What is Robust Optimizer?
Spam web alerts are another really widespread and really most commonly used scheme for exposing increasingly more people to risks of the Trojan Horse classification. In nearly all instances, the Robust Optimizer fraudulent software would be put into the spam e-mail as an adjoined catalog that the user is cheated onto running and/or getting on their machine. The minute the explained document receives started, the parasite begins and the system is no longer sheltered. However, as far as the likely signs are concerned, you might not realize anything if Robust Optimizer or another connected Trojan invades you. Some such malware have a tendency to act etc. aggressively and might bring about the device to undergo common freezes and BSOD crashes as well as accidental flaws.
Is Robust Optimizer a malware?
This may every so often draw the user’s attention to a probable Trojan Horse threat. There, regardless, are no assurances that this would take place in your case. In the majority situations, if a Trojan, like Robust Optimizer is presumed to remain secret and stay secretly for an prolonged amount of time, it would probably be capable of doing so. Still, as you’re here, reading this piece, you’ve no doubt observed some odd and abnormal process by Robust Optimizer in your computer which is what brought you here. In this case, we suggest you to track the next stages to eliminate Robust Optimizer if it greatly was able to infect your device.
Download Removal Toolto remove OptimizerRobust Optimizer Virus
We already mentioned some of the methods that viruses like Robust Optimizer or Robust Operator can get to you but you need to bear in mind that the full list of possible distribution channels used for the Robust Optimizer virus goes on and on and we can’t cover it all in such a short article. The critical thing is to always remain wary as long as via your browser – need to you detect any superficial item of details like a shady ad, site, page or note, exit it as quickly as possible and keep away from anything regarding it.
RobustOptimizer
RobustOptimizer, a notorious Trojan horse virus, employs deceptive distribution methods to infiltrate systems. It generally is distributed via nasty email attachments, utilities downloads from unreliable sources, or infected webpages. The second set up, RobustOptimizer or RobustOperator can carry out a variety of bad movements, containing spying, ransomware scattered, and statistics corruption. Its versatility and advanced abilities earn it a sizable safety jeopardize, alarming both operating system integrity and sensitive information security. To mitigate the probability posed by such PUP, computer users ought to exert warn when getting files or pressing on hyperlinks, periodically bring up to date their anti-spyware utility utility, and employ firewalls and other safety measures. Right away uninstalling any controversial files or software can assist block RobustOptimizer from performing its corrupt functions and defending the computer against further wreck.
Learn how to remove Optimizer from your computer
Step 1. Optimizer Removal from Windows
a) Windows 7/XP
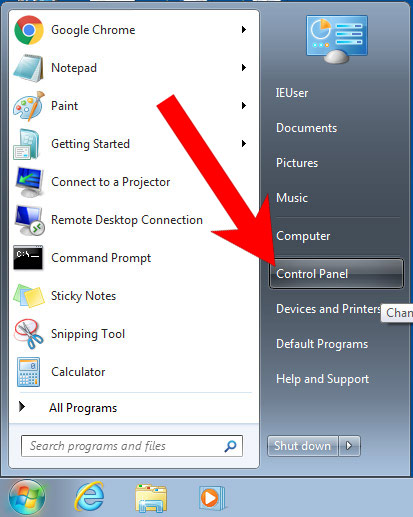
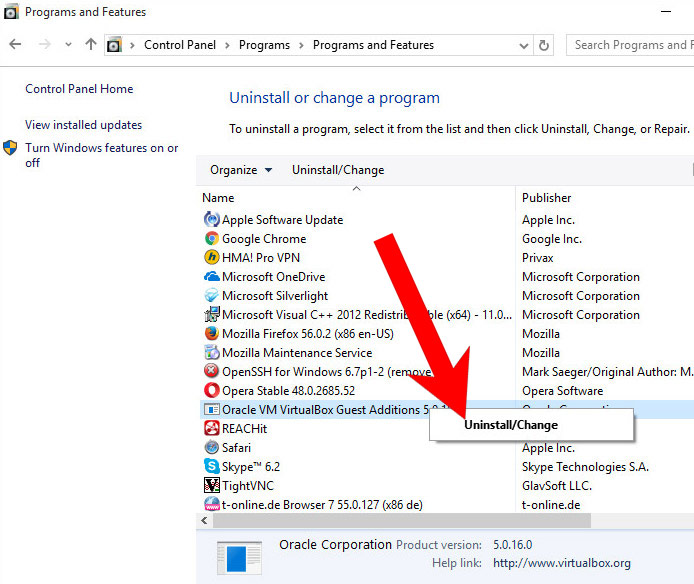
- Press on the Start icon.

