In the succeeding lines, we will attempt to address the usual malevolent implements of the contamination and its circulated channels so to advocate our readers in shielding their operating systems from it. If the info on this site arrives into you after Torpig has already infiltrated your os, you will then find precise instructions on how to eliminate this Trojan right below the post. Our security team has developed a thorough removal guidelines that explains in detail how to detect and terminate the all the infected files connected to this issue in a stage-by-step scheme.
Trojans are really complicated types of malicious software that could have different corrupt goals. Usually, cyber criminals who progress such malign pieces of applications use them for various unlawful process and shall schedule it according to their wants and criminal objectives. Sadly, each Trojan may be configured to execute something several and you can’t figure out what it may be until you encounter the bad results of its breach. Moreover, perils like Torpig, Wup.exe and Presenoker can endanger and contaminate your full device without providing any conspicuous signs of their appearance or process.
Download Removal Toolto remove TorpigA single Trojan Horse malicious software can commonly set up other problems in the operating system without any apparent signs. If not erased on time, Torpig, such as, may insert any arrangement of Ransomware, malware or akin malicious software into your computer. Besides, the Trojan can unidentified beginning varying malevolent scripts via a backdoor or take advantage of the device’s cracks to overlook the detection of the freshly included malicious software by defense tool.
The cyber crooks who remain behind the Trojan could always use it to accumulate private data connected to you or your place of operate and your commercial business. Passwords, bank quantities, personal identity documents, emails, contacts, etc., might be exposed to a remote server maintained by the criminals as. And when this data enters in their hands, the crooks could use it to harass you in a bunch of approaches, containing to blackmail you or to use your bank accounts.
Aside from all that we have just noted earlier, a Trojan for instance Torpig can offer remote entry to the corrupted machine for its designers. This proves the cyber criminals can promptly get into the full computer and make modifications to its registry keys, device indications, procedures and program.
The longer the infections stays in the device, the more harm it may create. In other words why the thing you ought to do as soon as you notice Torpig is to uninstall it without a wait, hopefully, former it has crafted any huge damage to your operating system.
If you have never ran into Trojans previous, you undoubtedly may call for help to deal with this viruses appropriately. That’s why, as we said, our analysts has produced a thorough removal instructions to assist you in identifying and uninstall all the Torpig akin files. We encourage you use the guides there in a package with a proper uninstallation program for hasty and successful Trojan termination.
Learn how to remove Torpig from your computer
Step 1. Torpig Removal from Windows
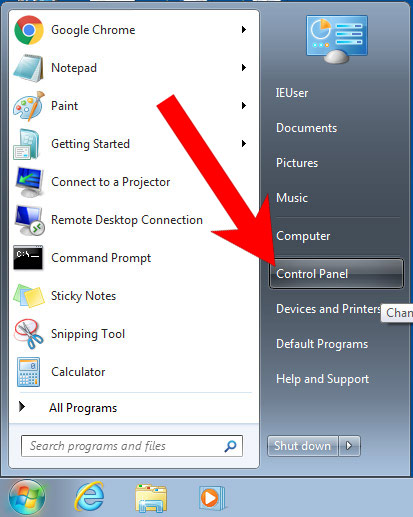
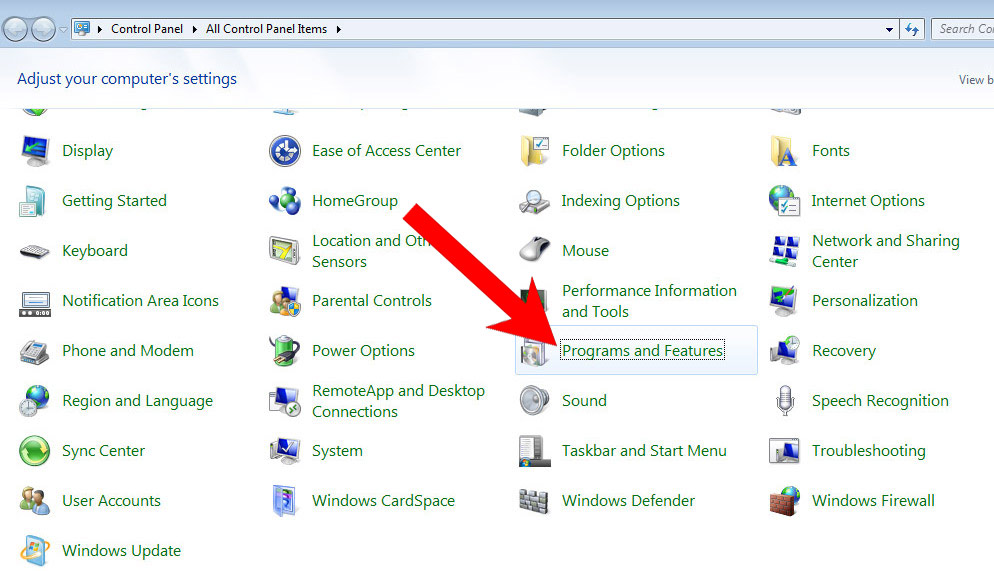
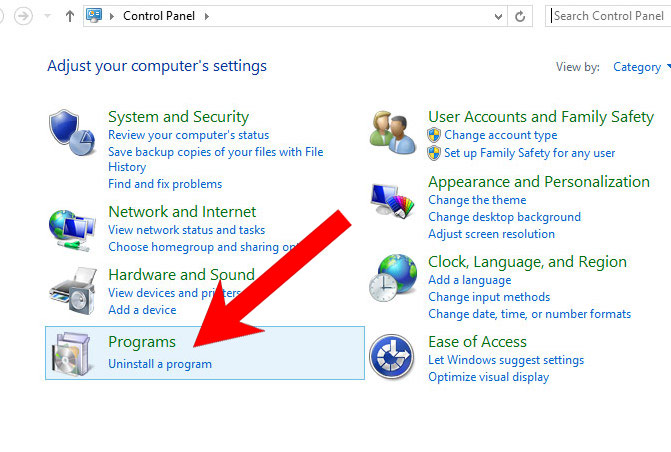
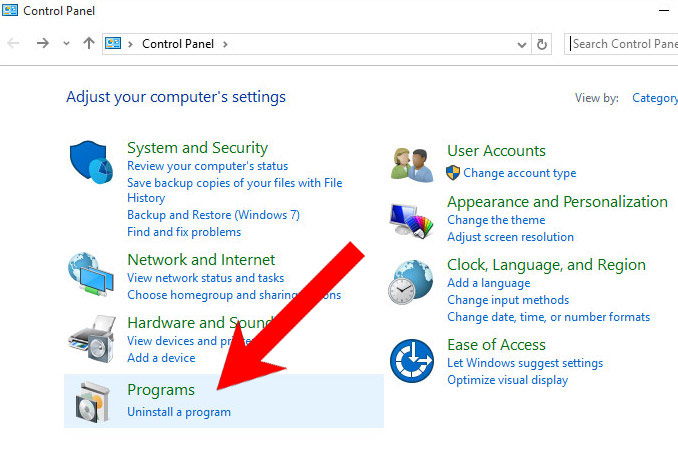
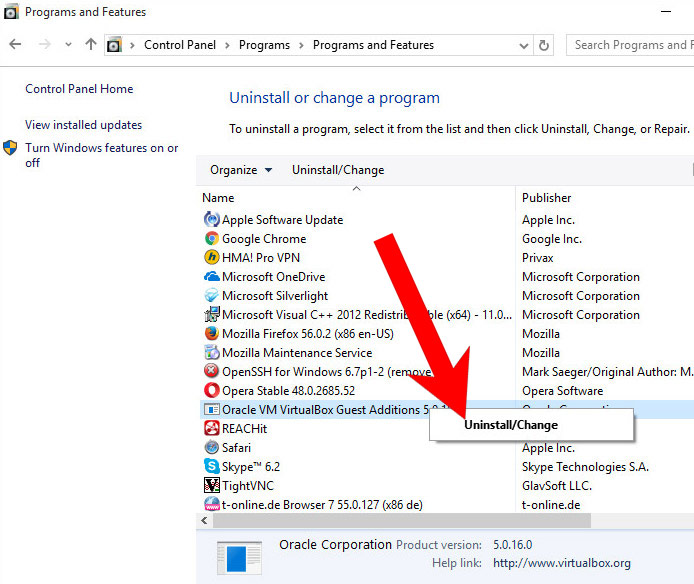
a) Windows 7/XP
- Press on the Start icon.

