This reveals why you Have presumably been not able to warning when or how the breach by it has occured.
A load of of our people arrived into to us relating to an email spam that they gotten in addition to the following notice:
Hello! Have you lately observed that I Have e-mailed you from your account? Yes, this merely means that I Have total entry to your system. For the final couple of months, I Have been watching you. Regardless curious how is that probable? Well, you Have been contaminated with infection springing from an adult web page that you entered. Alongside assistance of the Trojan malware, I Have whole entry to a system or any other pc. This purely means I can see you at any moment I are eager to on your screen by merely turning on your camera and microphone, without you even knowing it it. In addition, I Have on top of that got entry to your contacts category and all your correspondence. I Have a video of you wanking on the dropped screen, and on the right screen – the video you were watching although masturbating. Speculating how bad might this get? Along with merely one tap of my mouse, this video could be transmitted to all your social networks, and e-mail contacts. I may also share entry to all your e-mail correspondence and messengers that you employ. All you Have to perform to avoid this from occurring is – transmit bitcoins worth $1450 (USD) to my Bitcoin address (if you Have no indication on how to perform this, you are able to start you browser and merely search: “Buy Bitcoin”). My bitcoin address (BTC Wallet) is: 1D8qdtNLNbvugZyMYUyhzcGiCdFinxHgtH After receiving a verification of your payment, I will remove the video quickly, and that’s it, you shall never hear from me again. You Have 2 days (48 hours) to execute this transaction. As soon as you open this e-mail, I shall acquire a warning message, and my timer shall beginning ticking. Any try to document a complaint shall not lead to anything, because this e-mail can not be detected back, same as my bitcoin id. I Have been tackling this for a terribly lengthy time by now; I don’t grant any probability for a fault. If, by any shot I discover that you Have scattered this note together with everybody else, I shall broadcast your video as noted earlier.
Download Removal Toolto remove Have
There are all sorts of methods in which a Trojan Horse malicious software may happen. For example, getting, and beginning the attachment of some unreliable spam letter, or pressing on a download hyperlink that has been camouflaged as a attractive internet recommend exists two of the methods you are able to arrive a Trojan on your pc. Another greatly usual circulated scheme for such malicious software is the use of web pages that distribute pirated content. Oftentimes, cyber criminals as upload their dangerous program to such pages, and cover up them as some good tools or games. Regardless of the fact that it’s illegitimate, a lot of computer users go to pirate websites, and download stuff from them. If a computer user occurs to obtain a Trojan camouflaged as the installer of a software that the user aims, and the latter starts the the false installer and provides it their authorization to make modifications in the pc, the Trojan would get produced, and would now be free-of-charge to execute its insidious and damaging functions. As we mentioned former, the user might not even understand that a legitimate malware item has infiltrated their device. Counting on every individual case, there may or might not be noticeable symptoms of the Trojan Horse breach.
The Have you freshly detected that I Have e-mailed you from your account? Email
Nevertheless, if you think that you Have a reason to believe “Have you recently noticed” is in your system at the moment, it’s best to meticulously check your system for any malicious files and processes, and remove everything you may find. However, there is a issue in packages with that – generally, Trojan malware like “Have you newly noticed”, Walliant, Wup.exe lurk their files in device folders, and title them, as well as their procedures and Registry keys, as ordinary system-akin ones. This earns it tough both to locate the infections parts, and to eliminate them. Moreover, it boosts the probability of erasing something that you are not supposed to. For example, you might unintentionally terminate some vital system file, or Registry key, and thus generate the condition way harsher than it earlier is. For this reasoning, it’s greatest to thoroughly act in accordance with our guide, and if you Have any suspicions, request our aid in the comments, and/or employ the uninstallation application you’ll see related underneath.
Download Removal Toolto remove HaveThe harm “Have you lately noticed” may result in
Tailing on you, taking entire custody of your computer, adding other malicious software like Ransomware, extorting confidential statistics from your pc and on the internet accounts, and a great many of etc. are the probable makes use of of a Trojan Horse malicious software. The particular objective of “Have you lately noticed” isn’t yet notorious, but despite what it is, you ought to still a majority of certainly terminate the threat promptly, instead of being uncertain to discover what the result of its breach could be.
Learn how to remove Have from your computer
Step 1. Have Removal from Windows
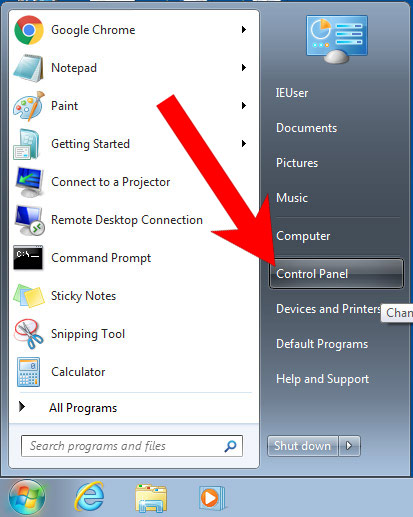
a) Windows 7/XP
- Press on the Start icon.

