If you have been looking for guide on how to delete a Trojan Horse titled RegHost from your pc, search no etc.. On this website, you will see a full elimination instructions in packages with phase-by-step guidelines on how to find and securely delete this malevolent contamination from your device. In the guidelines, you will also detect a advised efficient RegHost anti-spyware tool for automatic help.
But previous you go straight to the guidelines, let’s beginning from the begin: what is actually a Trojan Horse and what can a infection like RegHost threat do to a pc?
Trojans are a type of malicious software whose main aim is to grant remote entry to a computer and begin diverse adverse functions on it. The title of these malicious software is inspired by the mythical wooden horse utilized by the Greeks to slither into the supposedly not beatable city of Troy without increasing doubts. Similarly, this malicious software try to pass surreptitiously, launching a backdoor for a remote intruder to get into the operating system.
Download Removal Toolto remove RegHostHowever, generally, Trojans do etc. than just offer a backdoor – they are greatly resourceful elements of viruses which might also be implemented to document keystrokes and entered webpages, transmit content from the machine to remote servers, evil files, scam details, distributed other malware, and specially Ransomware malicious software, construct safety vulnerabilities, and much more damaging.
And, as we mentioned, the Trojan generally try to go undiscovered, so it would not be a notable surprise if a malicious software like RegHost indicates wholly no indications of its emergence in the device for a lengthy time. Basically, this kind of infections is designed to disguise procedures that can make the user fishy.
How? The malware is generally set up on the machine in packages with administrator privileges or core permissions. This way, the cyber criminal who manages it might have complete oversee of the computer and lurk varying procedures and files, block the anti-malware utility from doing its job, bypass, etc. This prohibits you from discovering that there has been a endanger in your pc, which develops it really hard to locate and eliminate the Trojan on time.
How can we become unclean?
There are so a bunch of approaches in which a Trojan for instance RegHost can get inside your system. An threat can take place because of a vulnerability in a tool which you have set up (for example Flash, Java, Adobe Reader) or when you download an compromised document which, when started, commits malevolent code that unnoticed sets up the infections without your ability. The criminals generally use some supposedly not malicious components of details like images, email attachments, relations, bogus ads, false choices, or infected pages, which, earlier interacted along with, provoke the parasite.
Unfortunately, because of a shortage of indications, it might take you weeks or even months to know that you have been infected. That’s why the safest method to safeguard on your own against Trojans and to identify and eliminate malware like RegHost infection on time is to make use of trustworthy security programs. A very good anti-malware program can scan the pc for contaminated procedures in the background and inform you about your device’s condition. It’s unnecessary to distinguish to you why you ought to take prompt action if a Trojan acquires discovered. The longer the malicious software stays in the system, the stronger the damage it could lead to. That’s why you have to not lose time and why it’s neccessary to act in accordance with the guidelines underneath to right away terminate RegHost malicious software.
Download Removal Toolto remove RegHostLearn how to remove RegHost from your computer
Step 1. RegHost Removal from Windows
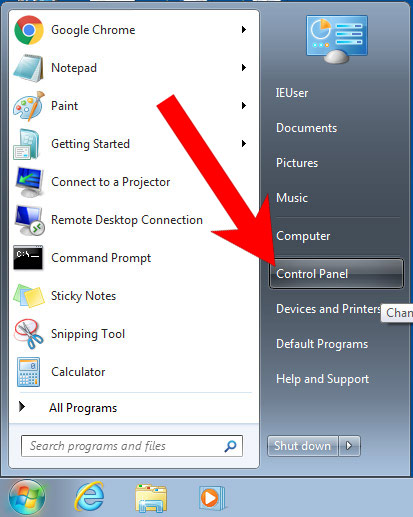
a) Windows 7/XP
- Press on the Start icon.

