You’ve undoubtedly heard connected to this bad classification of computer contaminations earlier – after all, the Trojan Horses are actually some of the most frequent shapes of malicious viruses, and they are moreover some of the the biggest part of adverse. Below, you will know relating to the stealthy origins of RAV Antivirus, the likely damage it could lead to to your operating system, the things you could do to maintain your computer shielded in the future, and finally, the way you may uninstall the Trojan from your machine whether it’s earlier in there.
RAVAntivirus
If RAVAntivirus is presently in your system, know that the consequences of its attack may vary depending on each instance. RAVAntivirus may be used differently, and it could be tasked together with various malicious movements.
For example, some such issues might be implemented to surreptitiously tail you, despite the fact that in other situations a Trojan could try to backdoor supplementary parasite onto your computer (Ransomware is normally spread together with Trojan Horse backdoors). A infection like RAV Antivirus should also be tasked alongside giving remote custody of your pc to the cyber criminals behind the threat breach. In regular, the faster you erase the threat the wiser – don’t delay for the result of the breach to get exhibited, and instead ensure to implement the guide from underneath promptly to delete the malware.
Download Removal Toolto remove AntivirusThe Trojan Horses are highly surreptitious parasite malicious software
A classic characteristic of viruses like RAV Antivirus, incredible detect, Walliant is their stealthiness – a majority of people don’t even figure out when or how an breach by a Trojan has took place. This is mostly attributed to the masquerade methods employed by a majority of Trojan Horses. To slither into your os, the biggest number of such risks need some arrangement of interaction from your side – generally this implies that the infections demands you to open its document, and offer it an Administrative consent to make alterations in the computer. Of course, nobody would knowingly do that if they be aware that the log in question is a Trojan Horse. This is why many Trojans are cleverly camouflaged as other applications – such that people wouldn’t suspect of being malevolent, and may in fact be inclined to engage with. For instance, if the virus is masked as the installer of a software, which software the user seeks, the latter would be more possible to start the invisible malware. Oftentimes, such Trojans camouflaged as the installers of some example of program are discovered on pirate portals where generally someone can upload anything. It’s not hidden that even if its unlawful to download pirated programs, a lot of people that, which, in turn, causes a high quantity of Trojan Horse viruses. Of course, pirate portals aren’t the only probable sources of this class of malware threats. Camouflaged Trojan Horse files may also be spread together with spam on the internet letters, false on the internet ads located on other superficial websites, false social media posts, and etc.. All in all, you should be very cautious on the internet if you do not desire to become a victim of Trojan Horses henceforth.
Learn how to remove Antivirus from your computer
Step 1. Antivirus Removal from Windows
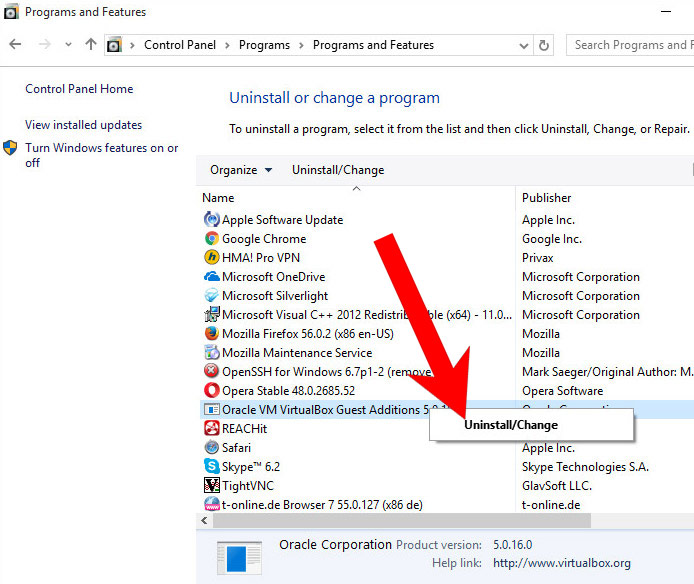
a) Windows 7/XP
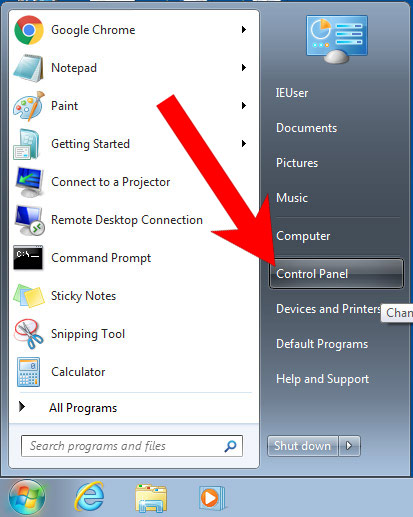
- Press on the Start icon.

