“Configure” Extension
“Configure” Extension is a browser hijacker that doesn’t do anything bad to the system, but it’s still can be considered as a possible security risk. Well-known for spamming the screen with troublesome adverts and pop-ups, “Configure” add-on is also famous for seizing the browser’s installation mode and encouraging some promoted search engine or home website onto it. The “Configure” add-on malicious software
In stable, browser redirect viruses are neither malware nor legit applications which might serve a convenient intention. Rather, they fall someplace in between those two classifications of an application and work in a bit bothering scheme.
There are tens classes of invaders and some are just utilities pieces that swap the user’s search engine or home webpage decisions. Applications like “Configure” and Poshukach together with trickier seizing abilities can be installed as stand-separately applications on the pc, and they may make a slew of alters to the os and browser modes. Some browser attackers use corrupt practices, for instance deceitful captchas on webpages, to gain access to the user’s Chrome, Firefox, or Edge browser so to make more traffic and increase their promoted pages in search engine outcomes. Pay-Per-tap and Pay-Per-outlook are the two the biggest number of common internet ad-sustained approaches employed by these kinds of apps utilities pieces and, as long as they are not illegitimate, these kinds of ad-sustained approaches regardless accompany their own dangers. “Configure” add-on is the usual representative of the browser intruder applications categorization and, as such, the ploys it makes use of to pull off its promotional motives may raise some uncertainties about the trustworthiness of a pc operating system that shouldn’t be bypassed.
Download Removal Toolto remove ConfigureIs “Configure” add-on a a harmful program?
The original impression of “Configure” plug-in explains that all this hijacker does is to place adverts on the web pages you visit as you search the web and acquire quite a few potentially redundant alterations to your explorer. Although you are reliable bypassing the pestering pop-ups, pop-unders and site routing, many people locate on their own stuck together with the new configurations of their browser and its behaviour. Fortunately that there is no prompt effect on the machine from the most frequent ads show and browser changes, but what you ought to realize is that those modifies may potentially be employed by other internet perils e.g Trojans, Ransomware cryptoviruses and infections for their access onto the pc.
