Trojans for example this one are extremely hazardous elements of malicious software and can be capable of hurting the machine and the user’s virtual privacy in particular ways. Below, we shall momentarily category some of the feasible approaches in which a powerful malware danger for instance this one may be used by its criminal makers.
Some people complained to us that they have gotten an Email alongside the following text:
I am sorry to inform you that your system was jeopardized. I’ll note what led to all of this. I have employed a no Day vulnerability in packages with a exclusive code to invade your pc via a web page. This is a difficult program that requires fleeting capabilities that I have. It functions as a chain in packages with particularly made and exceptional code and that’s why these kinds of an breach can go secretly. You merely call for one not patched vulnerability to be contaminated, and sadly for you – it operates that effortless. You were not oriented specially, but just became any of the quite a number unfortunate users who got hacked that day. All of this occurred various month ago. So I’ve had time to gather information on you. I believe you have already found out what is ready to take place next. During that time, my applications was peacefully recording information about your activity, portals that you enter, analyzes you do, texts you transfer. There is etc. to it, but I have listed various reasons for you to realize how massive this is. For you to obviously figure out, my tools owned your camera and microphone as well and it was not possible for you to learn about it. It was just relating to right timing for me to get you privacy breached. I’ve been being uncertain ample and are determined that it’s time to put an end to this. So here is my advise. Let’s title this a “consulting fee” I must delete the media content I have been recording. Your privacy remains unharmed, if I get the payment. Otherwise, I shall reveal the the biggest part of adverse content to your contacts and post it to a public tube for perverts to browse. I merely care relating to collecting paid. My modest consulting fee is 1650 US Dollars redirected in Bitcoin. Exchange rate at the time of the send. You should better relay that number to this wallet: 1NGCsGqSdNEKpptQ4DKbJEva59cTSk369o The fee is non negotiable, to be redirected in 2 industry days. We use Bitcoin to secure my identity.
Download Removal Toolto remove inform
Probable utilizes of a Trojan Horse malicious software
Large-scale botnet actions – right off the bat, we ought to tell you relating to one of such the biggest number of known techniques in which Trojans are apt to accustom yourself. A botnet is fundamentally group of connected devices, which are all managed from a single place. In this case, that place would be the hacker’s server. Each operating system contaminated by the Trojan becomes an ingredient of this botnet, and the botnet itself is employed to perform functions that can’t be executed from a single pc. Such jobs could be the mass scattered of spam notifications to increasingly more people over the net, or the mining of cryptocurrency revenue. Sometimes, botnets might also be utilized for denial of service invades – this is ultimately when a big amount of devices begin visiting a particular website with the intention to crash its servers via utter portion of visits. If ample pcs are in the botnet, the servers of the oriented website can’t manage that quite a lot of unforeseen visits, and would one day crash.
Sensitive tailing processes – Trojans like “I am sorry to inform you”, The incredible detect, Bokang Speedup must also be especially potent tailing utilities. They can observe the user’s keystrokes via keylogging procedures, and they can capture images from what’s taking place on the user’s screen. This generally authorizes the criminals behind the Trojan to retain extremely personal data like the user’s financial information, or their passwords and usernames for various pages. Needless to say, such information, when situated onto the bogus hands, might lead to some extremely nasty and malicious outcomes.
Backdoor movements – the third instance of how a Trojan could be employed is when these infections are employed for creeping other malicious software into a pc that has already been infected. Ransomware cryptoviruses are one of such a majority of regular examples of issues that get backdoored onto their victim’s computers via the assistance of Trojans. Of course, there relatively a lot any other type of malicious software can be backdoored together with a Trojan as well.
Download Removal Toolto remove informTaking into mind that those are merely three of the quite a lot of potential approaches a Trojan might be used, and in addition that malicious software like “I am sorry to inform you” can be adverse for the user, and their device, you are recommended to now investigate the instructions, and act in accordance with our guidelines that are there to erase the unpleasant “I am sorry to inform you” from your system.
Learn how to remove inform from your computer
Step 1. inform Removal from Windows
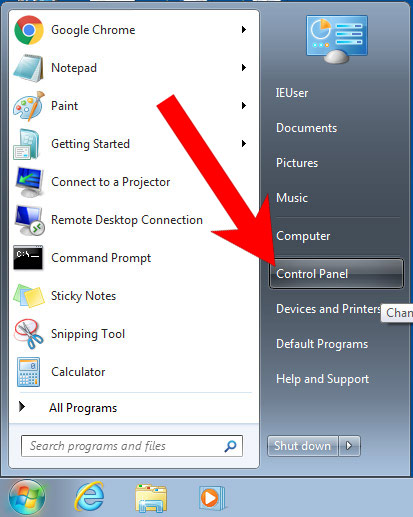
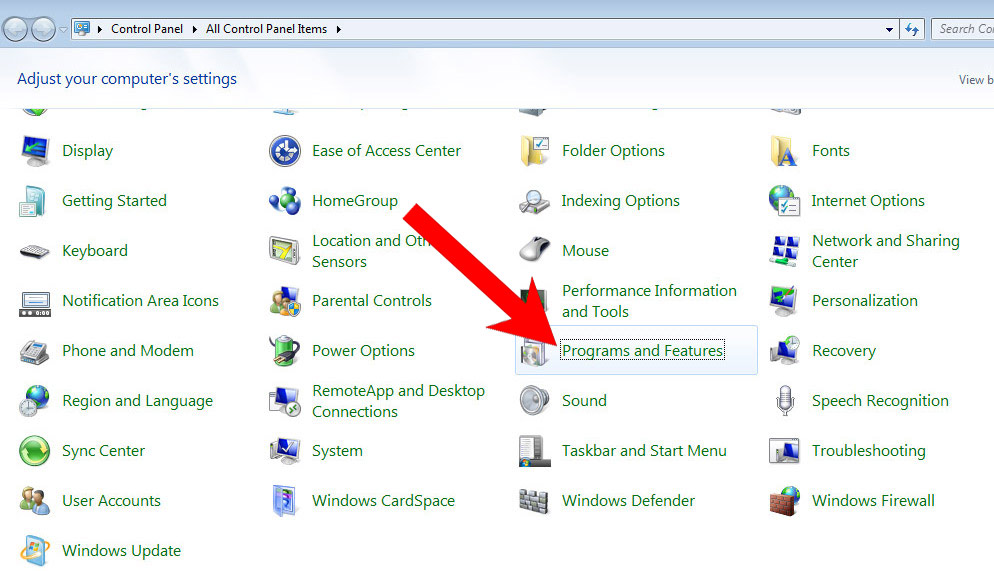
a) Windows 7/XP
- Press on the Start icon.