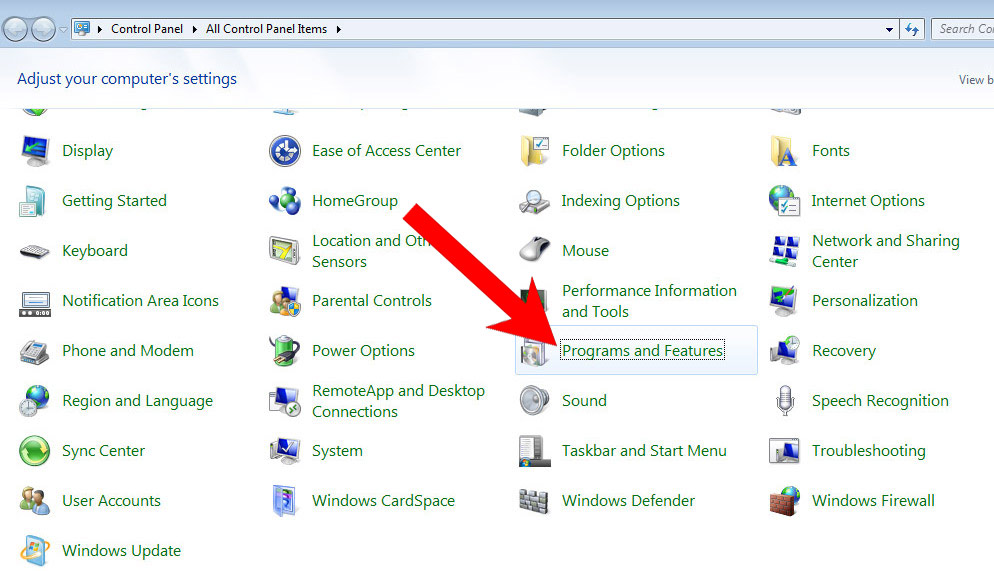
- Control Panel → Programs and Features.

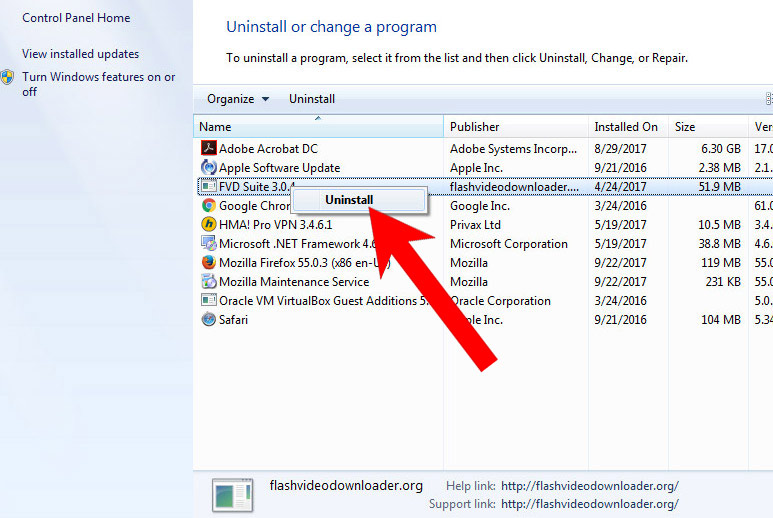
- Find the program you want to delete and press Uninstall.

b) Windows 8
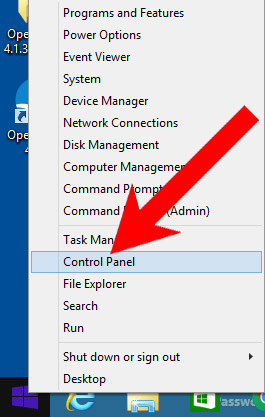
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

c) Windows 10
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

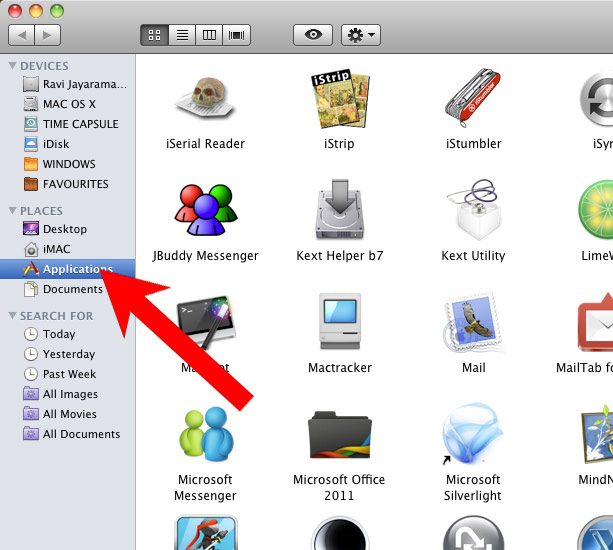
d) Mac OS X
- Open Finder and press Applications.

