What is “I Managed To Install A Spyware”?
The “I Managed To Install A malware” hoax includes fraudsters sending disturbing emails stating to have entered your pc with malware. These kinds of emails generally allege that the cyber criminal has accumulated compromising video footage by entering your webcam and inquiries payment, generally in Bitcoin, to overlook the spread of the footage. It’s essential to understand that these kinds of states are unfounded, developed to take advantage of fear for monetary get.
Some of our people reported a “I Managed To Install A Spyware” email scam that they have gotten, in packages with the following notification:
Hello, my perverted friend,
Unfortunately, the fact that our paths have crossed doesn’t mean anything good for you.
I have some type of useful news and bad news.
I’ll beginning alongside the bad news.Although you were browsing porn web pages, I Managed To Install A malware through your browser.
Download Removal Toolto remove I Managed To Install A
It has earned entry to your webcam, your browser history, and all your pcs, not just your computer system.This separately wouldn’t be a risk if merely I wasn’t specifically curious about your enjoy of the greatly suspicious genre of pornography.
You recognize what I suggest. I saved a copy of your webcam and screen recordings as you appreciate jerking off to these kinds of videos.
The video on the dropped movies a logging of your screen together with the clip, in spite of the fact that the one on the right presents you with in concrete time.There is no need to feel sorry for yourself or blame me for the situation – the fault here is yours alone because if you gaze into a dark abyss for too long,
this darkness eventually will come knocking at your door.
You should better even be grateful to fate that I’m the sole one who detected your unhealthy obsession and not your friends, group and fellow workers.And this is where I get to the essence of my notification – I can promptly organize this. Everyone you know, love and cherish,
everyone you’ve spent years building your reputation as a respectable and honorable person in front of,
will get a copy of the video of you self-pleasing yourself while watching these controversial videos.Each of your email and messengers contacts shall get these kinds of videos simultaneously.
You will be forced little dropped but to move to a different city, and maybe even another country, to eliminate the sick guy monitor that might be operating behind you.
However, this additionally may not help. As they say, the computer network remembers all.
There’s a high chance you shall ought to deal with the results for the rest of your life, regardless of your attempt to cleanse your title.Now, as I vowed, the desirable news.
I have a win-win cure for both you and me.
You recover your old free-of-charge life and I produce a trivial revenue.You should transfer $1340 to my Bitcoin wallet: 17aB5wwDJ6EGdz(edited)
If you are unfamiliar with cryptocurrency, it’s simple.
Download Removal Toolto remove I Managed To Install A
Category “crypto exchange” onto the search tools and select the alternative that matches you.
You can think of me as a kind of your life coach because if I didn’t show up in your life,
you would continue to lead the same destructive lifestyle as before.
So I rather did you a select, and selects are never free-of-charge.I need to warn you not to execute something stupid that you could do because of your inexperience, for instance:
; Contacting law enforcement.
I’m untraceable anyway, because cryptocurrencies are anonymous and I have access to all your devices,
so as soon as I notice you trying to do something like this, the compromising clips will be made public.
; Negotiating in packages with me by responding to this letter. My inquiries are ultimatums.
I produced this letter via your own email client, for that reason it is not possible to contact me!
; Resetting, reinstalling your computer or demolishing your pcs won’t assistance you.
I repeat: I acquire entry to them and if I find such process, hasta la vista, baby.I desire you all the perfect and specially delete your “interesting” tendencies.
You will then not merely no longer face users like me, but you shall additionally have a chance to come to a new quality level in your self-development.Bye!
