What is Atuct Application?
Atuct Application represents a peril inside the Trojan horse family, able to bring about chaos to your device and information. This malicious application generally believes the role of a digital operational, filching your personal information, passwords, and personal details, afterwards transmitting it to remote servers below the command of cybercriminals. Additionally, it might create hiding gateways for other malicious applications to get in, rendering your operating system very susceptible to assaults. Envision leaving your residence unsafe, similar to an open invitation to attackers. An valuable item, that should be noted before you make a decision how to manage the Atuct Application is its stealthiness. In a lot of the instances, it is quite complex to thoroughly regard Atuct Application by merely searching at likely indications. The argument is, the Trojan attempts to stay concealed for whilst possible so as to serve the criminal requires of its authors. That’s why, generally, it could appear like a utterly legit operating system log which can not be distinguished without the support of good antivirus program program.
Download Removal Toolto remove Atuct Application
Is Atuct Application a malware?
Distinguishing between a Trojan horse, e.g Atuct Application, and a conventional os malicious software can pose a challenge, but necessary distinctions exist to analyze. For example, Trojans repeatedly disguise on their own as benign files or programs, so if any concerns originate connected to a obtained piece, it’s sensible to exert prudence. Furthermore, Trojans generally operate secretly, staying away from the most frequent symptoms related to infections, like os sluggishness or crashes. Consequently, users ought to stay diligent for odd events, for example sudden pop-ups or forbidden access onto their files. Lastly, if the system shows unusual behavior, e.g unanticipated crashes or the initiation of applications without your permission or awareness, this highly advises the process of a Trojan like Atuct Application in the background.
The Atuct Application Virus
A very specific characteristic of the Trojan Horses is their unmatched versatility. Unlike the biggest number of of the system infections which are programmed to implement a single damaging chore, dangers for example the Atuct Application malware might begin a load of various criminal actions one after the other. They may also generally be re-programmed on the go to serve other malicious functions. That’s why the Atuct Application malicious software is clearly not probable for us to explain what precisely to anticipate from such malware and what kind of harm they can bring about to you and to the other victims. Below, we shall classification merely some of the most frequent employs of the representatives of the Trojan Horse classification, but you need to remember that there may be other malignant effects, which might be not noted here.
Generally, it is completely up to the crooks to determine how to implement their contaminated invention and what criminal deeds to do together with its assistance, but here are some of the most possible utilizes:
Download Removal Toolto remove Atuct Application- A os invader – one of such the biggest number of frequent things that a Trojan horse can do the moment it enters the pc is to malicious vital system files, predicament in addition to the installed programs and set some changes that may serve the hackers’ criminal agenda. Such motions might bring about routine untrustworthiness of the operating system, surprising crashes, pc glitches, relevant lethargic-down of the efficiency or harsher – a total computer corruption, which might depict the infiltrated os useless.
- A transmitter of other malware – Apart from hurting the os straightaway, greatly generally, the Trojan horse may be programmed to inject other infections into the corrupted pc. The security experts warn that an infection such as Atuct Application could operate as a backdoor for other common threats such as Ransomware, Banking Malware, Spyware or Rootkits and help them sneak inside the system undetected.
- A software for tailing – in certain situations, the criminals controlling the Trojan might not be curious about contaminating your computer and can instead be striving to tail you. They may assemble personal information connected to your confidential or efficient life, your whereabouts, your home and all the movements that you carry out from the contaminated machine. Together with all this information, they may easily harass you in a bunch of techniques.
AtuctApplication
Those of you who find it difficult to deal with AtuctApplication manually and are not sure which the actual malicious files and processes that need to be deleted are, are advised to not experiment with their malware-removal skills. It is more reliable for them to analyze their machine with the decent elimination tool for automatic aid, which is added to the guidelines in order to dodge unintended operating system damage.Because of its stealthy roots and highly damaging behavior, the most productive way to catch and delete the Trojan horse from the machine is to scan the computer with a legitimate defense application. If you don’t have such a tool or it has been stopped by the infections, you could attempt to use the specialist AtuctApplication elimination program on this site and join it with the by hand guidance in the uninstallation instruction to make sure that you have efficiently dealt with this issue.
Learn how to remove Atuct Application from your computer
Step 1. Atuct Application Removal from Windows
a) Windows 7/XP
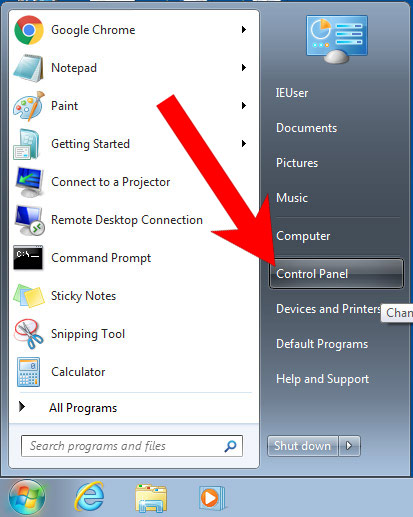
- Press on the Start icon.

