Trojan horse, or as the biggest part of users call them Trojans, are among the the biggest part of widespread and the biggest part of mischievous parasite classes on the net. On this website, we shall share in addition to you relevant information on how to shield your pc from these malicious software, how to stay away from their transmitters and, most notably, how to erase them. We are on top of that going to display you in bundles with a specialized deletion guide for one namely harmful Trojan-based parasite called “Microsoft account security data was added”. Steer together with us if you are having inconvenience along with this exact infection and implement the guide below to cautiously eliminate it. Former you scroll down, regardless, enables at the beginning grant you some minimal data relating to these kinds of fraudulent os risks. A Trojan Horse is a malicious program intended to get into the oriented user’s operating system in a greatly stealthy way and to then commit certain malignant motions in the pc. Usually, the Trojans are used to take or immoral information but they are usually also related to the circulation of other infections such as Ransomware and malware, which is the consequences of their knowledge to set up gaps in the device and to open security gaps that may easily be taken advantage of. Criminals generally use damaging such software as “Microsoft account security data was added” to get remote entry, clearly prohibited, to a system to get into its files and wreck the pc. Trojans are on top of that accustomed for financial deception, scam of details, tailing and other hurtful actions that might put the victim’s machine and privacy in significant hazard.
Download Removal Toolto remove security
The following security info was recently added to the Microsoft account
A specific trait of the infections like “The following security info was recently added to the Microsoft account” is their ability to hide deep in the system for an indefinite period of time. Normally, it is somewhat complex to find a Trojan Horse transmitter as “The following security data was newly included in the Microsoft account” generally pretends to be a lawful document or is not disclosed in some appealing note, web-link, email attachment or a utilities installer.
That’s why, if you don’t have a legitimate security program, you could easily get hoaxed into pressing on something evil and you could not even get alerted about the infection that has occured.
Threat generally means no indications of its arrival and surreptitiously starts its malicious movements in the background.
That’s why identifying and getting rid of the Trojan isn’t simple and, in the majority of cases, you might need an excellent anti-malware utility to observe it.
At this truth, the rational question of a computer user who is bothered connected to their device security is: “What complications ought to I anticipate if I get contaminated by a Trojan like “Microsoft account security data was added”?” sadly, there is no general respond to this question since Trojans are hugely resourceful elements of malicious software and may be programmed to carry out a load of certain malign processes. It all relies on what precisely the cyber criminals would like to implement them for. To offer you a common concept of their maliciousness, let’s beginning by indicating that these kinds of are viruses for the most part created to wicked statistics, to steal private data, to spy or to be spread other malicious software. Trojans may generally shape the troublesome drive so to spoil the documents stored on it or to implant other destructive code in the computer that can carry out a certain damage. Risks for example “Microsoft account security data was added” parasite might also scam information, specially monetary data and offer their developers in addition to remote entry. That’s why they need to be deleted right after you identify them.
Download Removal Toolto remove securityLearn how to remove security from your computer
Step 1. security Removal from Windows
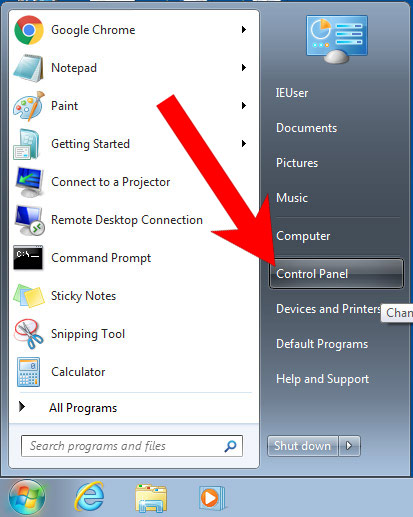
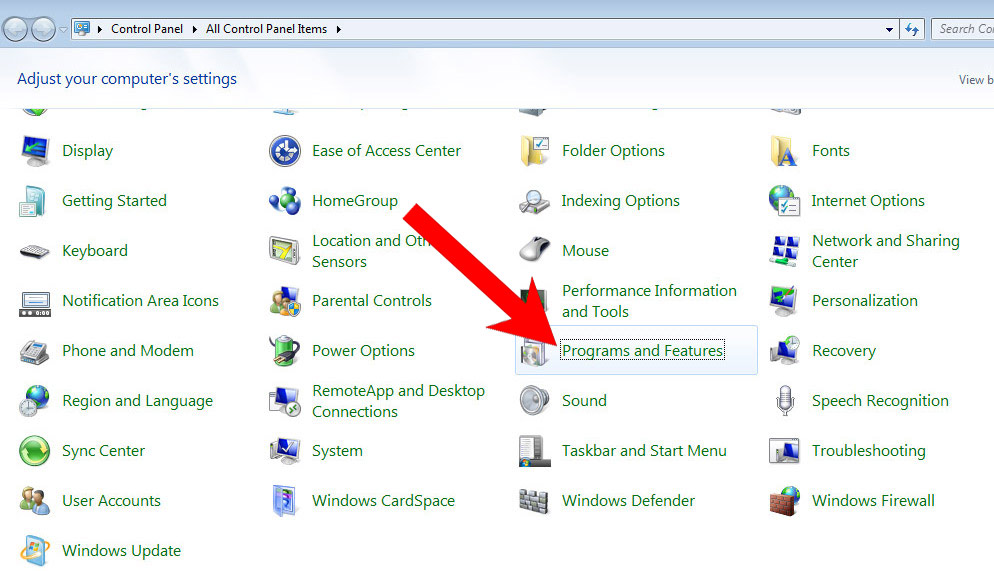
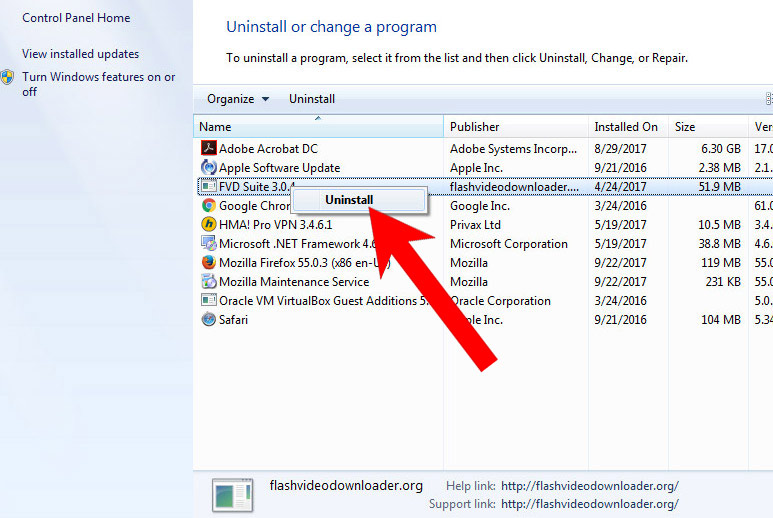
a) Windows 7/XP
- Press on the Start icon.