P.S. Pretty friendly suggestions: henceforth, take what you do on the internet etc. severely.
Key Characteristics of the Scam:
- Impersonation: Scammers send emails that appear to be from your own email domain, creating a sense of alarm and authenticity.
- Jeopardizing Content: The emails include dangers of disclosing supposed recordings of sensitive minutes unless a fine is paid.
- Request for Bitcoin: fees are requested in Bitcoin, manipulating the cryptocurrency’s anonymity.
Infiltration ploys: Myth vs. Reality
Many victims wonder how scammers could have possibly accessed their webcams. In truth, these kinds of states are generally completely bogus. The schemes used by schemers involve:
- Psychological Manipulation: The hoax counts on inducing worry, expecting that the fear of public embarrassment shall cancel out wise recommendation.
- Mass Email Campaigns: Sc
ammers send out thousands of emails, banking on the probability that some recipients will be tricked into believing the threat is real, despite not having any actual spyware or access to webcams.
- Spoofing ways: they could use email spoofing ways to create it seem that the email is coming from your own address, manipulating technical loopholes in email protocols to deceitful the sender’s identity.
How to Avoid Falling Victim to the “I Managed To Install A Spyware” Scam
Protecting yourself from such scams requires vigilance and adherence to best practices in digital hygiene:
- Don’t react: interacting with the cyber criminals, even to decline or bogus them, only shows that your email address is functioning. Evading the email is the safest reaction.
- Improve safeguarding Measures: Use strong, one-of-a-kind passwords for all of your accounts and permit two-item authentication any place probable.
- Bring up to date periodically: Keep your system and anti-malware utility utility up-to-date to safeguard against tangible malware dangers.
- Pretext Your Webcam: When not in use, physically pretext your webcam to block any chances of prohibited collecting.
- Educate on your own: Awareness of the schemes used by schemers can quite significantly lower the chances of falling pray to such deceits.
Blocking Sextortion Scam Websites and Emails
To further safeguard against sextortion scams, you can take proactive measures to block scam websites and emails:
- Use Email Filters: the biggest part of email functions advise techniques to filter out spam or dubious emails. Use those programs to prevent emails including particular keywords relating to sextortion deceits.
- Utilize Browser protection plugins: set up plugins that prevent notorious deception portals and caution you connected to fishy connections.
- Article and prevent cyber criminals: if you get a sextortion email, article it as spam or scam inside your email platform. This not merely aids optimize the platform’s scanning algorithms but on top of that helps in shielding others.
- Put into action Web scanning Solutions: contemplate through web scanning solutions that may deny access to well-known malicious web pages. These kinds of solutions are generally an ingredient of thorough a security application parcels.
- Remain notified: tail decent cybersecurity news sources to remain up-to-date on new hoaxes and risks. Consent is power in the digital realm.
Conclusion: Empowerment Against Digital Threats
The “I Managed To Install A Spyware” and Hello My Perverted Friend Email sextortion scam, while frightening, is a bluff designed to exploit human vulnerabilities. Perception the scam’s roots and through robust digital hygiene practices can secure you from such risks. Remember, the capacity to remain sheltered on the internet generally rests in your hands via cautioned, careful participation in bundles with digital ways. By employing the advisable preventative measures and adopting a cautious mindset towards unwelcome emails, you are able to navigate the internet with assurance, realizing you’re well-sheltered against the tricks of digital extortionists.
Learn how to remove I Managed To Install A from your computer
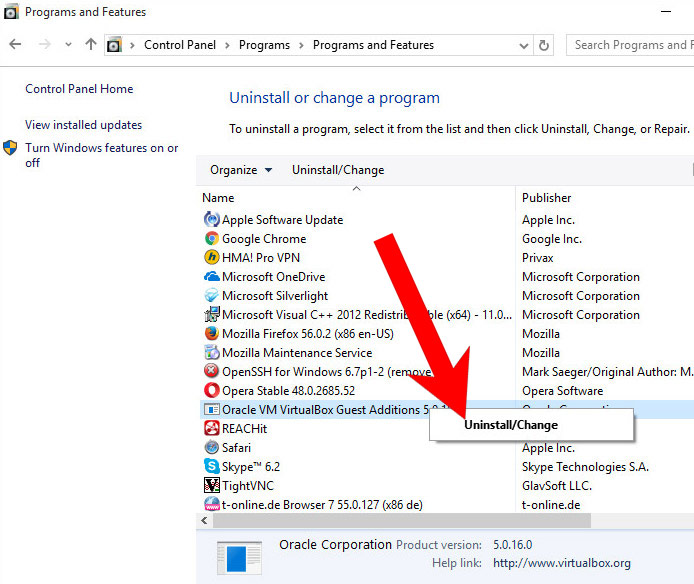
- Step 1. I Managed To Install A Removal from Windows
- Step 2. Delete I Managed To Install A from browsers
Step 1. I Managed To Install A Removal from Windows
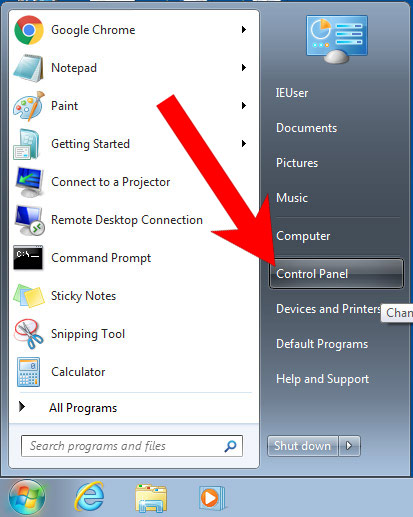
a) Windows 7/XP
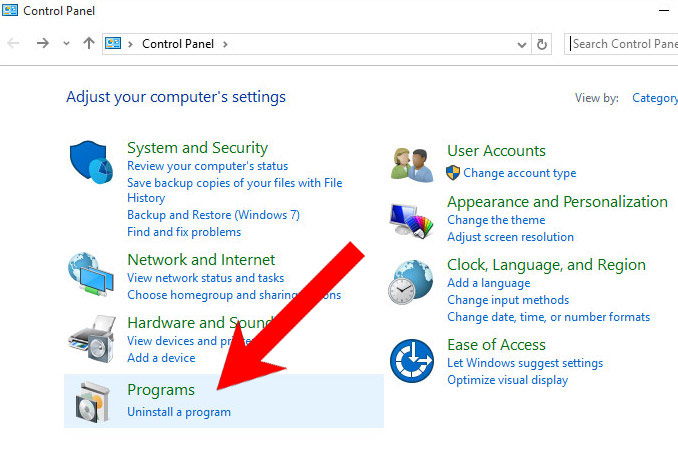
- Press on the Start icon.