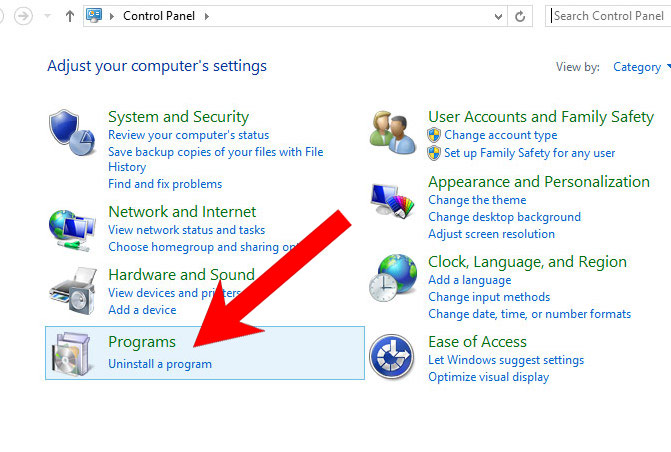
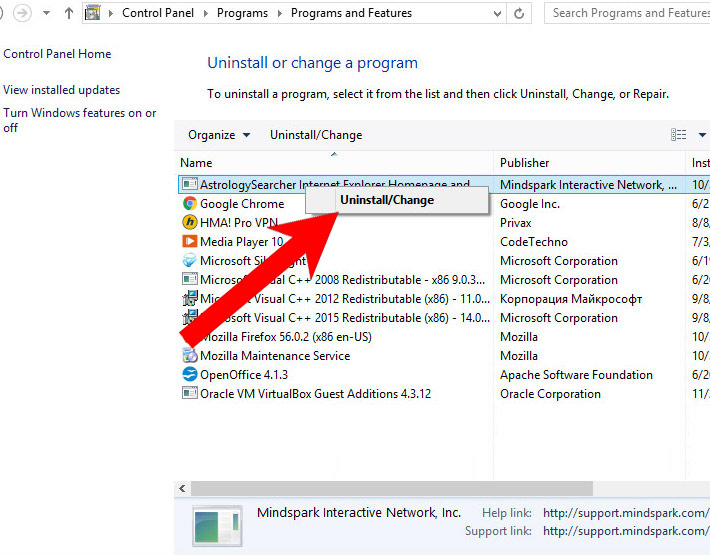
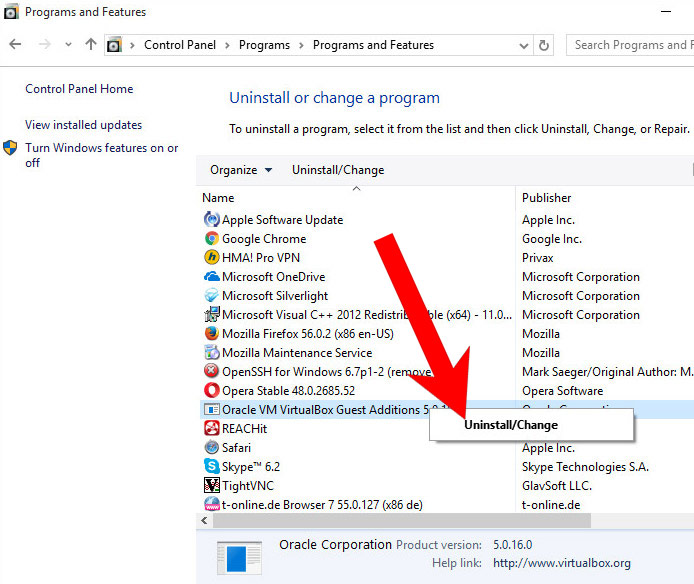
- Control Panel → Programs and Features.