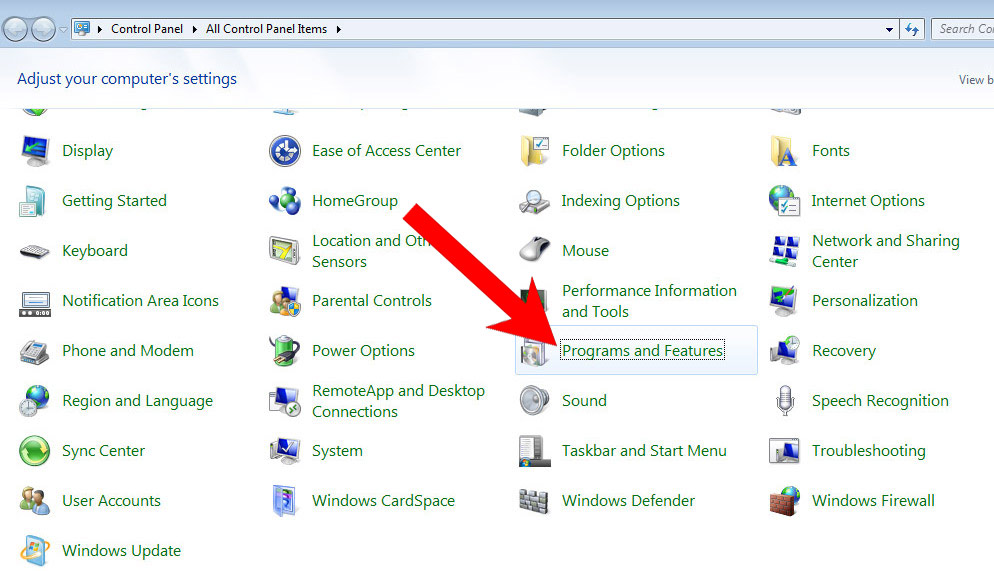
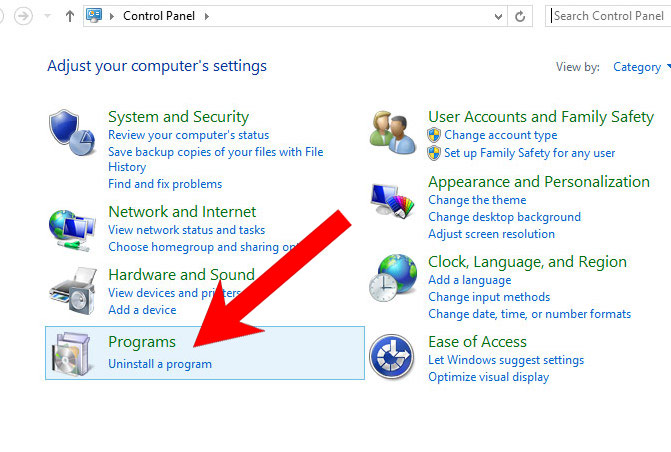
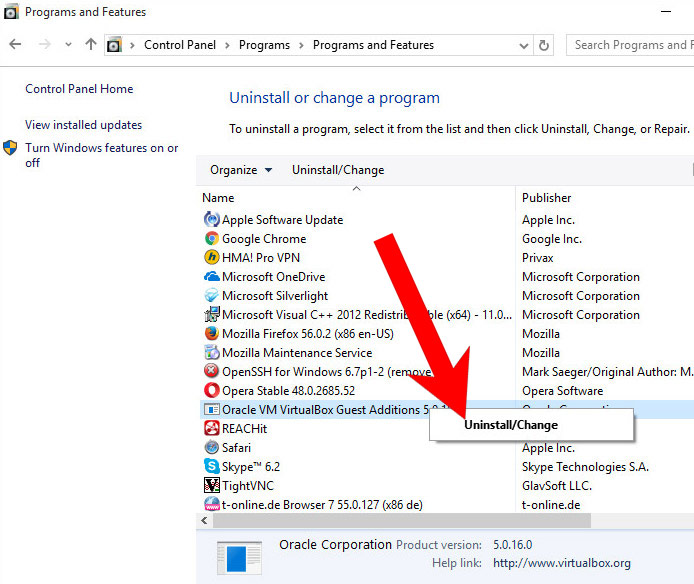
- Control Panel → Programs and Features.

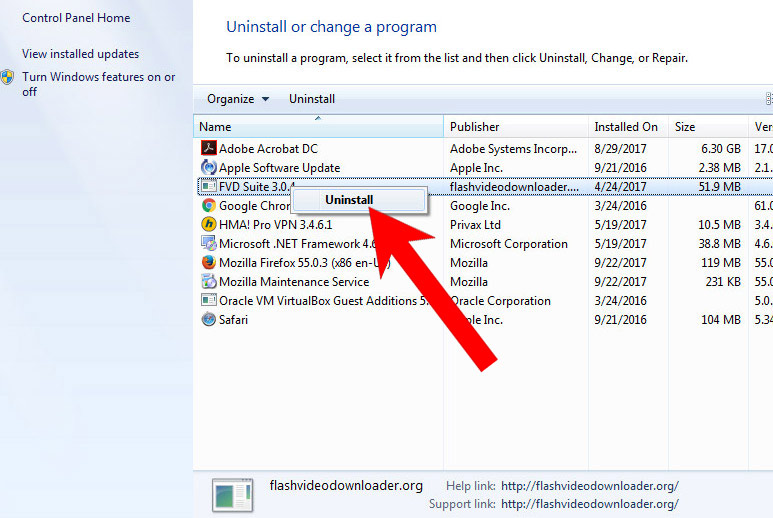
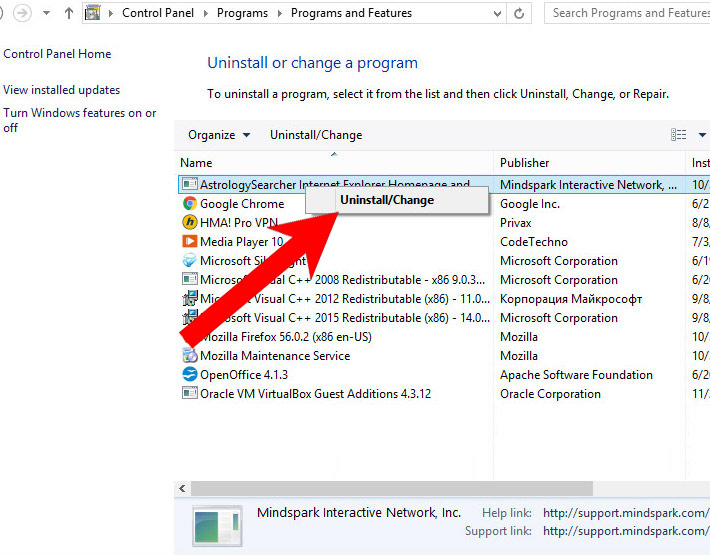
- Find the program you want to delete and press Uninstall.