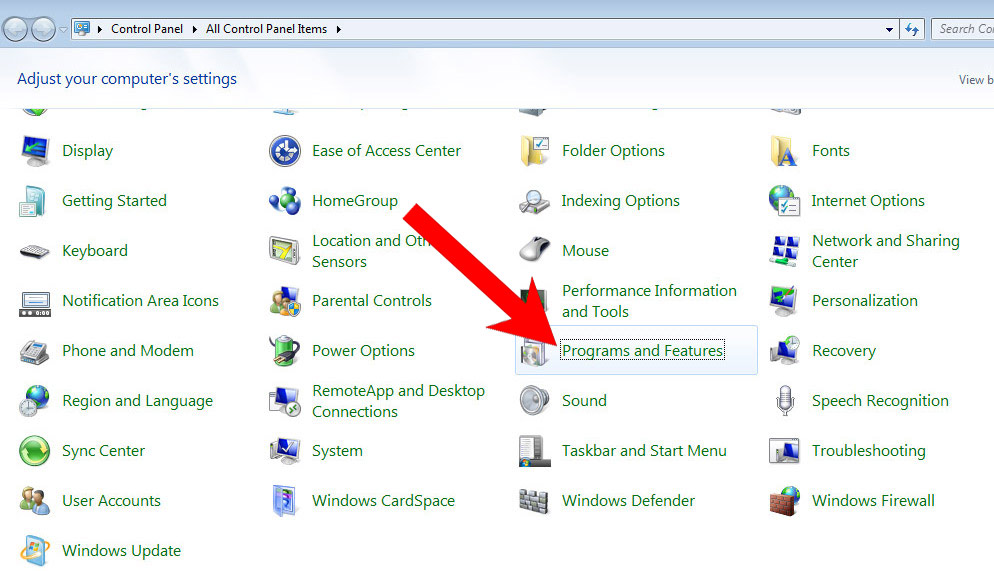
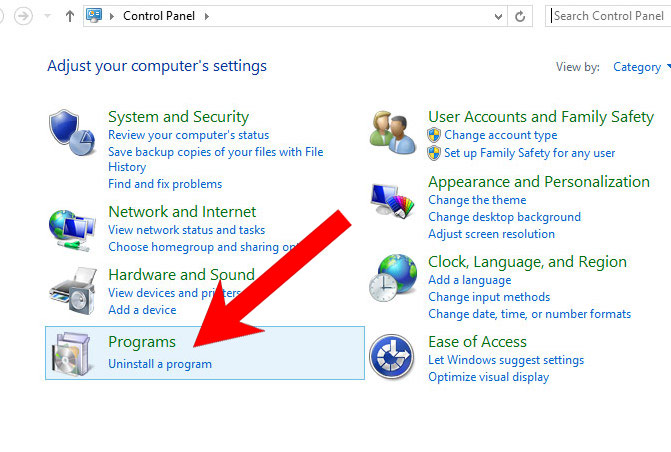
- Control Panel → Programs and Features.

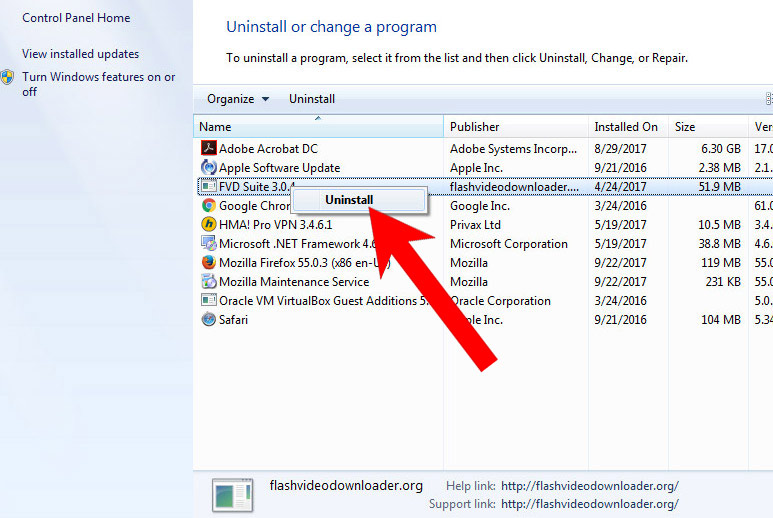
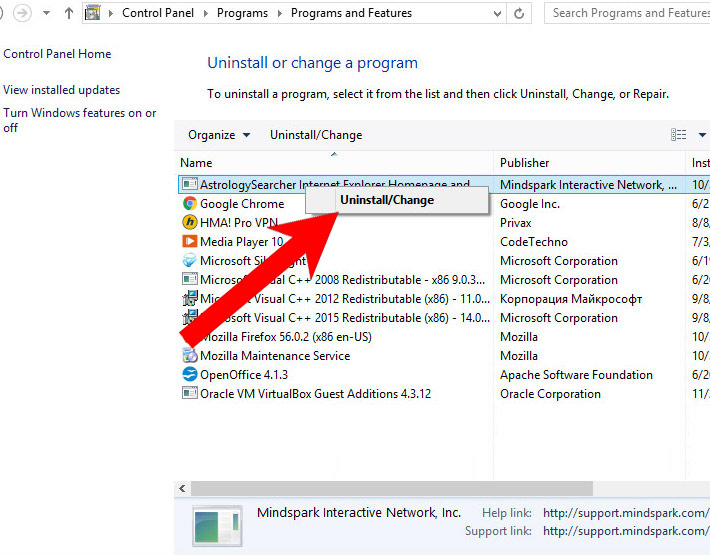
- Find the program you want to delete and press Uninstall.