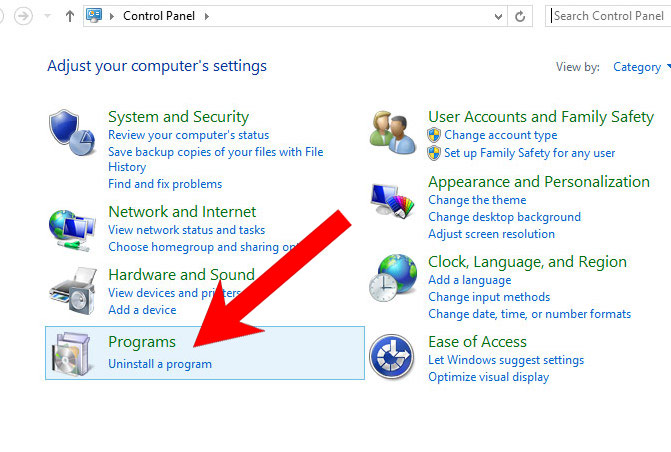
- Control Panel → Programs and Features.

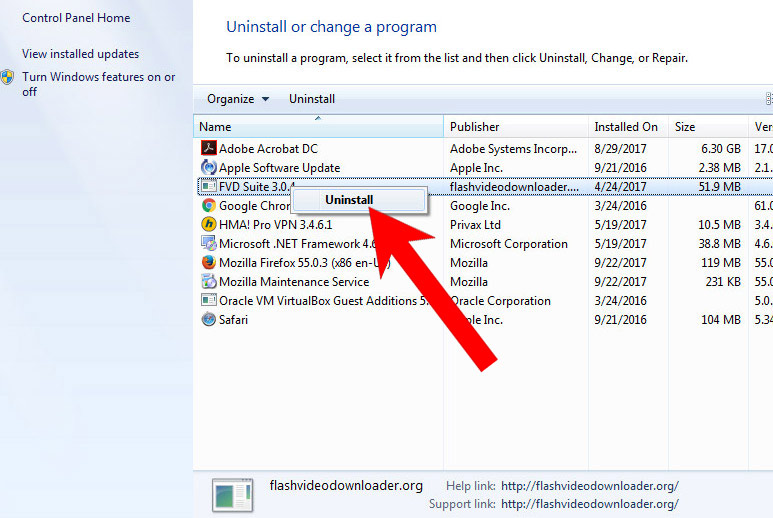
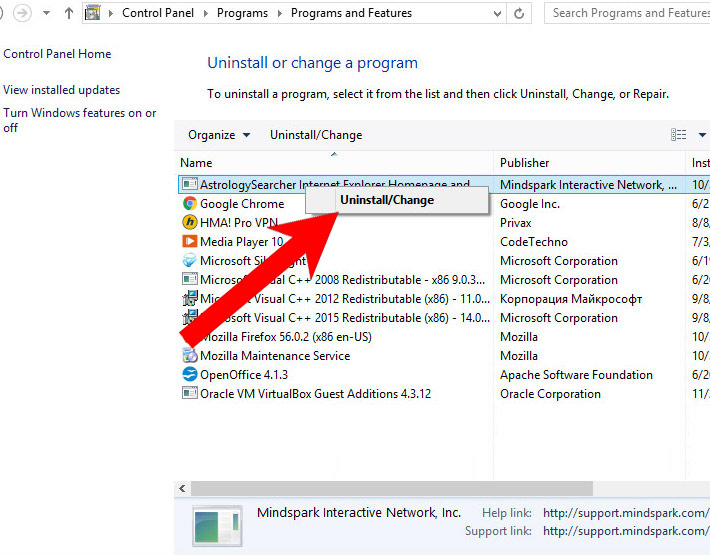
- Find the program you want to delete and press Uninstall.

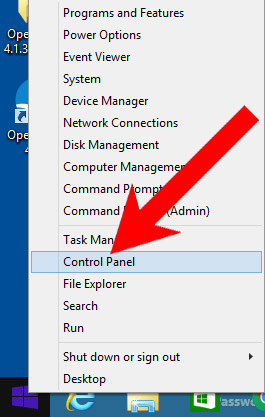
b) Windows 8
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

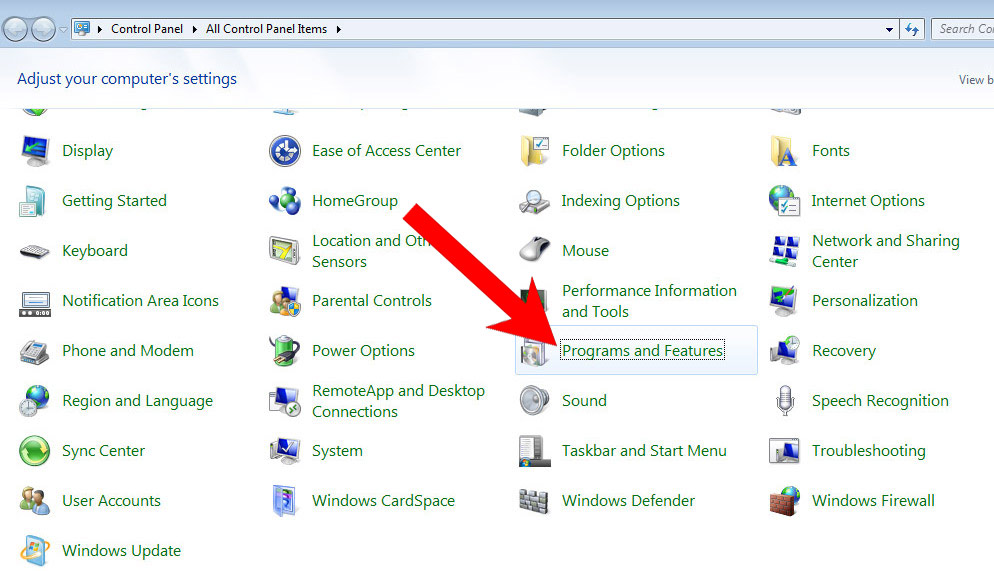
c) Windows 10
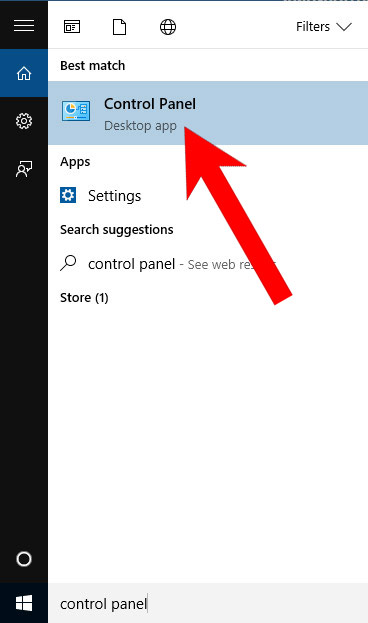
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

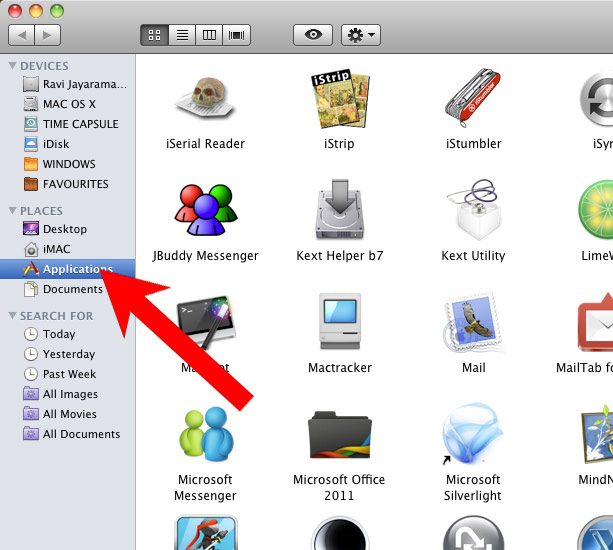
d) Mac OS X
- Open Finder and press Applications.