b) Windows 8
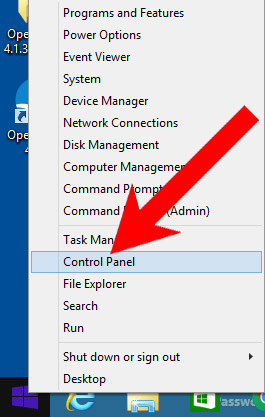
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

c) Windows 10
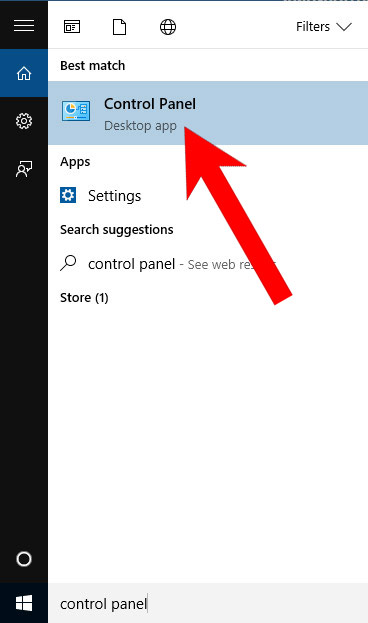
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

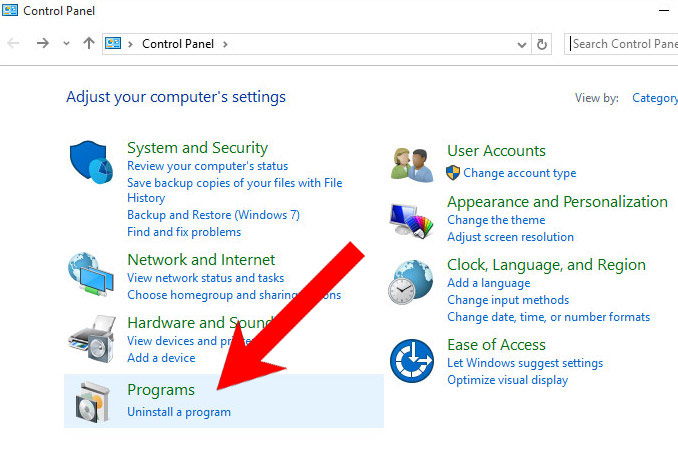
- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

d) Mac OS X
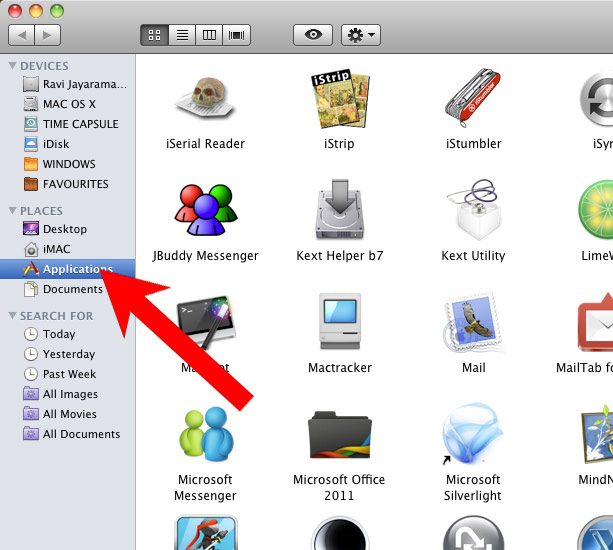
- Open Finder and press Applications.

- Check all suspicious programs you want to get rid of.
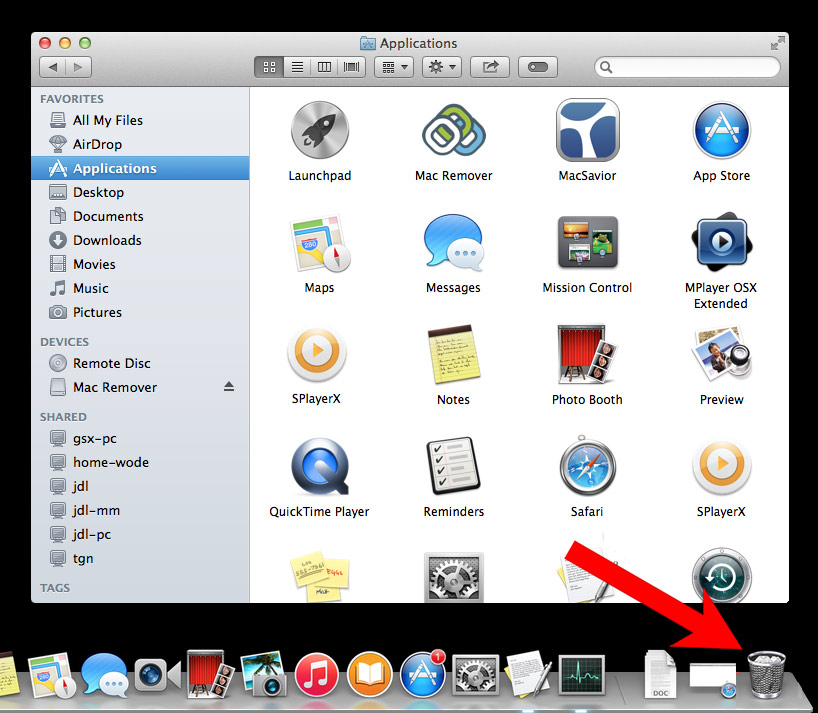
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete RegHost from browsers
a) Remove RegHost from Microsoft Edge
Reset Microsoft Edge (Method 1)
- Open Microsoft Edge.
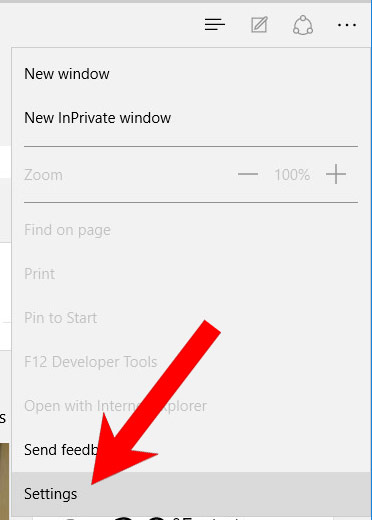
- Press More located at the top right corner of the screen (the three dots).