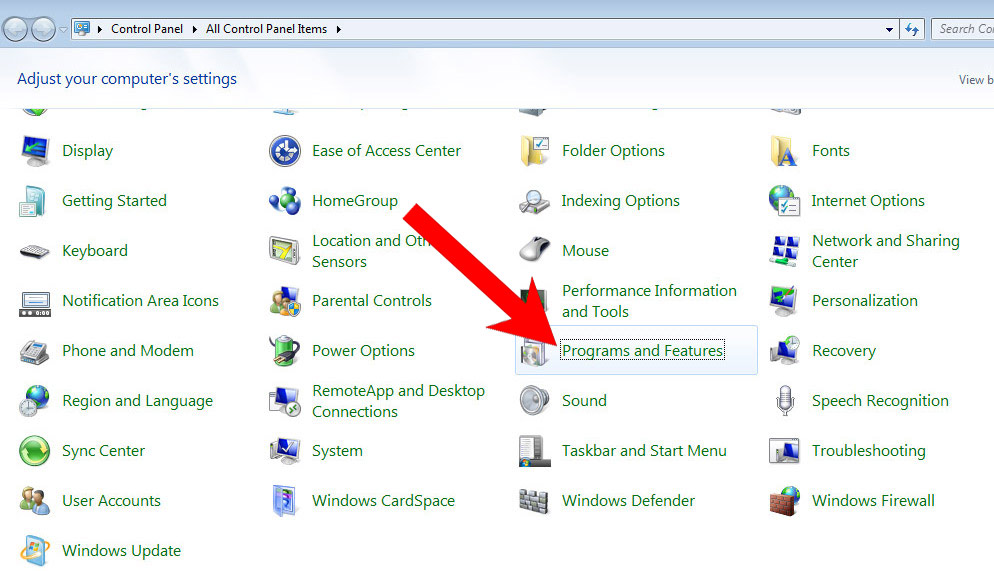
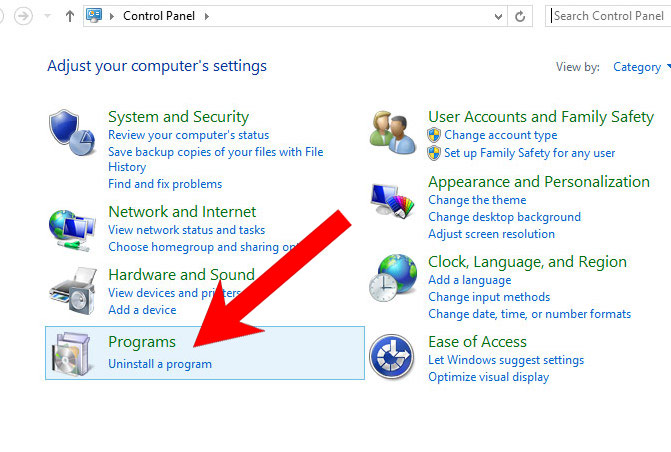
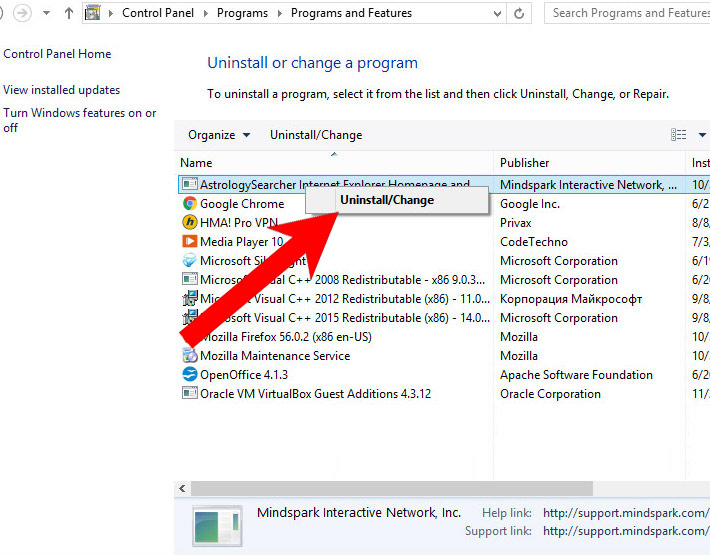
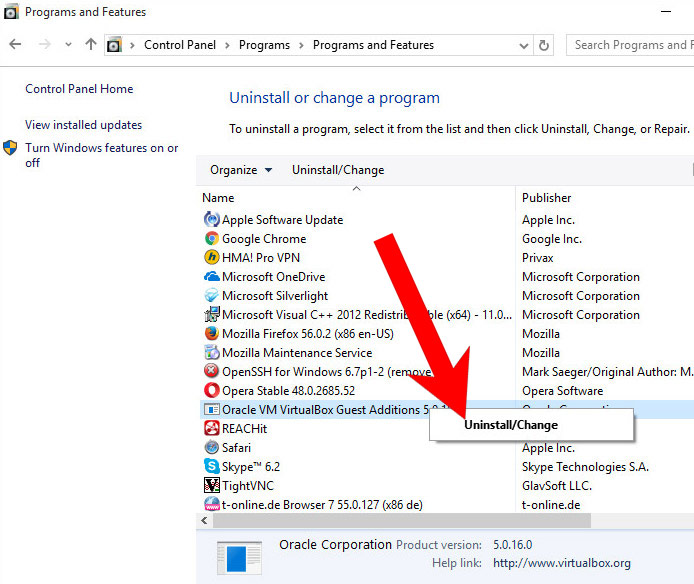
- Control Panel → Programs and Features.

