your operating system and eliminate the insidious parasite that’s at the present moment running in it. However, it is suggested to at the start learn something etc. relating to the details of this Trojan, so that you obtain a solid perception of what you are chanced upon together with, and what the likely outcomes of its breach could be.
Download Removal Toolto remove Trojan.W97M.CVE202230190.A
The resourceful implements of Trojans like Trojan.W97M.CVE202230190.A
Trojan.W97M.CVE202230190.A, like many other representatives of its threat classification like Energy.exe, Bloom.exe, is an infection which will potentially be accustomed in all kinds of techniques, for the completion of a bunch of varied malignant functions. We can not go over all feasible methods such malware could be employed, but we can regardless offer you some examples of what you may anticipate from this viruses:
- Information scam and tailing – digital information has never been etc. profitable, and the cyber crooks are well conscious of that. This is why most of them utility their Trojan Horse malicious software to surreptitiously spy on their victims and attempt to get some confidential details from their pcs. For position, a Trojan which might keylog whatever you classification on your keyboard can promptly discover more about your monetary data, or the usernames and the passwords of your on the internet accounts. From then on, there’s no mentioning what sort of horrible deeds the cyber crooks may begin with this type of details prepared onto their hands.
- Backdooring processes – a Trojan is generally employed as an application for fixing other infections onto the oss of its victims. A very prominent example of this happening is when a Ransomware encryption-virus gets secretly sneaked inside the computer of its victim by a Trojan backdoor infection. In such situations, the Trojan Horse wouldn’t straightaway cause damage to the operating system, but it could serve as a gateway to all sorts of other damageful malicious software, and it can download them into the oriented pc without any malware signs.
- Botnet organization – Trojans like Trojan.W97M.CVE202230190.A are well-notorious for their skill to set up networks of remotely managed operating systems that are all contaminated by the same malware. Such botnets could be employed by the crooks for completing cryptocurrency mining functions, spam note campaigns, and even distribution denial of service invades on several known pages.
Currently, the objective of Trojan.W97M.CVE202230190.A stays unfamiliar because of absence of appropriate study. However, if you suspect that this infection could be in your pc, you desperately shouldn’t spend any time – ensure to at once check your device by following our instruction, and terminate anything potentially malign that might enter detected.
Learn how to remove Trojan.W97M.CVE202230190.A from your computer
- Step 1. Trojan.W97M.CVE202230190.A Removal from Windows
- Step 2. Delete Trojan.W97M.CVE202230190.A from browsers
Step 1. Trojan.W97M.CVE202230190.A Removal from Windows
a) Windows 7/XP
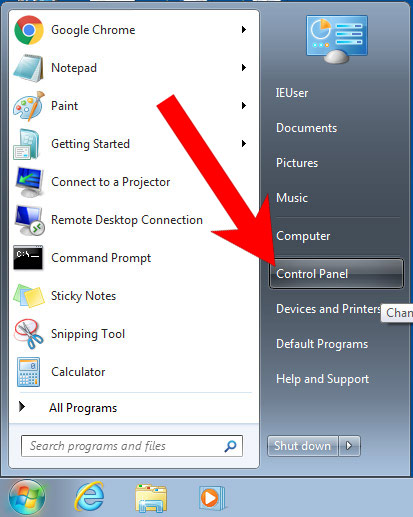
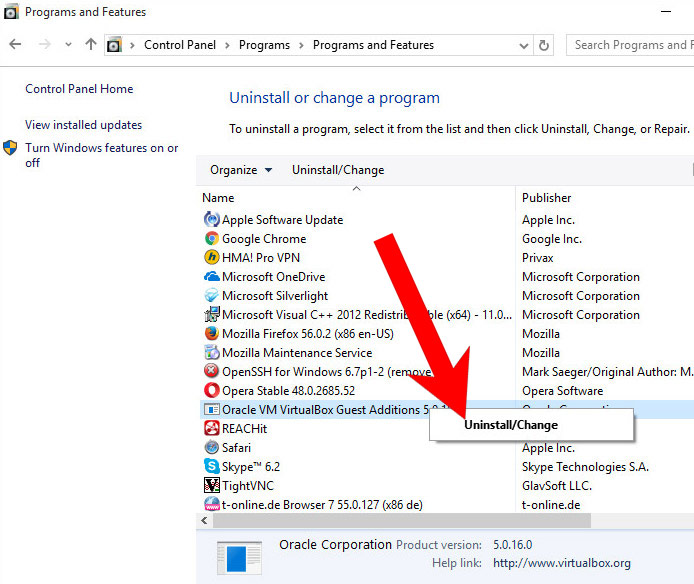
- Press on the Start icon.