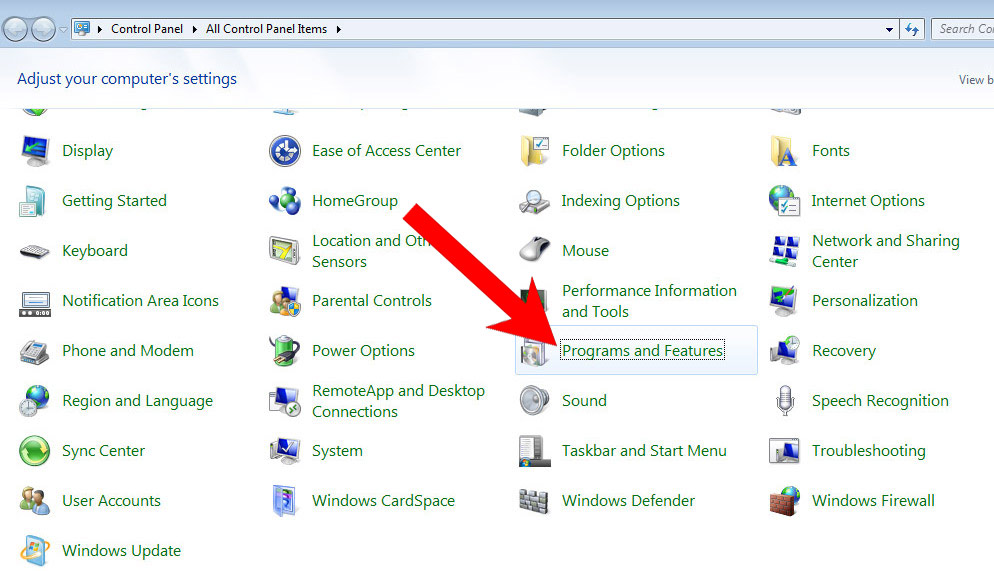
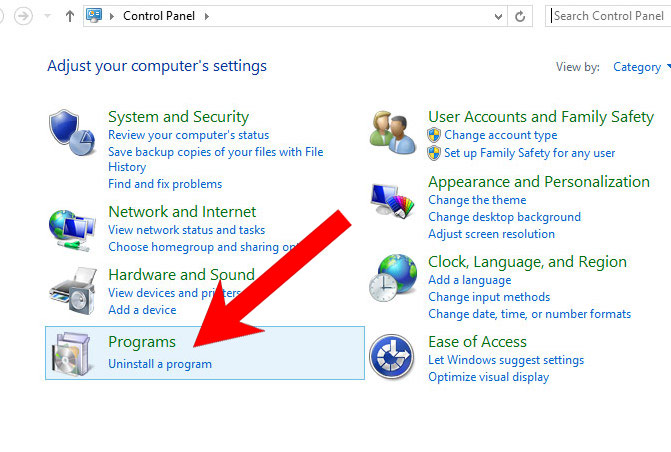
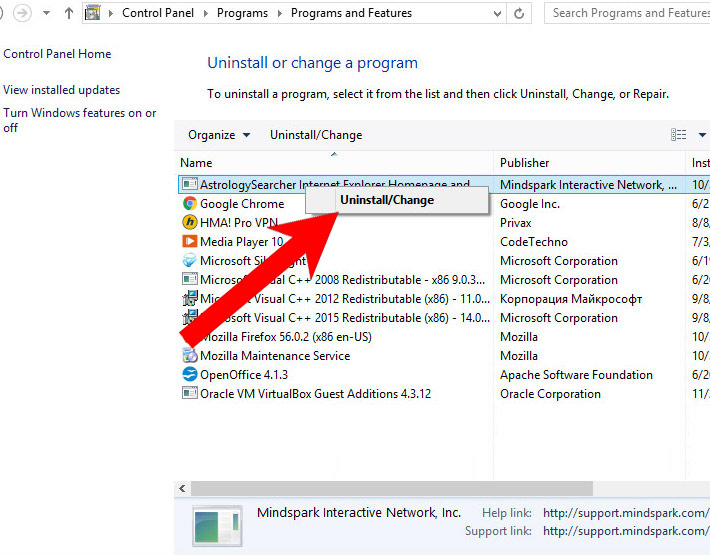
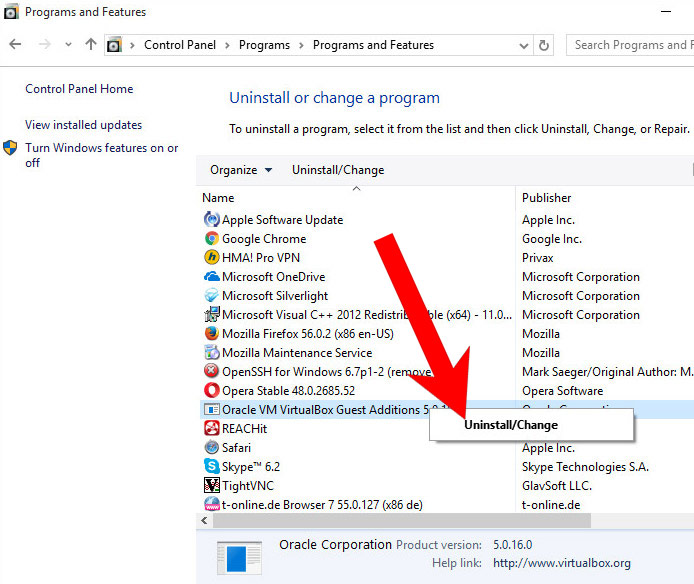
- Control Panel → Programs and Features.