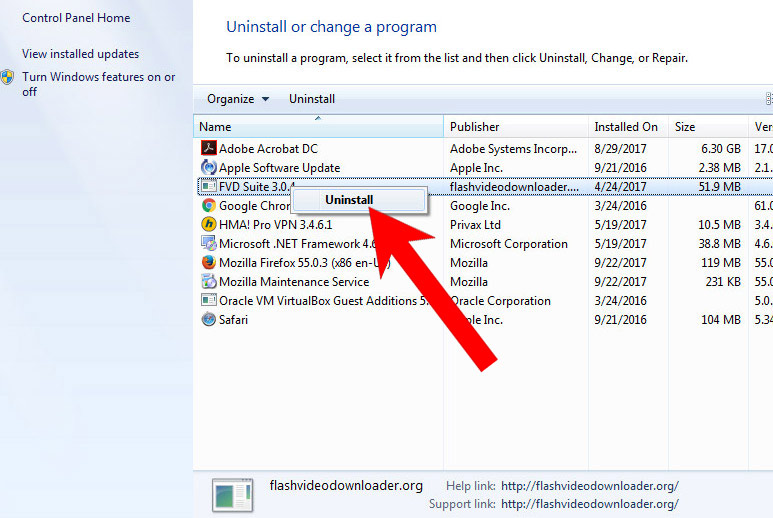
- Find the program you want to delete and press Uninstall.

b) Windows 8
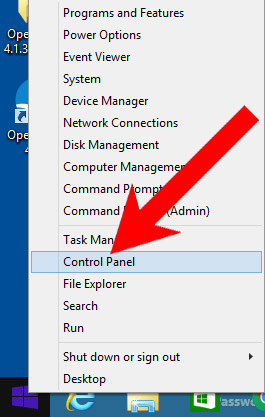
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

c) Windows 10
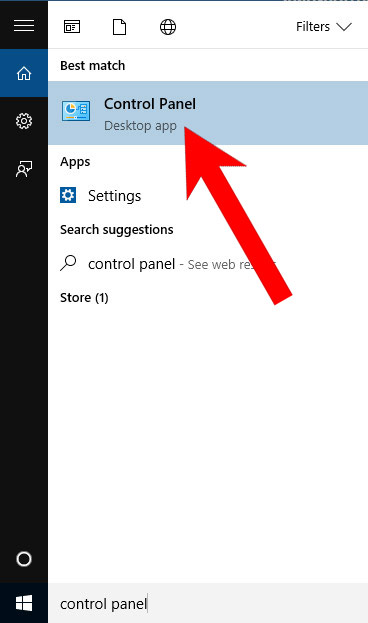
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

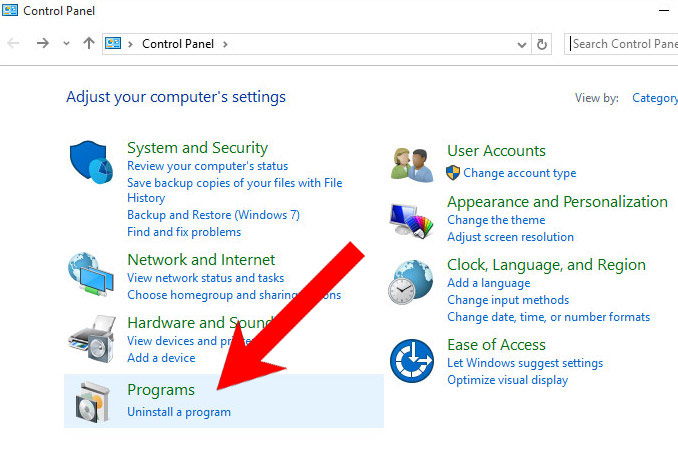
- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

d) Mac OS X
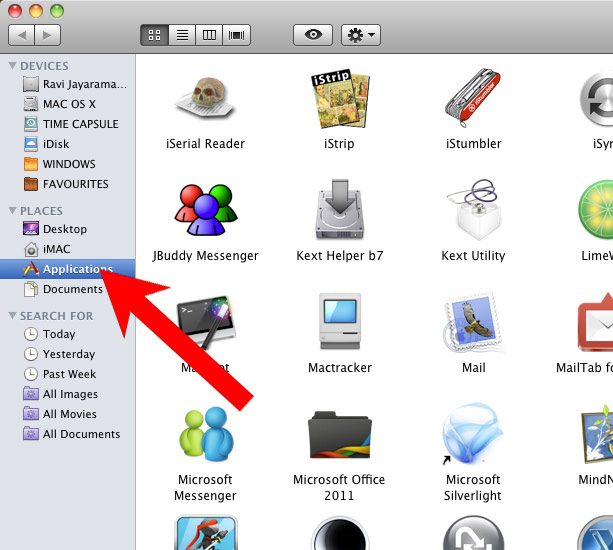
- Open Finder and press Applications.