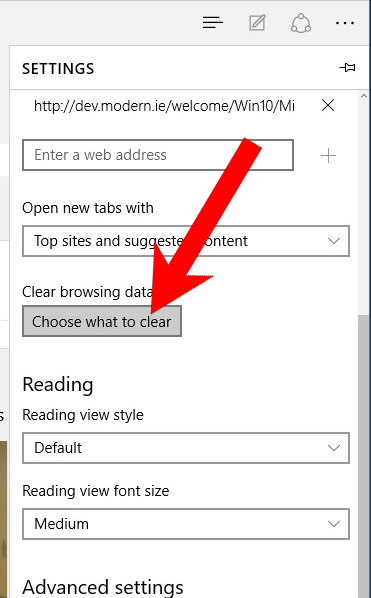
- Settings → Choose what to clear.

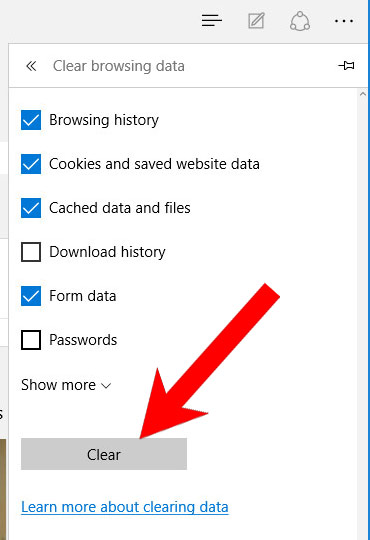
- Check the boxes of the items you want removed, and press Clear.

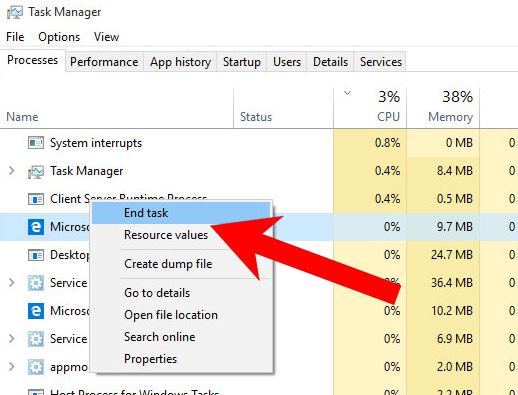
- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
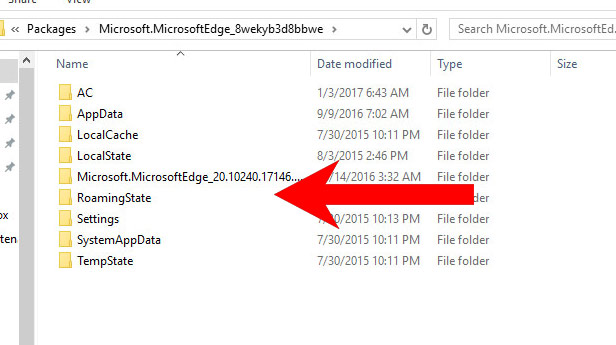
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

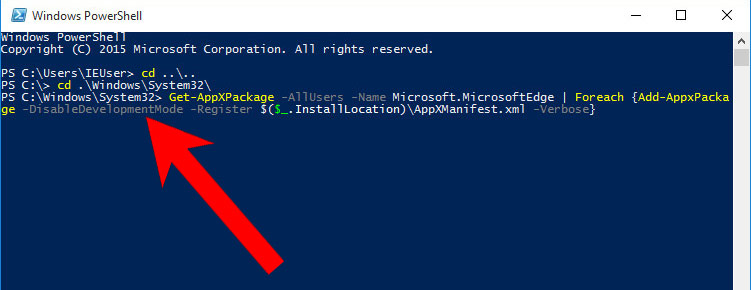
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
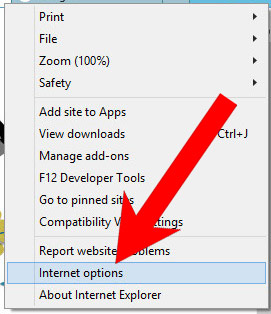
b) Remove RegHost from Internet Explorer
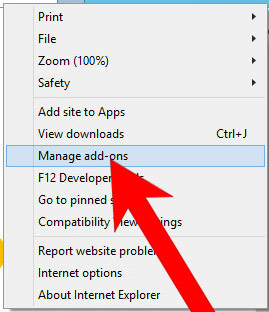
- Open Internet Explorer and press on the Gear icon.