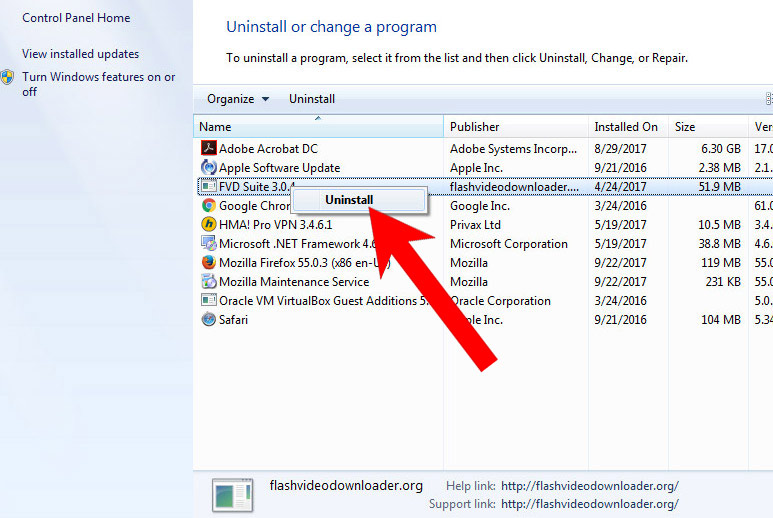
- Find the program you want to delete and press Uninstall.

b) Windows 8
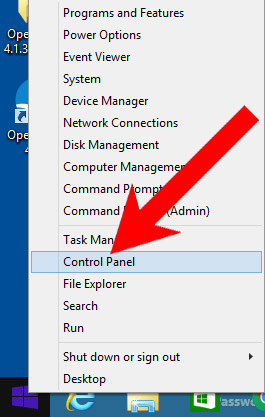
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

c) Windows 10
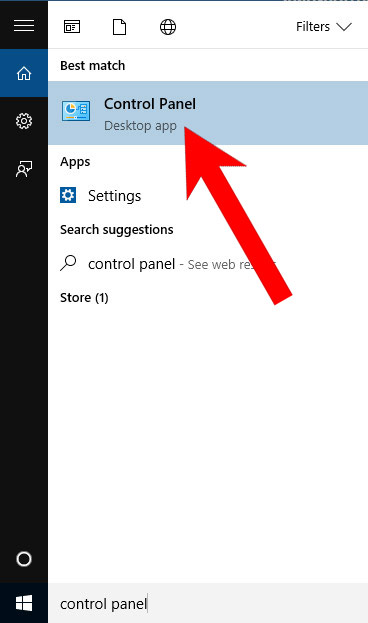
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

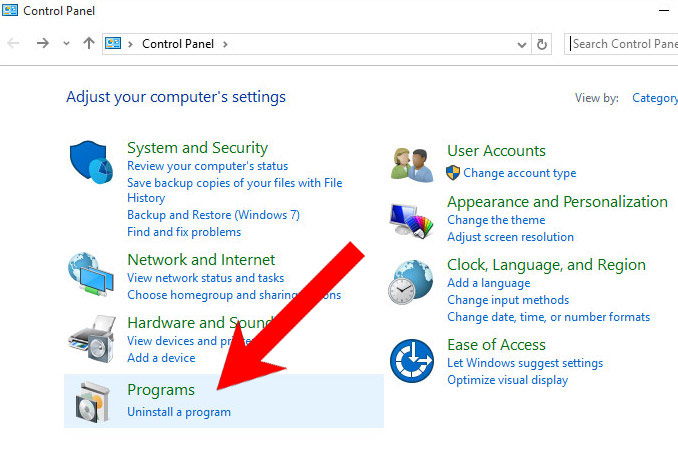
- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

d) Mac OS X
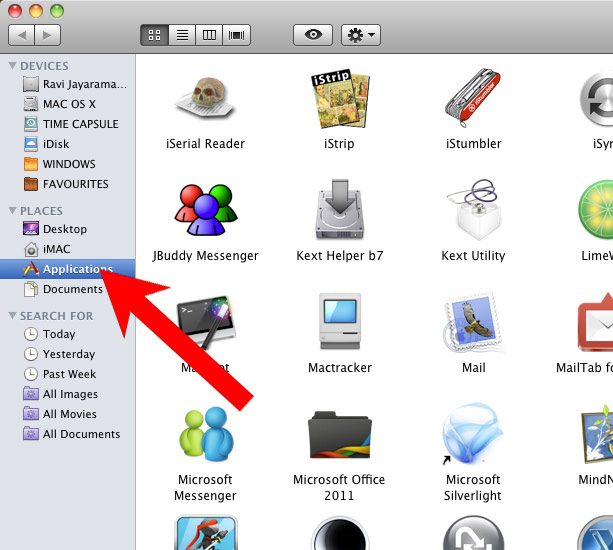
- Open Finder and press Applications.