- Check all suspicious programs you want to get rid of.
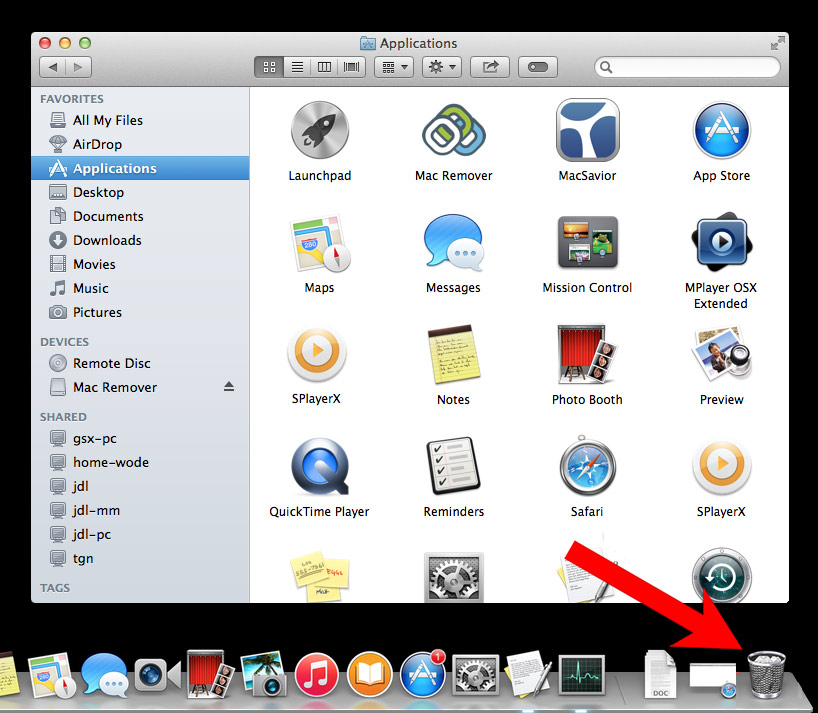
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete Have from browsers
a) Remove Have from Microsoft Edge
Reset Microsoft Edge (Method 1)
- Open Microsoft Edge.
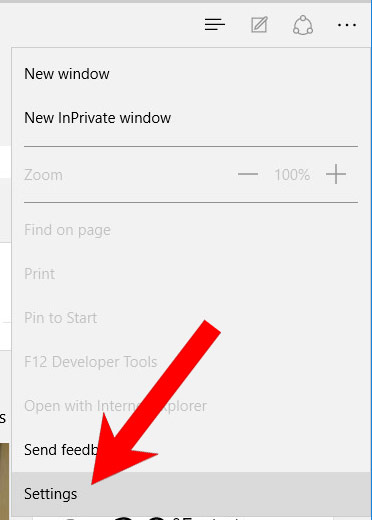
- Press More located at the top right corner of the screen (the three dots).

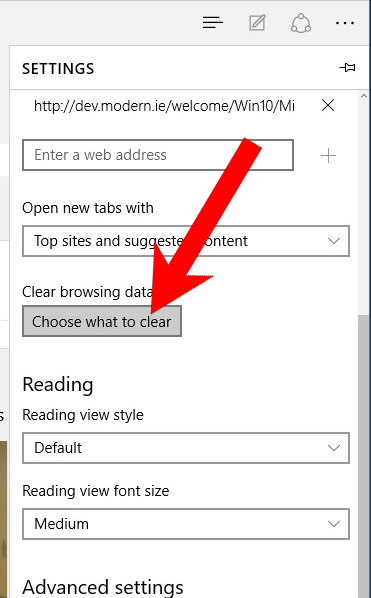
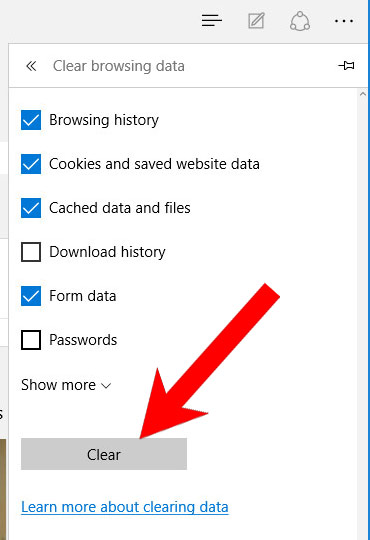
- Settings → Choose what to clear.

- Check the boxes of the items you want removed, and press Clear.

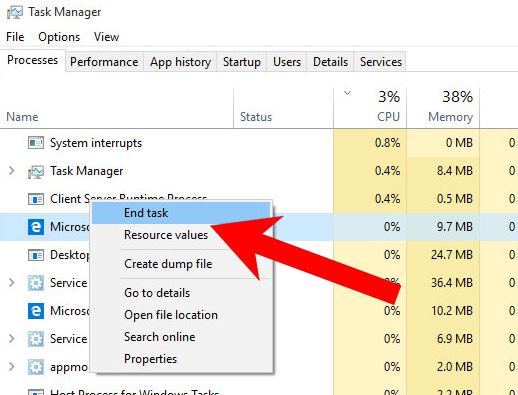
- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
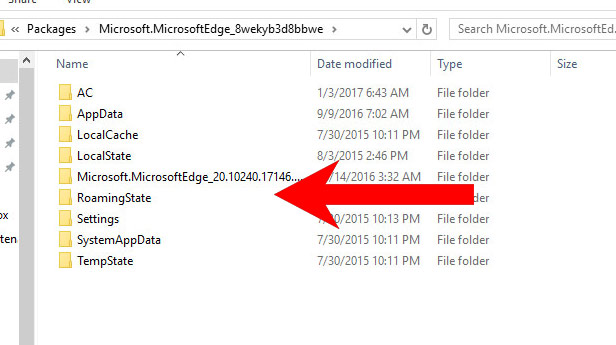
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