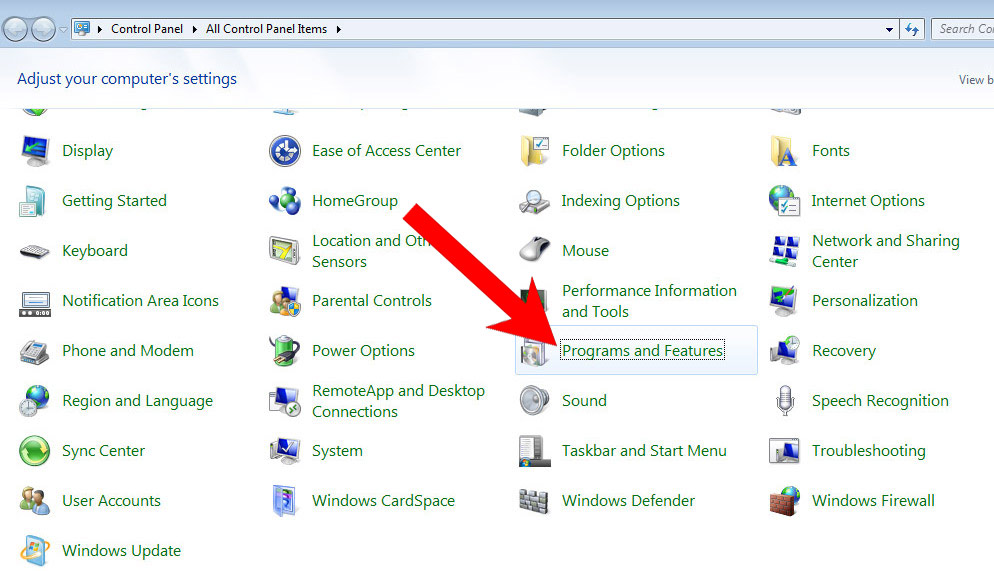
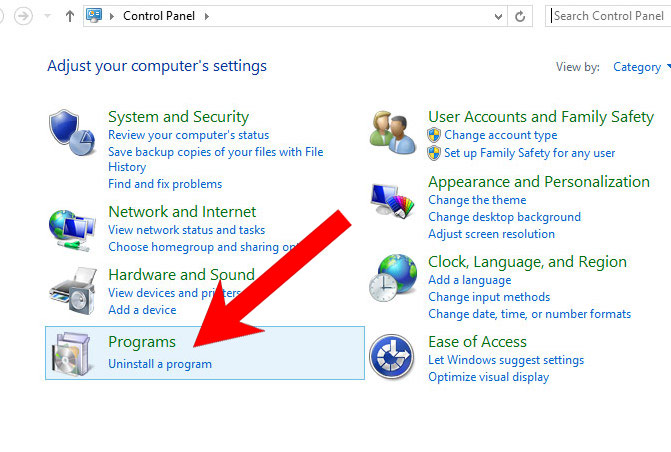
- Control Panel → Programs and Features.

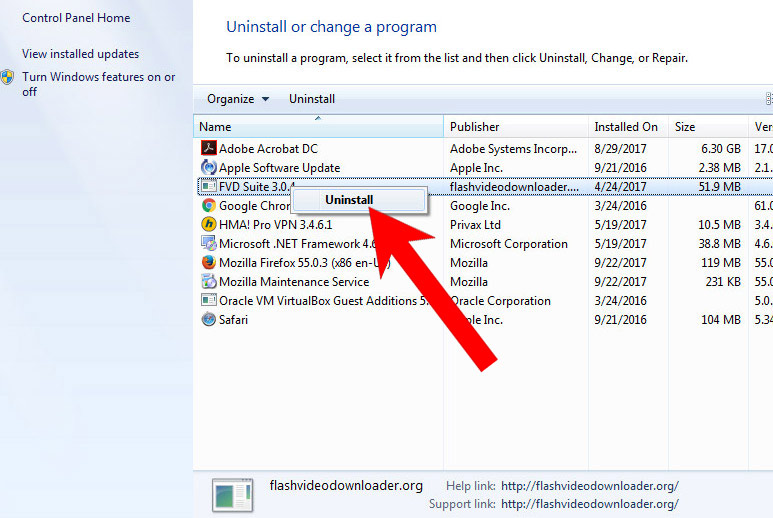
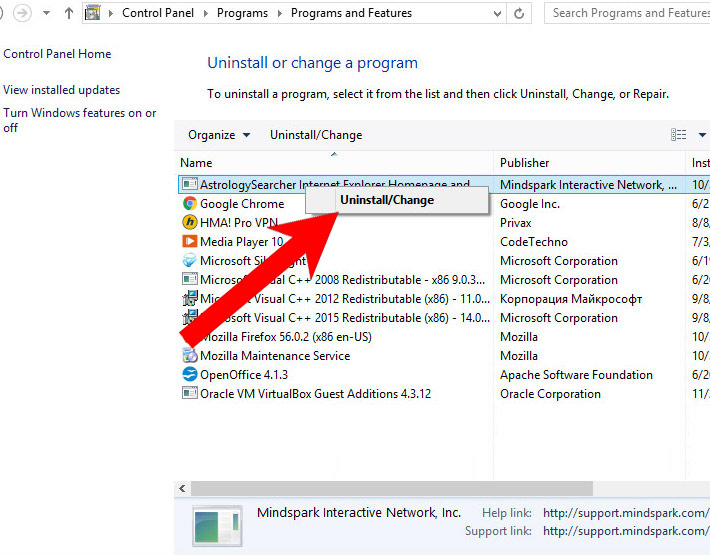
- Find the program you want to delete and press Uninstall.