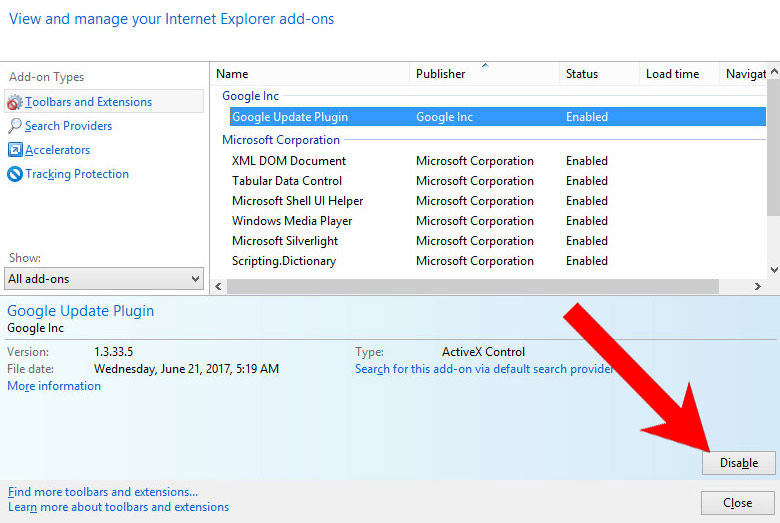
- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
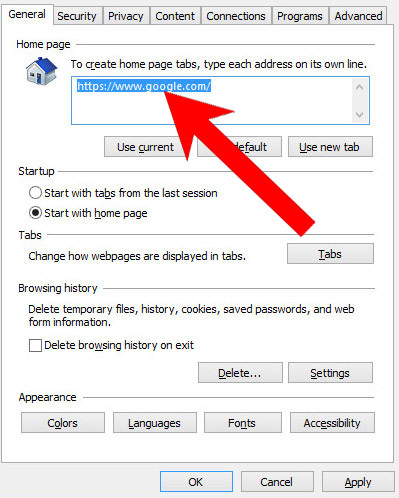
c) Restore your homepage on Internet Explorer
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
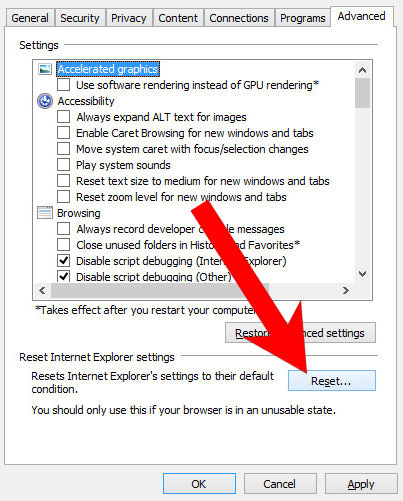
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

- At the bottom, you will see a Reset button. Press that.
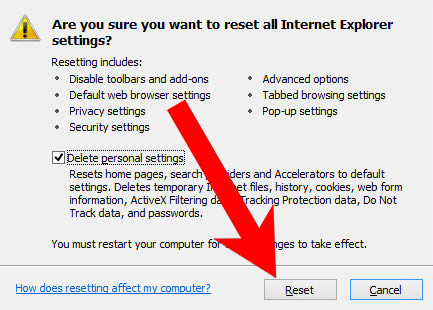
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
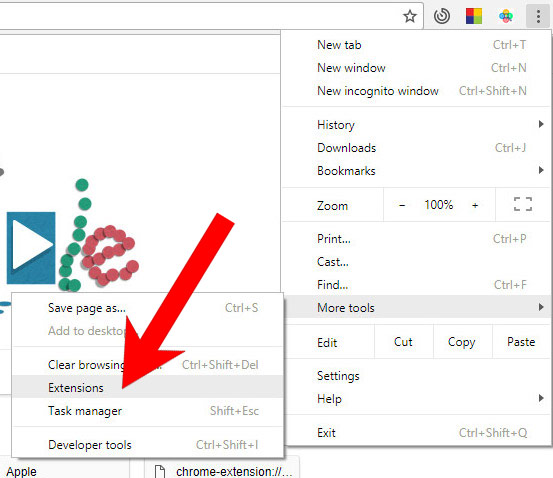
e) Remove RegHost from Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
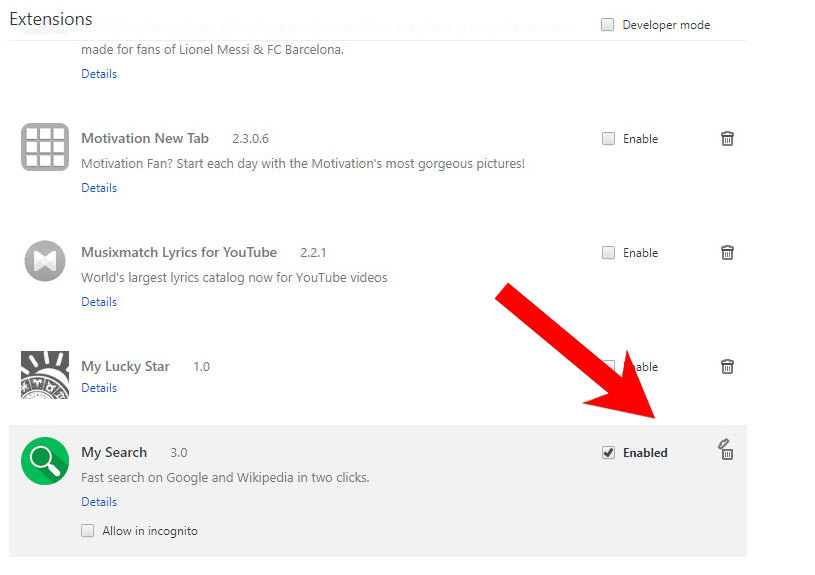
- Choose More tools and Extensions.

- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
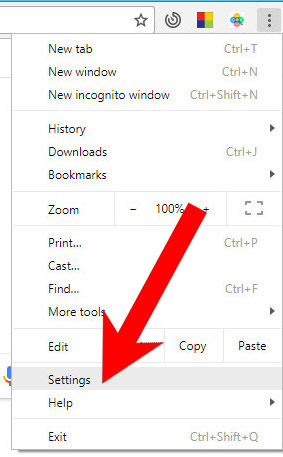
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

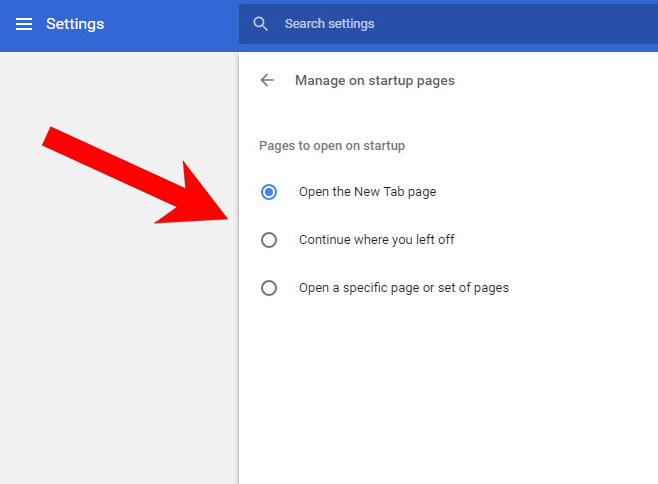
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

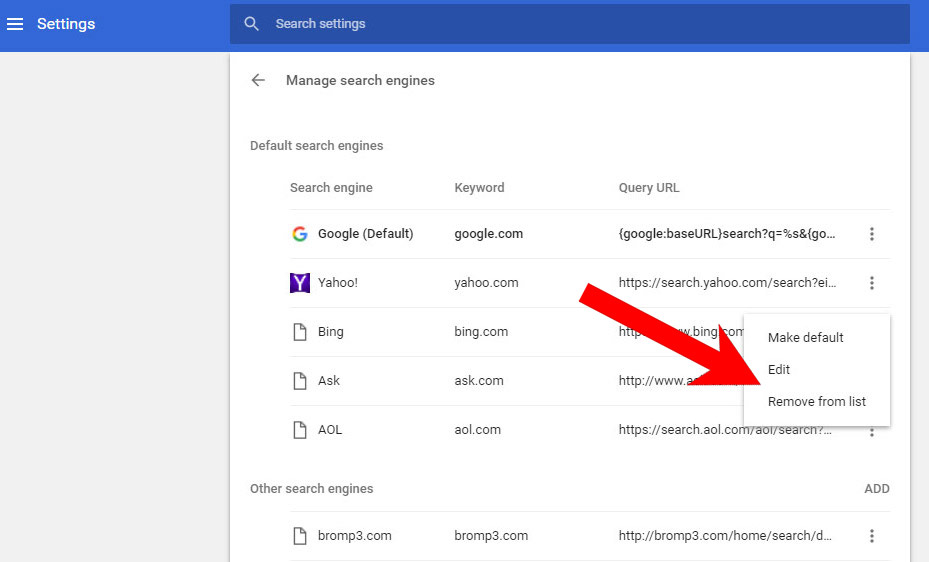
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
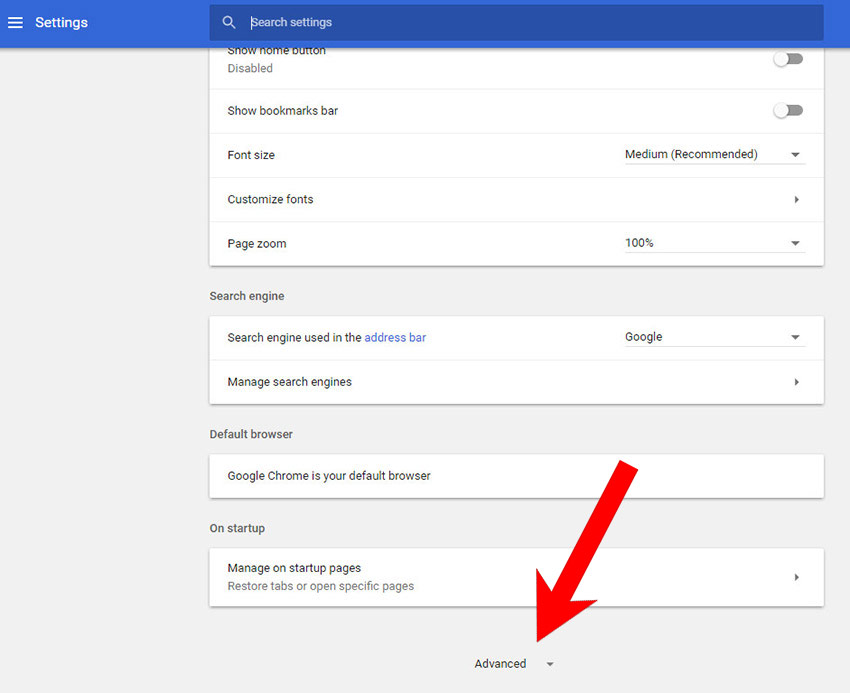
- Choose Settings.