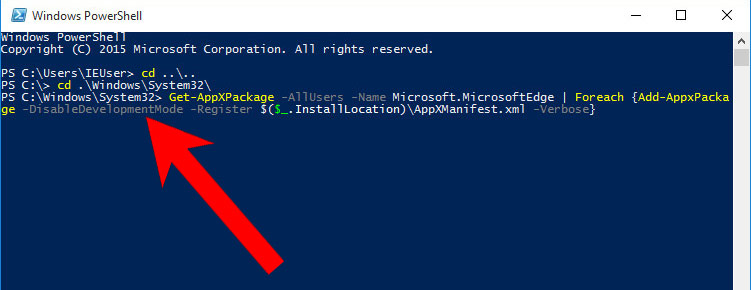
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
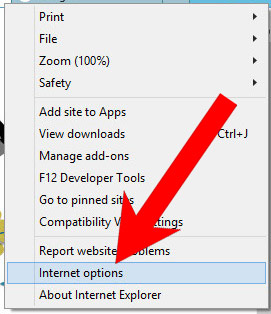
b) Remove Have from Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
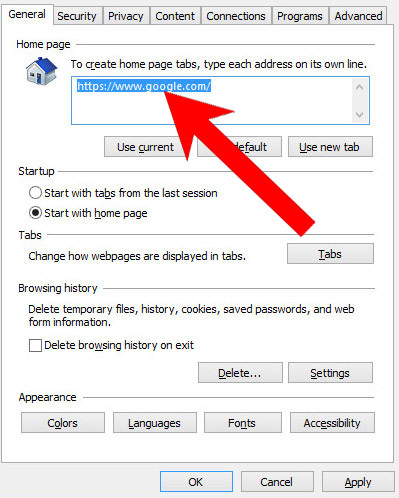
c) Restore your homepage on Internet Explorer
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
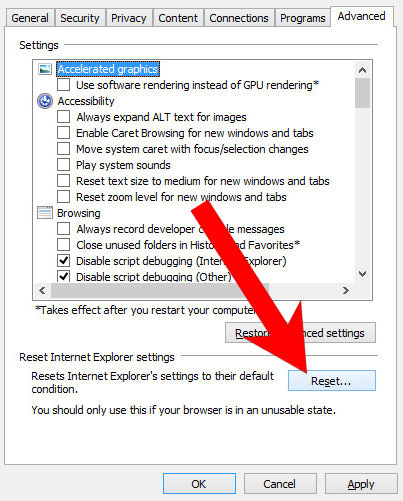
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

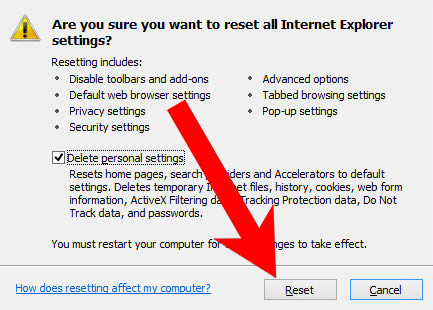
- At the bottom, you will see a Reset button. Press that.
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
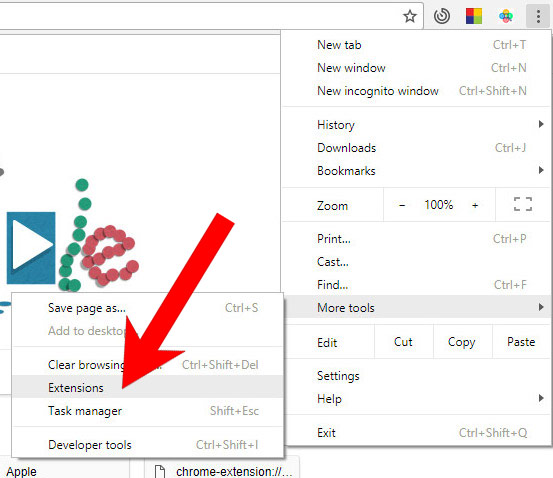
e) Remove Have from Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose More tools and Extensions.