- Check all suspicious programs you want to get rid of.
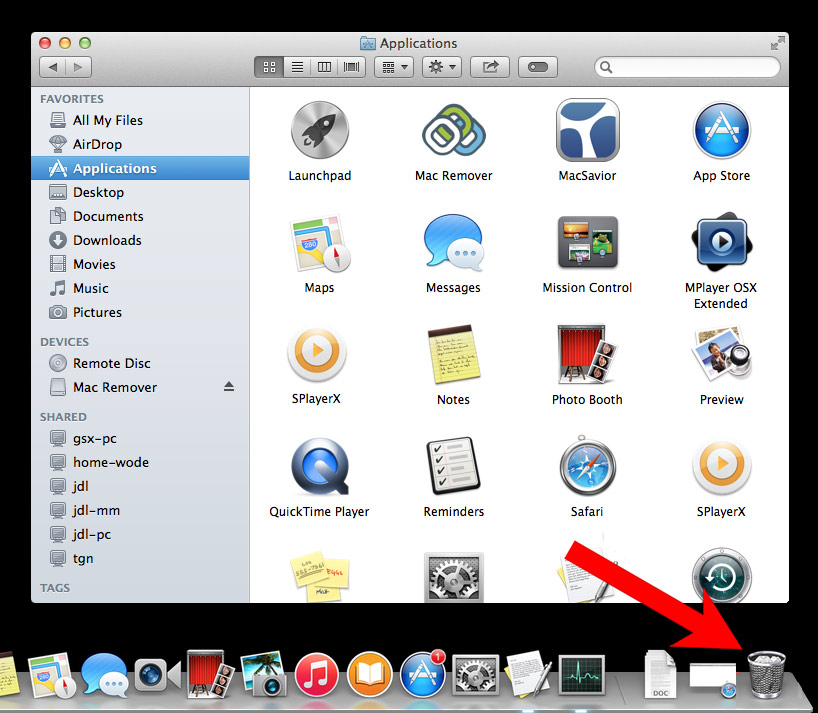
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete I Managed To Install A from browsers
a) Remove I Managed To Install A from Microsoft Edge
Reset Microsoft Edge (Method 1)
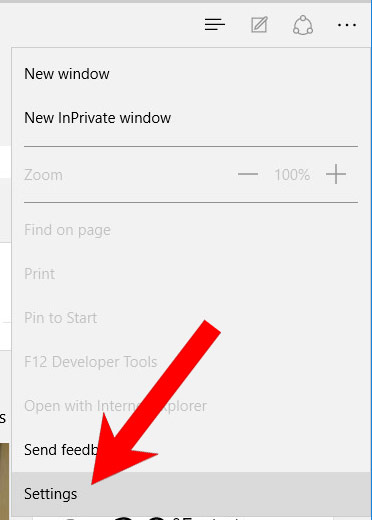
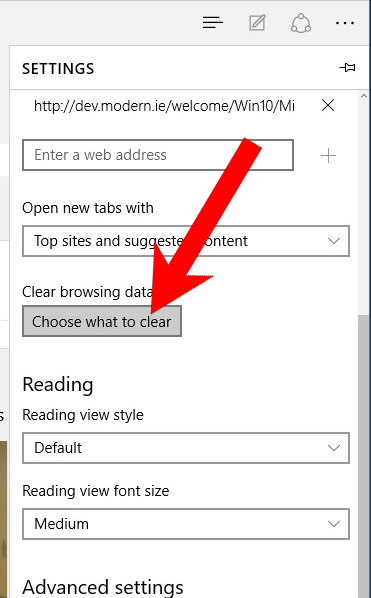
- Open Microsoft Edge.
- Press More located at the top right corner of the screen (the three dots).

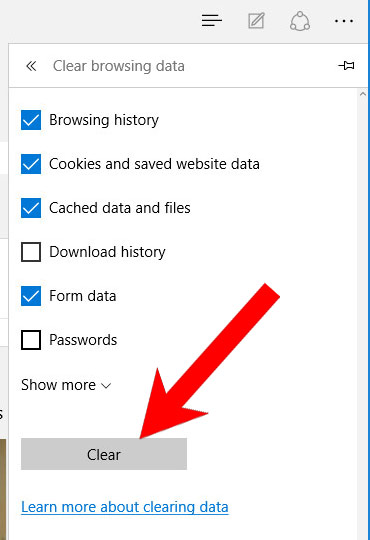
- Settings → Choose what to clear.

- Check the boxes of the items you want removed, and press Clear.