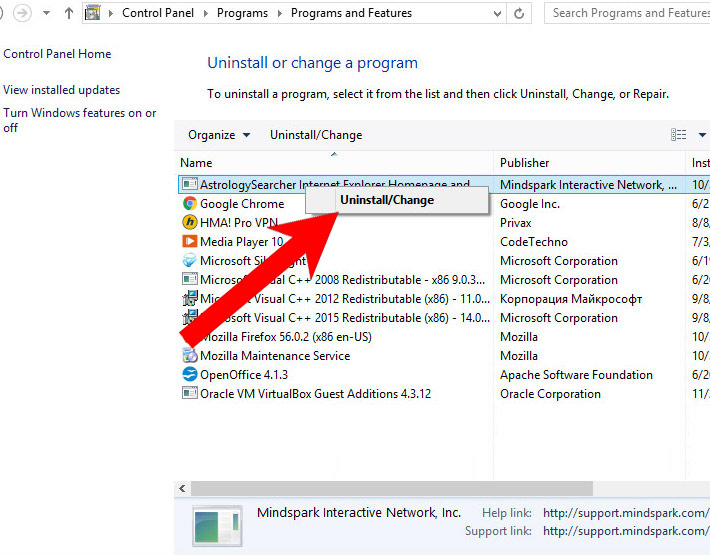
- Control Panel → Programs and Features.