Sadly, the biggest part of hijacker programs don’t have a lot handle over the adverts and web links they are providing on the screen, and this comes along with its own perils. For position, when users tap on the accidental adverts that “Configure” plugin makes, they hazard ending up on malevolent portals or portals infected with a malicious virus that looks to be dependable and profitable from a at the beginning look. The the biggest number of classic reaction when being led to a an infected site is to merely exit the browser tab without pressing on anything else.
However, this might not always be feasible as cybercriminals are collecting etc. innovative in baiting people in bundles with sensible-searching content which might trick you onto revealing your private details, or getting some lawful-searching tools and, in this manner, putting your system and computer at jeopardy. To lower that jeopardize, we encourage that you avoid pressing on anything that “Configure” plug-in shows on your screen or, get rid of the hijacker software and delete all of its linked files and modes. If carried out accordingly, this will erase all the annoying adverts and browser modifies and prohibit you from being insecure to phishing pages or sites that could circulated malicious software like Trojans, Ransomware, malicious software, malware and other connected on the internet perils.
Download Removal Toolto remove ConfigureWhether you need assist, “Configure” add-on can be removed from your device by following the stage-by-step invader an elimination guide detected just at the end of this article. To salvage some time, you could also wish to use a powerful anti-malicious software tool. A mixture of both ways will assure that “Configure” add-on won’t return in an automatic way the next time you reboot the system.
Learn how to remove Configure from your computer
Step 1. Configure Removal from Windows
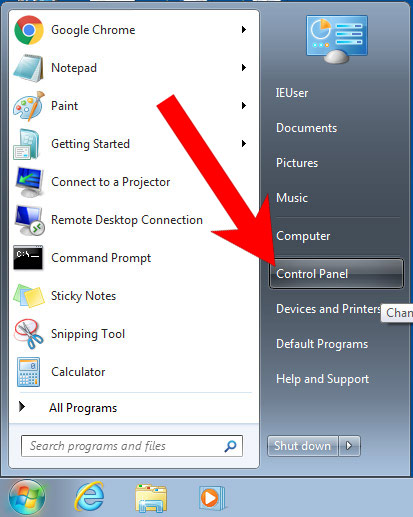
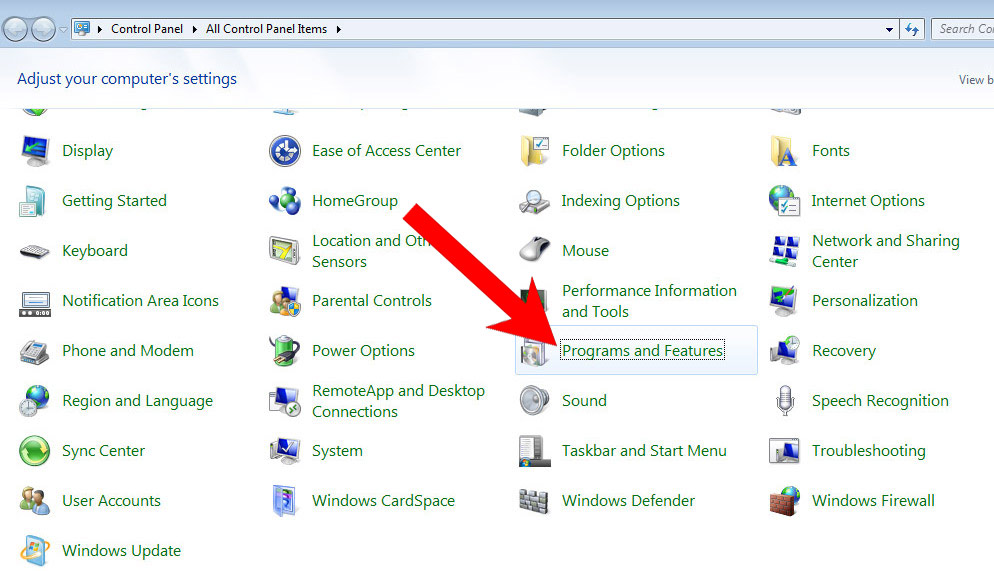
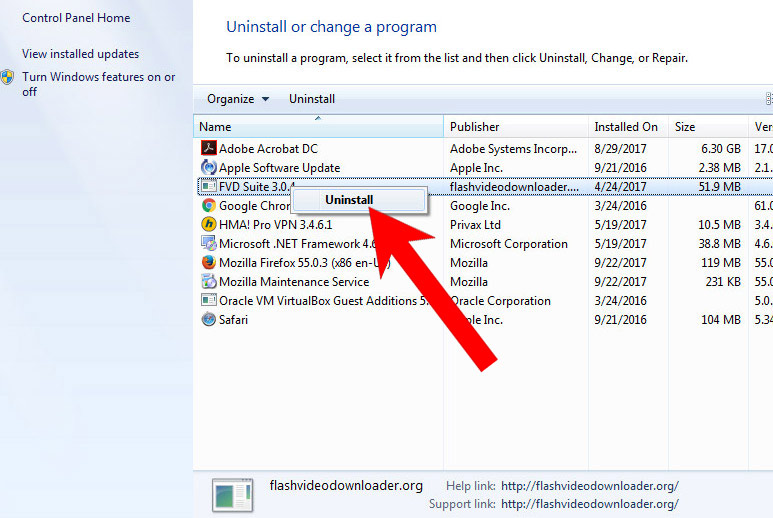
a) Windows 7/XP
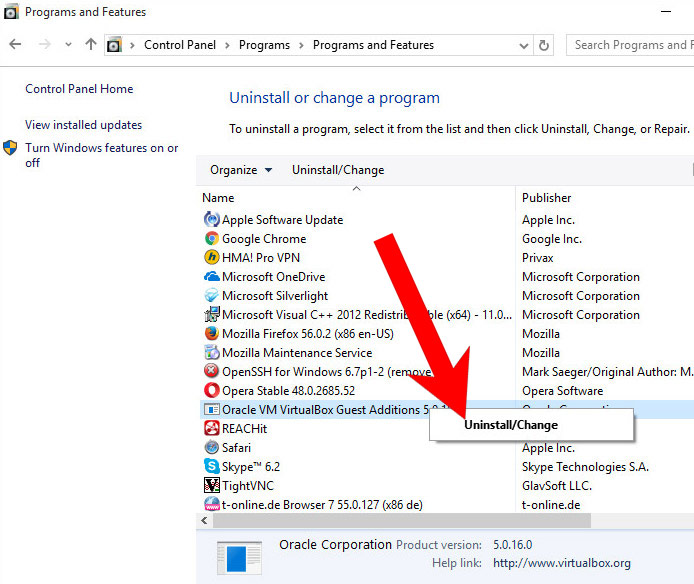
- Press on the Start icon.