- Check all suspicious programs you want to get rid of.
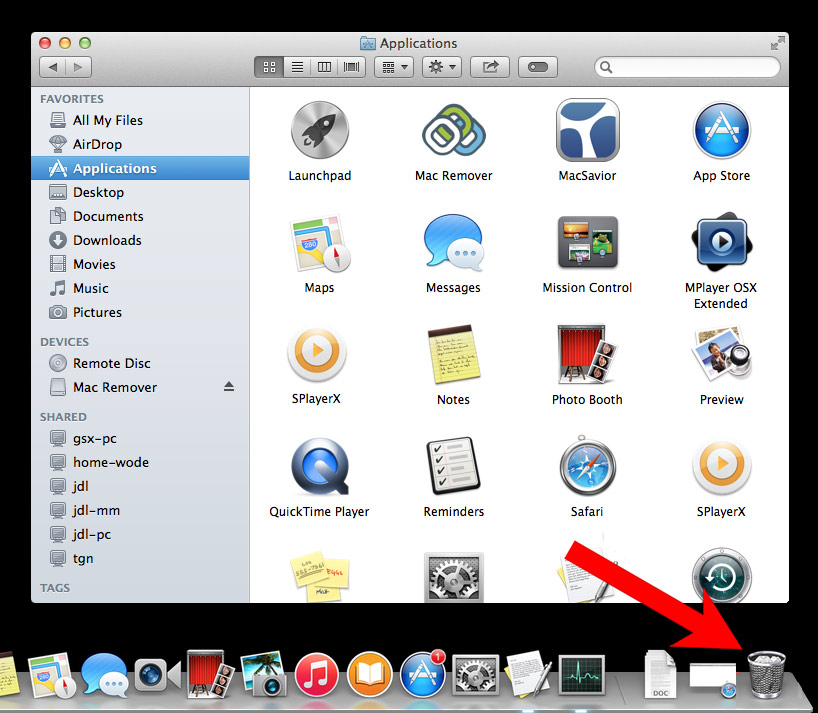
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete Antivirus from browsers
a) Remove Antivirus from Microsoft Edge
Reset Microsoft Edge (Method 1)
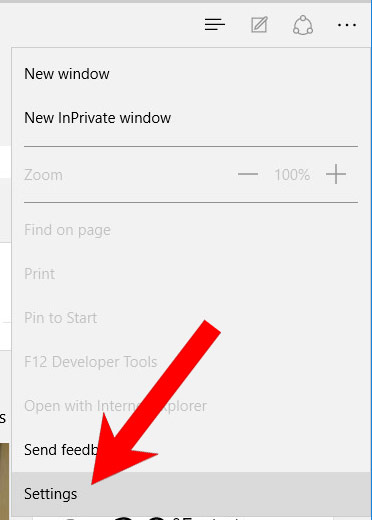
- Open Microsoft Edge.
- Press More located at the top right corner of the screen (the three dots).

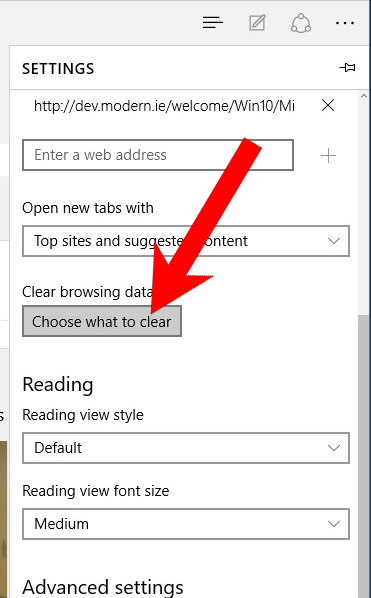
- Settings → Choose what to clear.

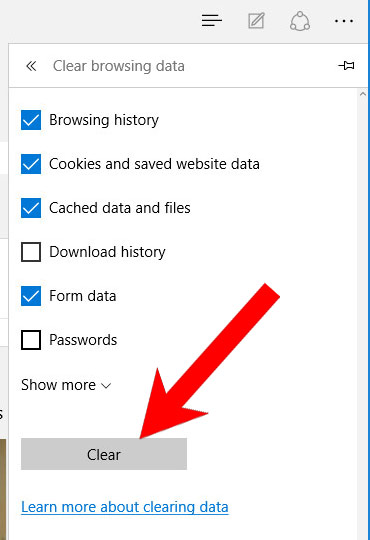
- Check the boxes of the items you want removed, and press Clear.

- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
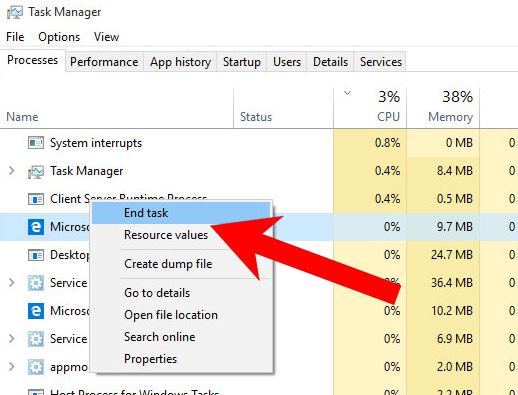
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
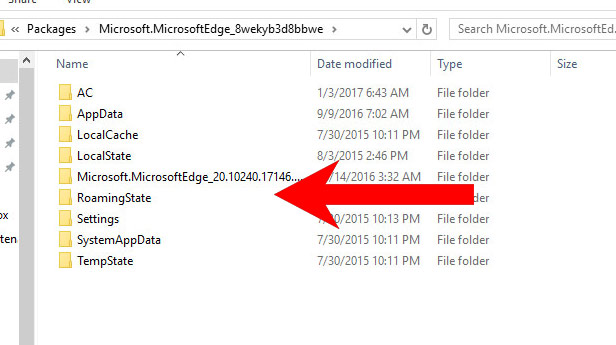
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

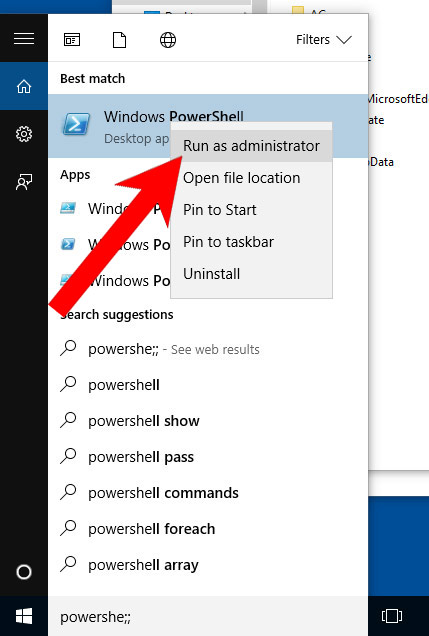
- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

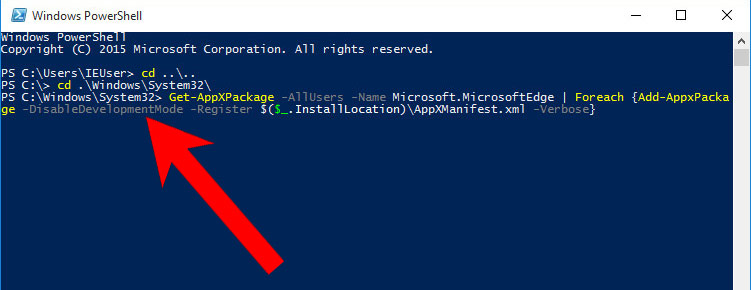
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
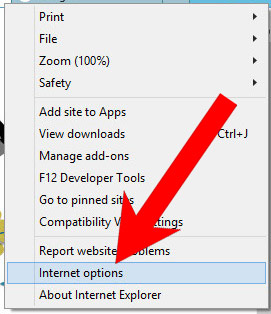
b) Remove Antivirus from Internet Explorer
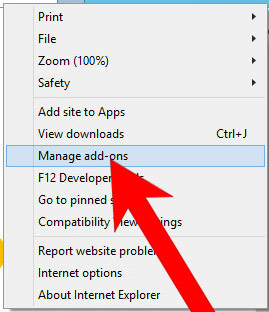
- Open Internet Explorer and press on the Gear icon.