b) Windows 8
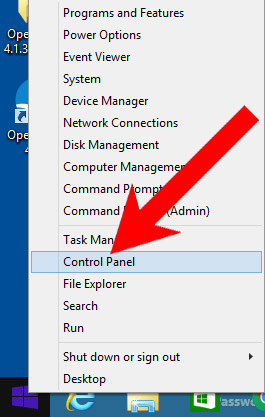
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

c) Windows 10
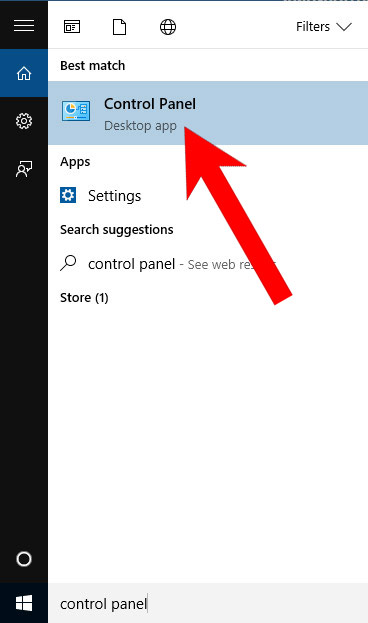
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

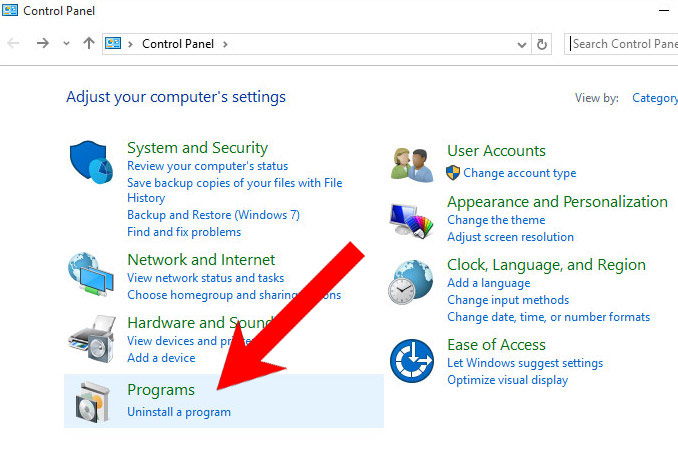
- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

d) Mac OS X
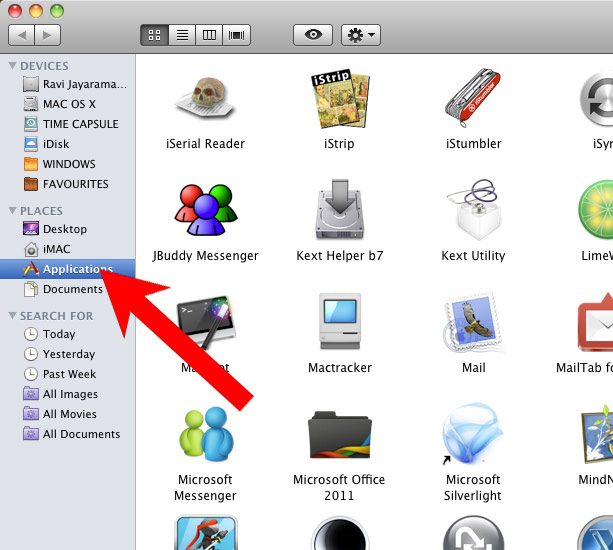
- Open Finder and press Applications.