b) Windows 8
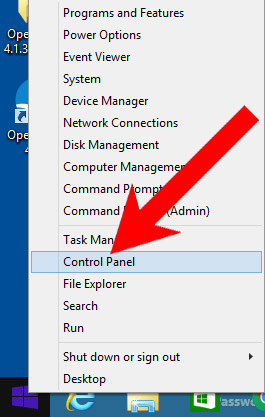
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

c) Windows 10
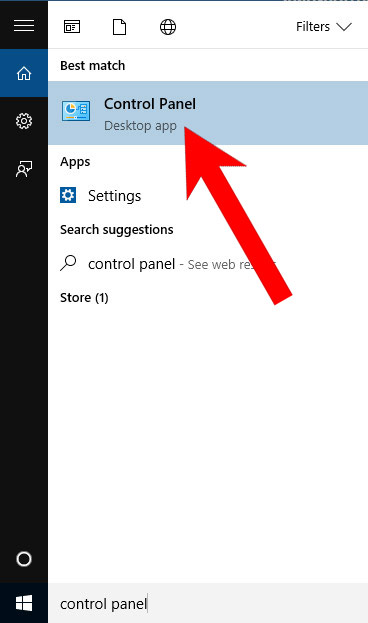
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

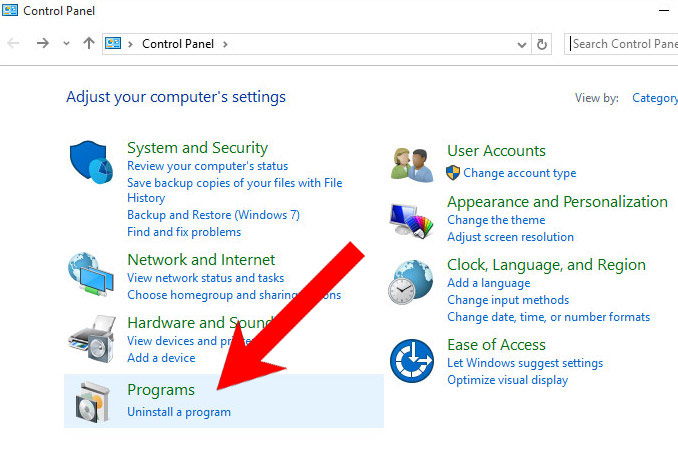
- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

d) Mac OS X
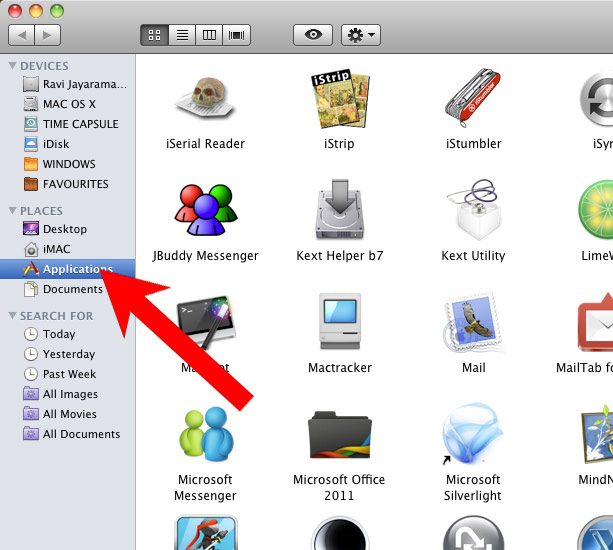
- Open Finder and press Applications.

- Check all suspicious programs you want to get rid of.
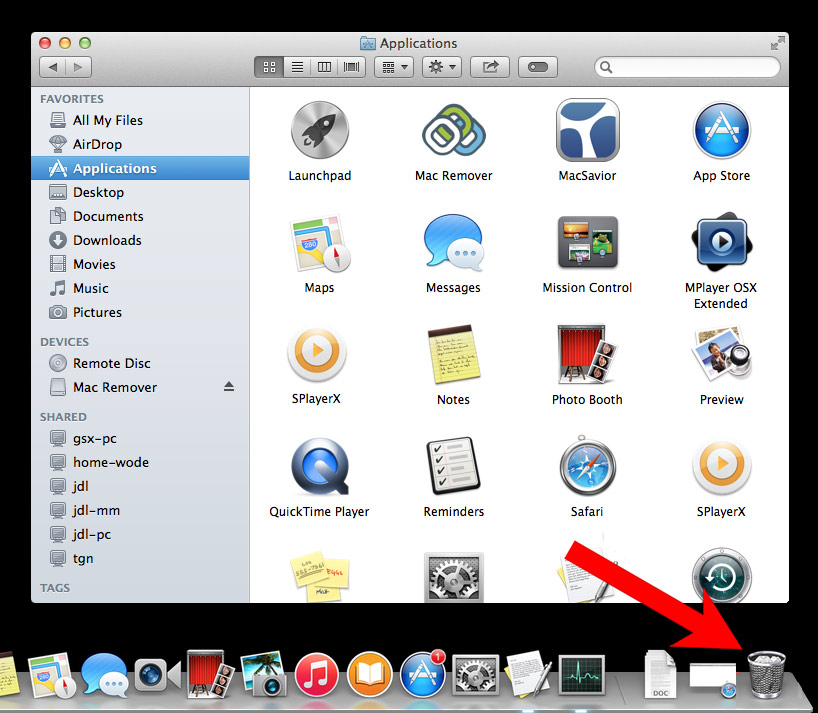
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete Optimizer from browsers
a) Remove Optimizer from Microsoft Edge
Reset Microsoft Edge (Method 1)
- Open Microsoft Edge.
- Press More located at the top right corner of the screen (the three dots).