- Check all suspicious programs you want to get rid of.
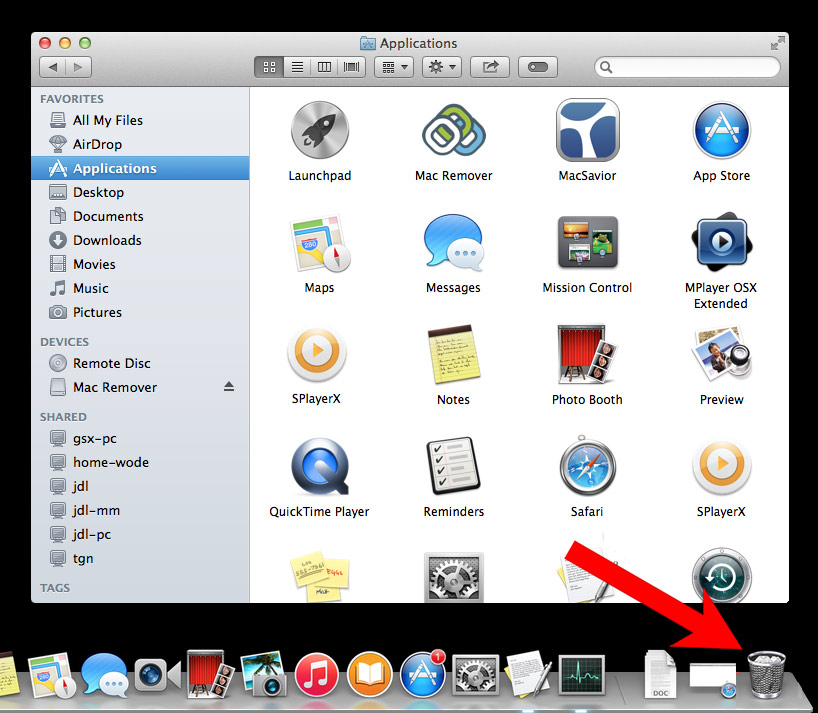
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete Atuct Application from browsers
a) Remove Atuct Application from Microsoft Edge
Reset Microsoft Edge (Method 1)
- Open Microsoft Edge.
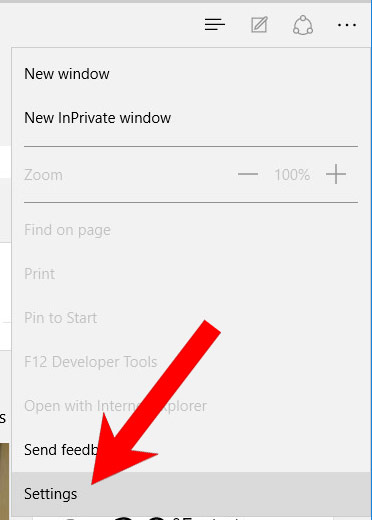
- Press More located at the top right corner of the screen (the three dots).

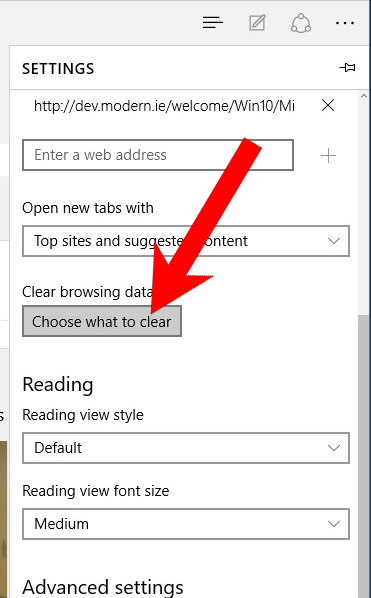
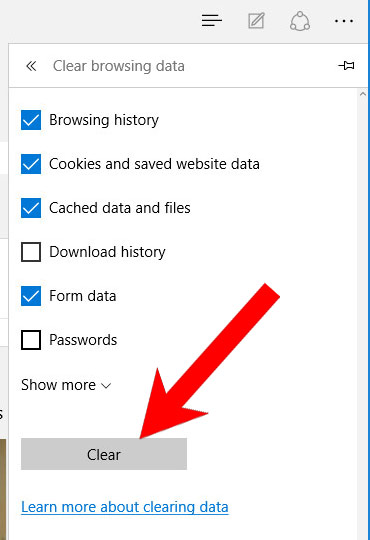
- Settings → Choose what to clear.

- Check the boxes of the items you want removed, and press Clear.

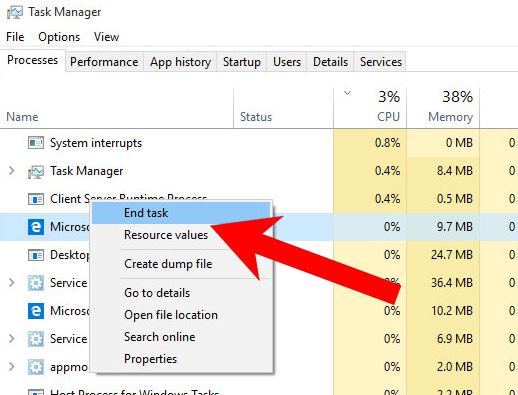
- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
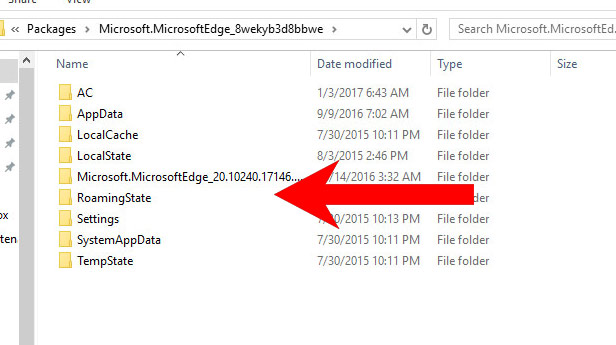
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

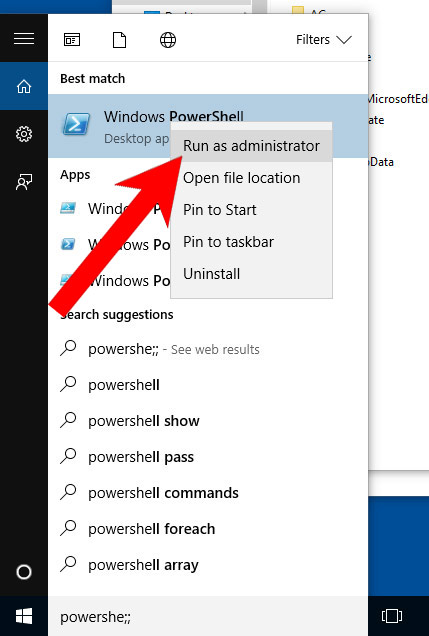
- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