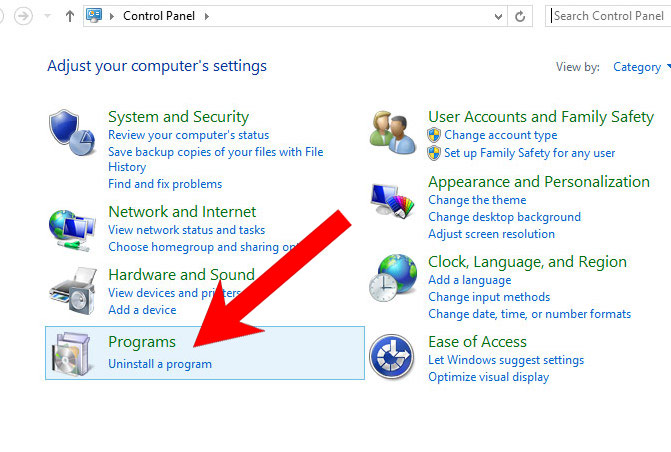
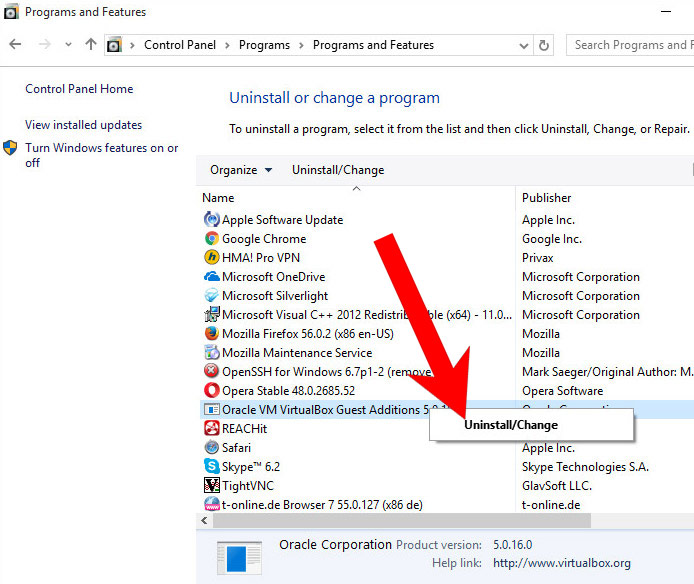
- Control Panel → Programs and Features.

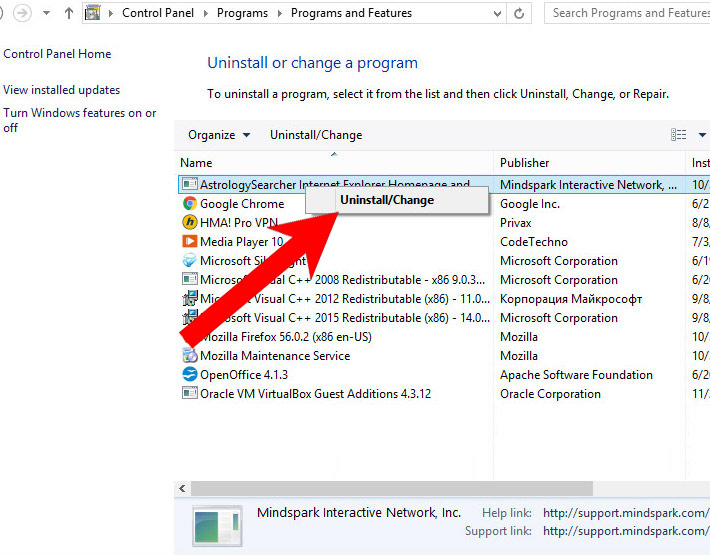
- Find the program you want to delete and press Uninstall.