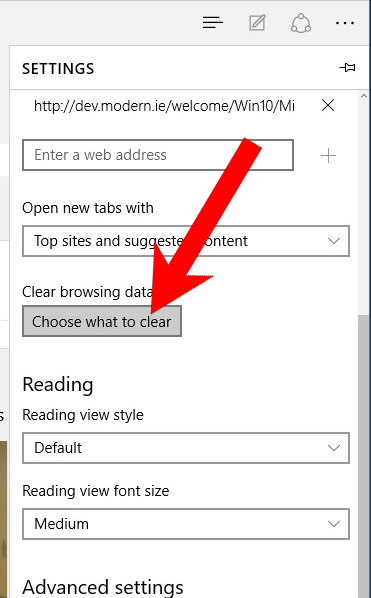
- Settings → Choose what to clear.

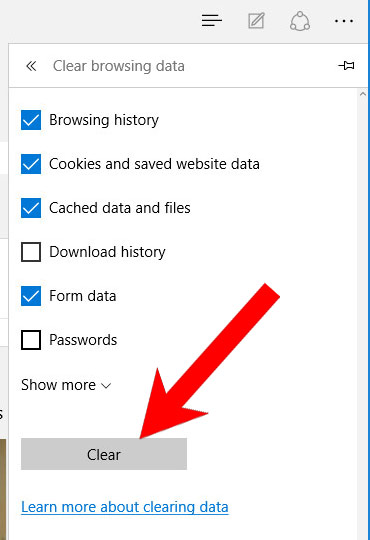
- Check the boxes of the items you want removed, and press Clear.

- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
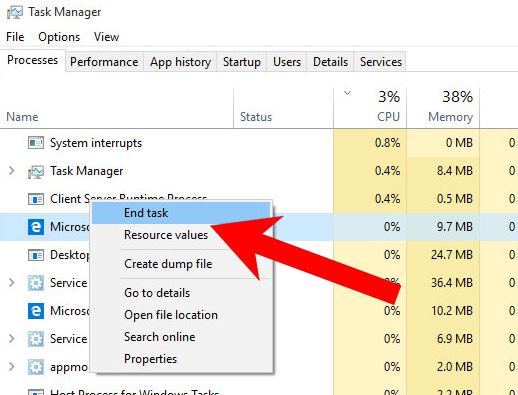
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
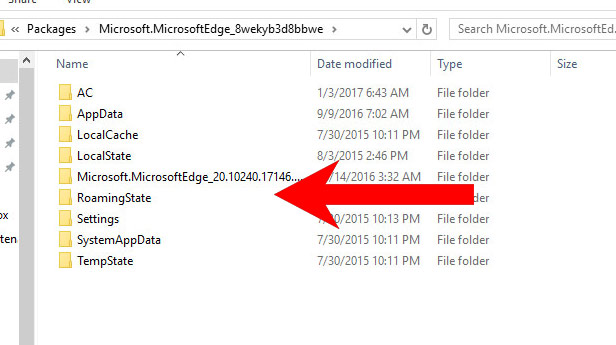
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

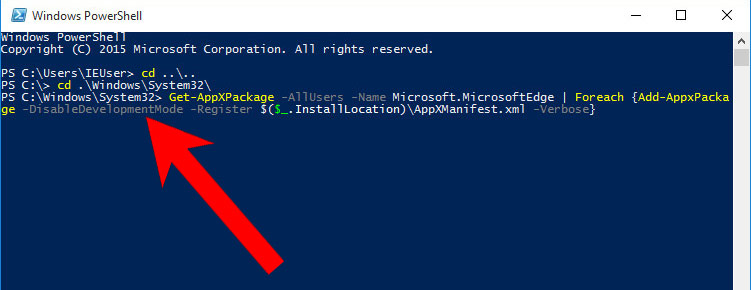
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
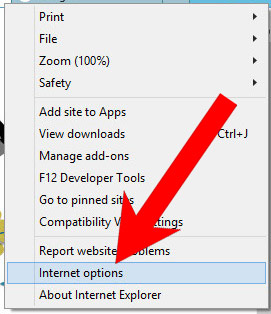
b) Remove Optimizer from Internet Explorer
- Open Internet Explorer and press on the Gear icon.