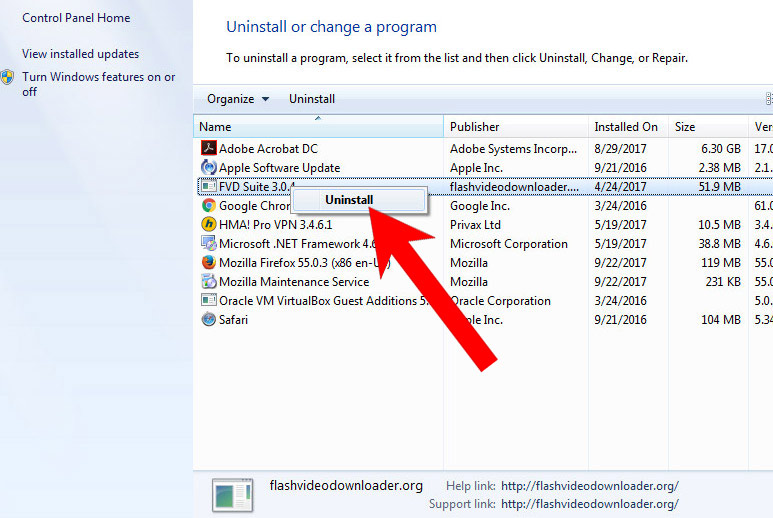
- Find the program you want to delete and press Uninstall.

b) Windows 8
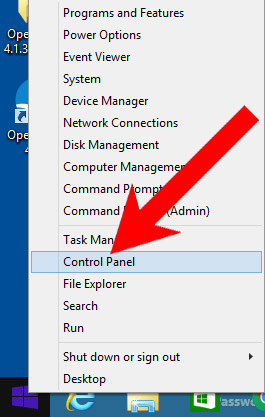
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

c) Windows 10
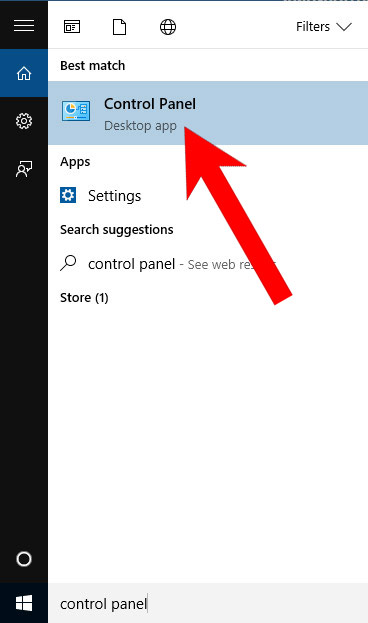
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

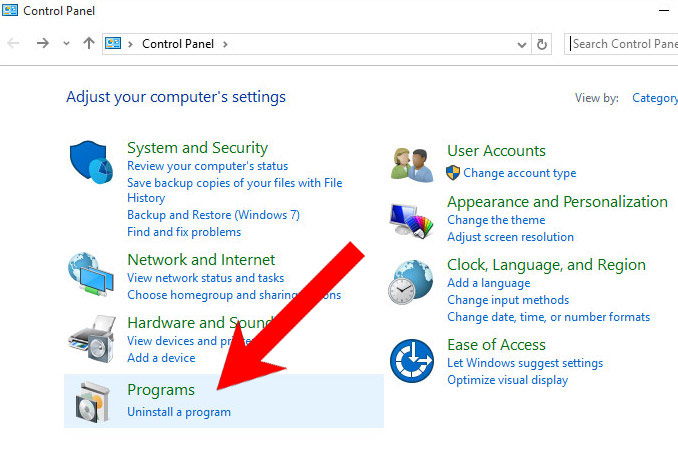
- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

d) Mac OS X
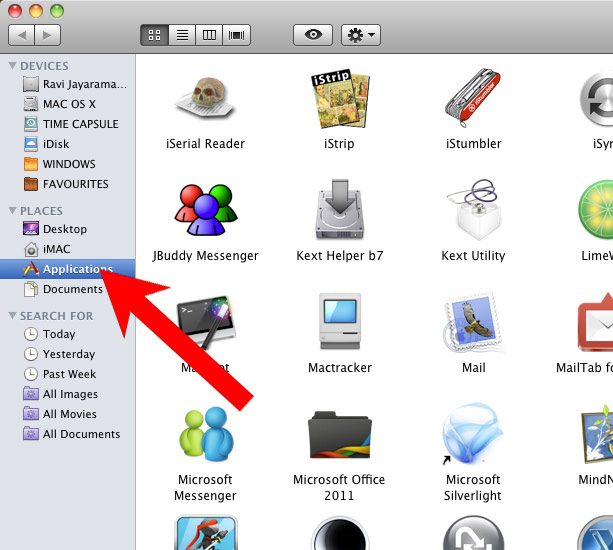
- Open Finder and press Applications.