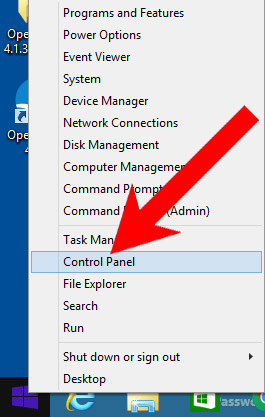
b) Windows 8
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

c) Windows 10
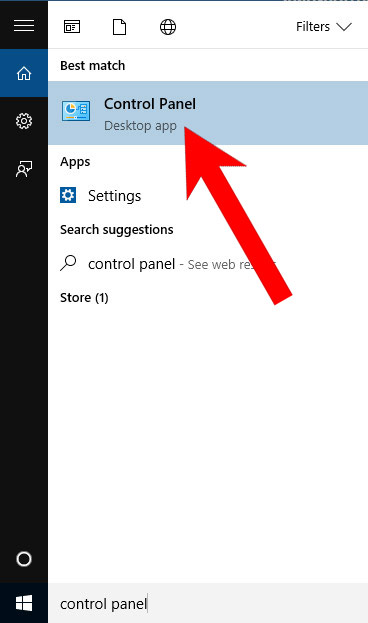
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

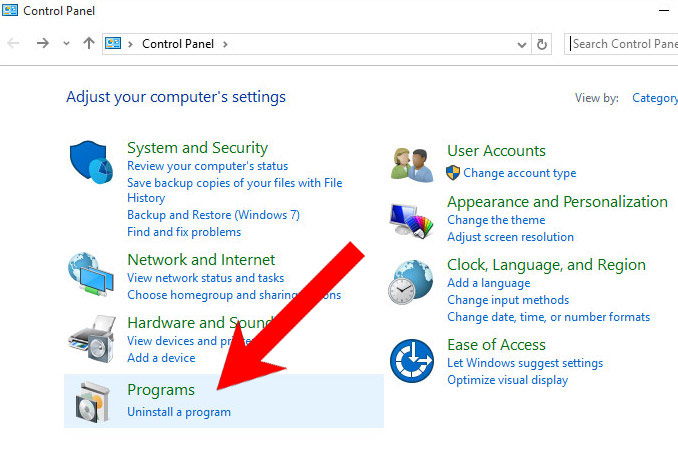
- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

d) Mac OS X
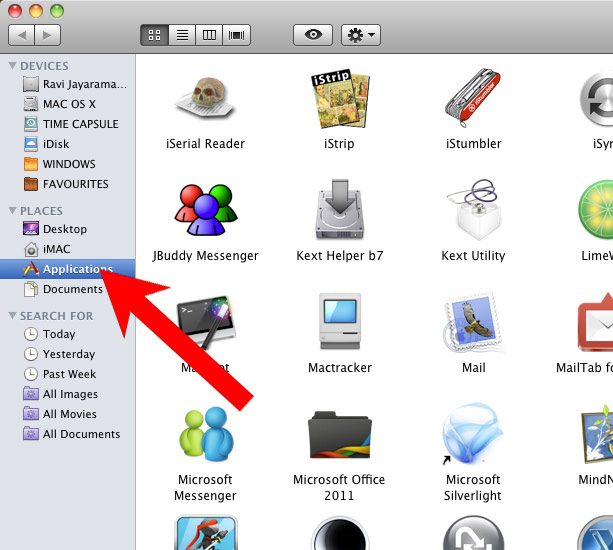
- Open Finder and press Applications.

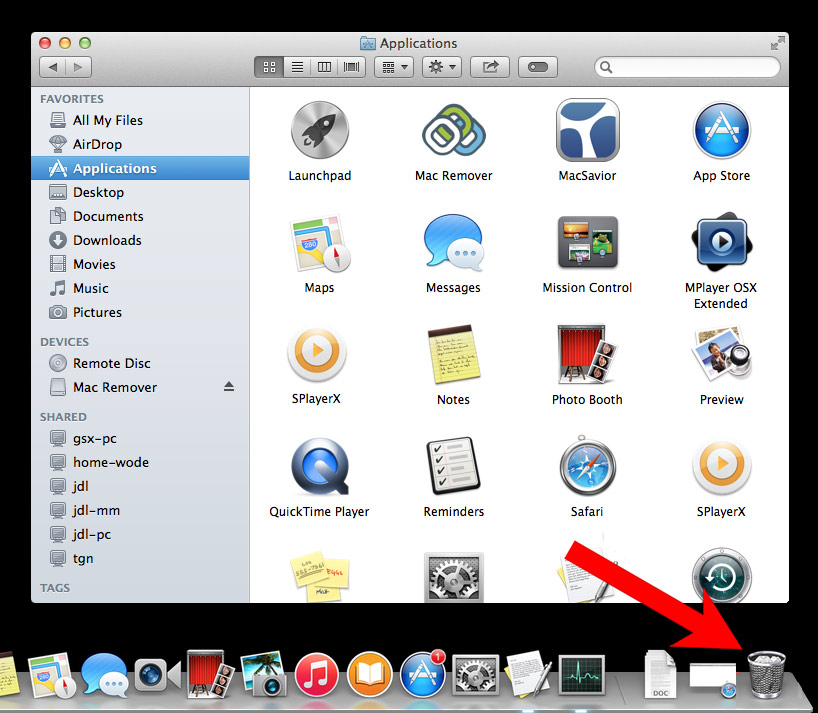
- Check all suspicious programs you want to get rid of.
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete security from browsers
a) Remove security from Microsoft Edge
Reset Microsoft Edge (Method 1)
- Open Microsoft Edge.
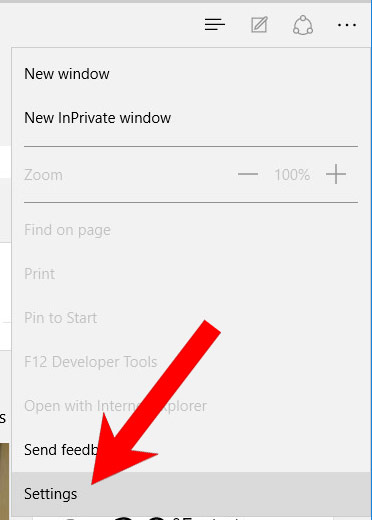
- Press More located at the top right corner of the screen (the three dots).