- Check all suspicious programs you want to get rid of.
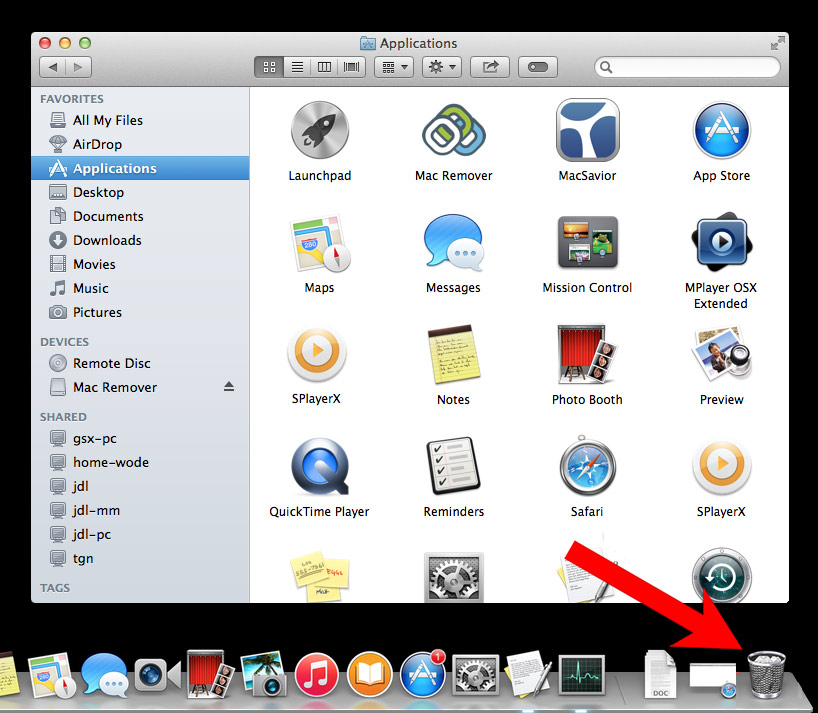
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete Trojan.W97M.CVE202230190.A from browsers
a) Remove Trojan.W97M.CVE202230190.A from Microsoft Edge
Reset Microsoft Edge (Method 1)
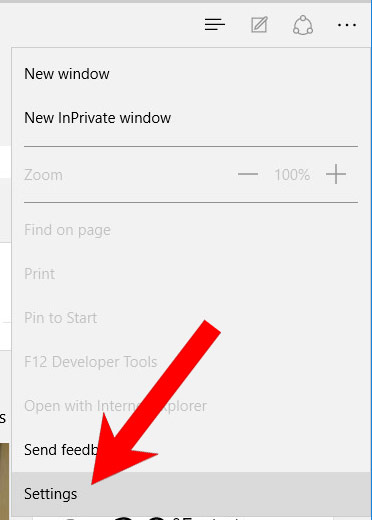
- Open Microsoft Edge.
- Press More located at the top right corner of the screen (the three dots).

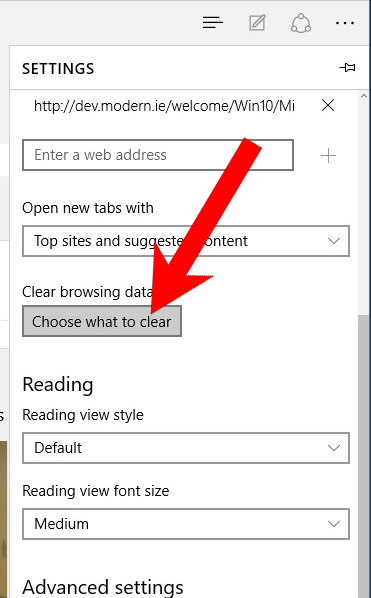
- Settings → Choose what to clear.

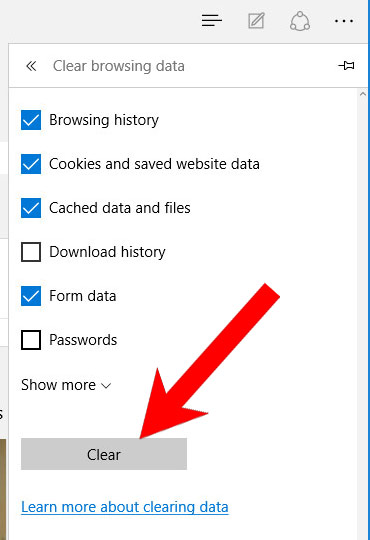
- Check the boxes of the items you want removed, and press Clear.

- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
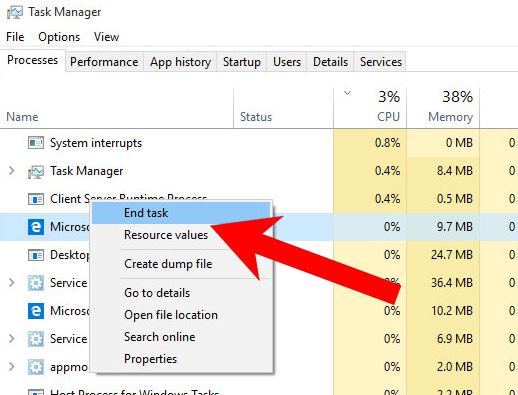
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
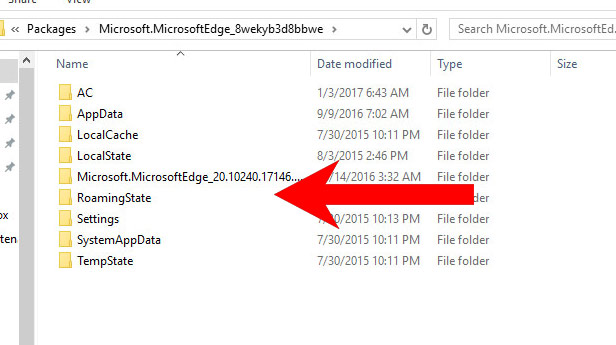
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