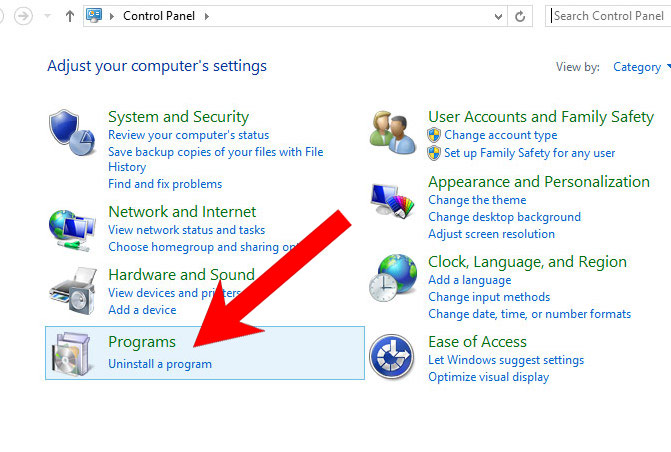
- Control Panel → Programs and Features.

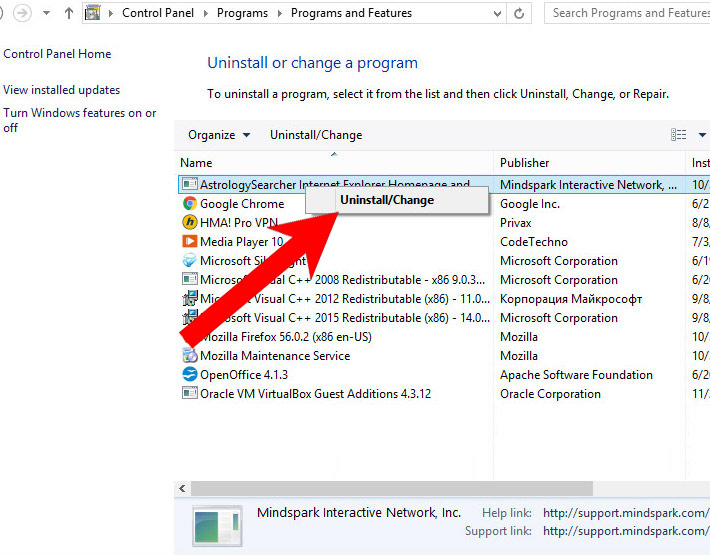
- Find the program you want to delete and press Uninstall.

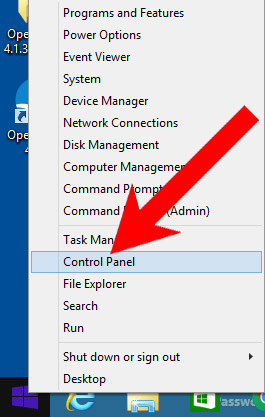
b) Windows 8
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

c) Windows 10
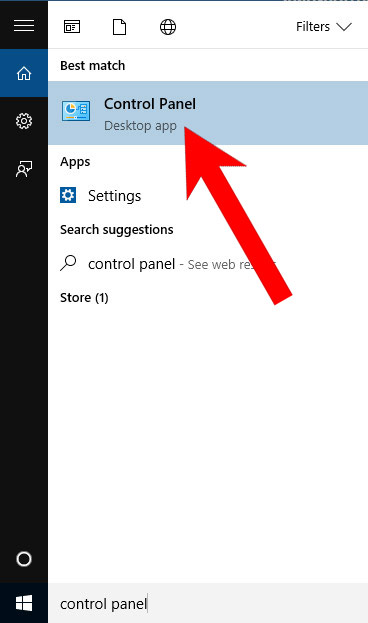
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

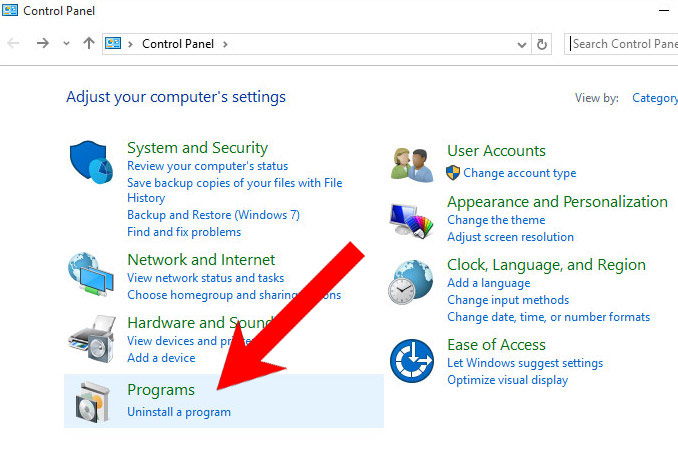
- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

d) Mac OS X
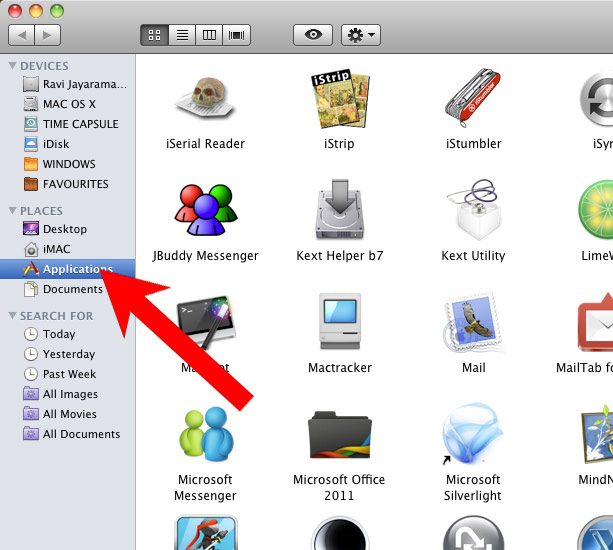
- Open Finder and press Applications.