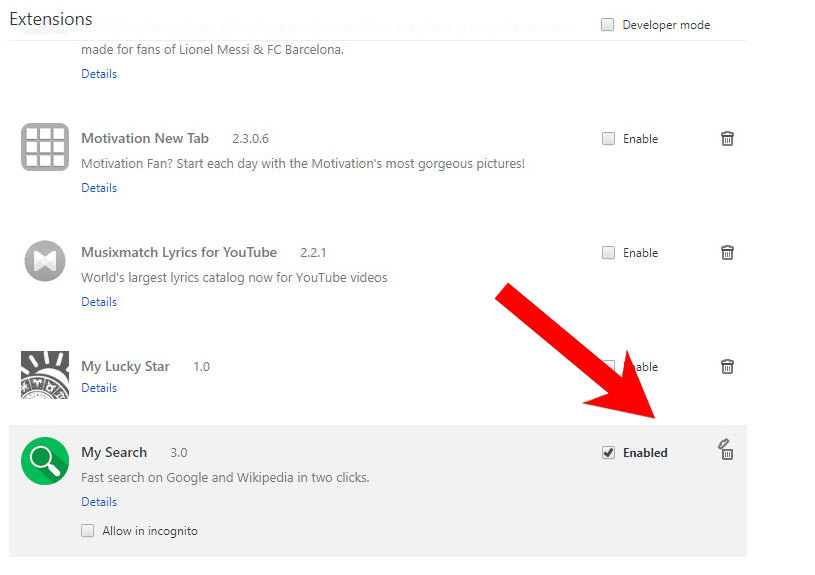
- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
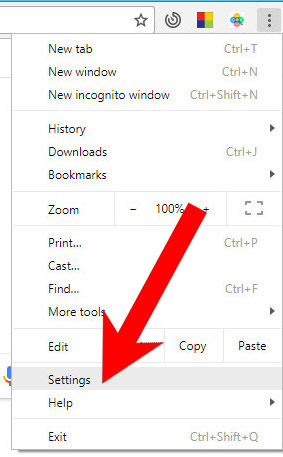
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

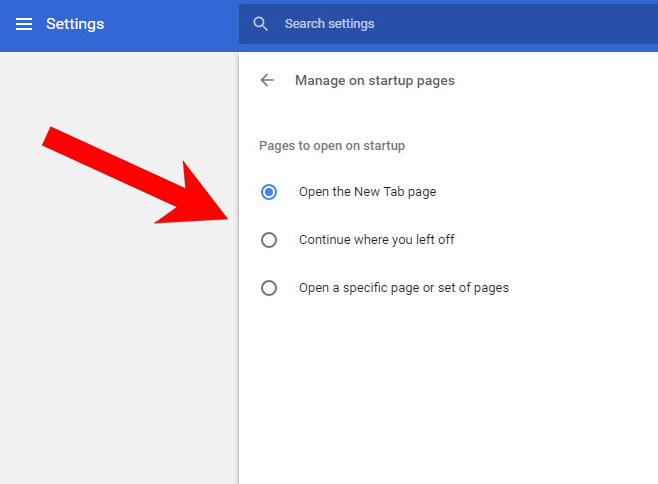
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

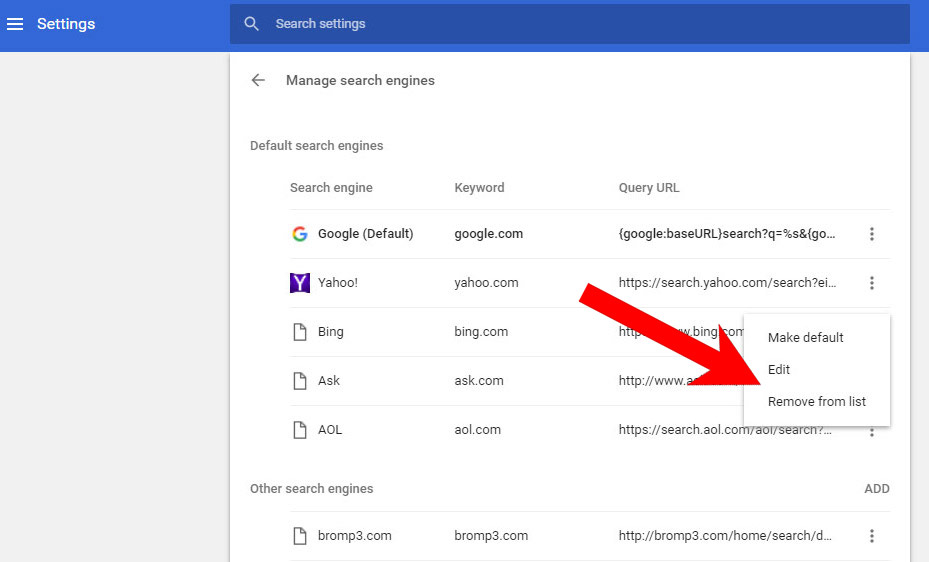
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
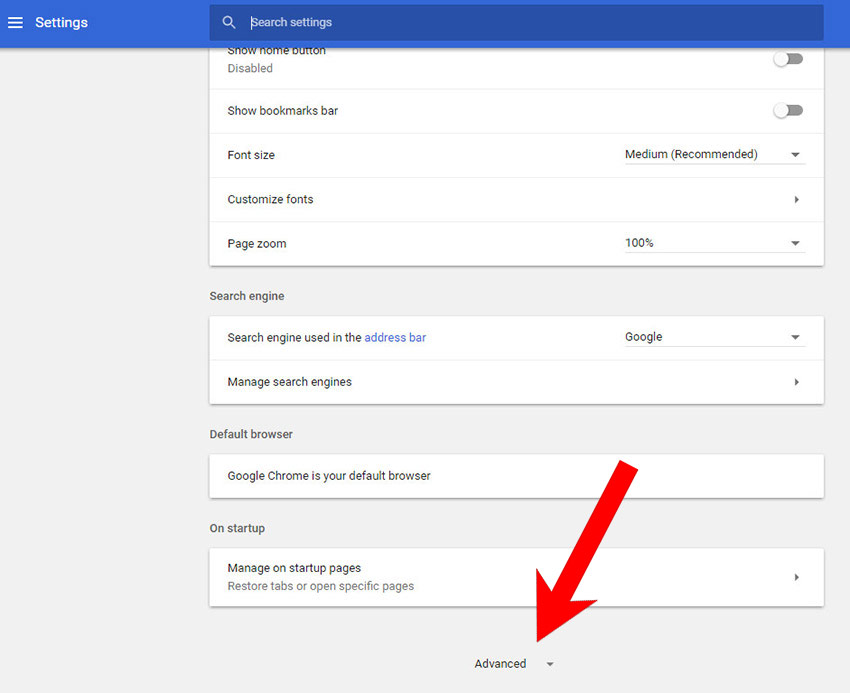
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