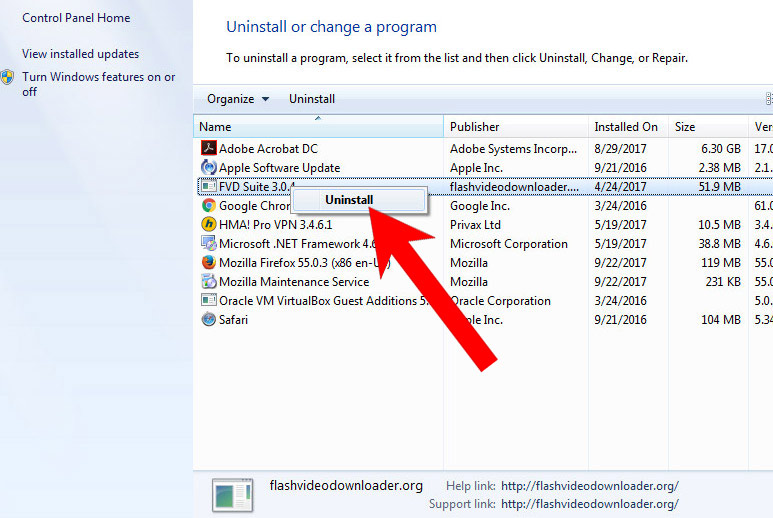
- Find the program you want to delete and press Uninstall.

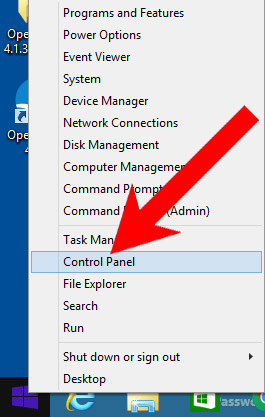
b) Windows 8
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

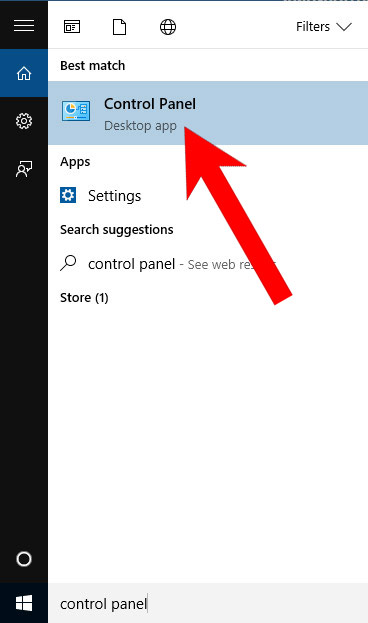
c) Windows 10
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

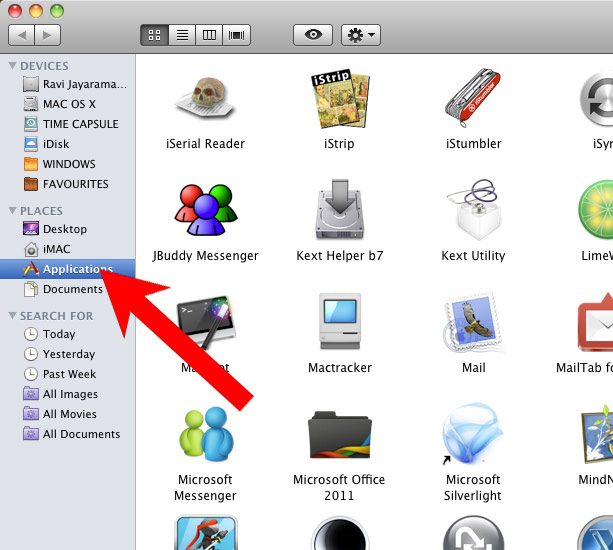
d) Mac OS X
- Open Finder and press Applications.