- Check all suspicious programs you want to get rid of.
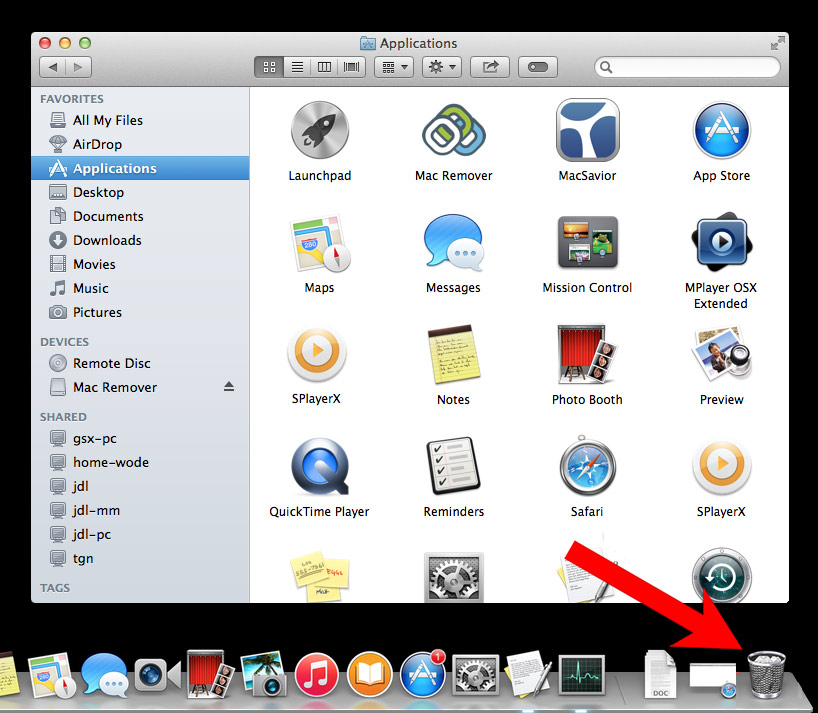
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete Configure from browsers
a) Remove Configure from Microsoft Edge
Reset Microsoft Edge (Method 1)
- Open Microsoft Edge.
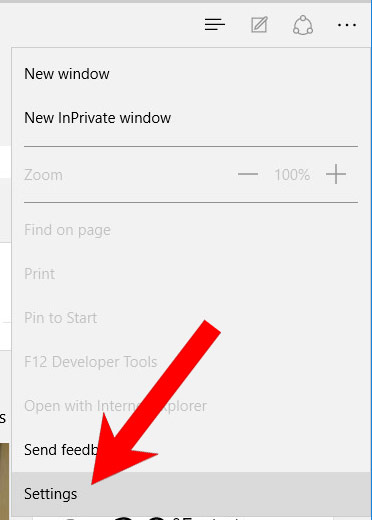
- Press More located at the top right corner of the screen (the three dots).

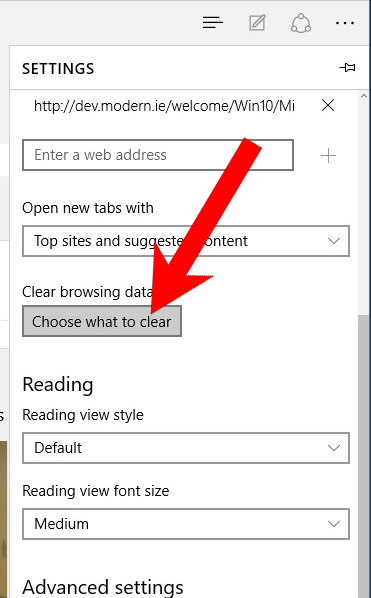
- Settings → Choose what to clear.

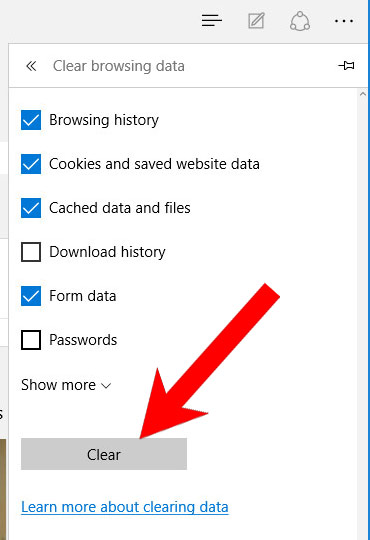
- Check the boxes of the items you want removed, and press Clear.

- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
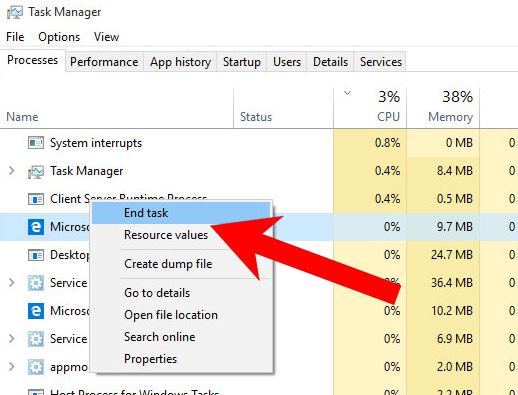
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
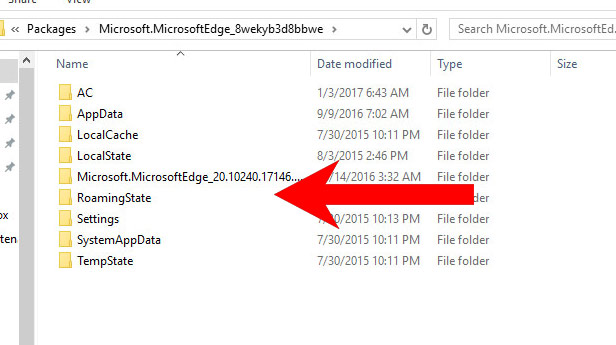
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