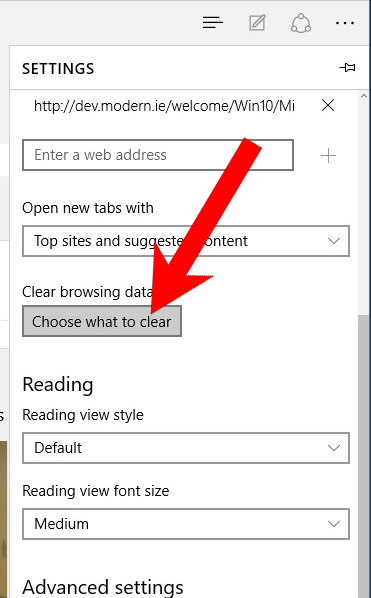
- Settings → Choose what to clear.

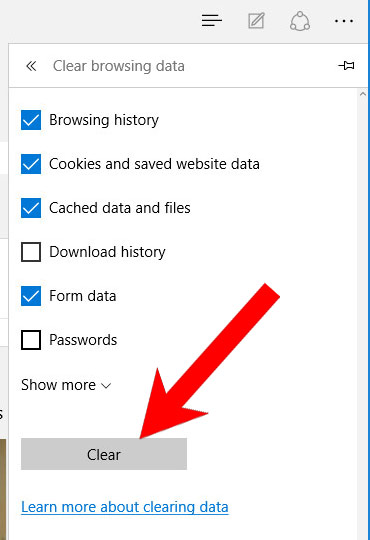
- Check the boxes of the items you want removed, and press Clear.

- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
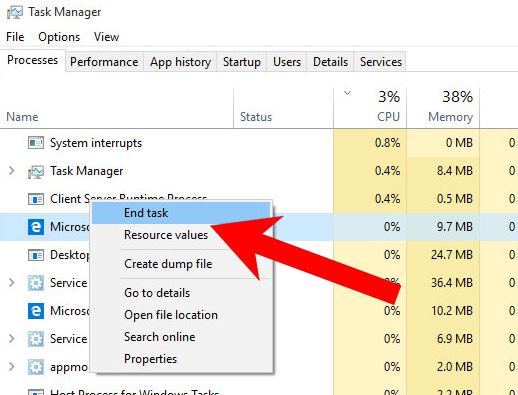
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
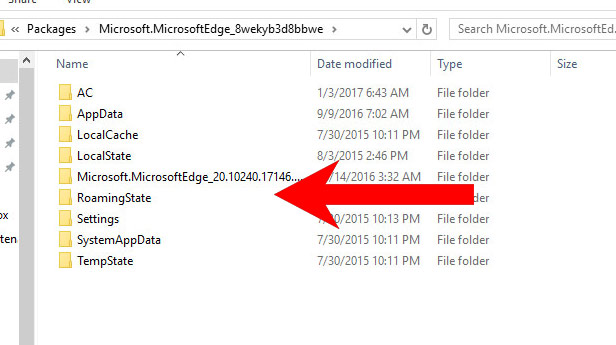
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

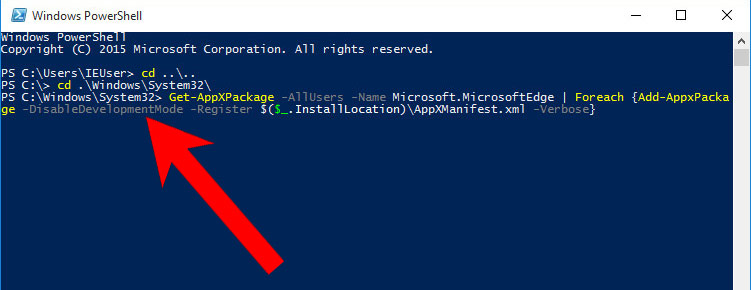
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
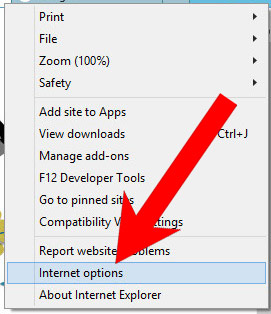
b) Remove security from Internet Explorer
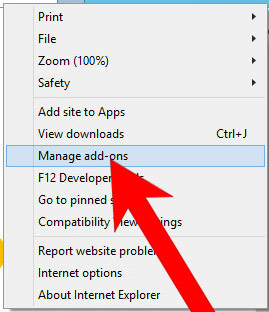
- Open Internet Explorer and press on the Gear icon.