- Scroll down and press on Show advanced settings.

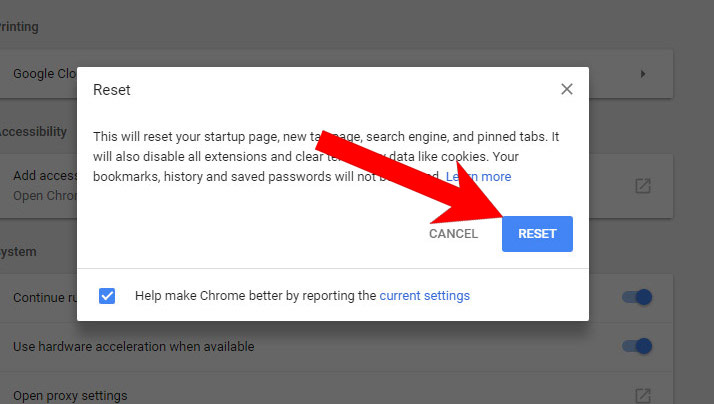
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
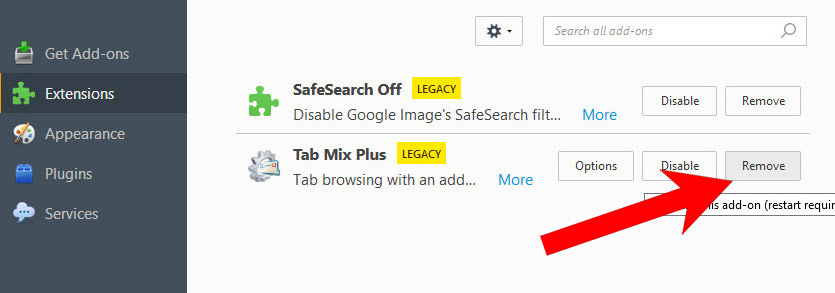
h) Remove RegHost from Mozilla Firefox
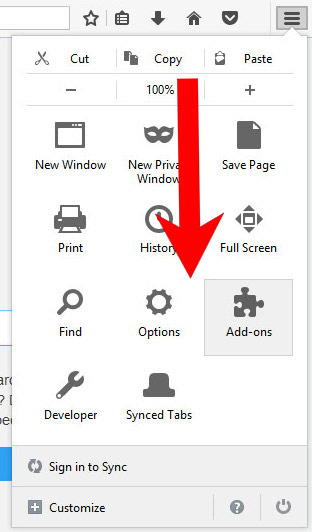
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Select Add-ons.

- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
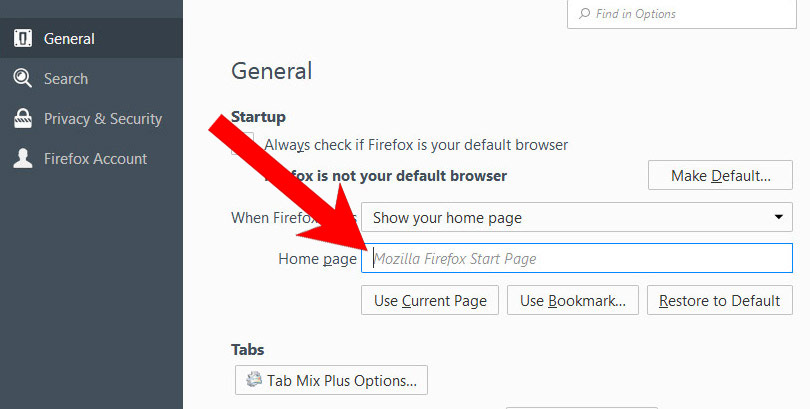
i) Restore your homepage on Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
- Select Options.

- In General, click Restore to Default below the Home Page field.