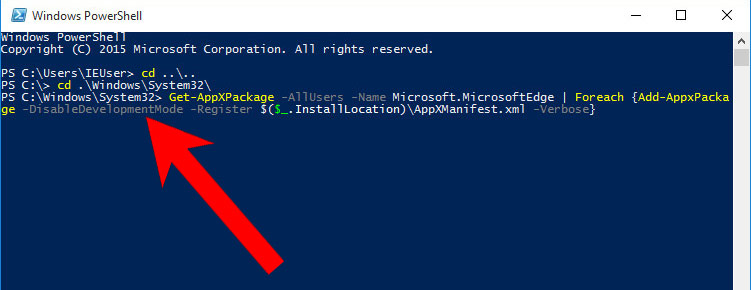
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
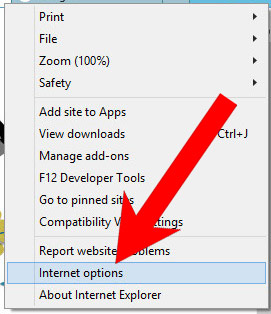
b) Remove Trojan.W97M.CVE202230190.A from Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
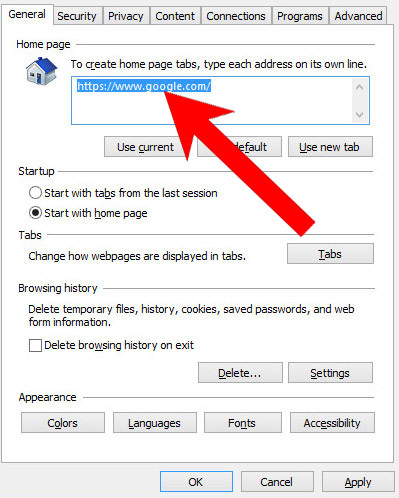
c) Restore your homepage on Internet Explorer
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
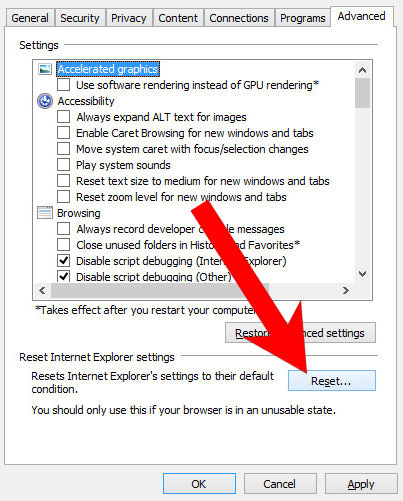
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

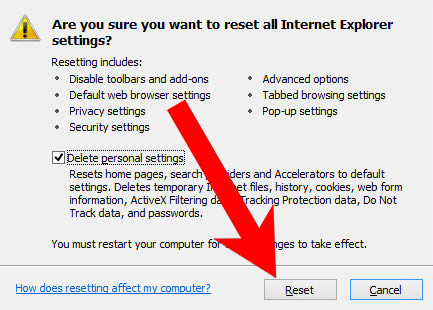
- At the bottom, you will see a Reset button. Press that.
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
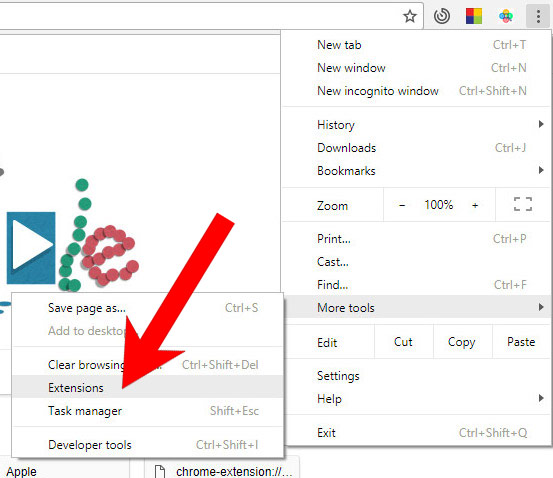
e) Remove Trojan.W97M.CVE202230190.A from Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose More tools and Extensions.