- Check all suspicious programs you want to get rid of.
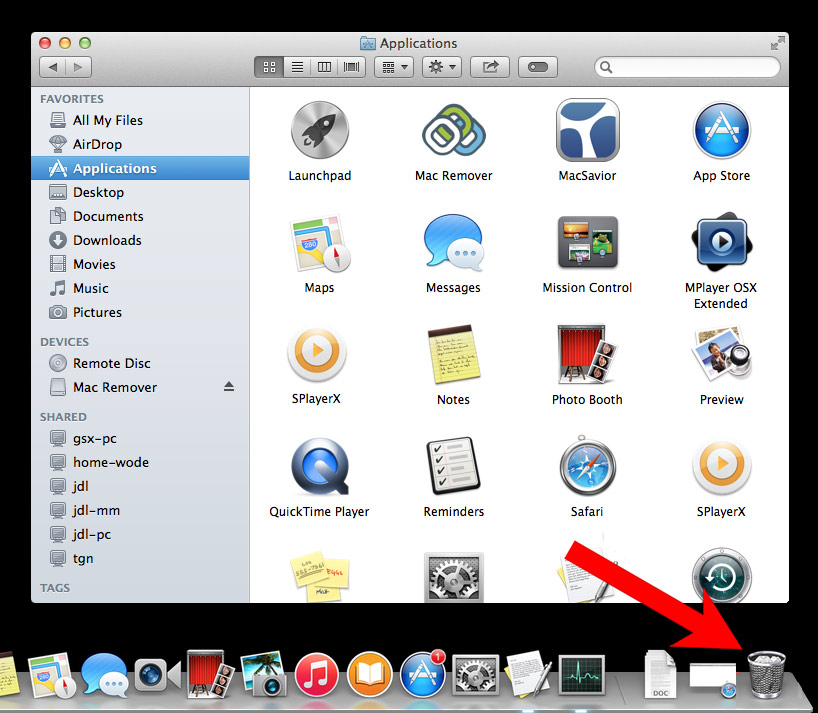
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete Torpig from browsers
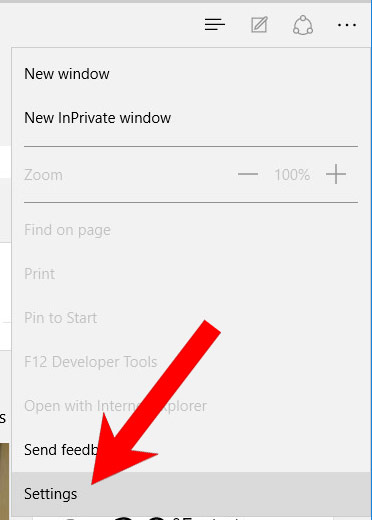
a) Remove Torpig from Microsoft Edge
Reset Microsoft Edge (Method 1)
- Open Microsoft Edge.
- Press More located at the top right corner of the screen (the three dots).

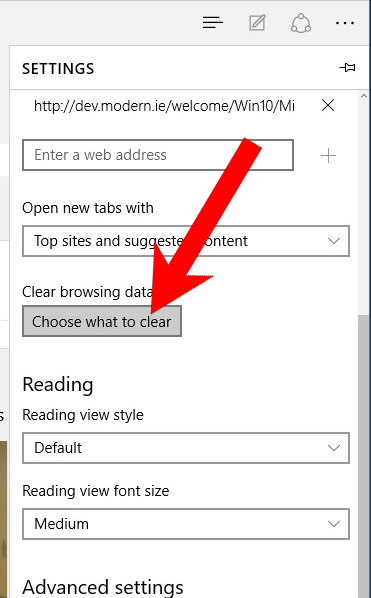
- Settings → Choose what to clear.

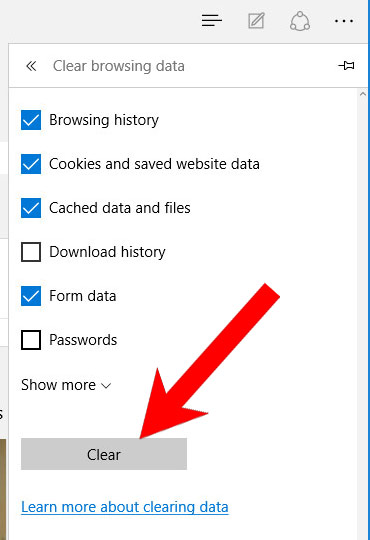
- Check the boxes of the items you want removed, and press Clear.

- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
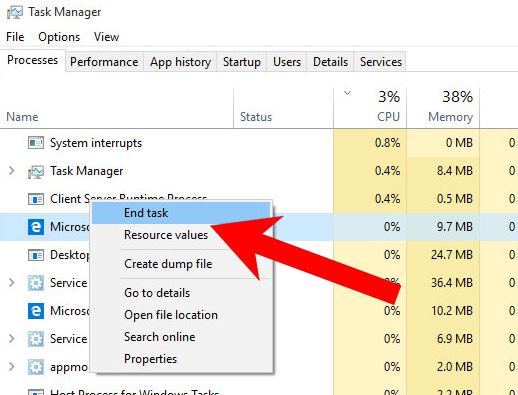
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
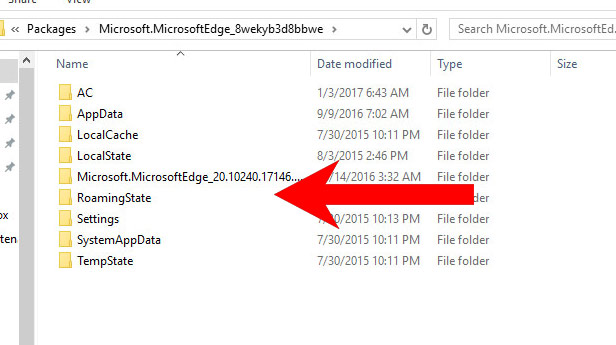
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