- Check all suspicious programs you want to get rid of.
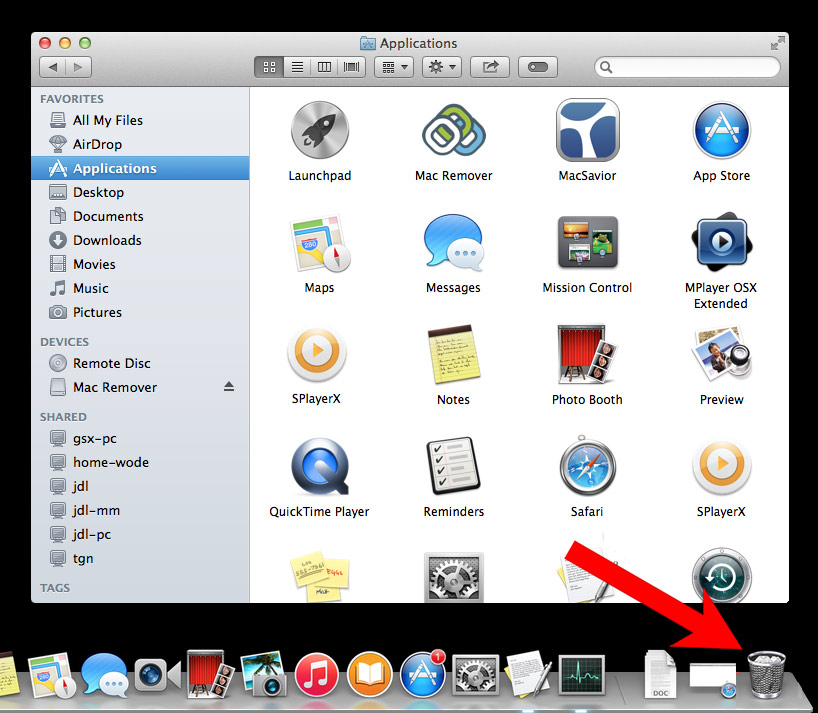
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete inform from browsers
a) Remove inform from Microsoft Edge
Reset Microsoft Edge (Method 1)
- Open Microsoft Edge.
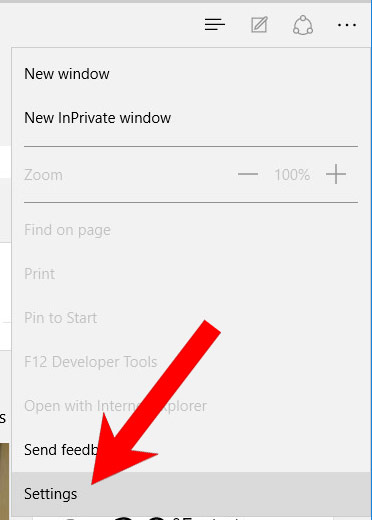
- Press More located at the top right corner of the screen (the three dots).

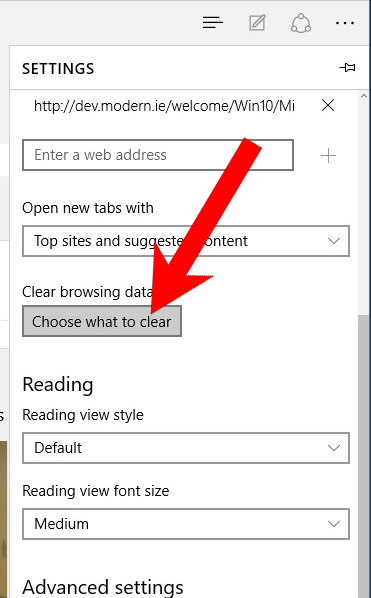
- Settings → Choose what to clear.

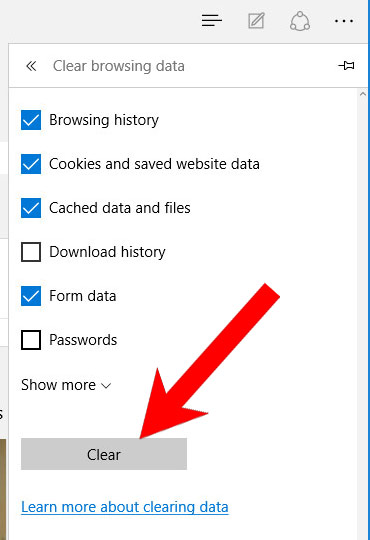
- Check the boxes of the items you want removed, and press Clear.

- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
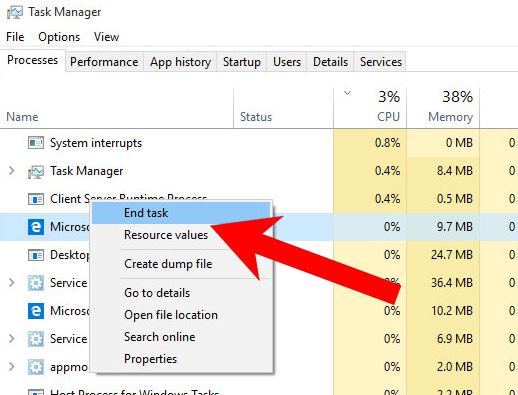
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
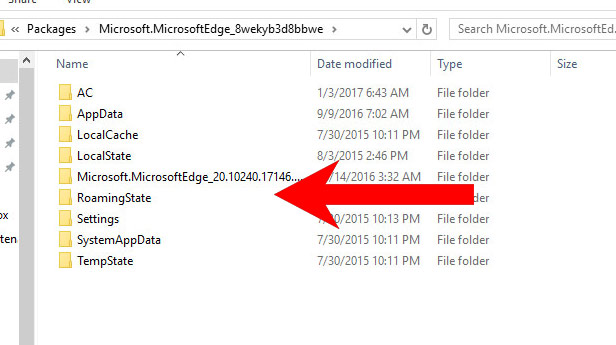
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