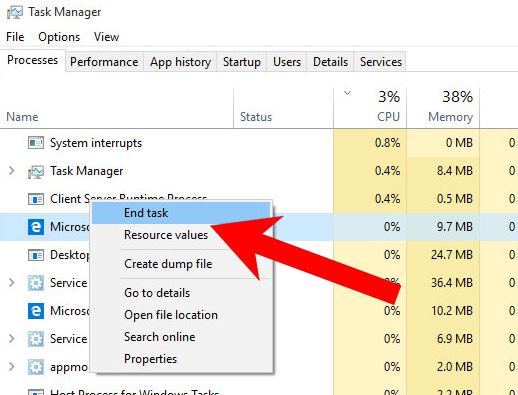
- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
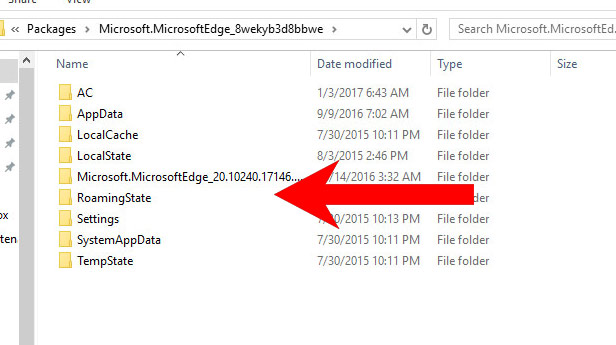
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

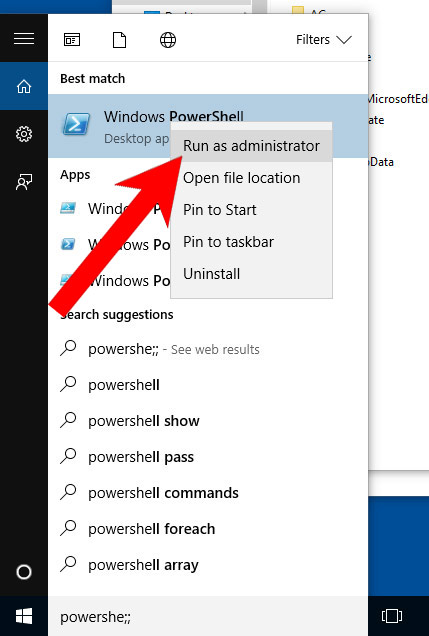
- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

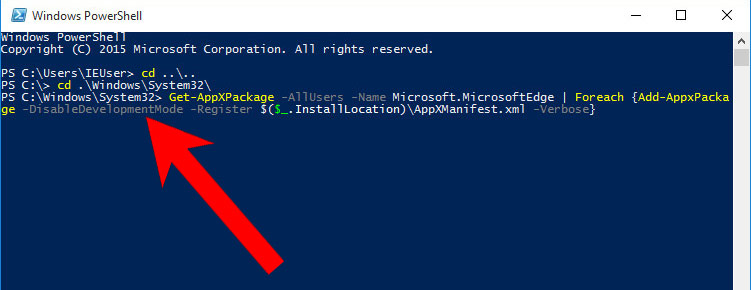
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
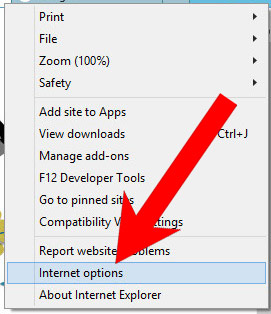
b) Remove I Managed To Install A from Internet Explorer
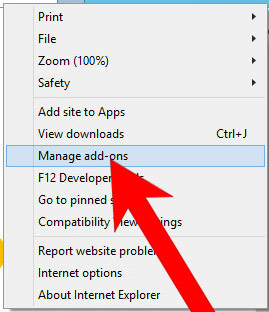
- Open Internet Explorer and press on the Gear icon.

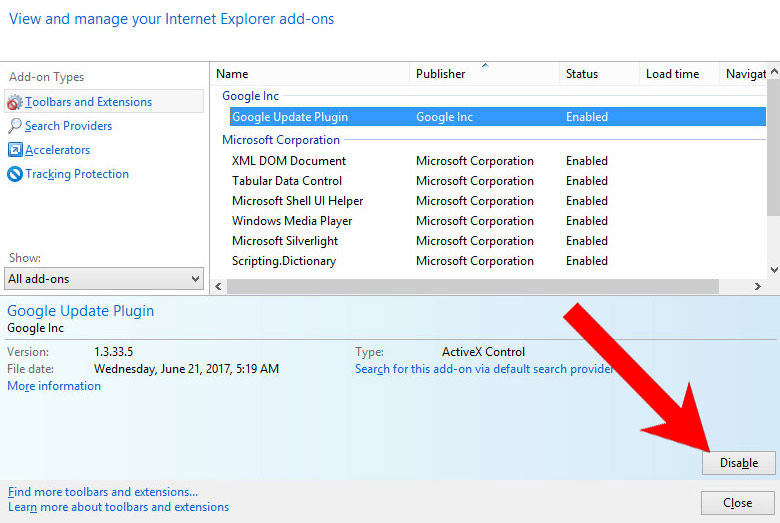
- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
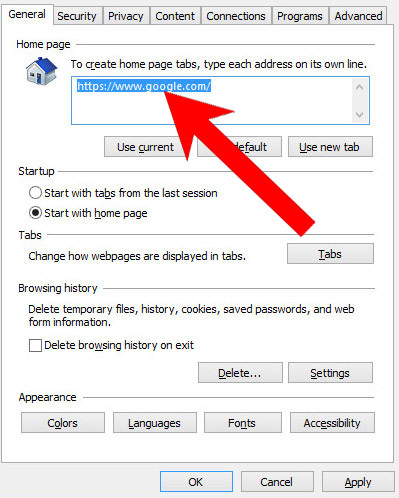
c) Restore your homepage on Internet Explorer
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
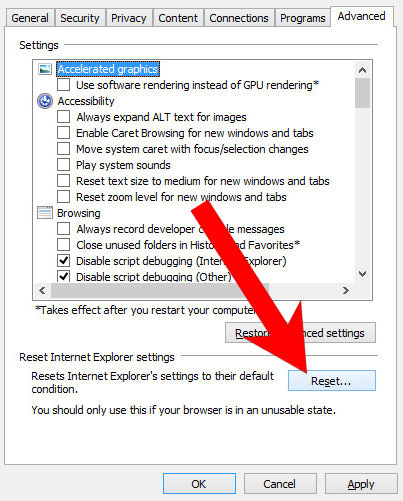
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