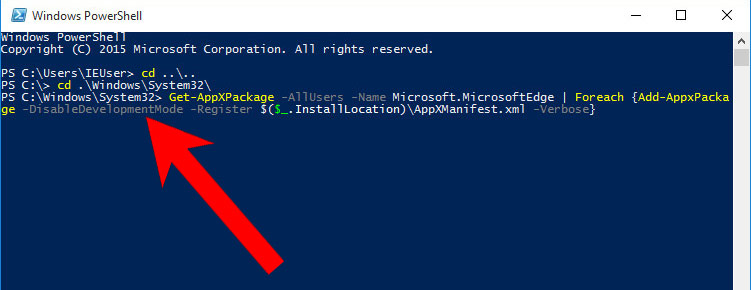
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
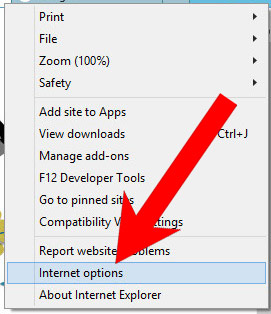
b) Remove Torpig from Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
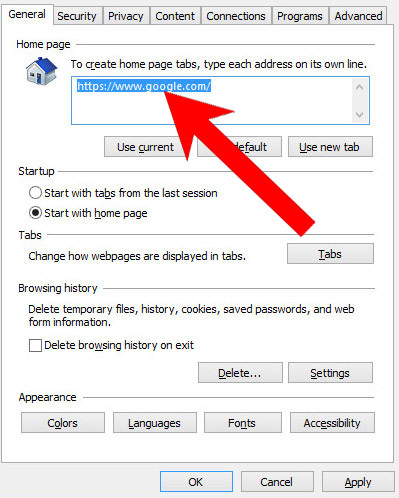
c) Restore your homepage on Internet Explorer
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
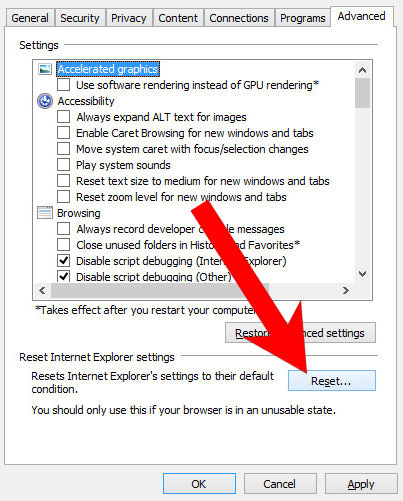
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

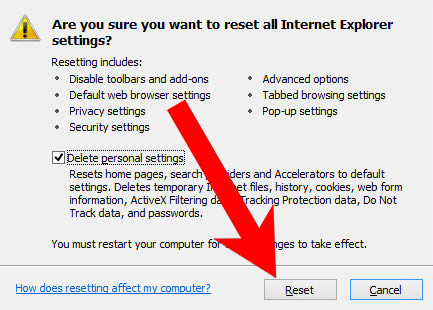
- At the bottom, you will see a Reset button. Press that.
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
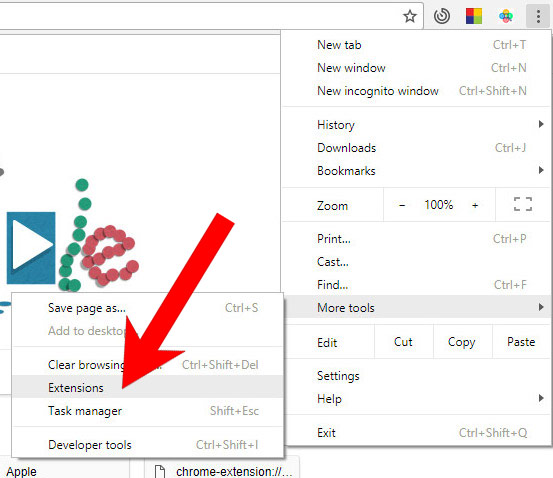
e) Remove Torpig from Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
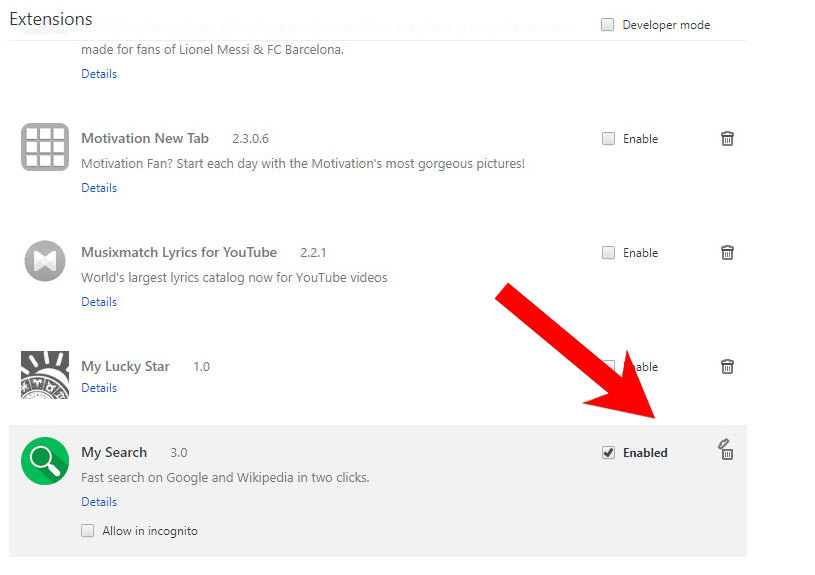
- Choose More tools and Extensions.

- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
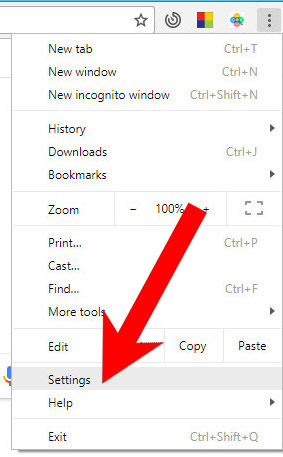
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

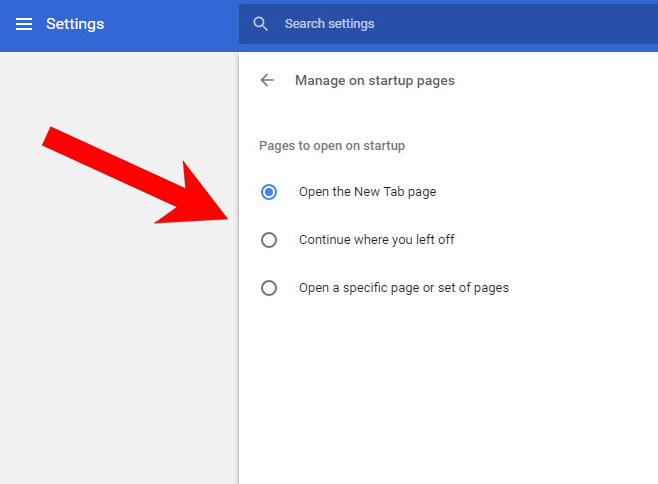
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

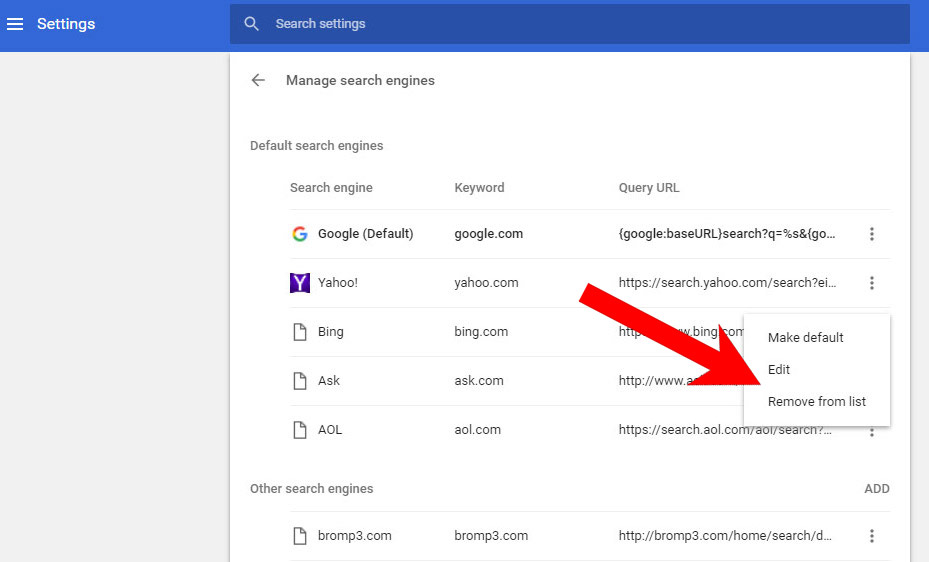
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
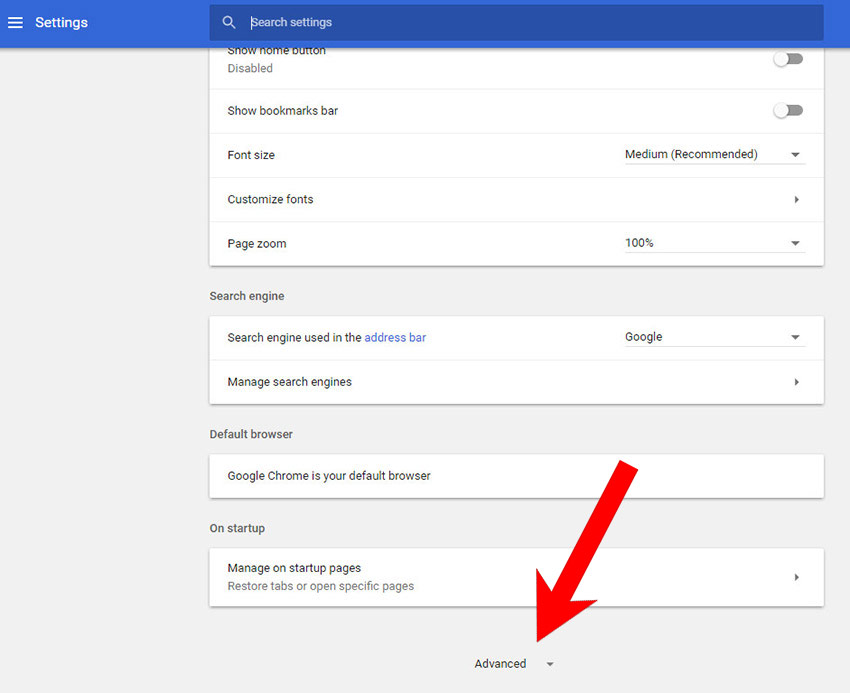
- Choose Settings.