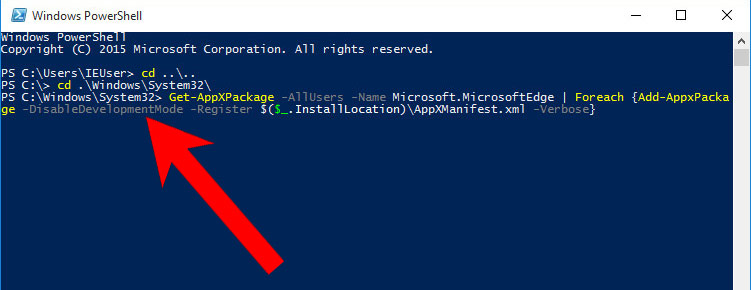
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
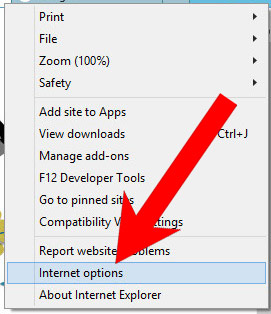
b) Remove inform from Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
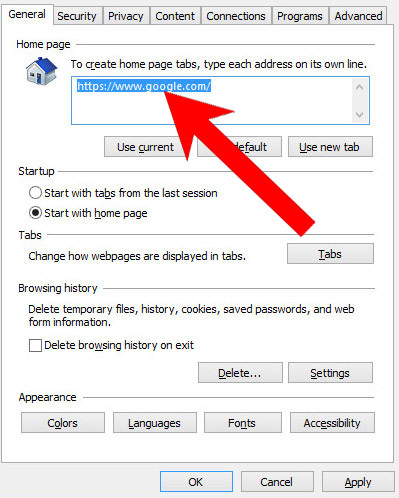
c) Restore your homepage on Internet Explorer
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
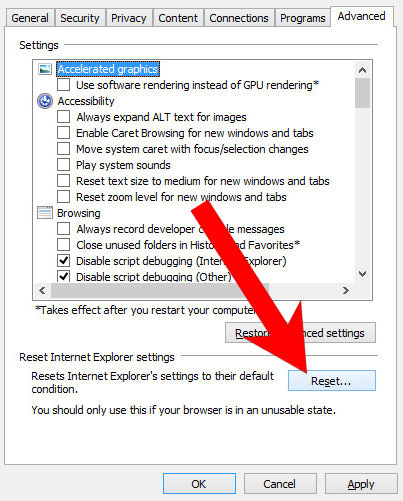
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

- At the bottom, you will see a Reset button. Press that.
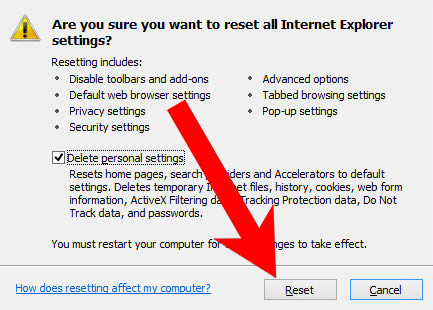
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
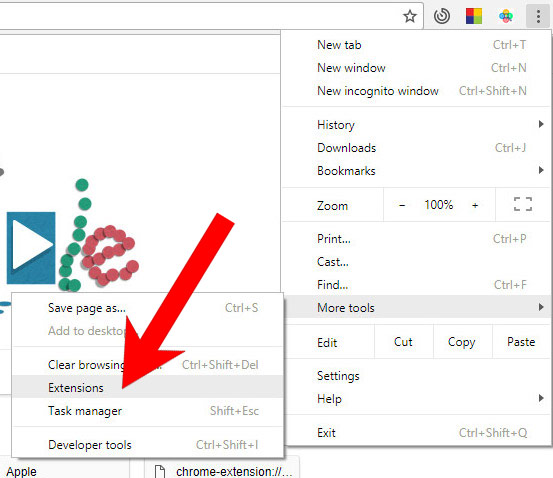
e) Remove inform from Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose More tools and Extensions.