- Scroll down and press on Show advanced settings.

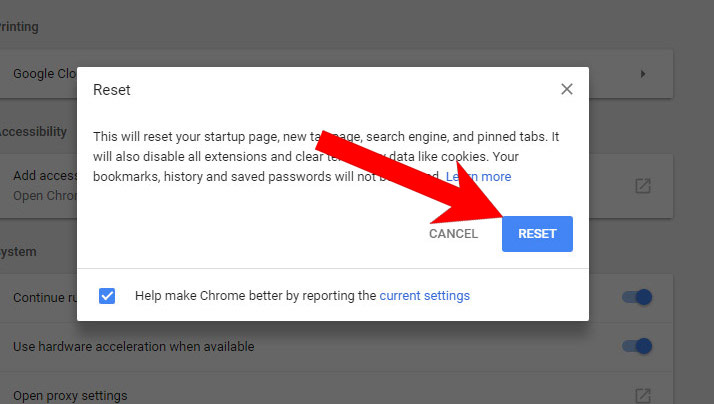
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
h) Remove Have from Mozilla Firefox
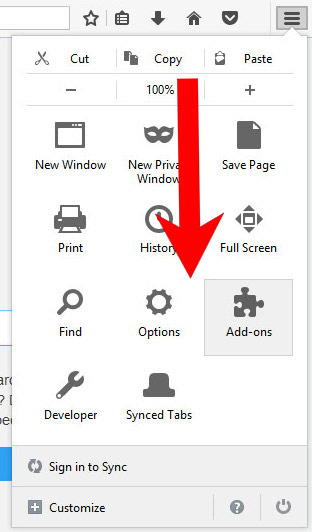
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Select Add-ons.

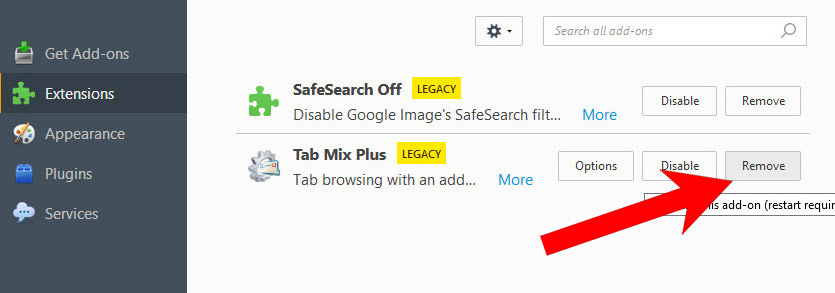
- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
i) Restore your homepage on Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
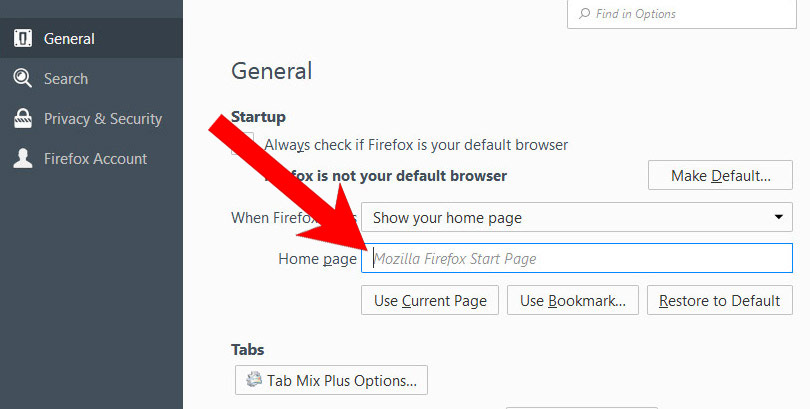
- Select Options.