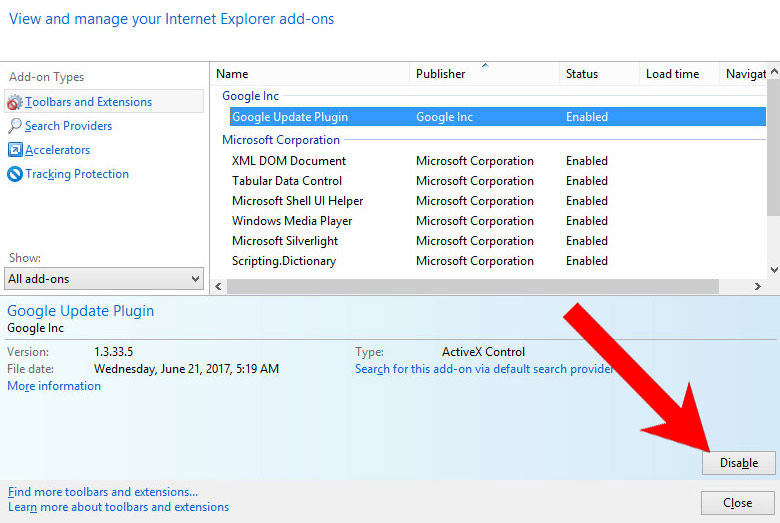
- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
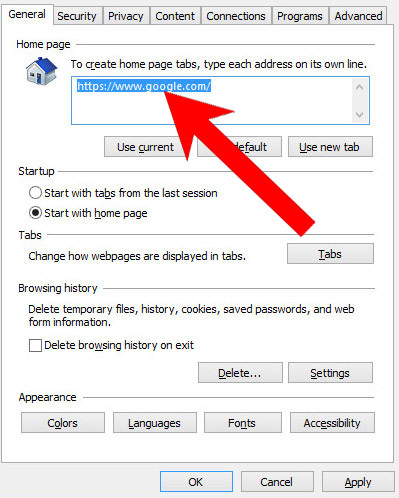
c) Restore your homepage on Internet Explorer
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
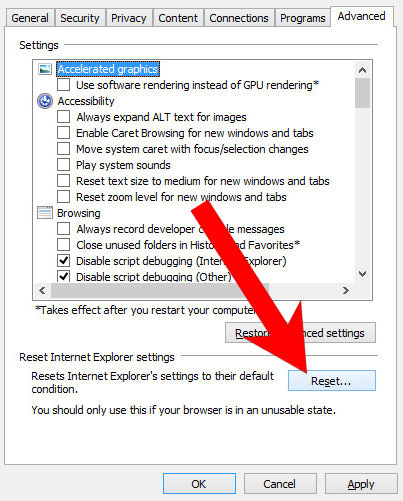
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

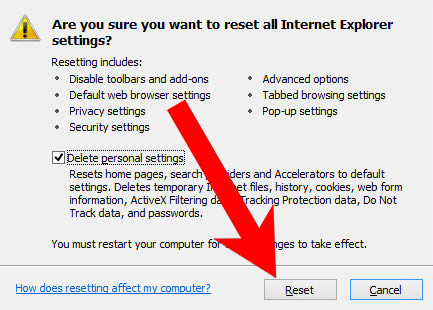
- At the bottom, you will see a Reset button. Press that.
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
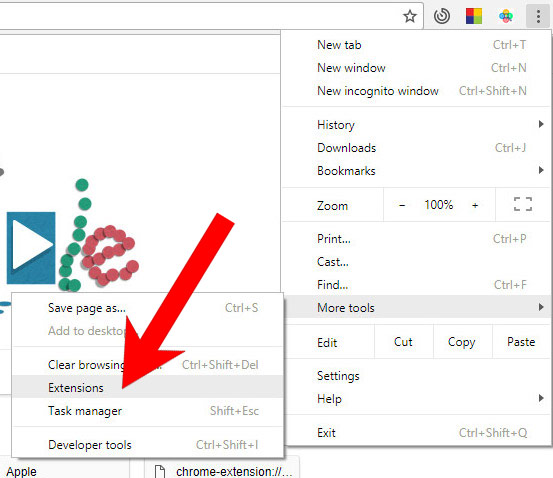
e) Remove Antivirus from Google Chrome
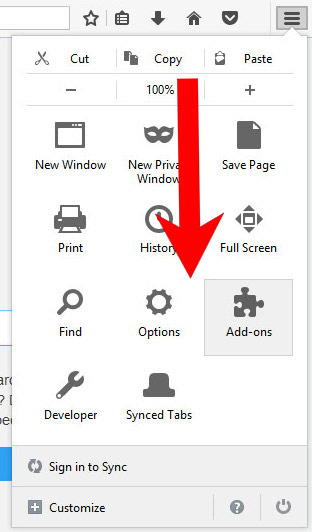
- Open Google Chrome and press the menu icon on the right, next to the URL field.
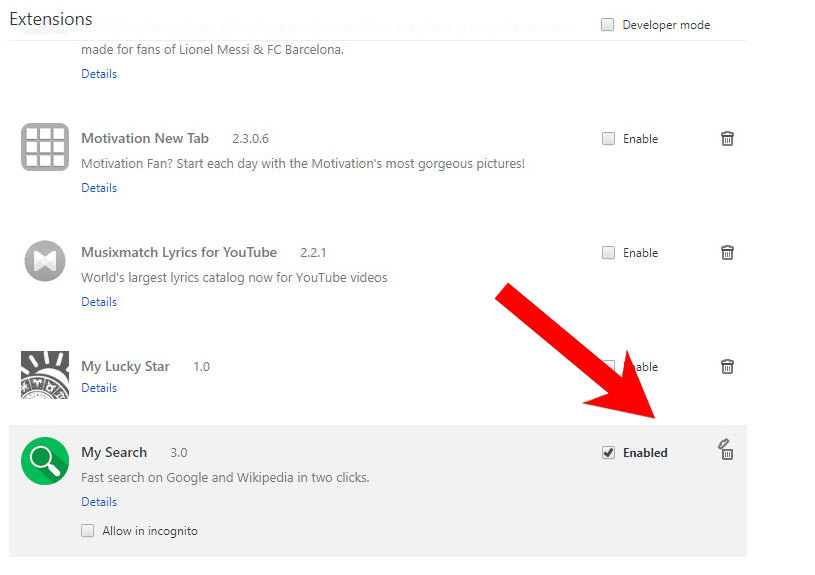
- Choose More tools and Extensions.

- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
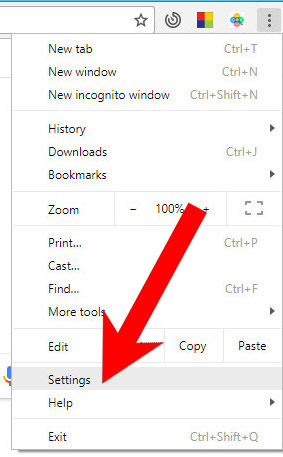
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

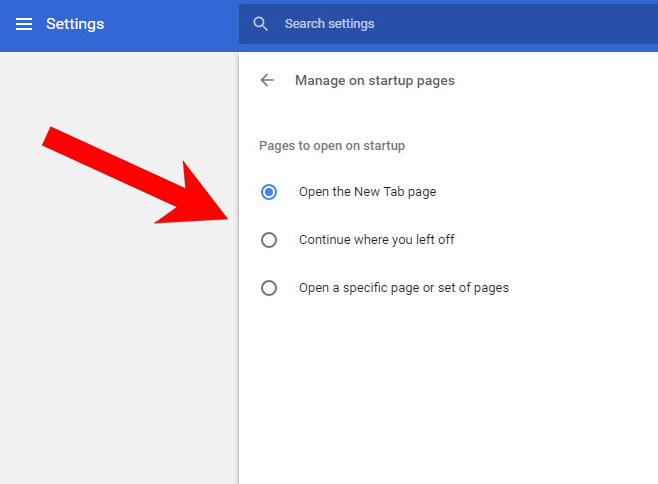
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

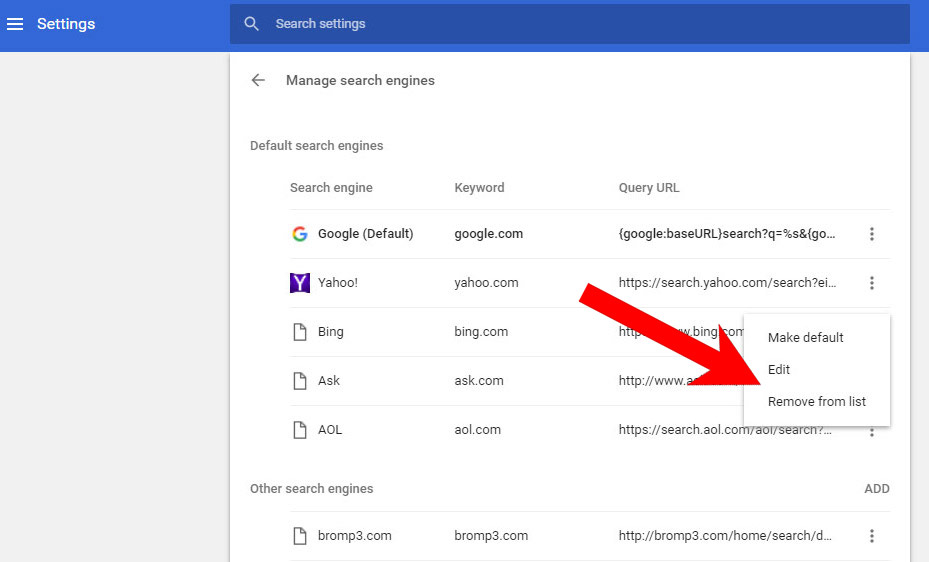
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
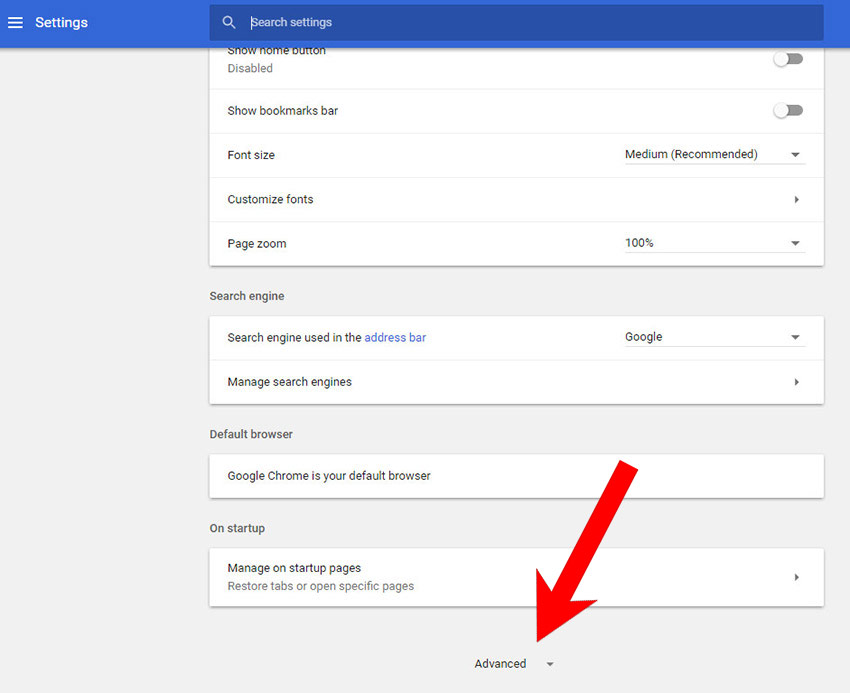
- Choose Settings.