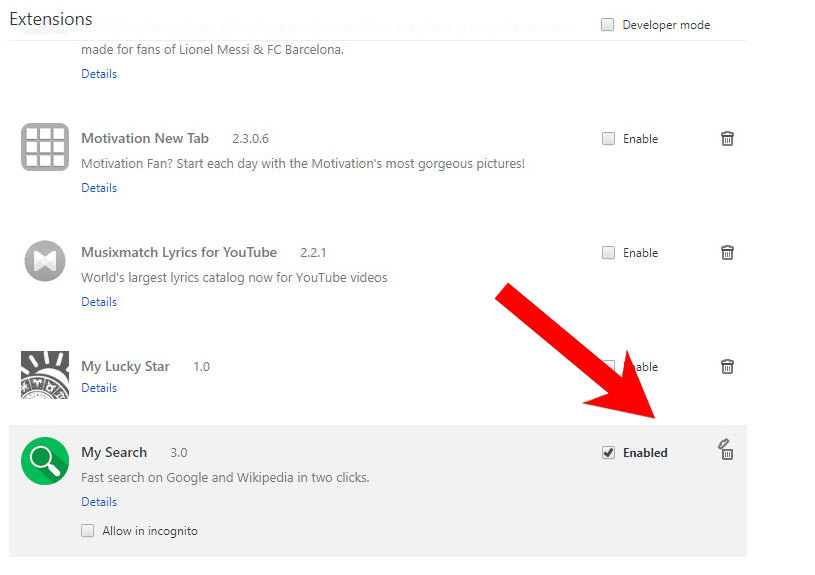
- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
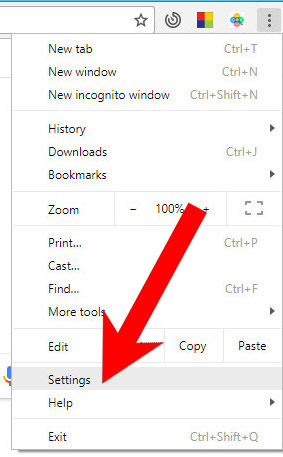
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

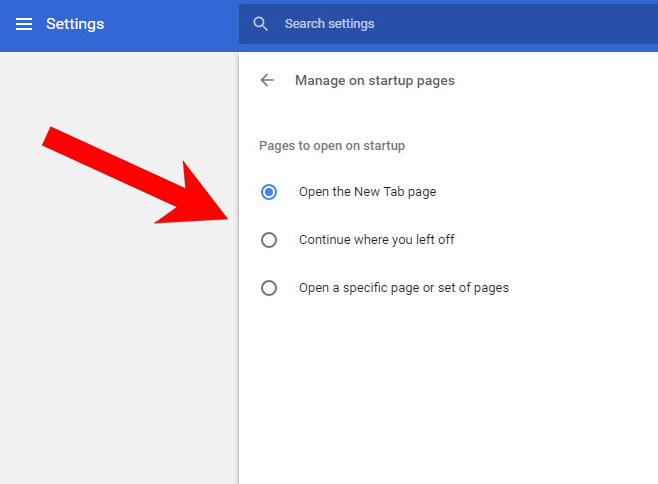
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

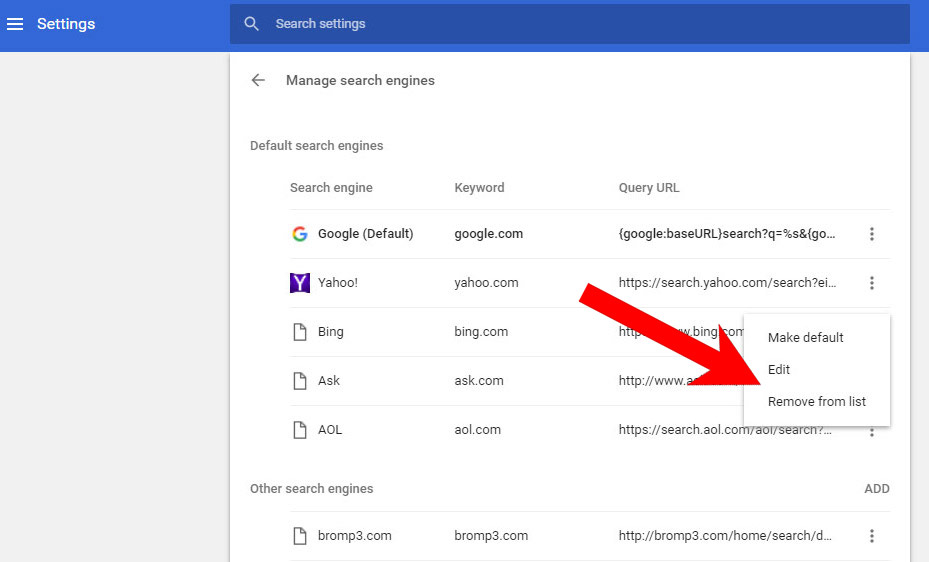
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
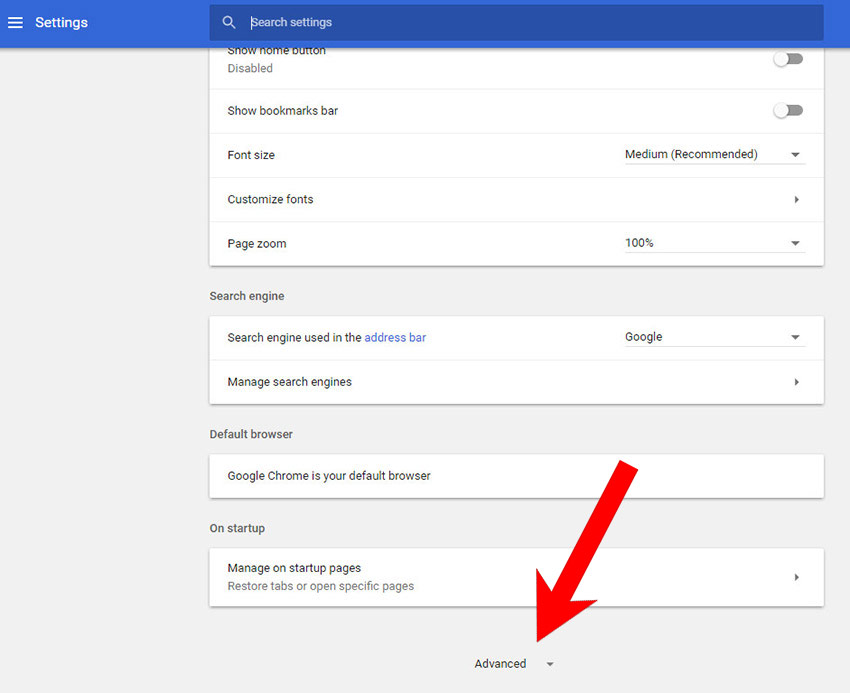
- Choose Settings.