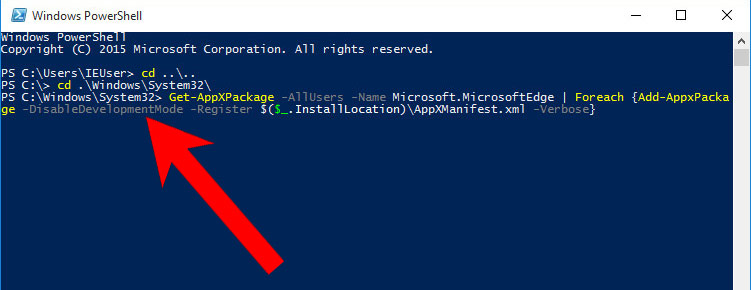
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
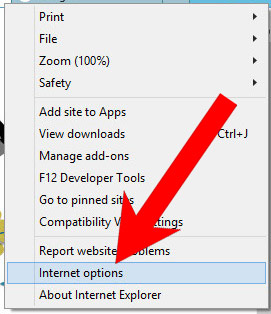
b) Remove Atuct Application from Internet Explorer
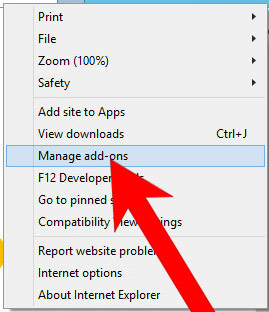
- Open Internet Explorer and press on the Gear icon.

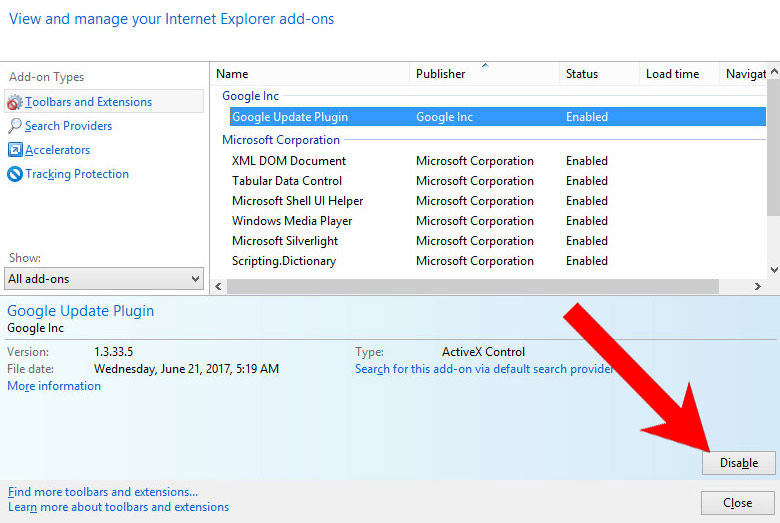
- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
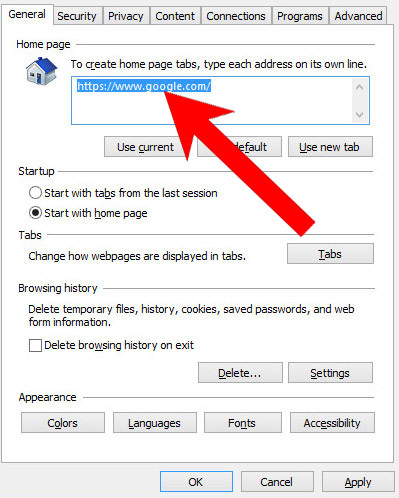
c) Restore your homepage on Internet Explorer
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
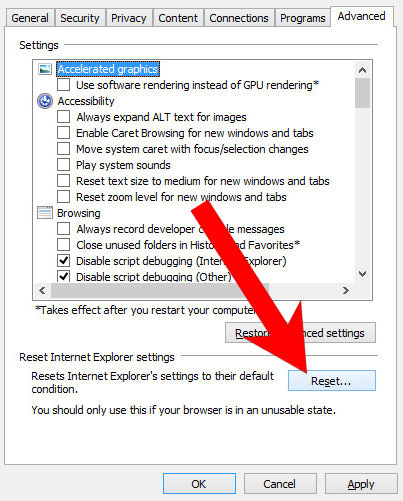
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