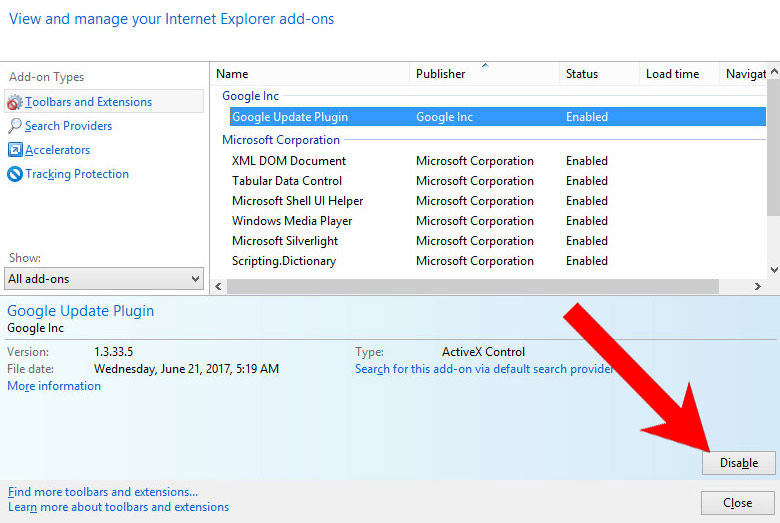
- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
c) Restore your homepage on Internet Explorer
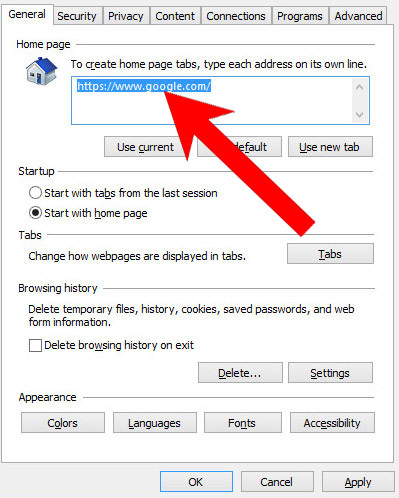
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
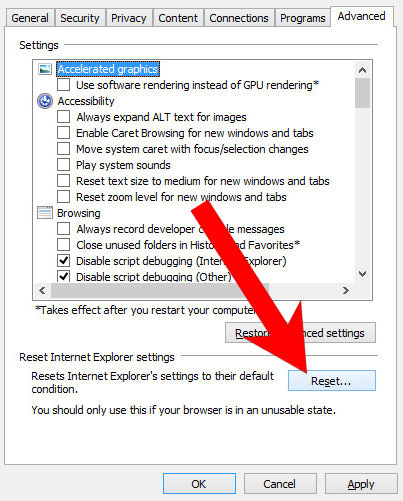
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

- At the bottom, you will see a Reset button. Press that.
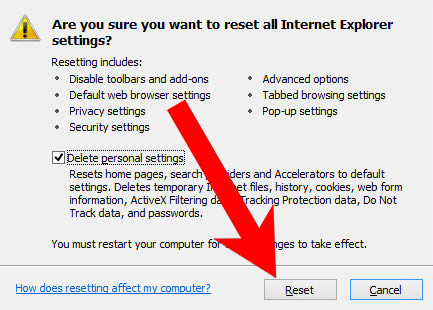
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
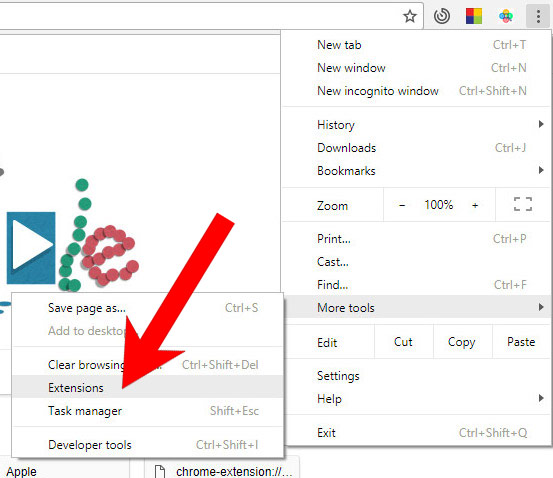
e) Remove Optimizer from Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
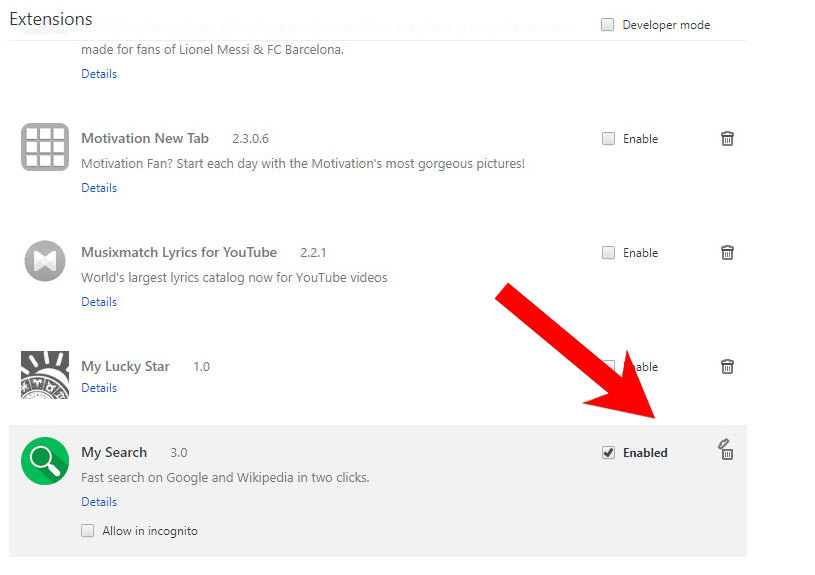
- Choose More tools and Extensions.

- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
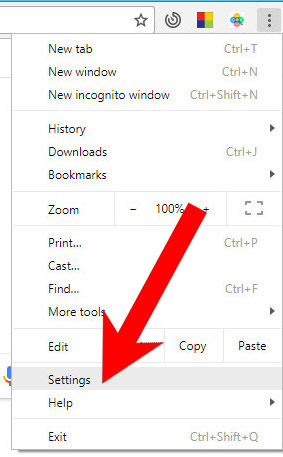
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

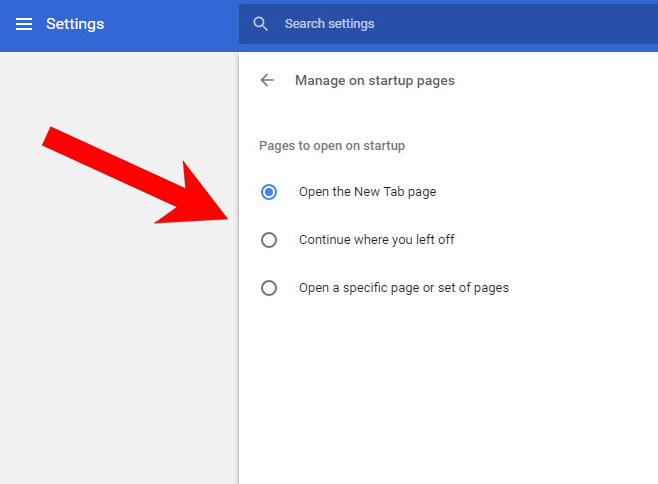
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

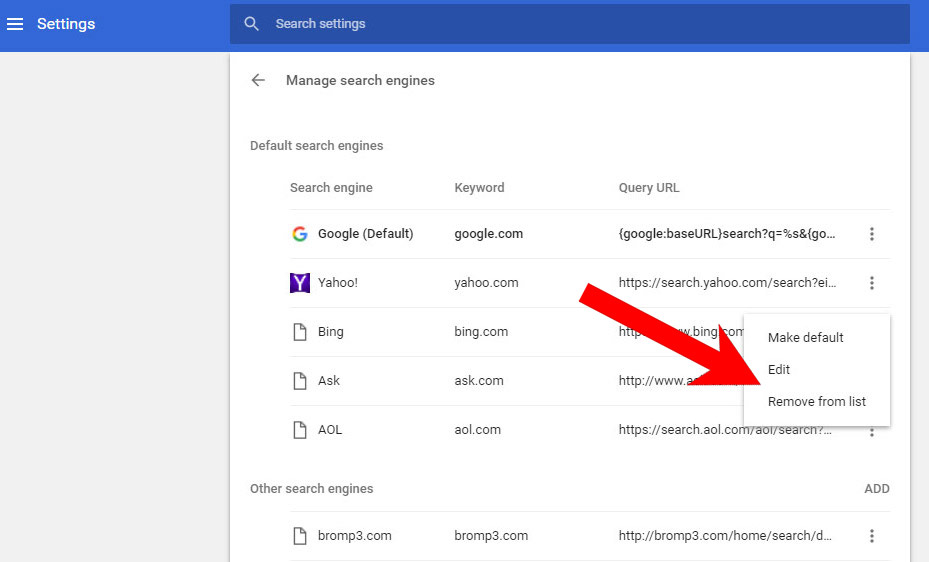
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
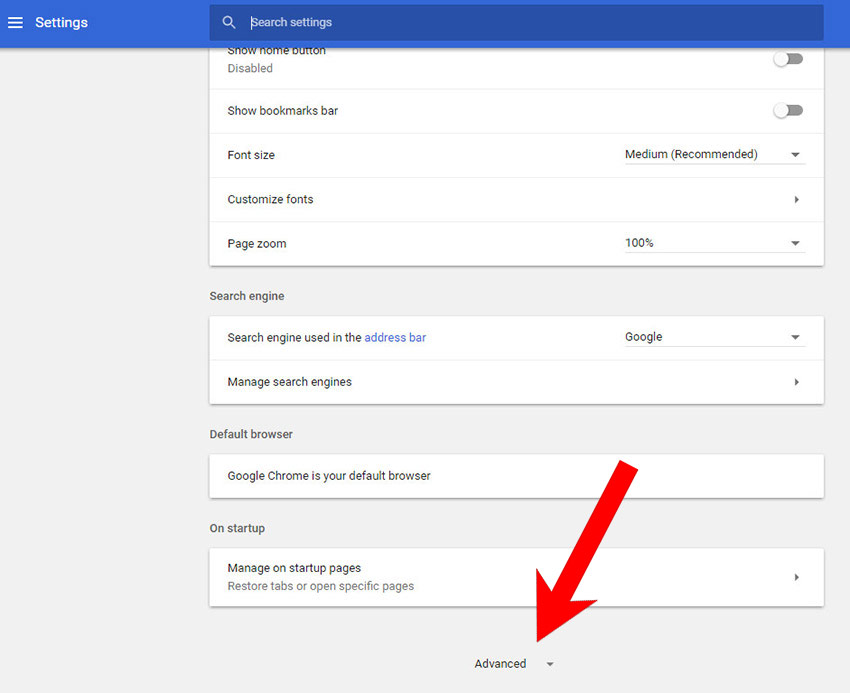
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