- Scroll down and press on Show advanced settings.

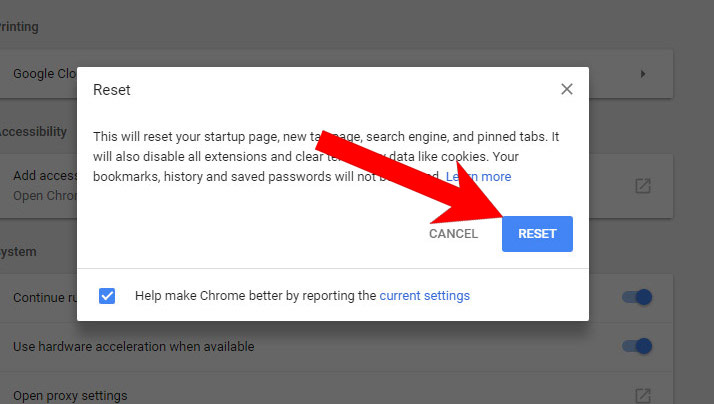
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
h) Remove inform from Mozilla Firefox
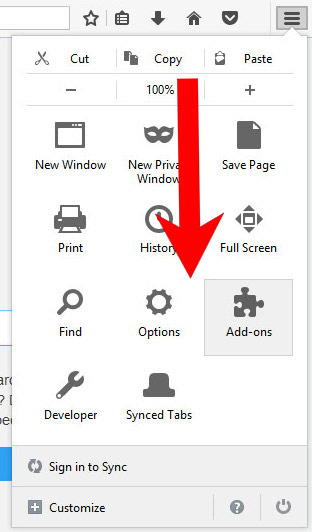
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
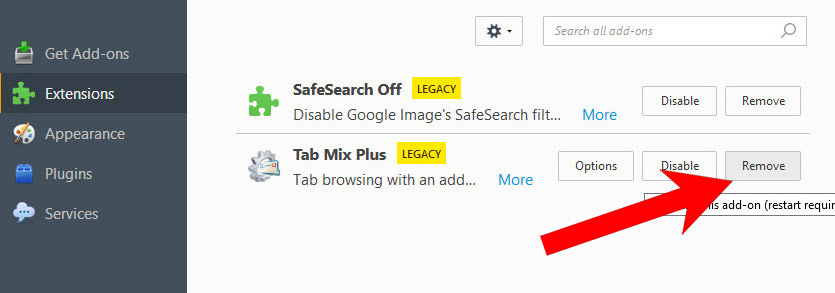
- Select Add-ons.

- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
i) Restore your homepage on Mozilla Firefox
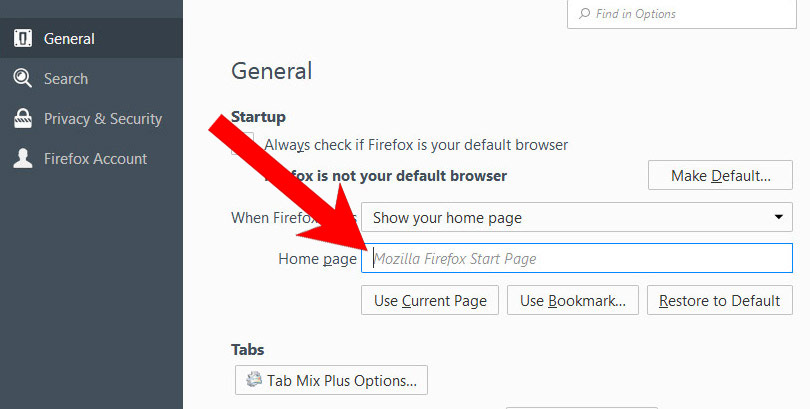
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
- Select Options.