- Scroll down and press on Show advanced settings.

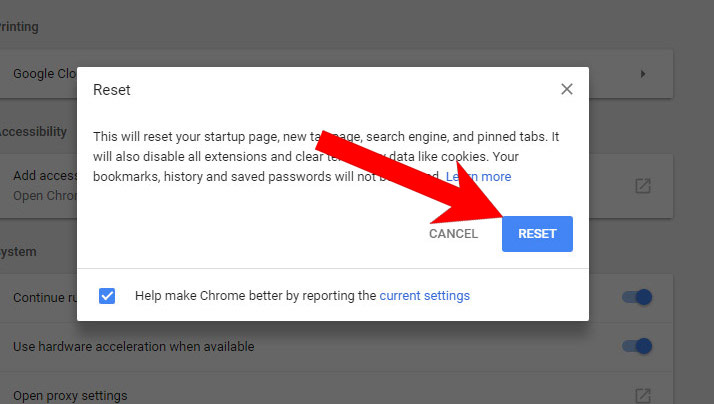
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
h) Remove Torpig from Mozilla Firefox
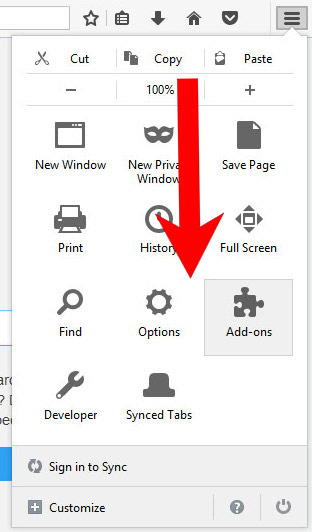
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Select Add-ons.

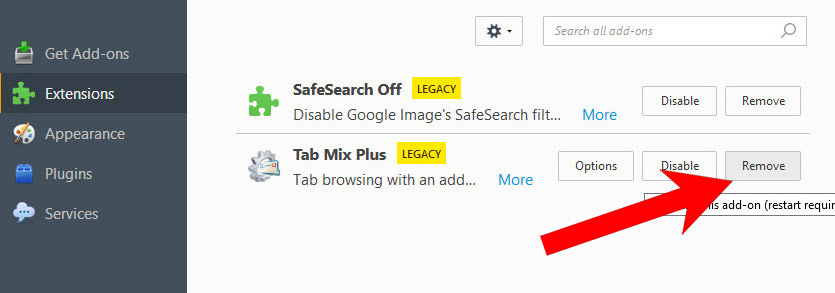
- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
i) Restore your homepage on Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
- Select Options.

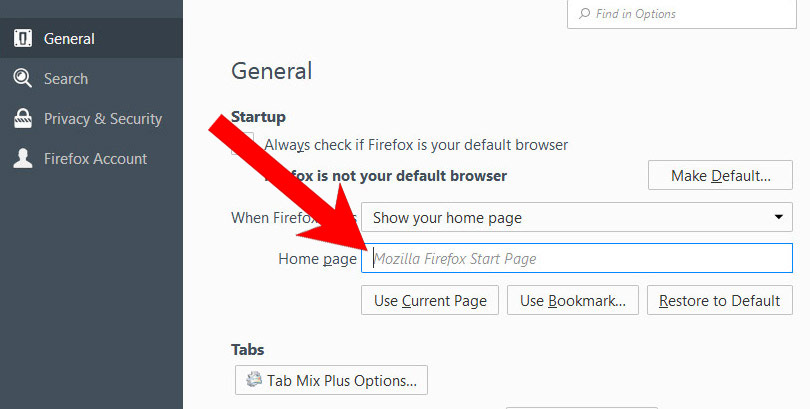
- In General, click Restore to Default below the Home Page field.

j) Reset Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
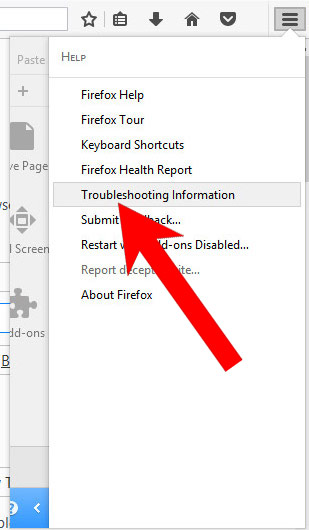
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