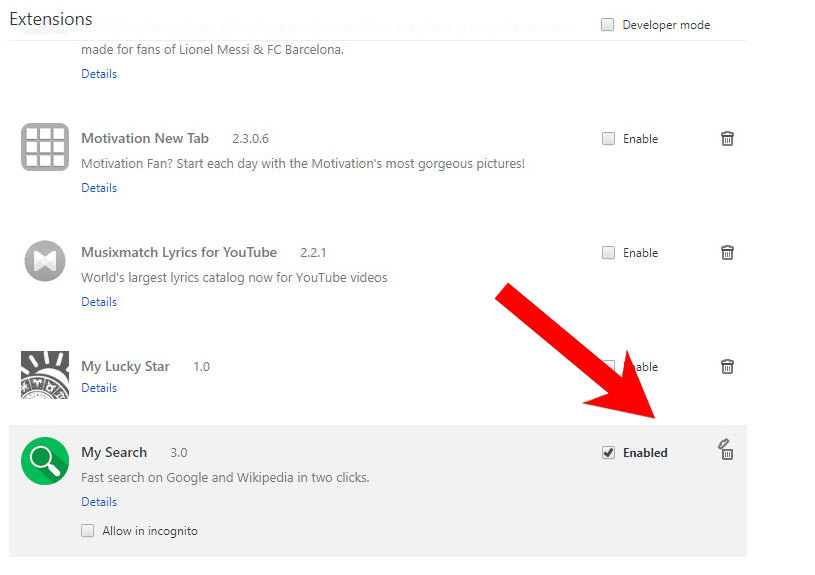
- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
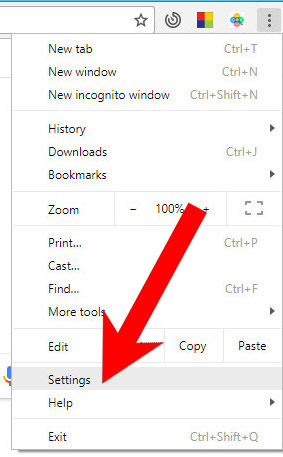
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

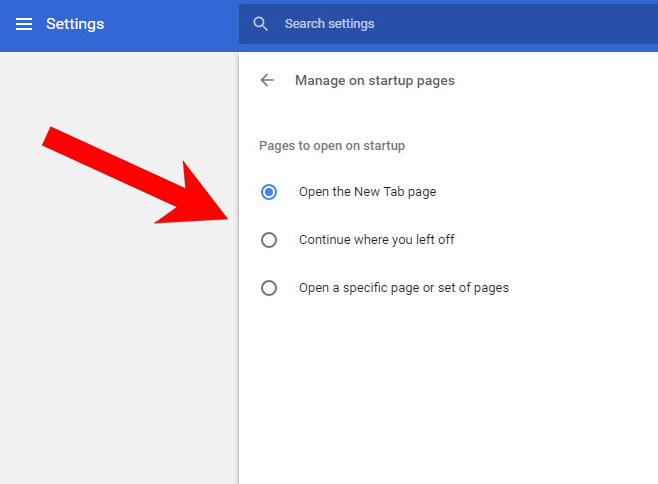
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

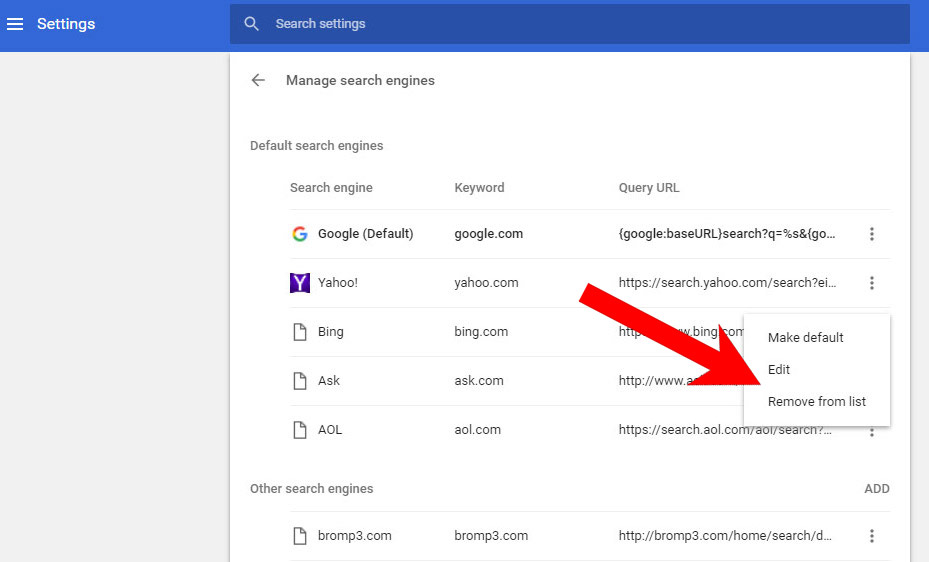
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
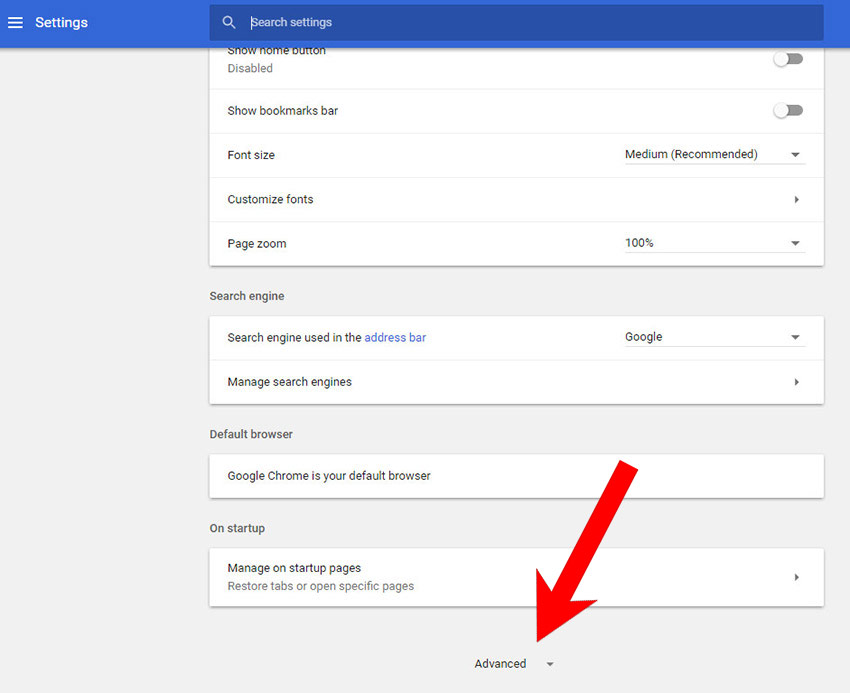
- Choose Settings.