- At the bottom, you will see a Reset button. Press that.
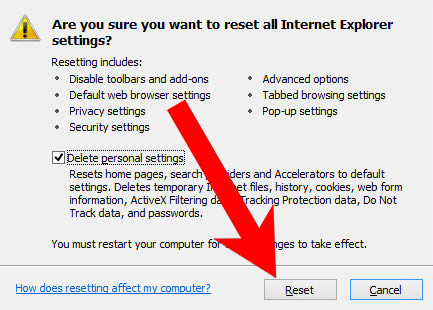
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
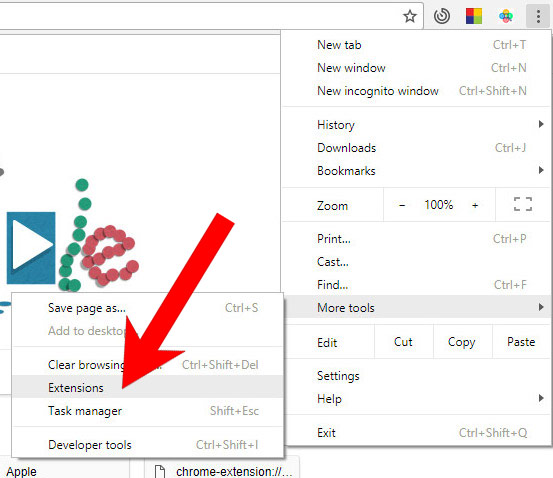
e) Remove Atuct Application from Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
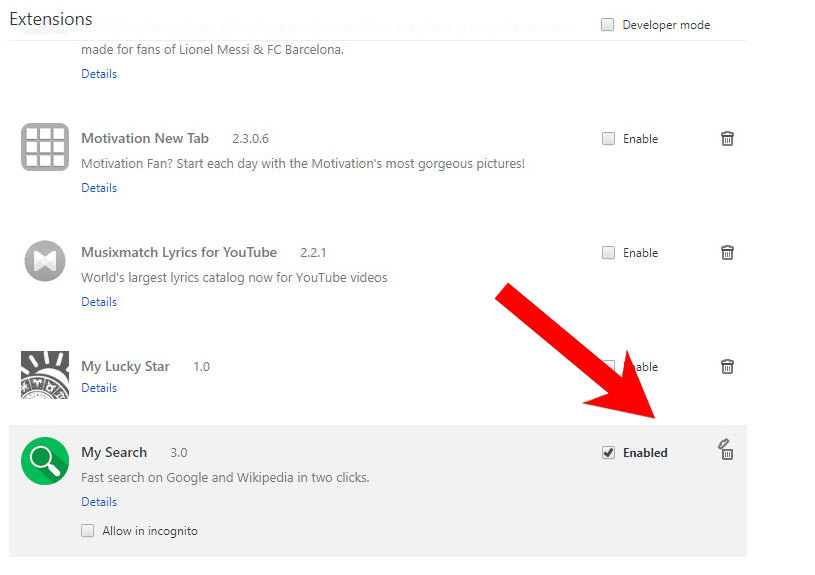
- Choose More tools and Extensions.

- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
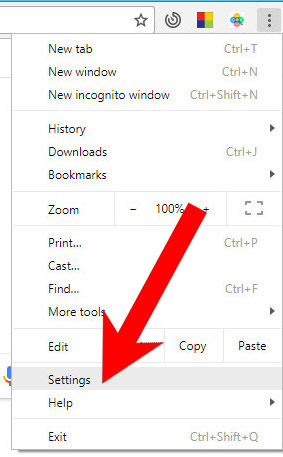
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

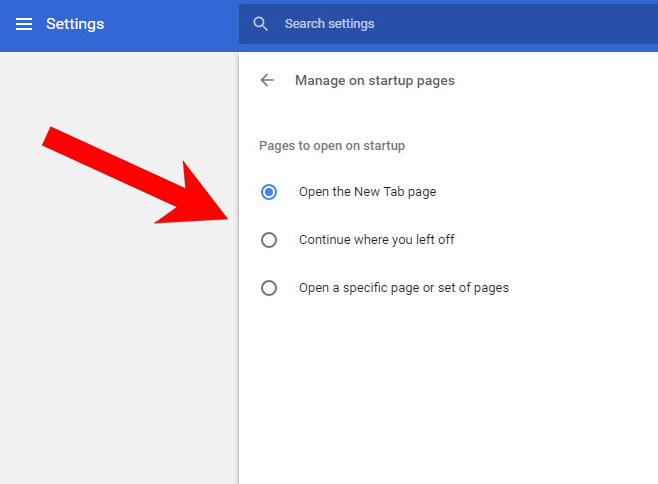
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

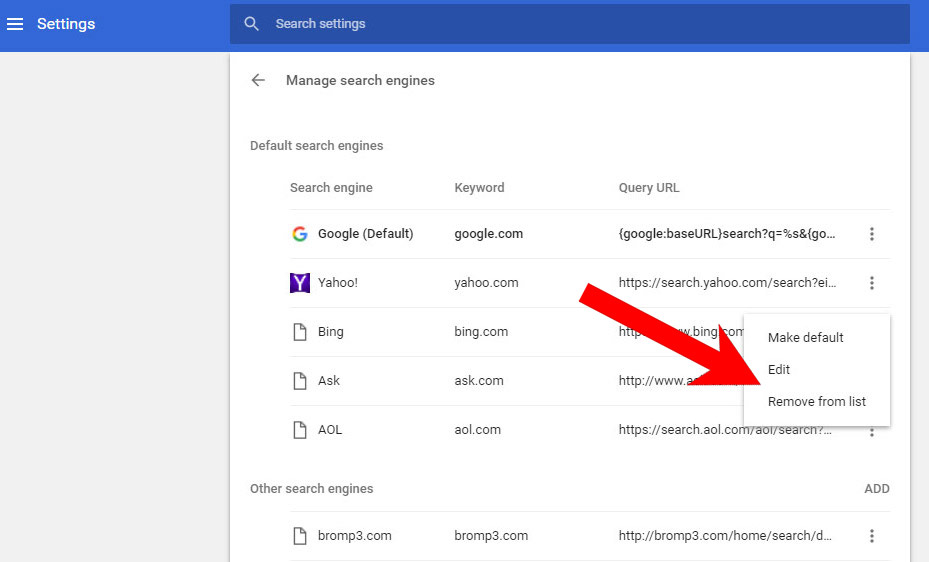
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