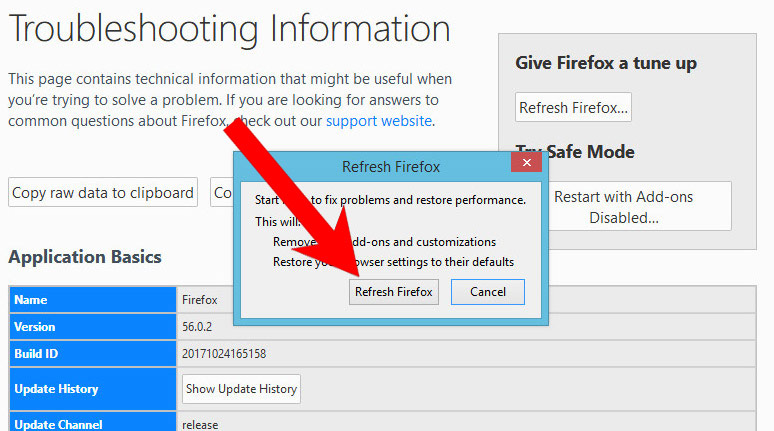
- Select the Refresh Firefox option.

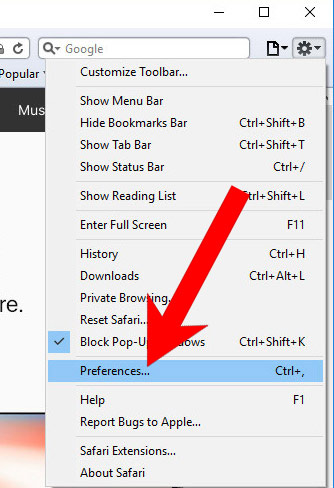
k) Remove Torpig from Safari (for Mac)
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

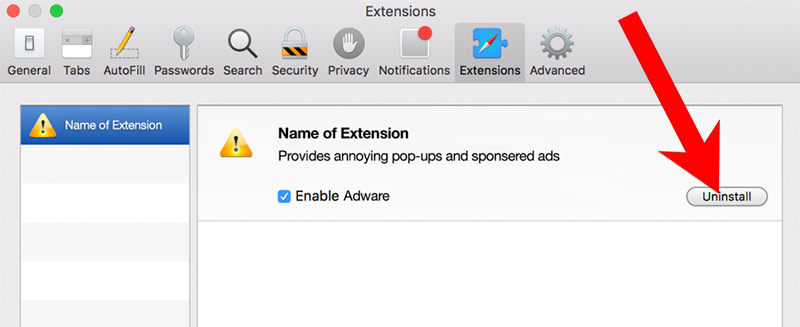
- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
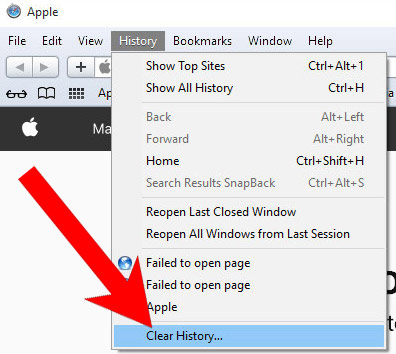
l) Reset Safari
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
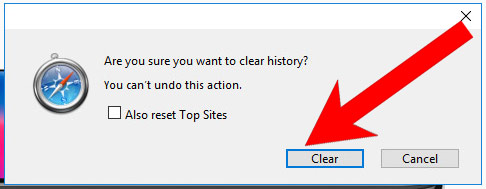
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

- Press on Safari at the top of the screen and select Preferences.

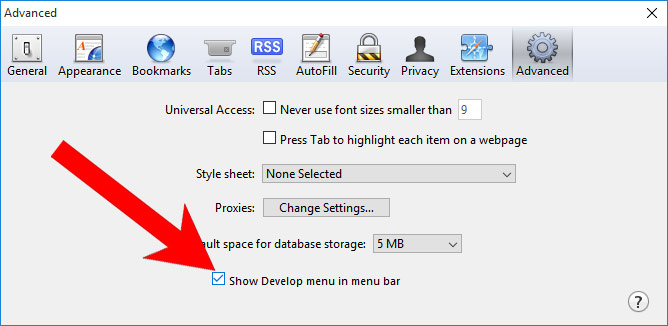
- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
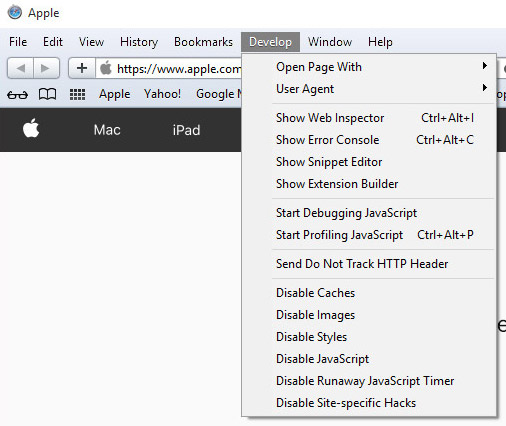
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.