- Scroll down and press on Show advanced settings.

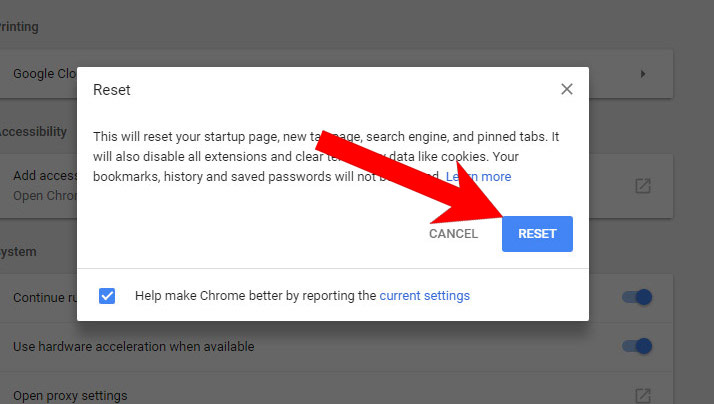
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
h) Remove Optimizer from Mozilla Firefox
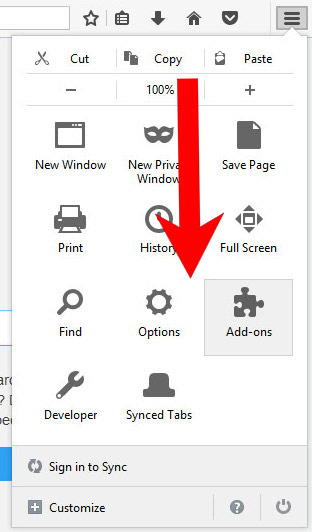
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
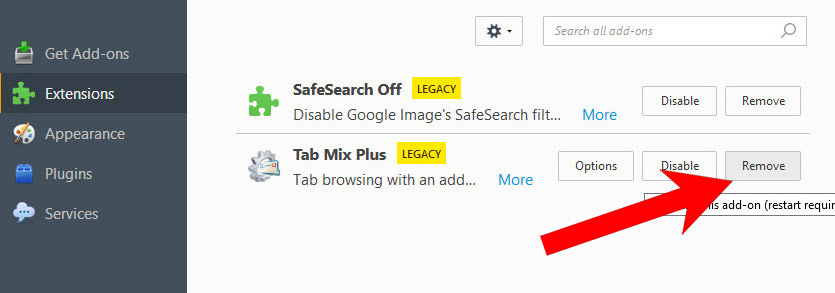
- Select Add-ons.

- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
i) Restore your homepage on Mozilla Firefox
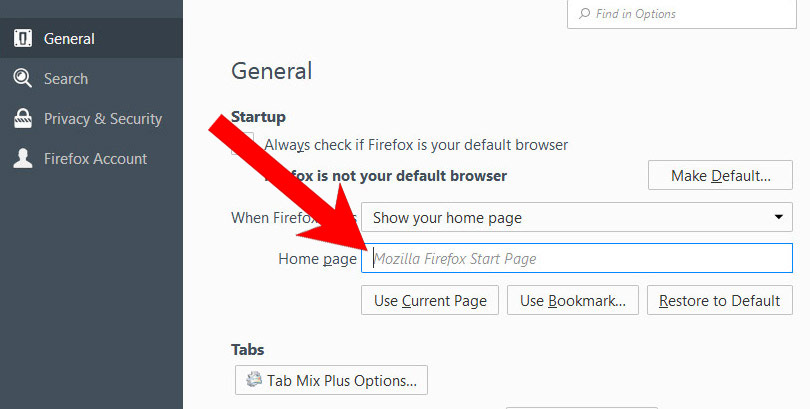
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
- Select Options.