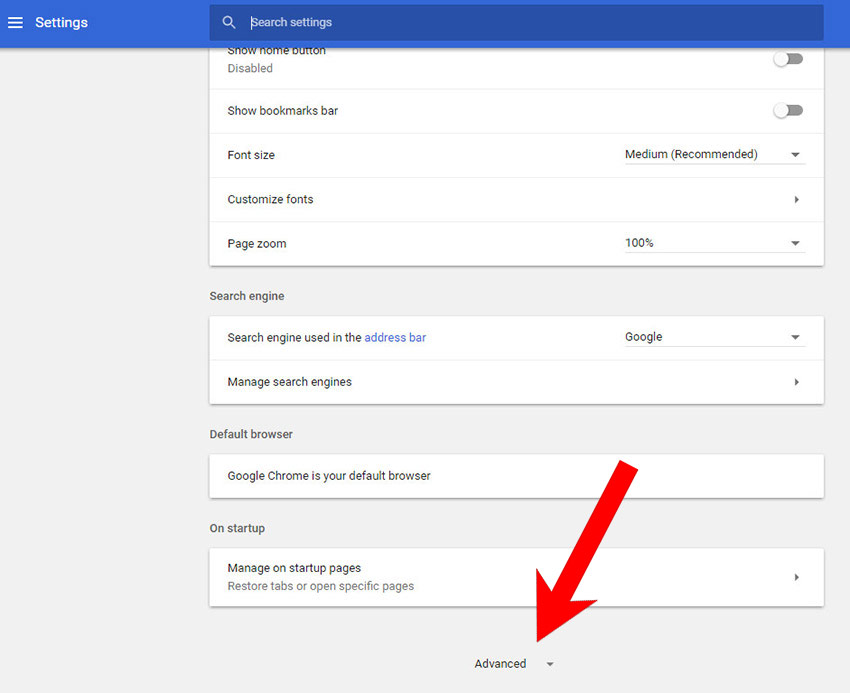
- Scroll down and press on Show advanced settings.

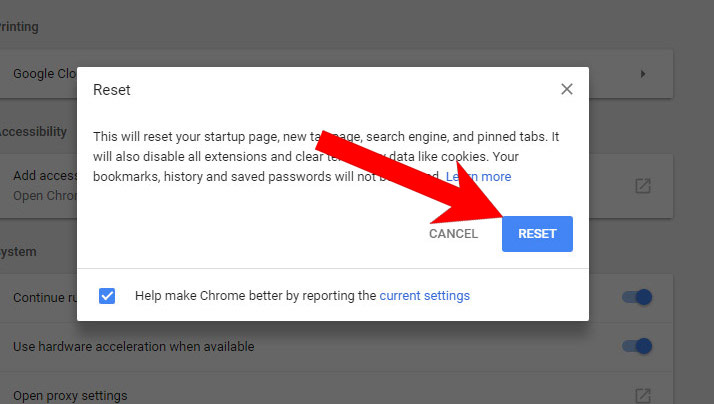
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
h) Remove Atuct Application from Mozilla Firefox
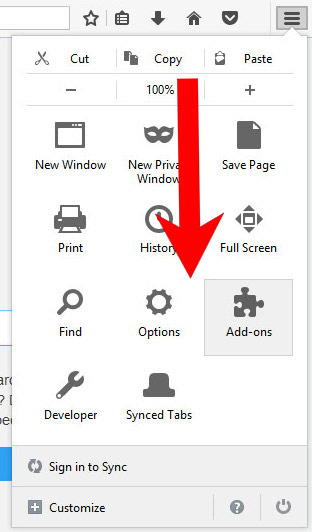
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
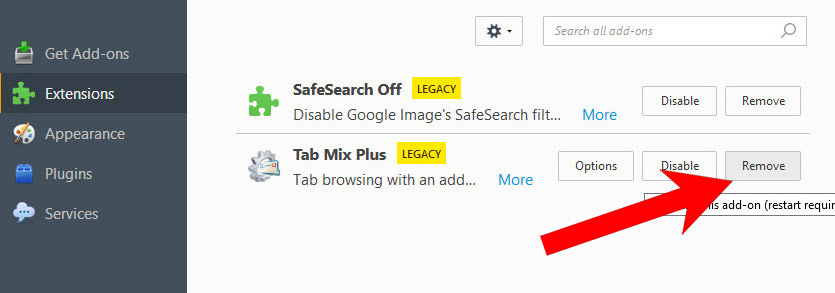
- Select Add-ons.

- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
i) Restore your homepage on Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
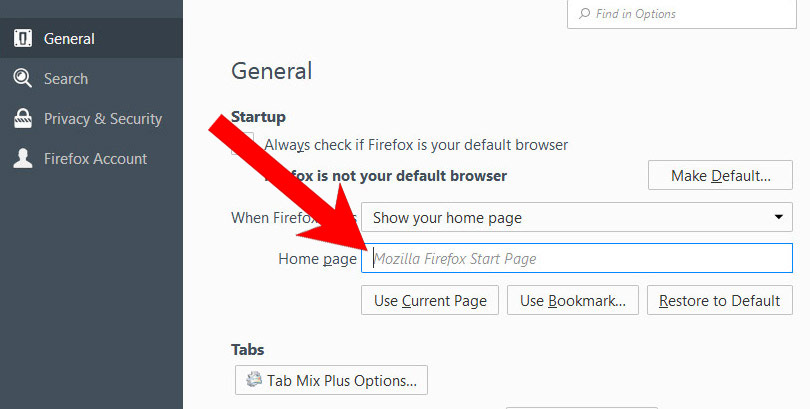
- Select Options.