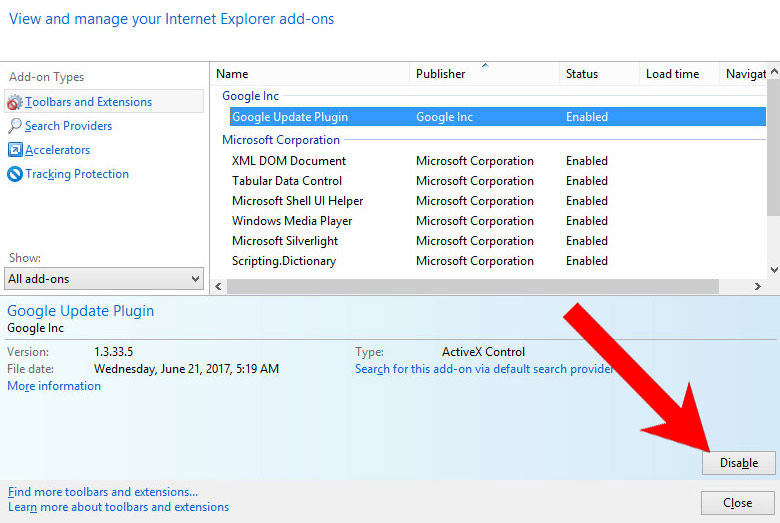
- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
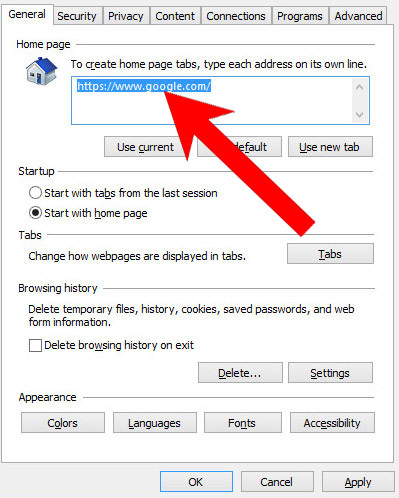
c) Restore your homepage on Internet Explorer
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
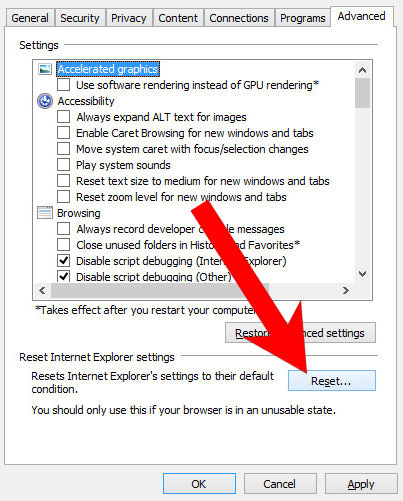
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

- At the bottom, you will see a Reset button. Press that.
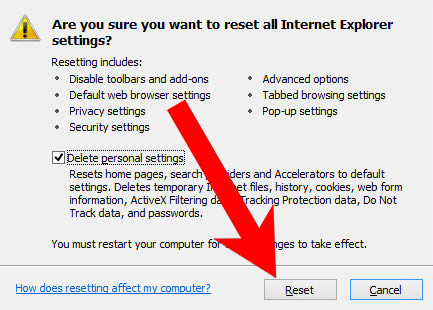
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
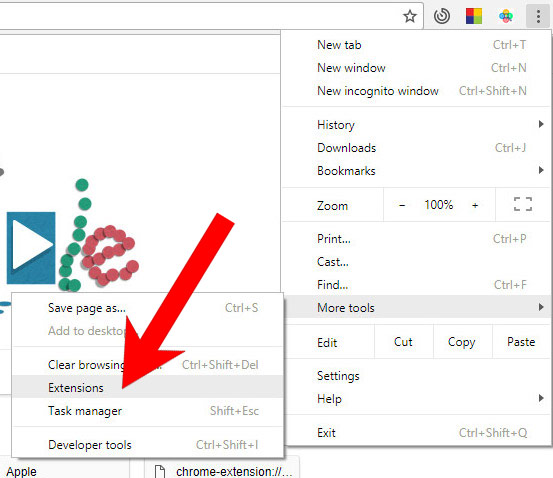
e) Remove security from Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose More tools and Extensions.