- Scroll down and press on Show advanced settings.

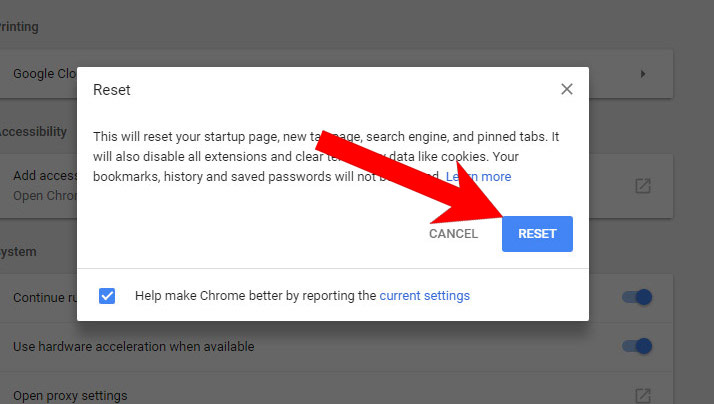
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
h) Remove Trojan.W97M.CVE202230190.A from Mozilla Firefox
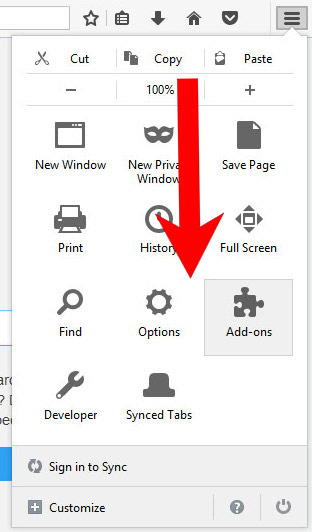
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Select Add-ons.

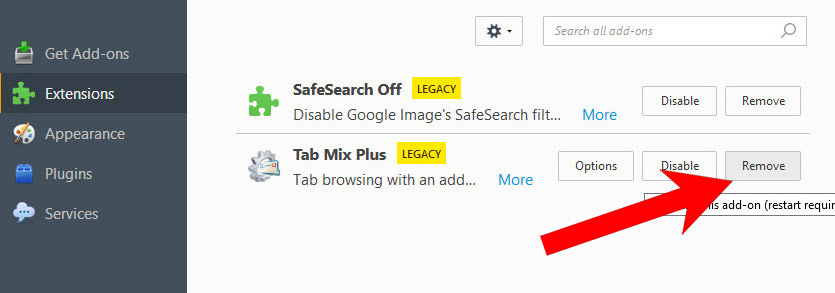
- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
i) Restore your homepage on Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
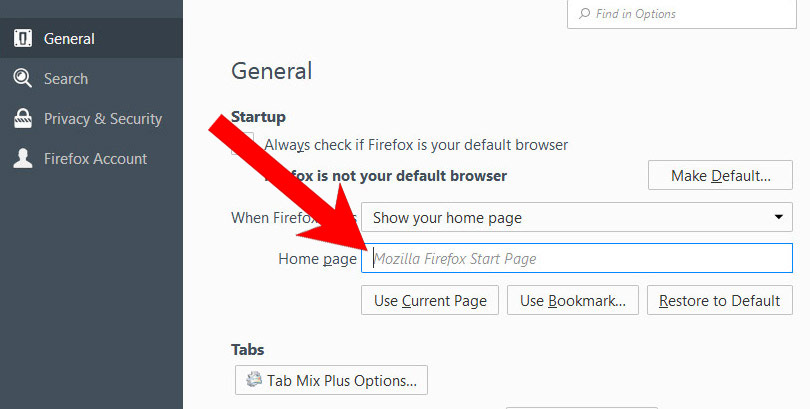
- Select Options.