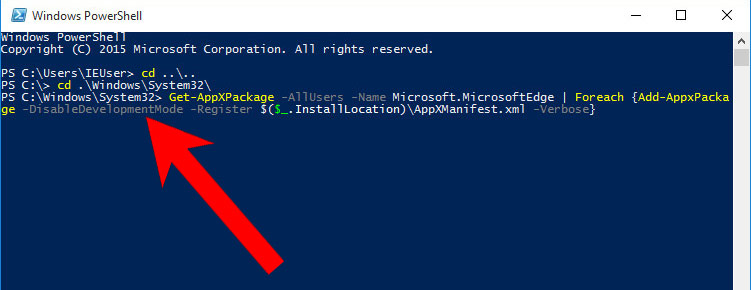
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
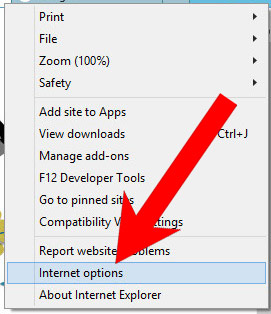
b) Remove Configure from Internet Explorer
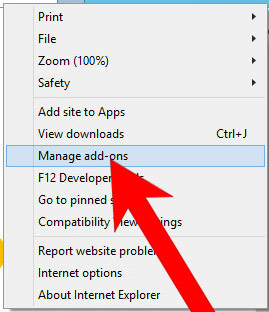
- Open Internet Explorer and press on the Gear icon.

- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
c) Restore your homepage on Internet Explorer
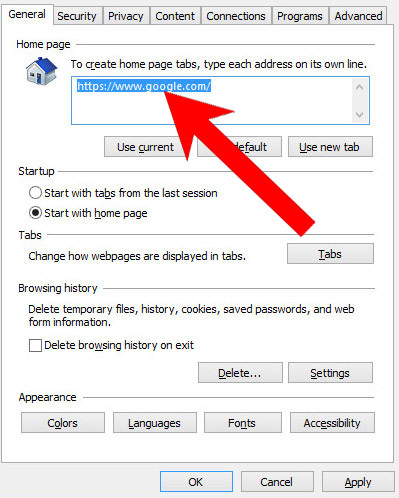
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
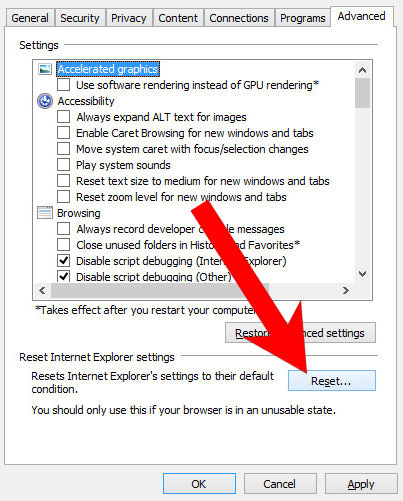
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

- At the bottom, you will see a Reset button. Press that.
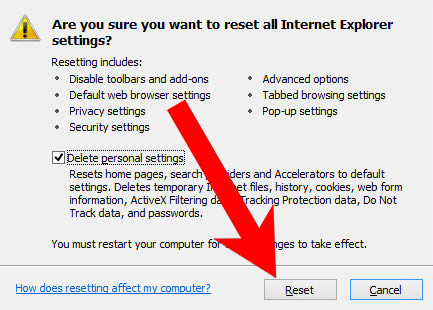
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
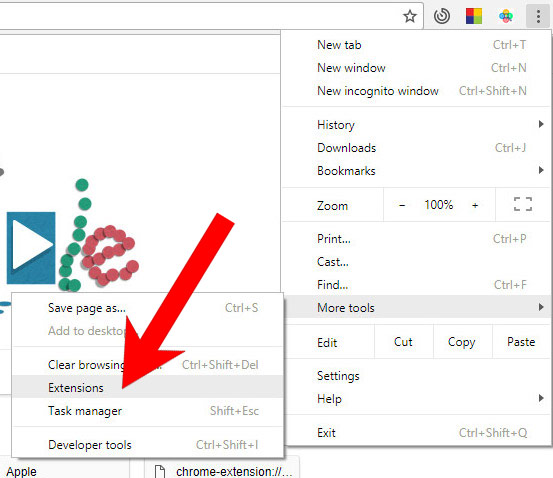
e) Remove Configure from Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
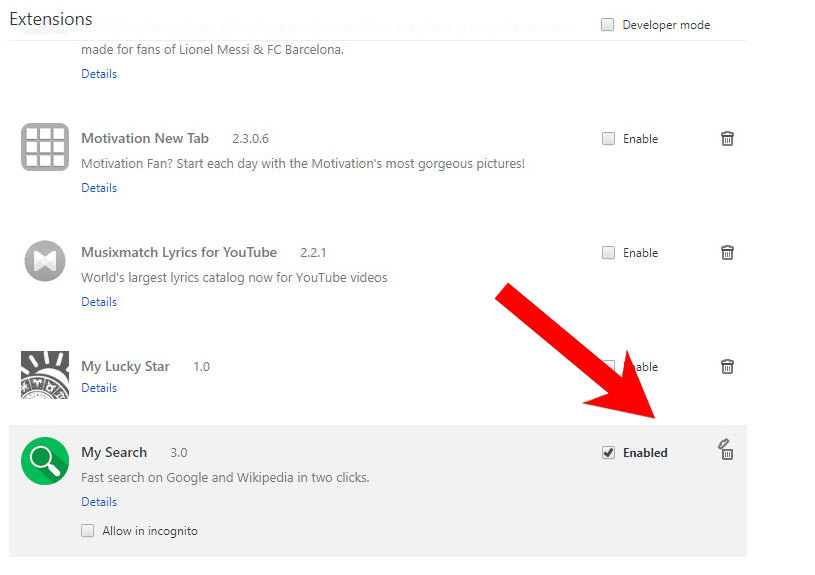
- Choose More tools and Extensions.

- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
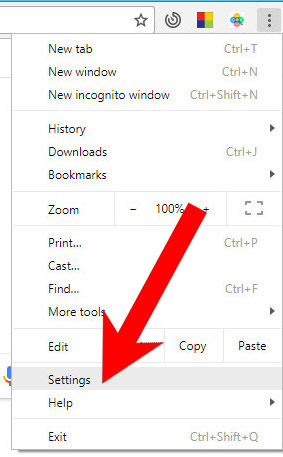
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

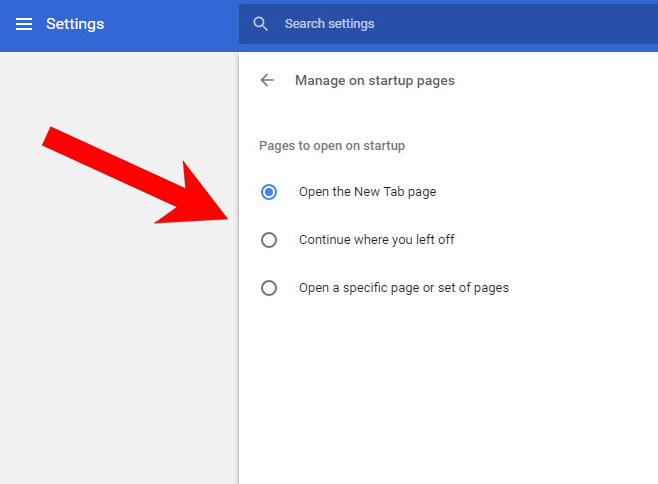
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

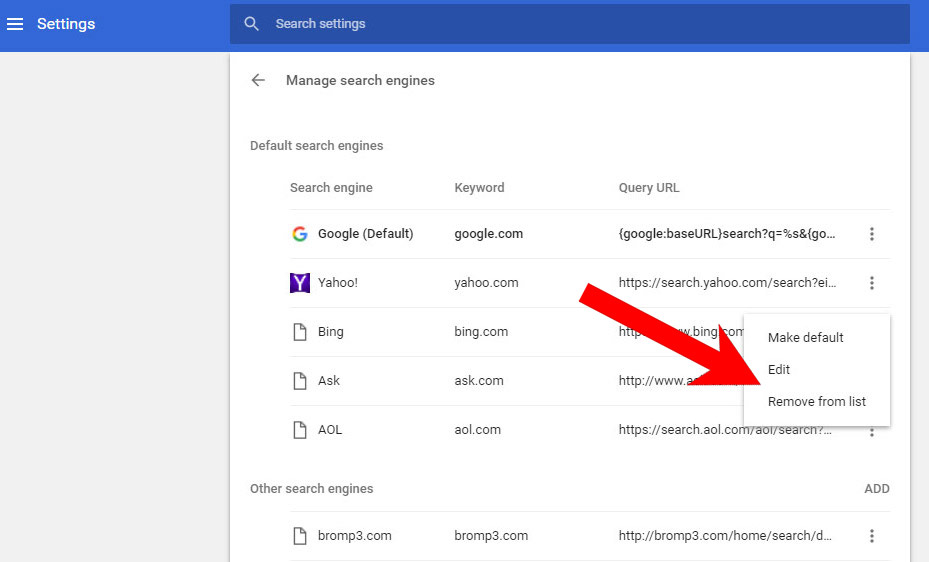
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