- In General, click Restore to Default below the Home Page field.

j) Reset Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
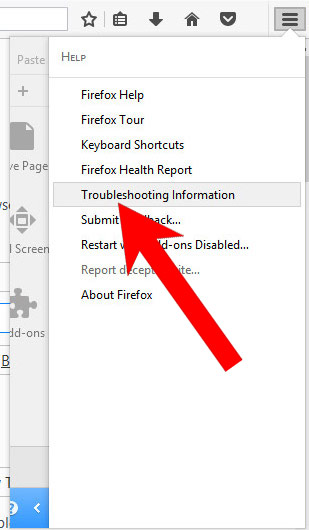
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

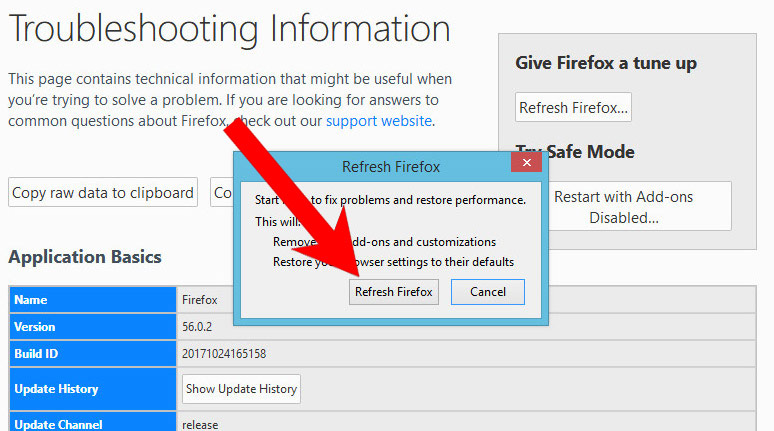
- Select the Refresh Firefox option.

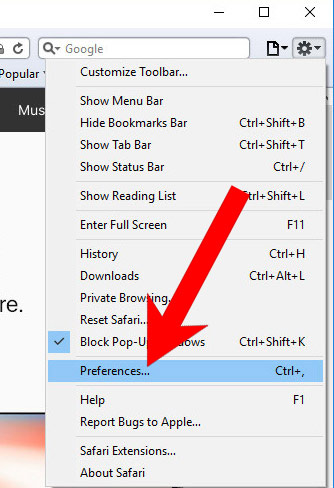
k) Remove Atuct Application from Safari (for Mac)
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

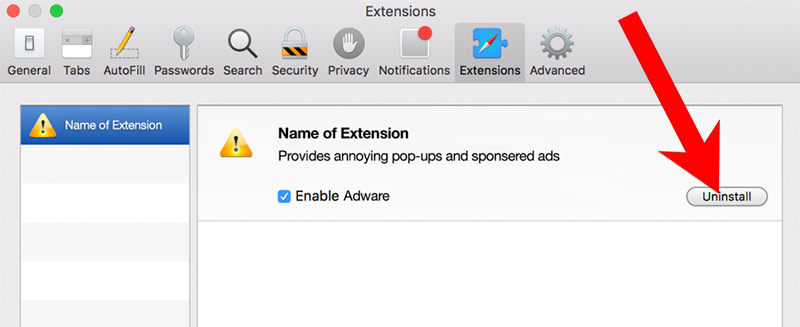
- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
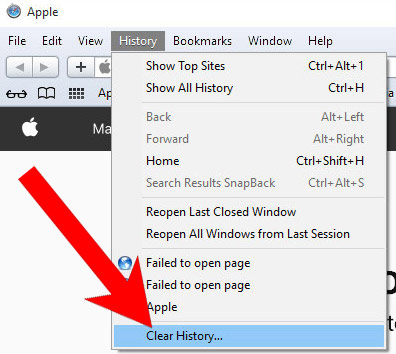
l) Reset Safari
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
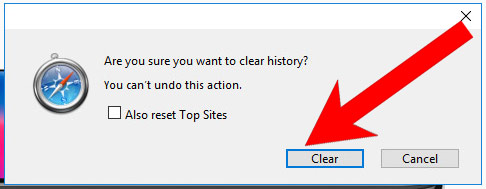
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

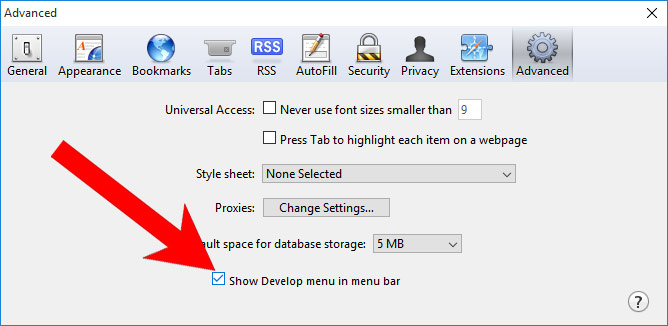
- Press on Safari at the top of the screen and select Preferences.

- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
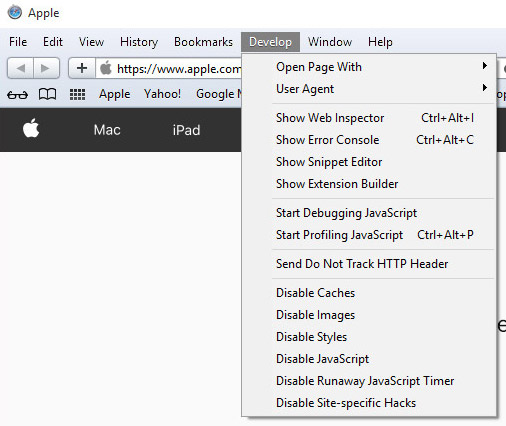
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.