- At the bottom, you will see a Reset button. Press that.
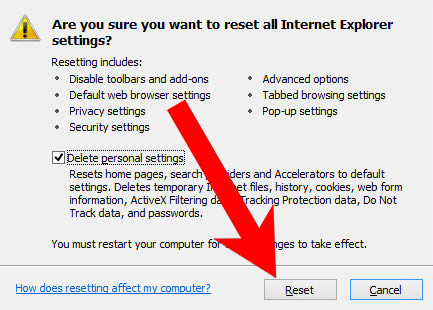
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
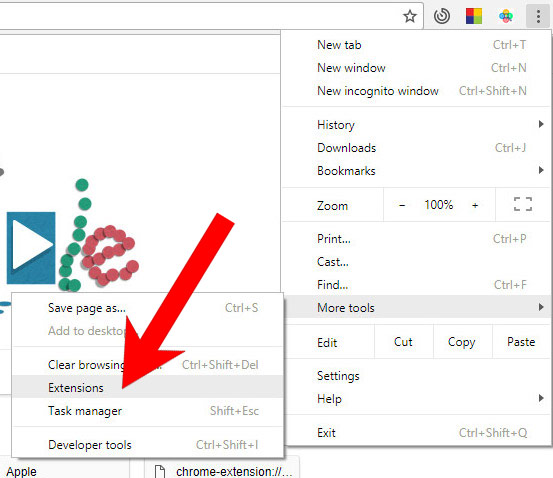
e) Remove I Managed To Install A from Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
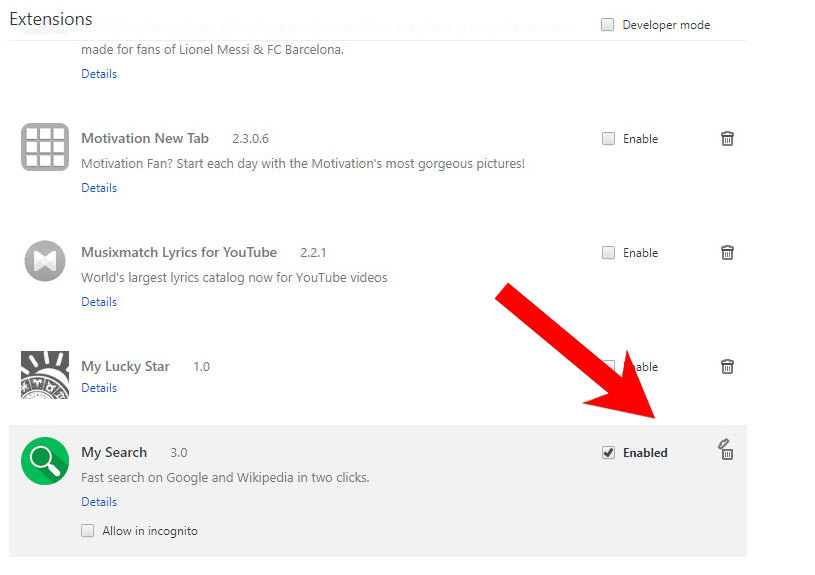
- Choose More tools and Extensions.

- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
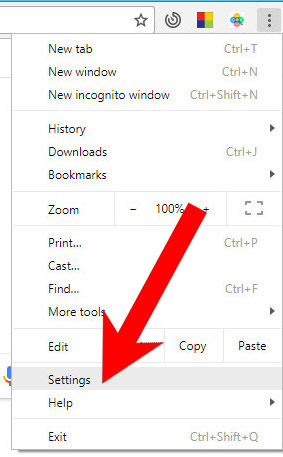
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

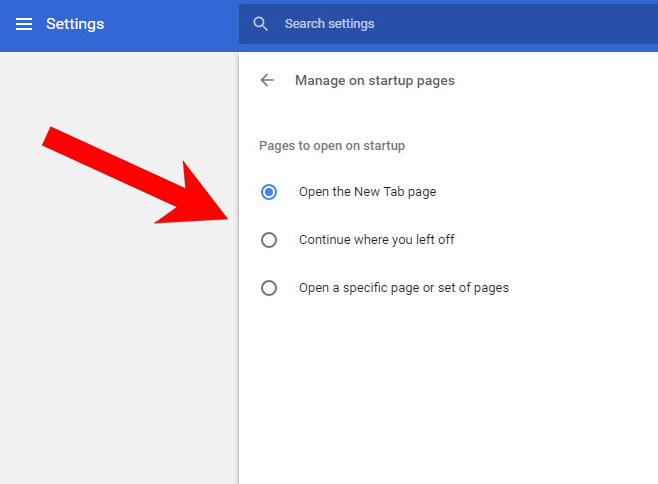
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