- Scroll down and press on Show advanced settings.

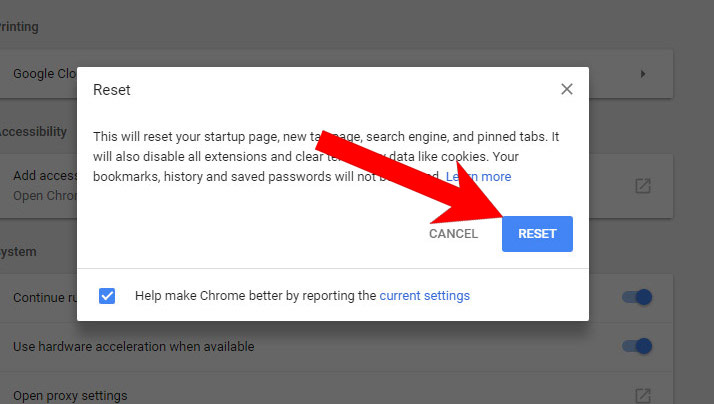
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
h) Remove Antivirus from Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Select Add-ons.

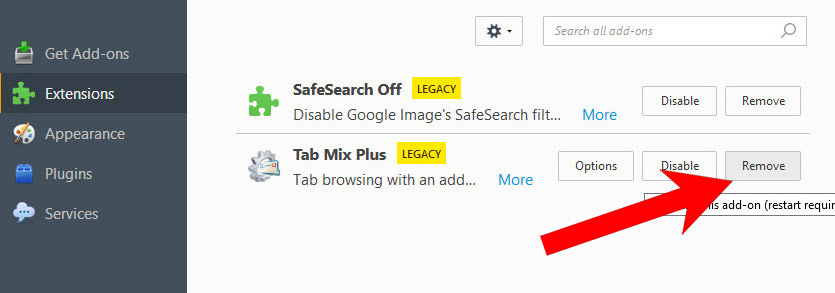
- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
i) Restore your homepage on Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
- Select Options.

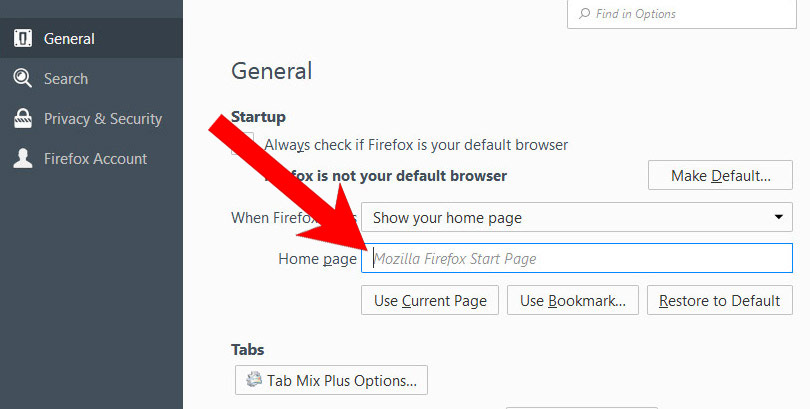
- In General, click Restore to Default below the Home Page field.

j) Reset Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
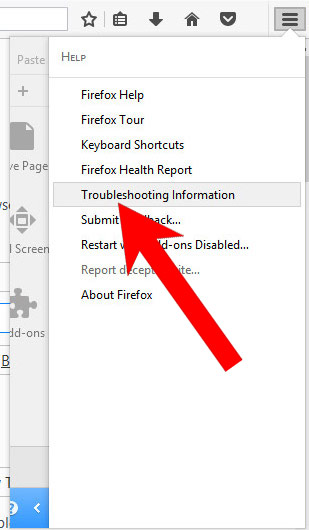
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