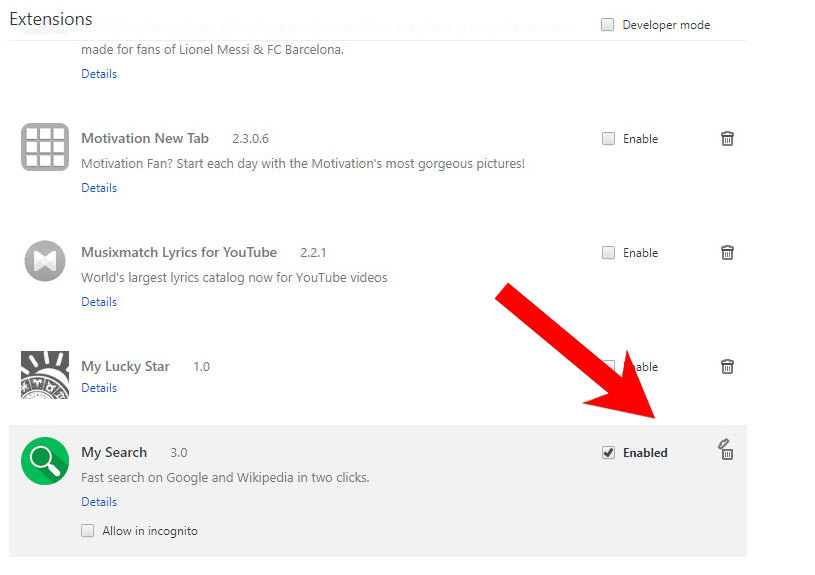
- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
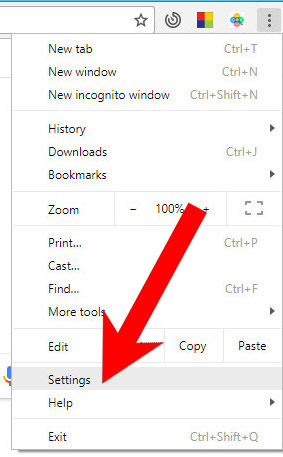
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

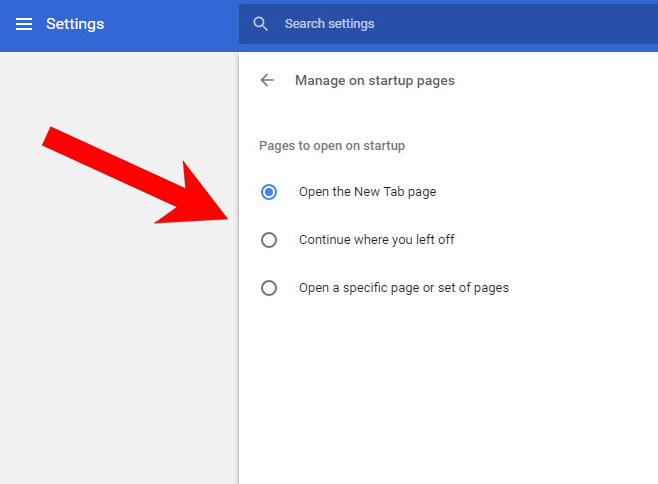
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

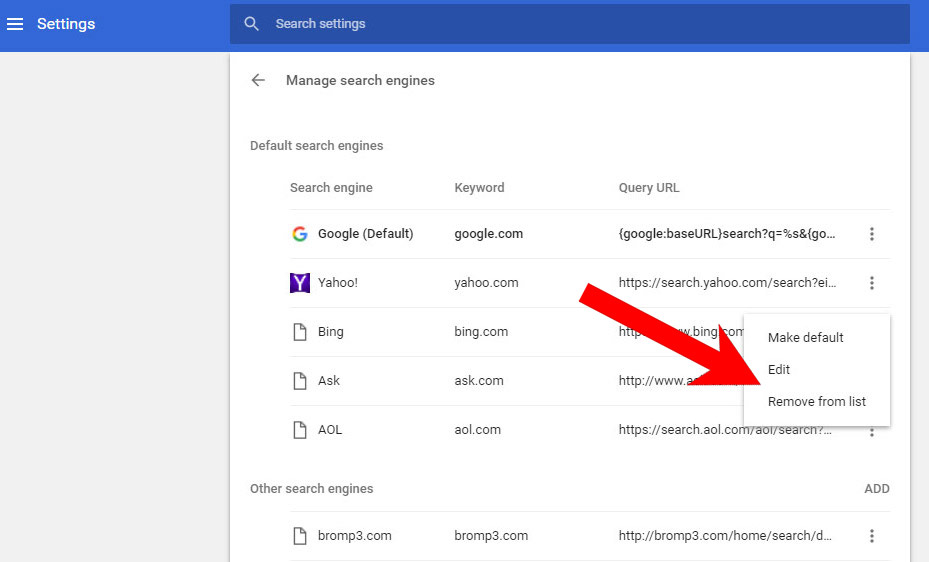
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
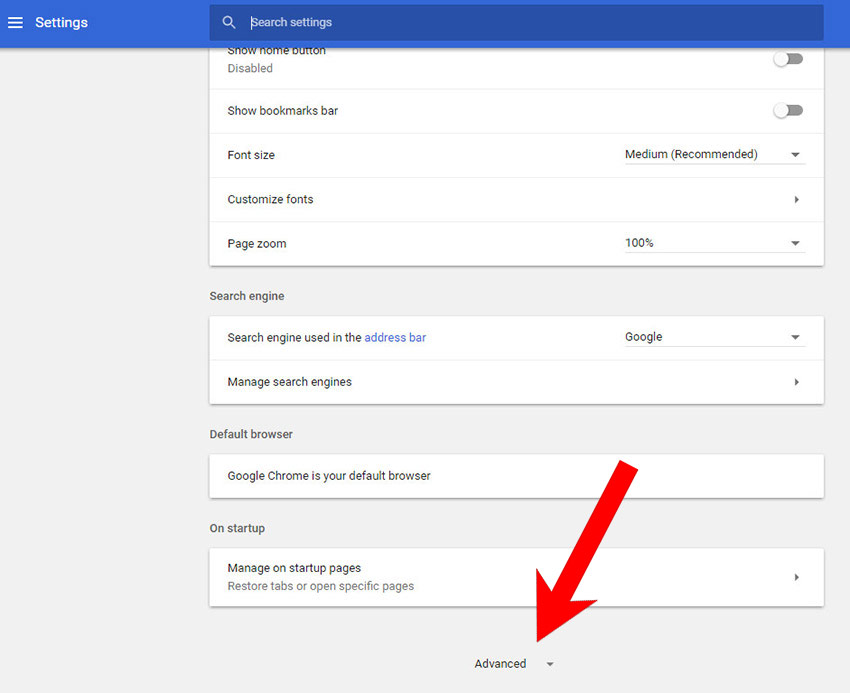
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