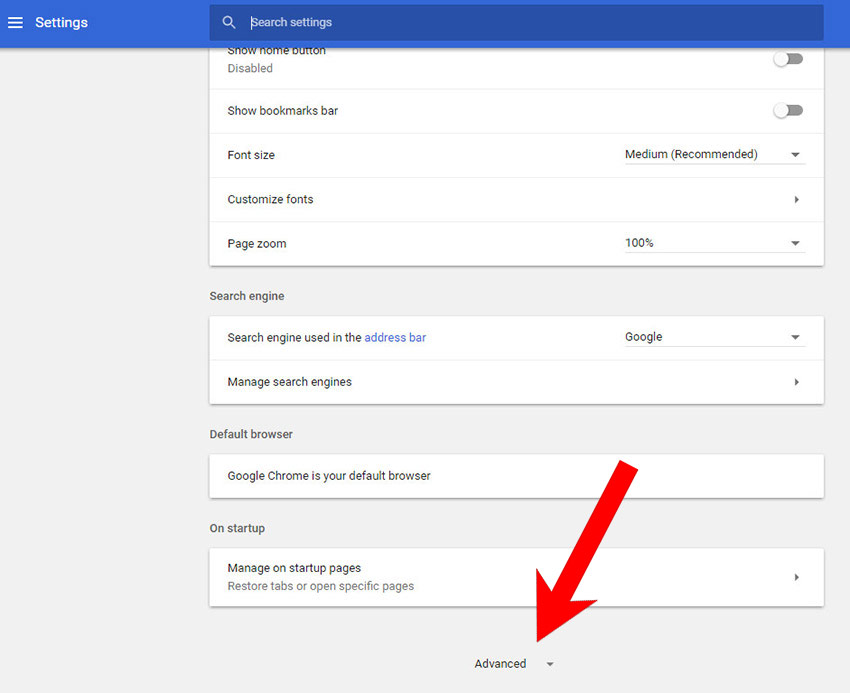
- Scroll down and press on Show advanced settings.

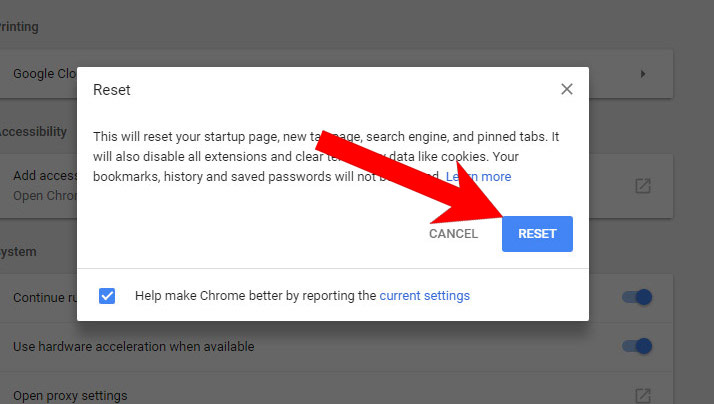
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
h) Remove Configure from Mozilla Firefox
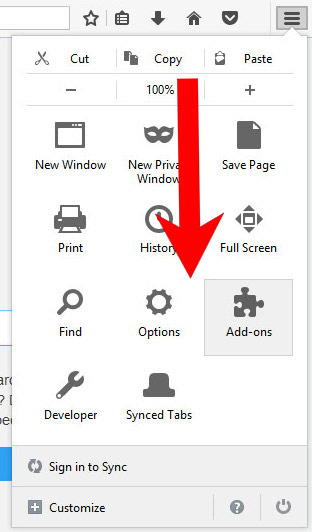
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Select Add-ons.

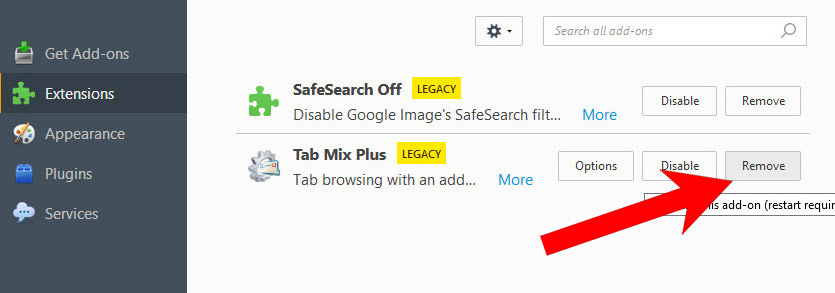
- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
i) Restore your homepage on Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
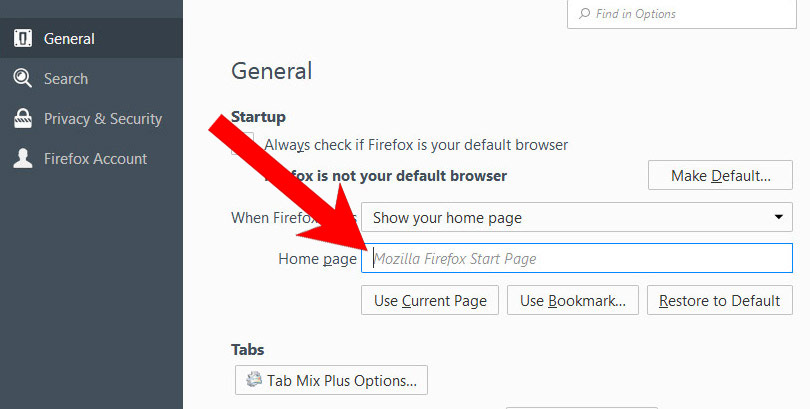
- Select Options.