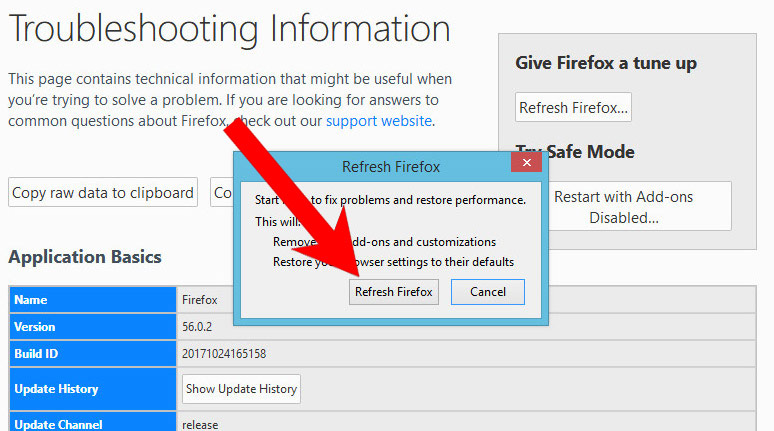
- Select the Refresh Firefox option.

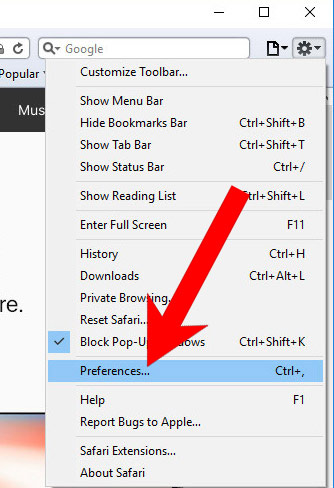
k) Remove Antivirus from Safari (for Mac)
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

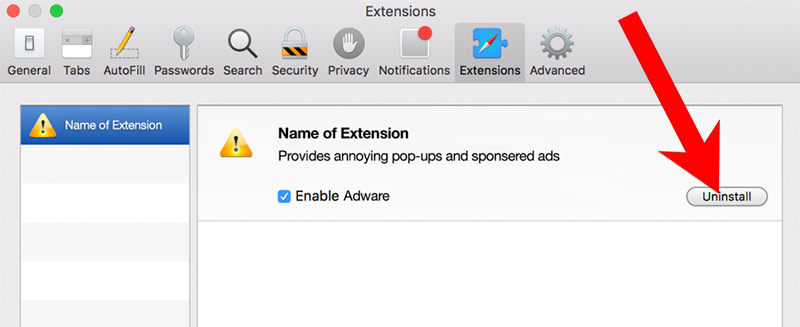
- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
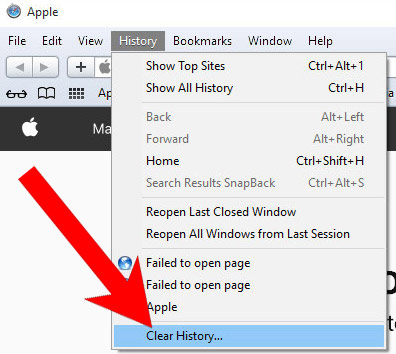
l) Reset Safari
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
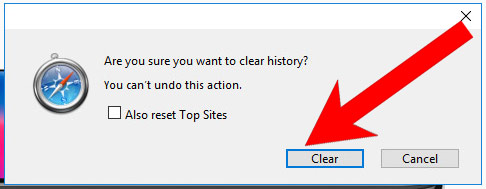
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

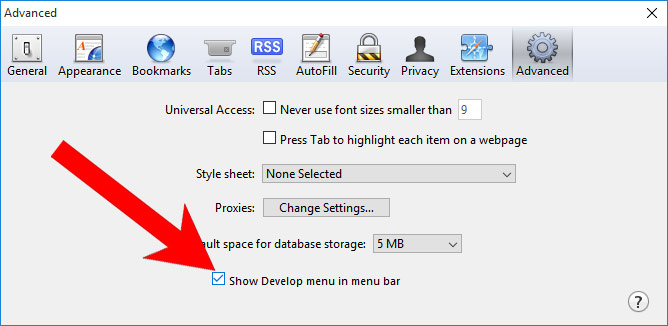
- Press on Safari at the top of the screen and select Preferences.

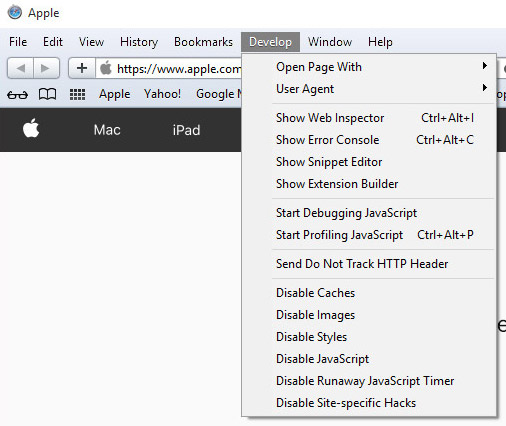
- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.