- Scroll down and press on Show advanced settings.

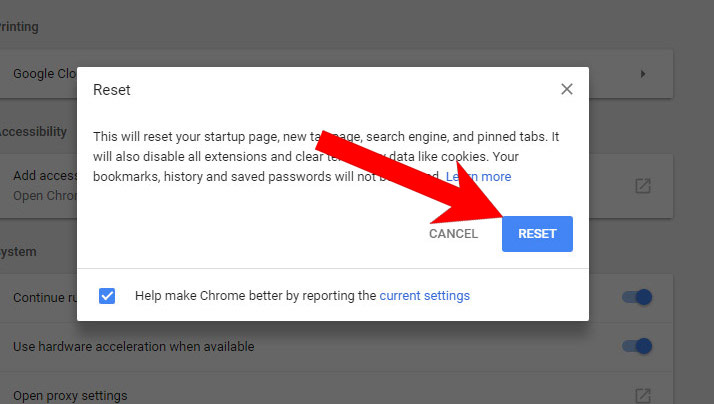
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
h) Remove security from Mozilla Firefox
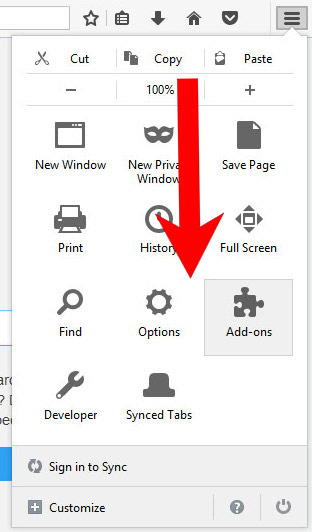
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
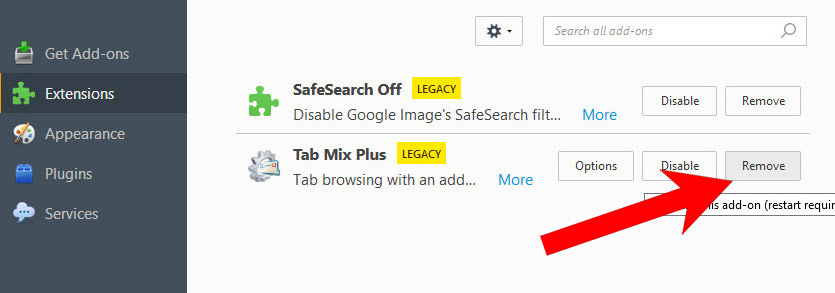
- Select Add-ons.

- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
i) Restore your homepage on Mozilla Firefox
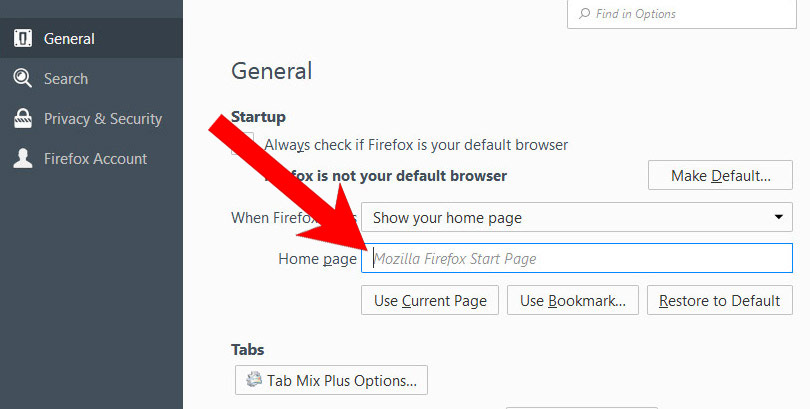
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
- Select Options.