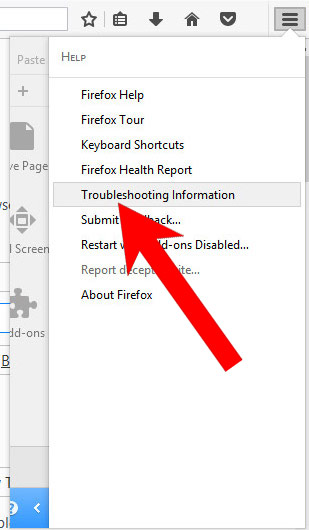
j) Reset Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

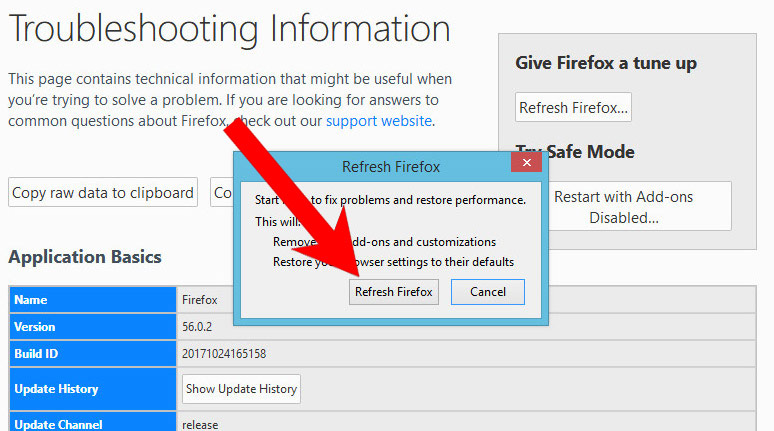
- Select the Refresh Firefox option.

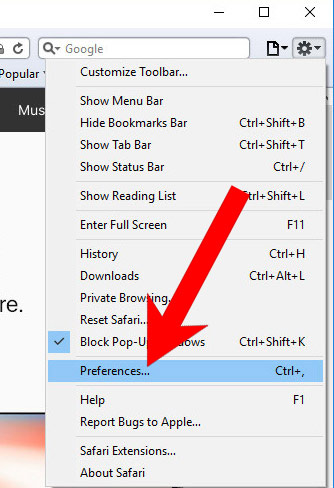
k) Remove RegHost from Safari (for Mac)
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

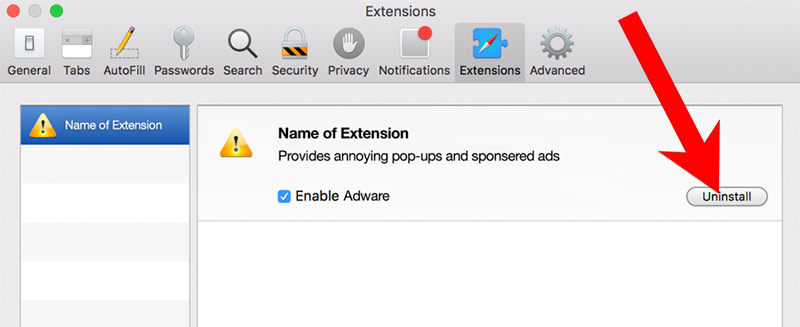
- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
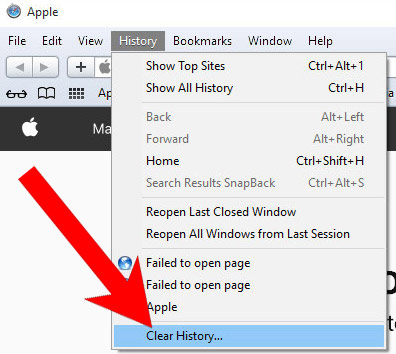
l) Reset Safari
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
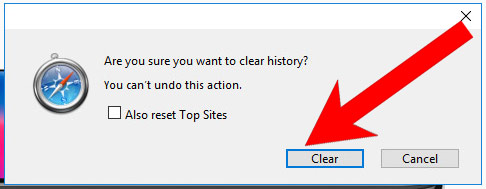
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

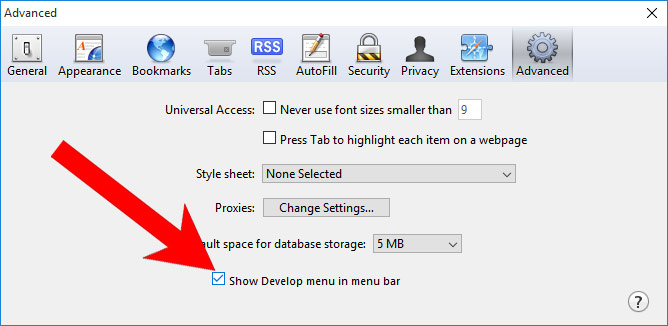
- Press on Safari at the top of the screen and select Preferences.

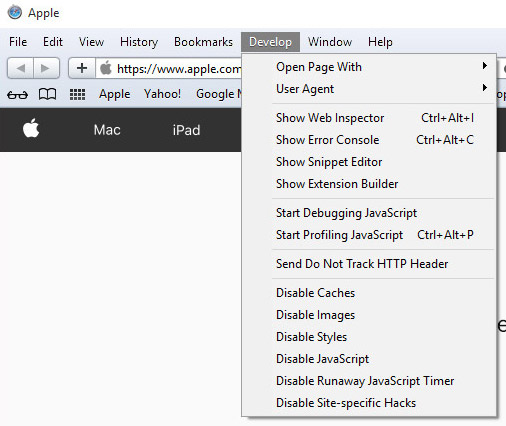
- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.