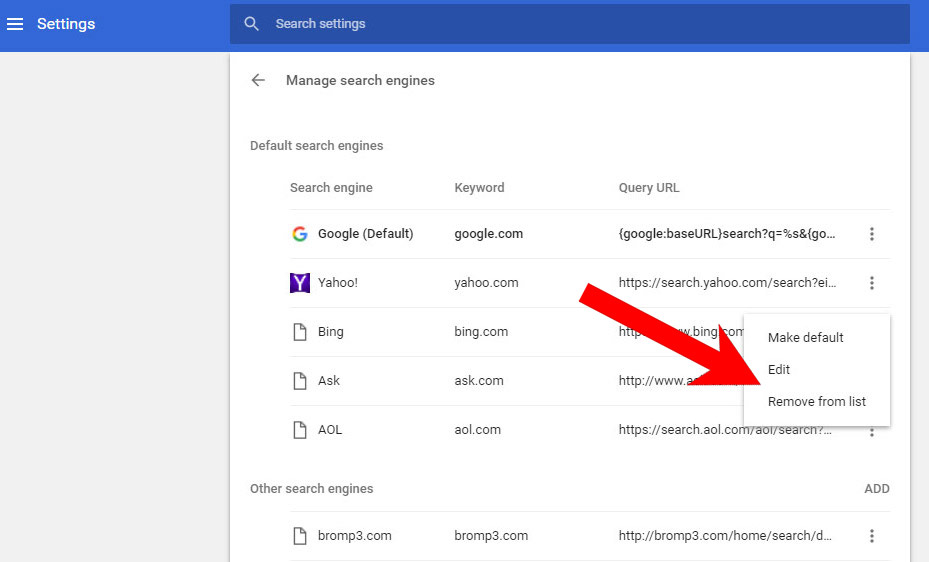
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
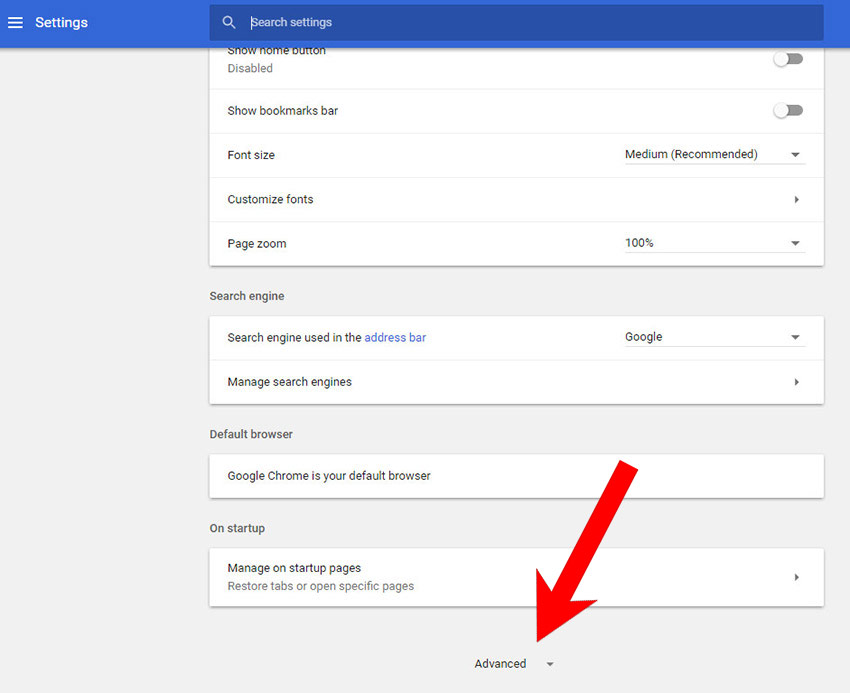
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

- Scroll down and press on Show advanced settings.

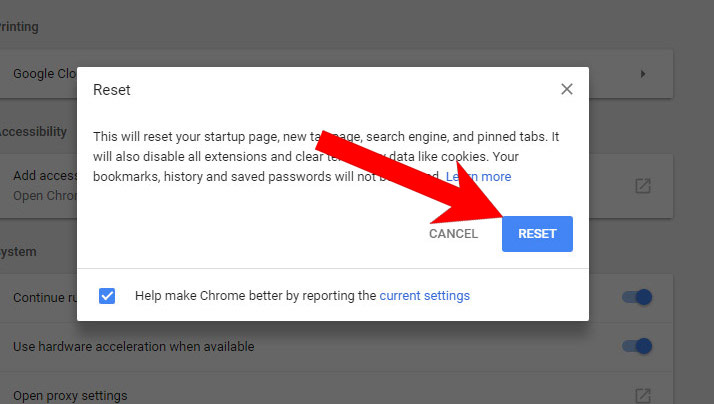
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
h) Remove I Managed To Install A from Mozilla Firefox
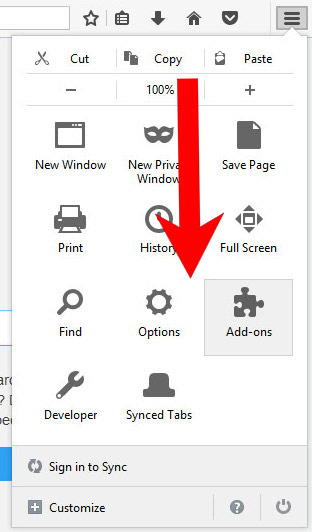
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Select Add-ons.

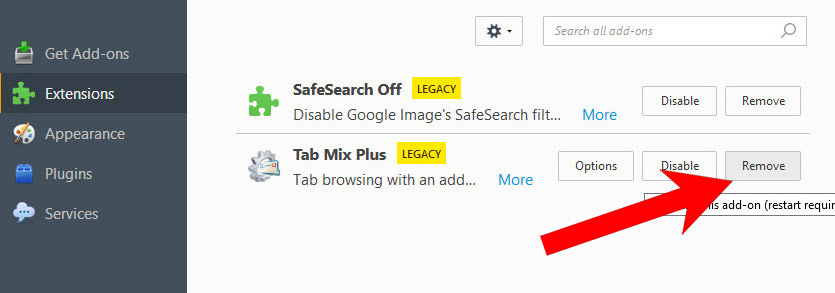
- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
i) Restore your homepage on Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
- Select Options.

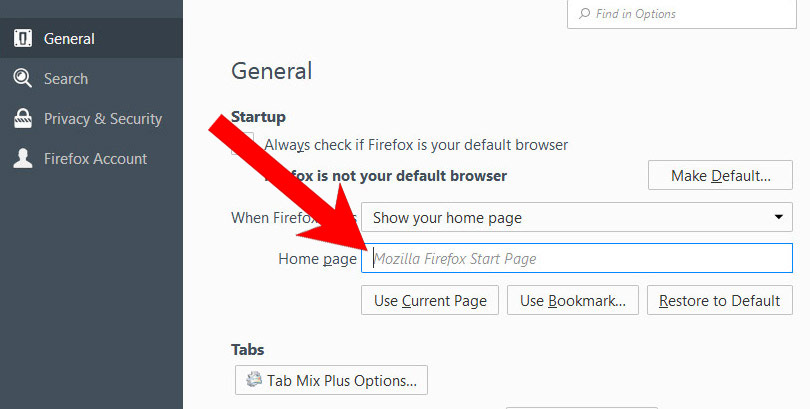
- In General, click Restore to Default below the Home Page field.