- In General, click Restore to Default below the Home Page field.

j) Reset Mozilla Firefox
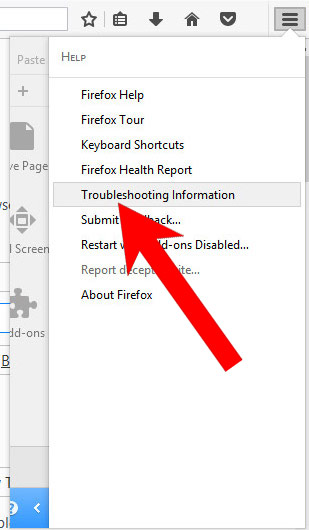
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

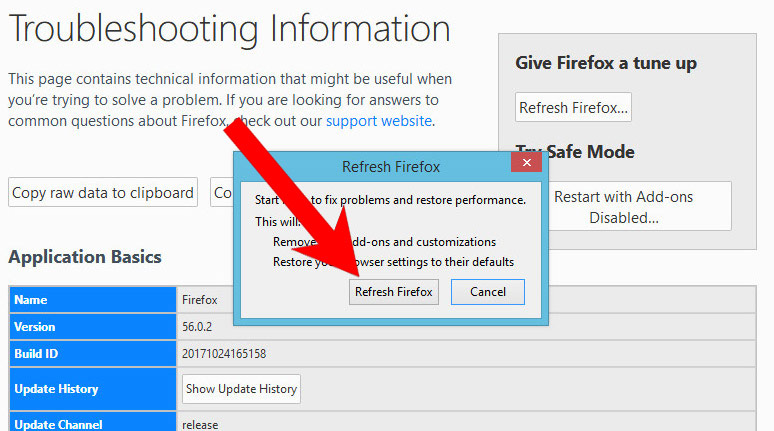
- Select the Refresh Firefox option.

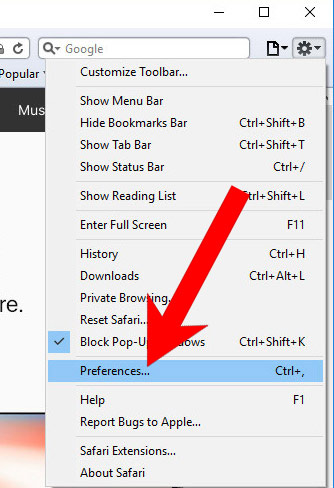
k) Remove Trojan.W97M.CVE202230190.A from Safari (for Mac)
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

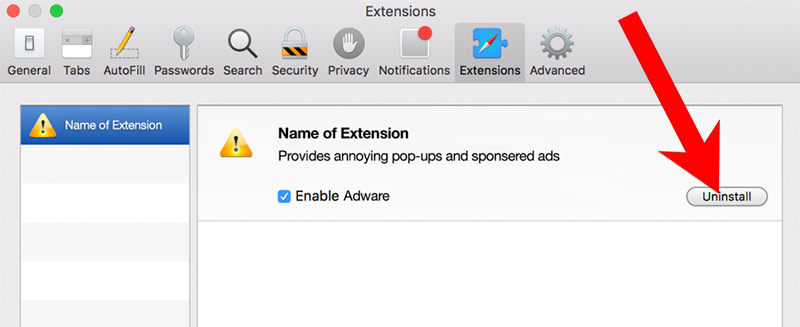
- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
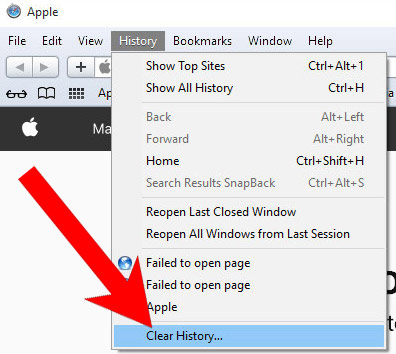
l) Reset Safari
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
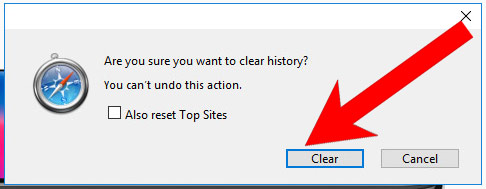
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

- Press on Safari at the top of the screen and select Preferences.

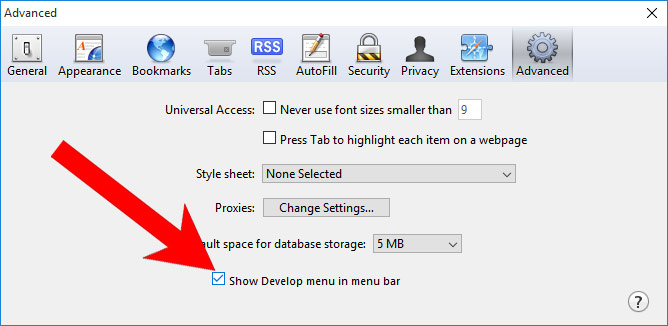
- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.