- In General, click Restore to Default below the Home Page field.

j) Reset Mozilla Firefox
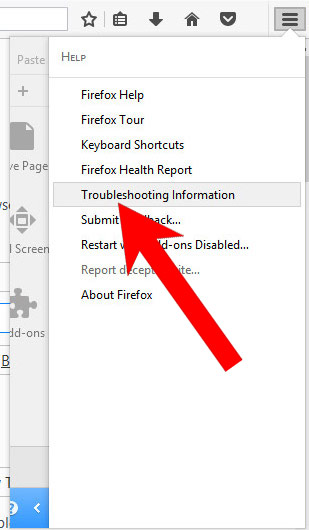
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

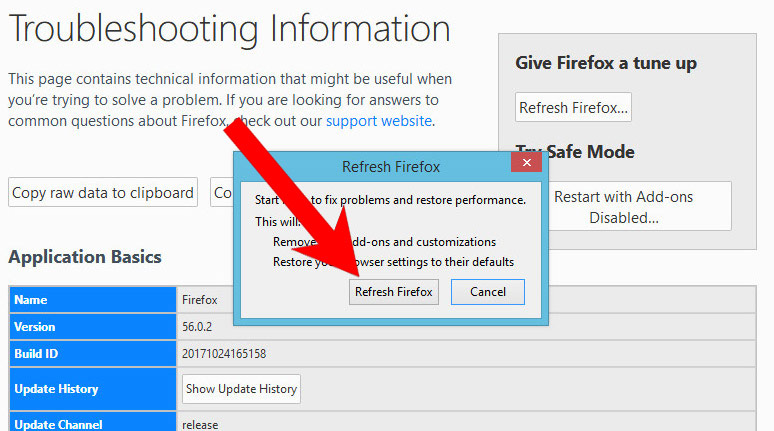
- Select the Refresh Firefox option.

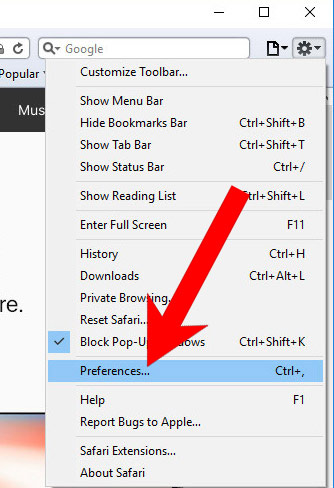
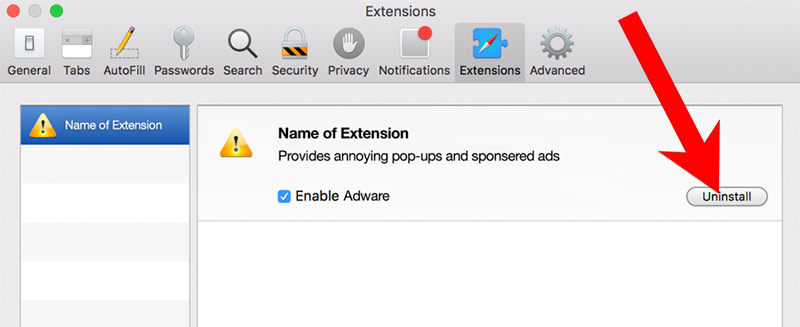
k) Remove inform from Safari (for Mac)
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
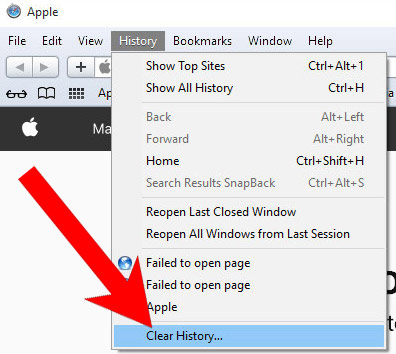
l) Reset Safari
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
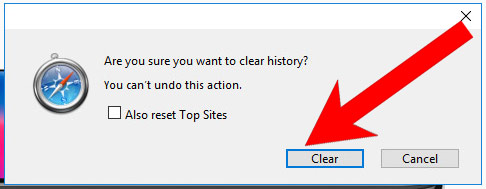
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

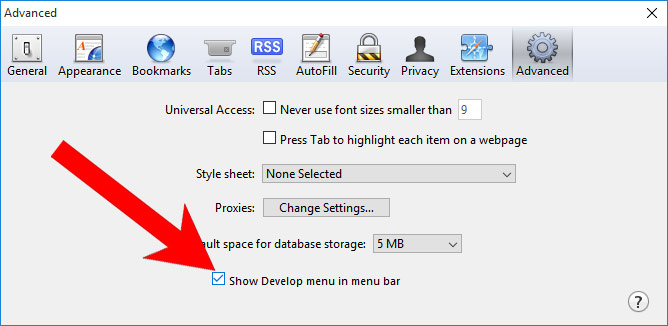
- Press on Safari at the top of the screen and select Preferences.

- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
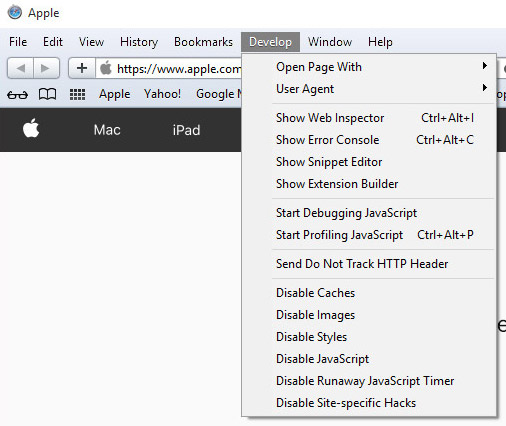
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.