- In General, click Restore to Default below the Home Page field.

j) Reset Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
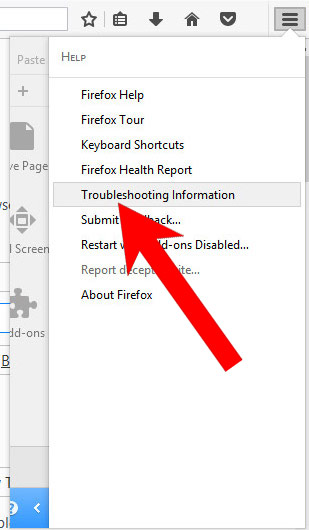
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

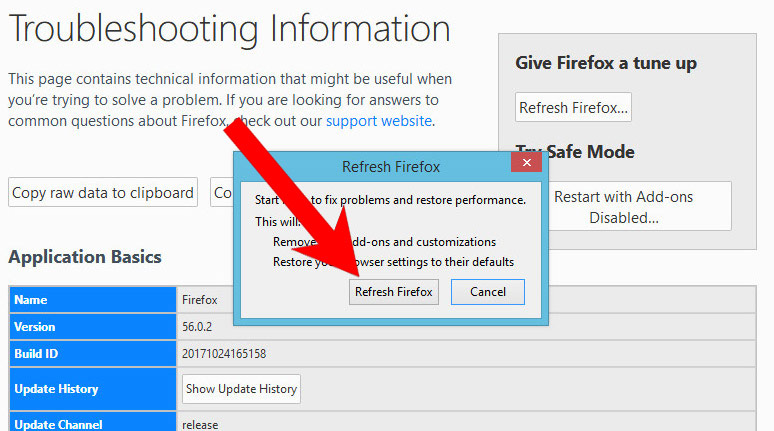
- Select the Refresh Firefox option.

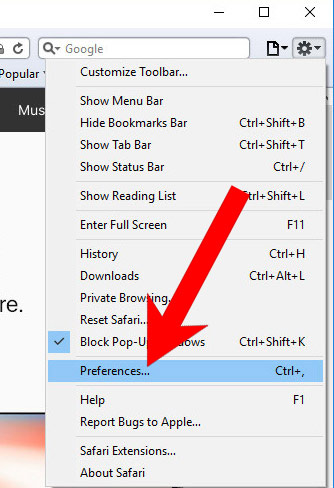
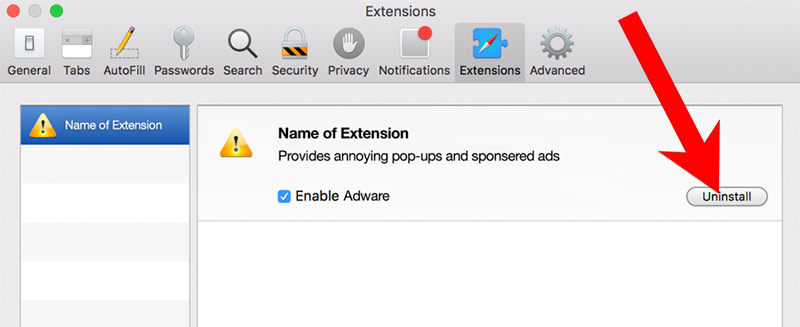
k) Remove Have from Safari (for Mac)
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
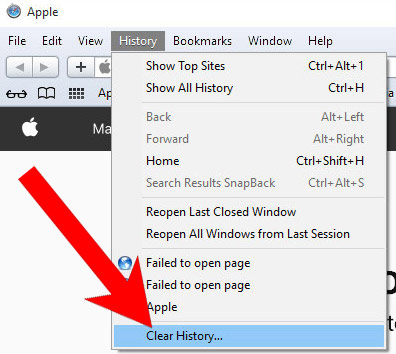
l) Reset Safari
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
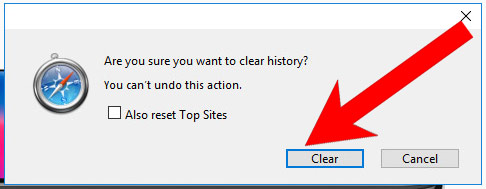
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

- Press on Safari at the top of the screen and select Preferences.

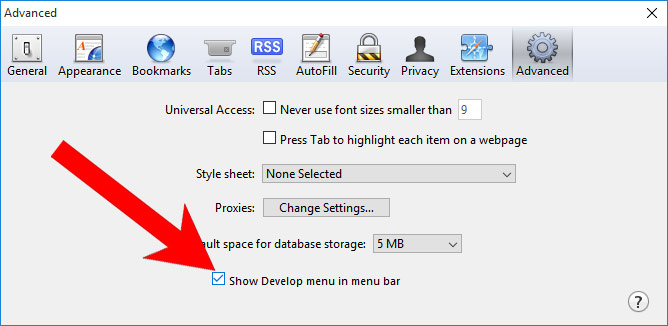
- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
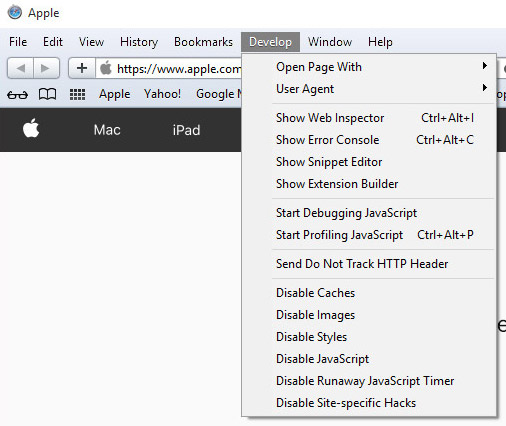
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.