- In General, click Restore to Default below the Home Page field.

j) Reset Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
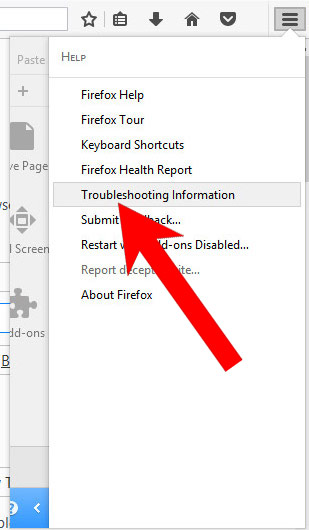
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

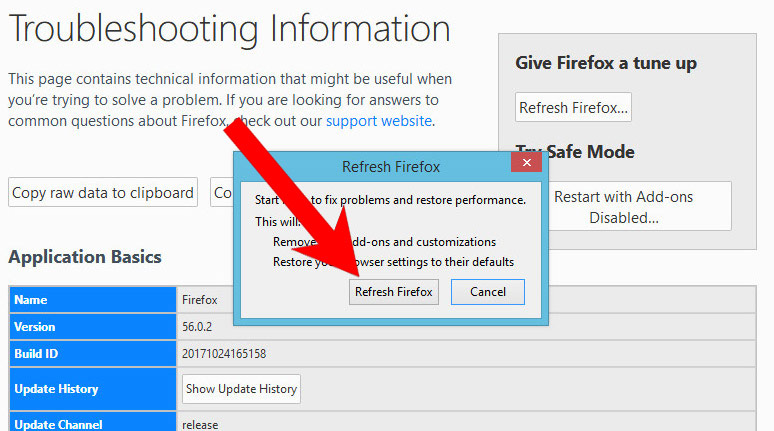
- Select the Refresh Firefox option.

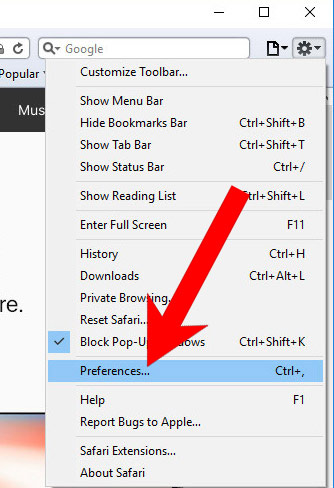
k) Remove Configure from Safari (for Mac)
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

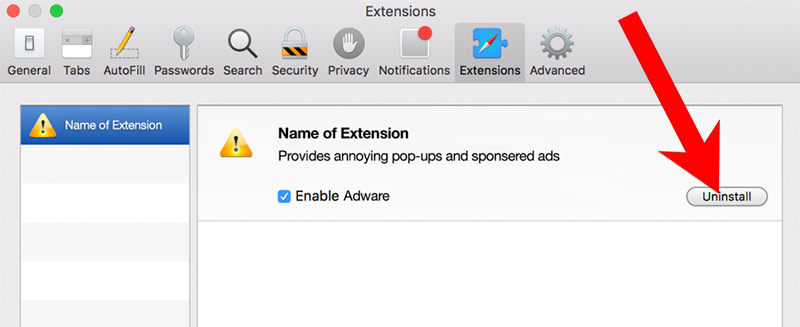
- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
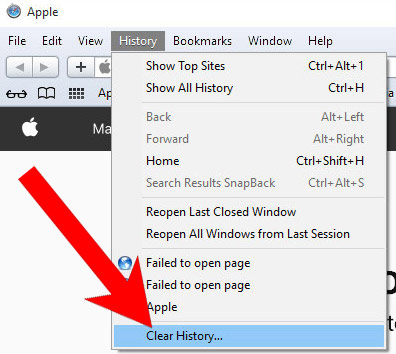
l) Reset Safari
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
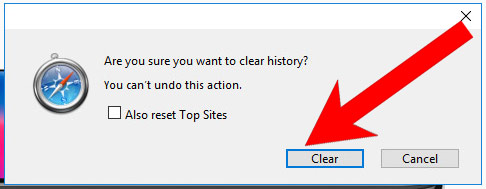
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

- Press on Safari at the top of the screen and select Preferences.

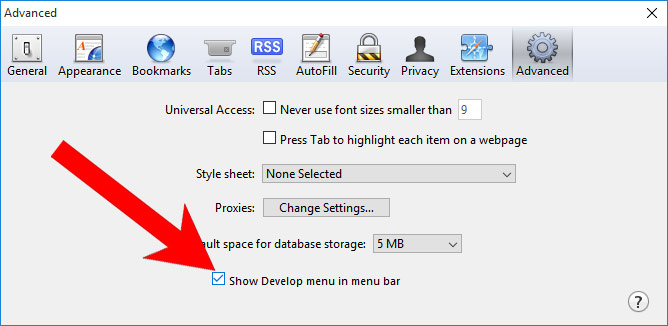
- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
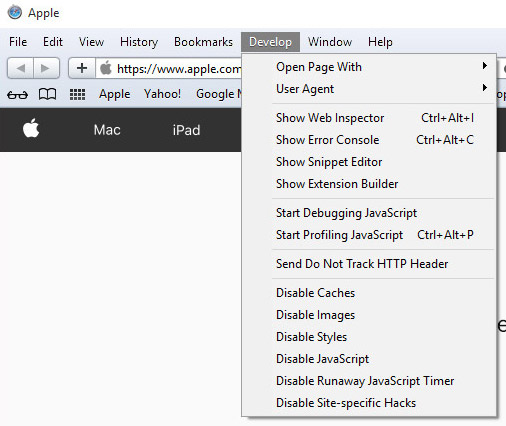
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.