- In General, click Restore to Default below the Home Page field.

j) Reset Mozilla Firefox
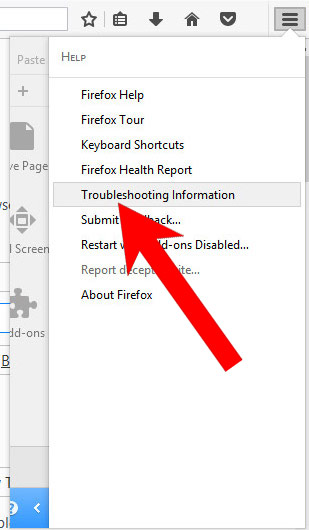
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

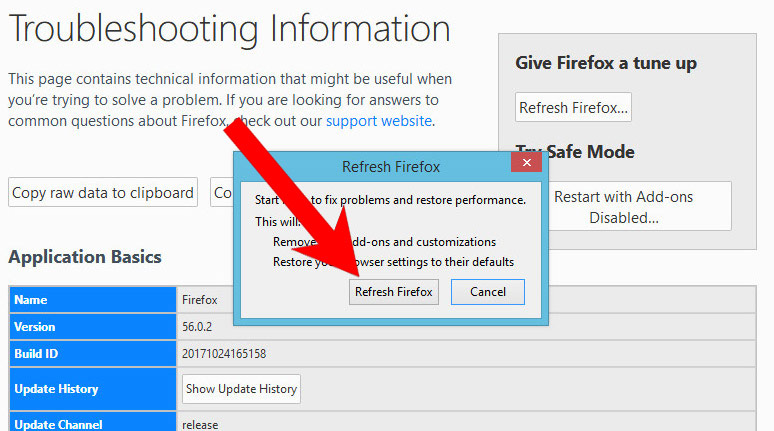
- Select the Refresh Firefox option.

k) Remove Optimizer from Safari (for Mac)
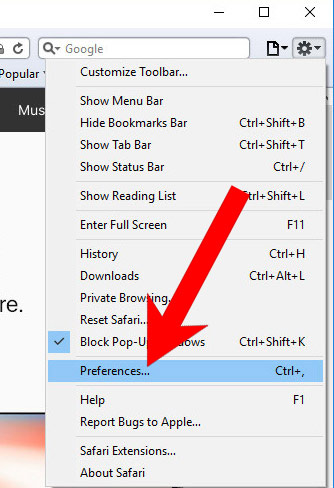
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

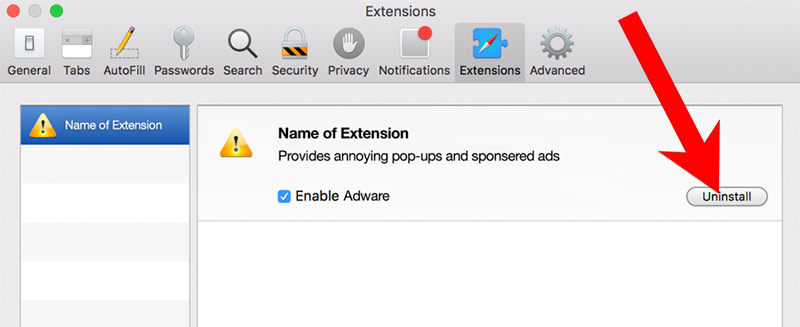
- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
l) Reset Safari
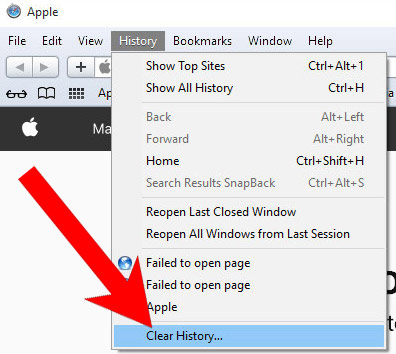
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
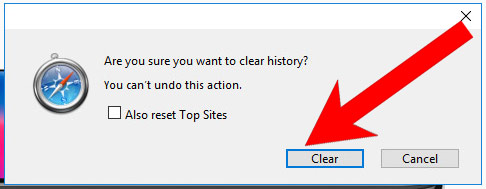
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

- Press on Safari at the top of the screen and select Preferences.

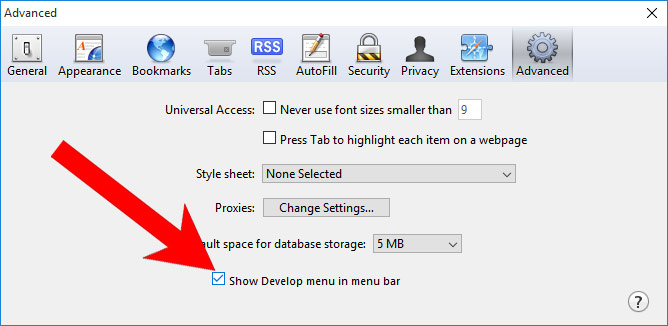
- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
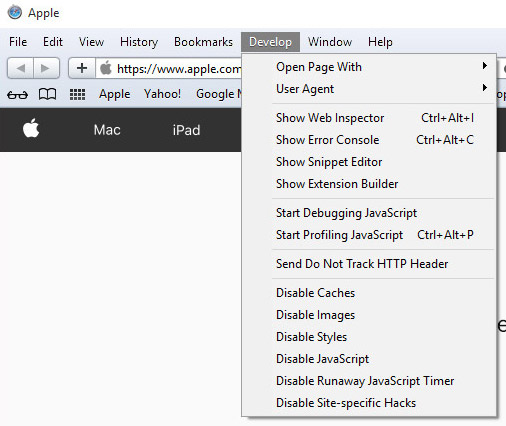
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.