j) Reset Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
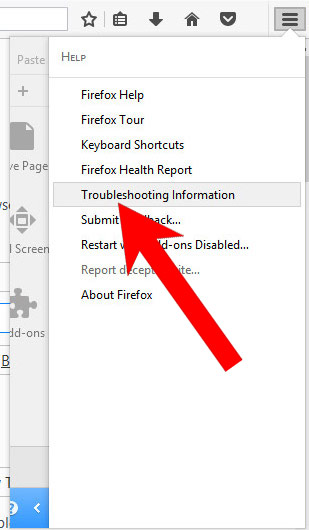
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

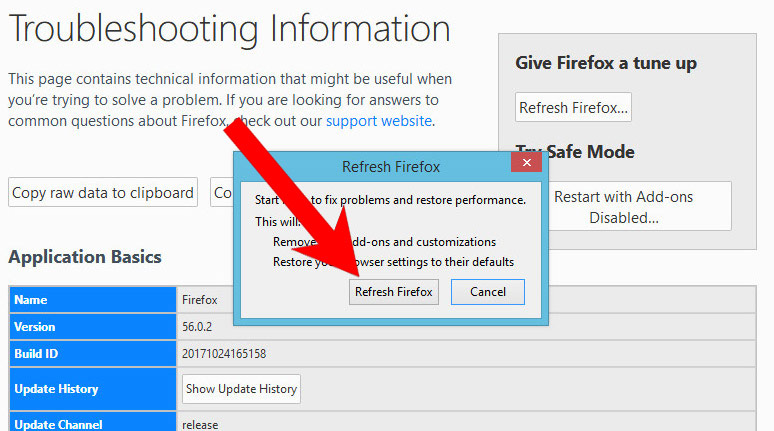
- Select the Refresh Firefox option.

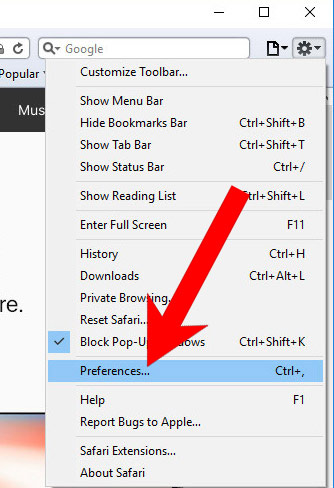
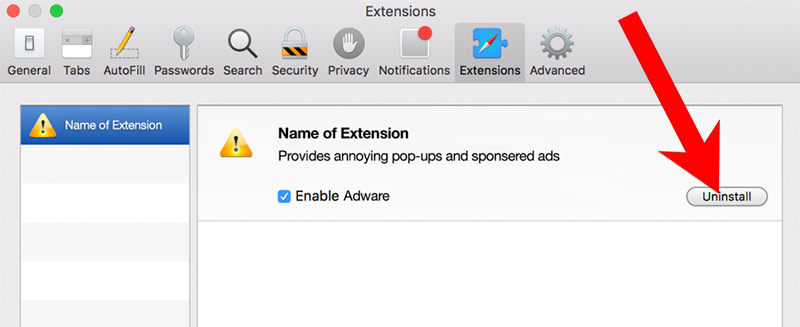
k) Remove I Managed To Install A from Safari (for Mac)
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
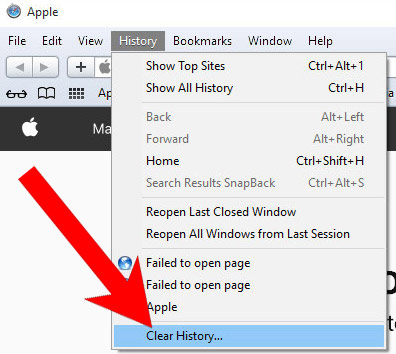
l) Reset Safari
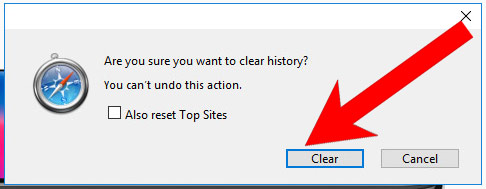
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

- Press on Safari at the top of the screen and select Preferences.

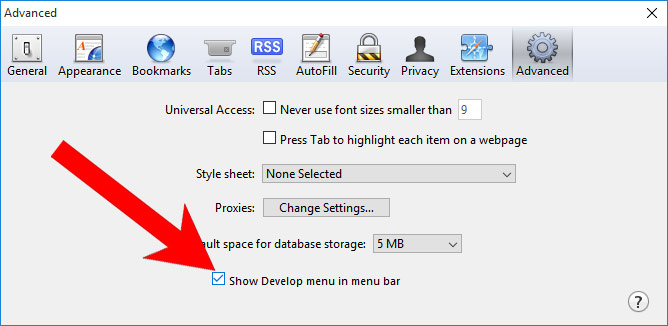
- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
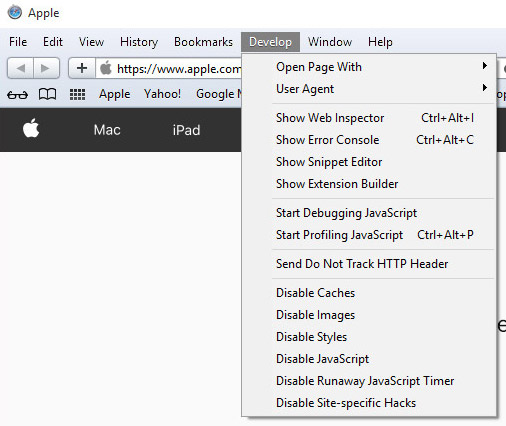
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.