- In General, click Restore to Default below the Home Page field.

j) Reset Mozilla Firefox
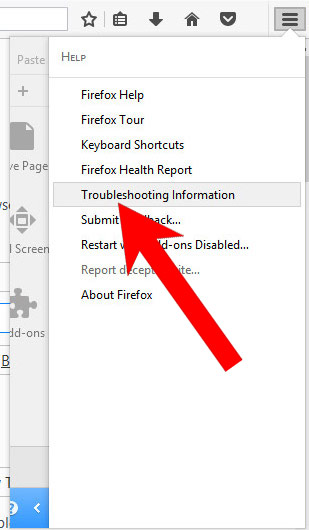
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

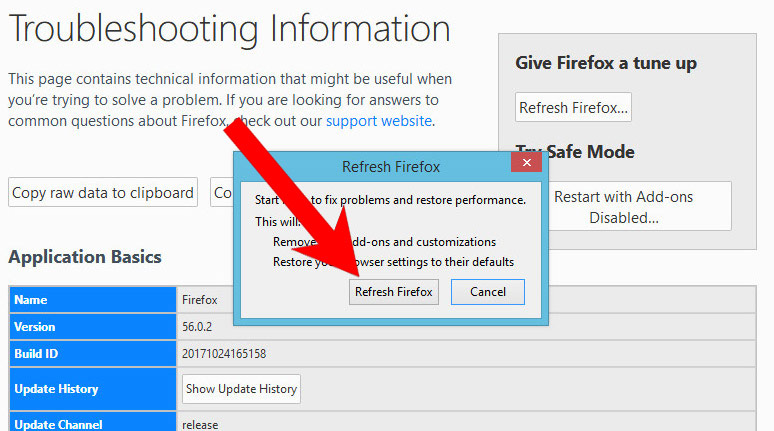
- Select the Refresh Firefox option.

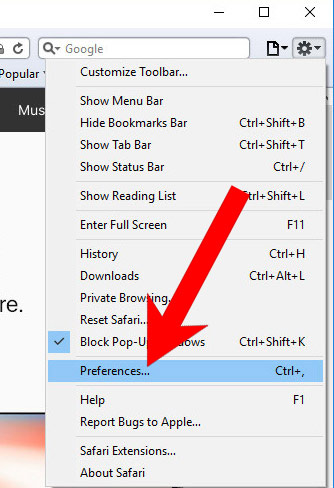
k) Remove security from Safari (for Mac)
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

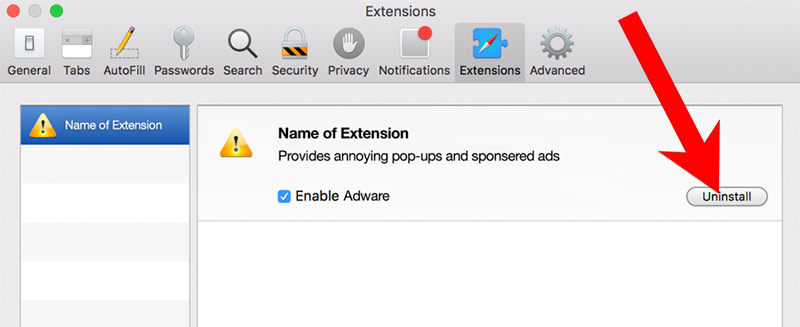
- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
l) Reset Safari
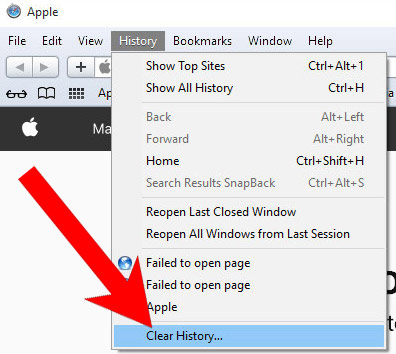
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
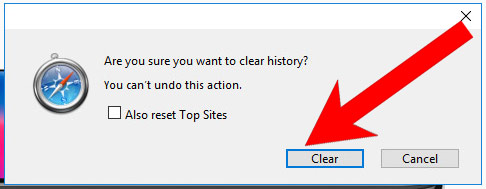
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

- Press on Safari at the top of the screen and select Preferences.

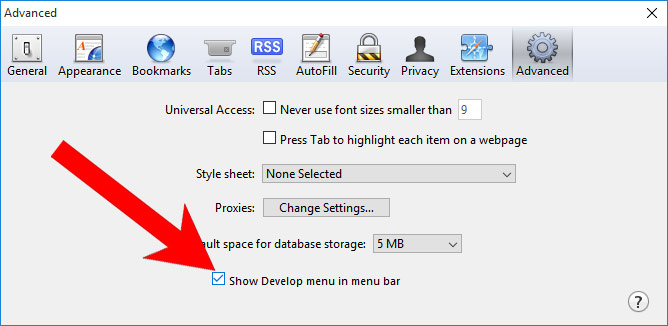
- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
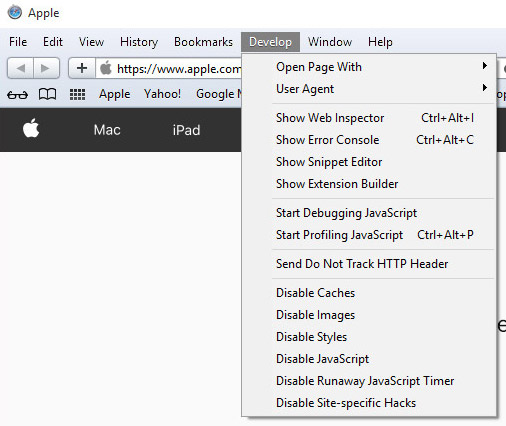
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.