Some people have been receiving this bogus email as an issue:
Greetings. I monitored your device on the net for a lengthy time and successfully was able to hack it. It was not troublesome for me, as I have been in this industry for a lengthy time. When you entered a pornography web page, I managed to put a infection on your device that gave me complete entry to your system, specifically your camera, microphone, phone calls, messengers, what occurs on your screen, phone book, passwords to all social networks, etc. To disguise my malicious software, I have prepared a certain driver which is up-to-date each 4 hours and generates isn’t possible to locate it. I captured video of your screen and camera pc and edited a video of you masturbating in one component of the screen and a pornographic video that you started at that moment in the other component of the screen. I can securely transmit any information from your system to the web, as well as someone who is collected in your contacts, messengers and social networks. I might also offer someone entry to your social networks, emails and messengers. If you don’t are keen me to carry out it, then: send $1400 (US dollars) to my Bitcoin wallet. My Bitcoin wallet address:
Download Removal Toolto remove I monitored your device on the net
A Trojan’s novelty is one of those things that presents it an bogus advantage in the come across of antimalware. This is because of the uncomplicated point that a malicious software that has not yet been recognized by protection experts can’t be packaged with the malware definitions of a exhibited anti-malware program. Hence, it is generally able to avoid a computer’s defenses without hurdle, which earns it all the more harmful.
I monitored your device on the net is one of those Trojans that has merely just been detected by researchers. And as a result tons of new viruses in addition to it are being reported by people at the time of writing.
Because of its novelty, regardless, there’s in addition the matter of not understanding all the details connected to I monitored your device on the net. Trojans are infamously adaptable and could be programmed for an particularly sizable variety of varied fraudulent functions. And that leaves us regardless in ought of the precise intention that this specific example of malicious software serves. So regardless of the fact that we can’t locate it, we can at least display you a look of what the likely usages can be.
Here’s a small quantity of the well-known techniques in which the cyber criminals behind I monitored your device on the net can be through it.
- Resource exploitation. A Trojan like I monitored your device on the net might be set to corrupt your computer’s resources, e.g its RAM and CPU, so to perform numerous functions on behalf of the crooks. For instance, a very well known thing Trojans are utilized for is mining cryptocurrencies on the victims’ oss. Alternatively, your computer system can be affected in a botnet and be put to run sending out spam, contaminating other systems or even partaking in big-scale DDoS invades.
- Regardless of the fact that this isn’t the usual usability, it might regardless occur that you arrive a Trojan programmed to spoil details or even malicious your operating system.
- Trojans like I monitored your device on the net are well-known noses. They can implement a variety of methods and mechanisms via which they can buy confidential details from people. For example, I monitored your device on the net may log your keystrokes and as a result get access to all the information you category via your keyboard. Alternatively, a Trojan like this could be set to share your screen alongside the hackers and even shift on your webcam or mic.
- Deception is easily the typical usability and it’s identical to tailing in that quite a lot of of the methods overlap. However, the end outcome is that here you are without doubt cheated of something: your social media profiles, profits and even your identity.
Certainly there’s no ought to carry on this category so to depict how not secure this malware may potentially be. Therefore, terminating I monitored your device on the net need to be at the top of your classification of priorities. And to aid you do this efficiently, we’ve made a certain uninstallation guidelines just beneath this post. In it we’ve additionally connected a specialist termination software if you would kind of have this procedure done in an automatic way.
Learn how to remove I monitored your device on the net from your computer
- Step 1. I monitored your device on the net Removal from Windows
- Step 2. Delete I monitored your device on the net from browsers
Step 1. I monitored your device on the net Removal from Windows
a) Windows 7/XP
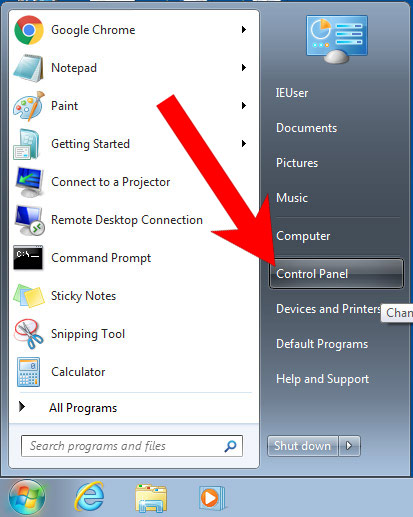
- Press on the Start icon.

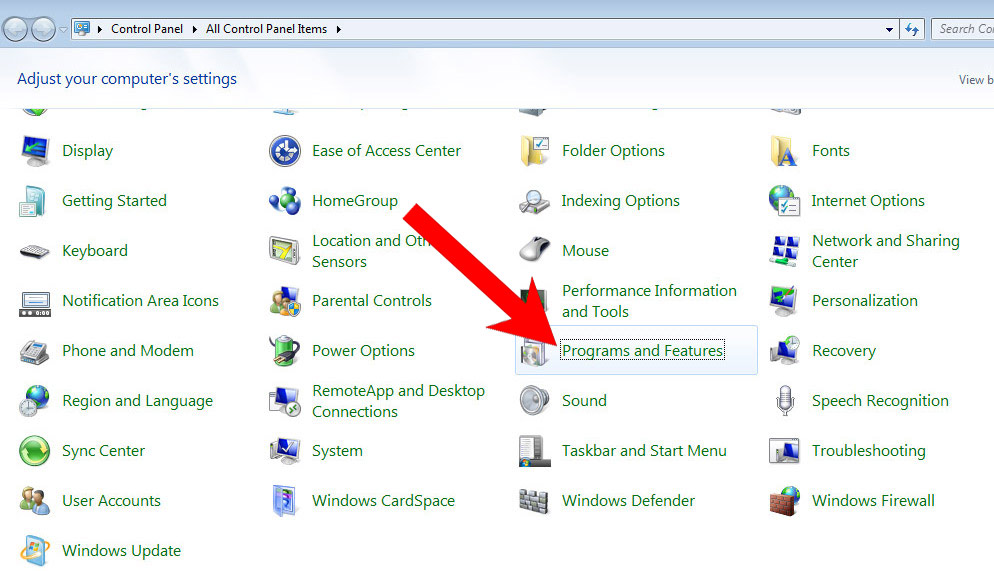
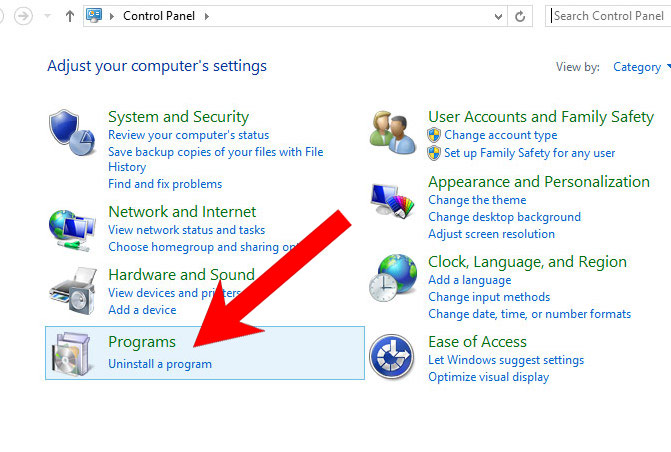
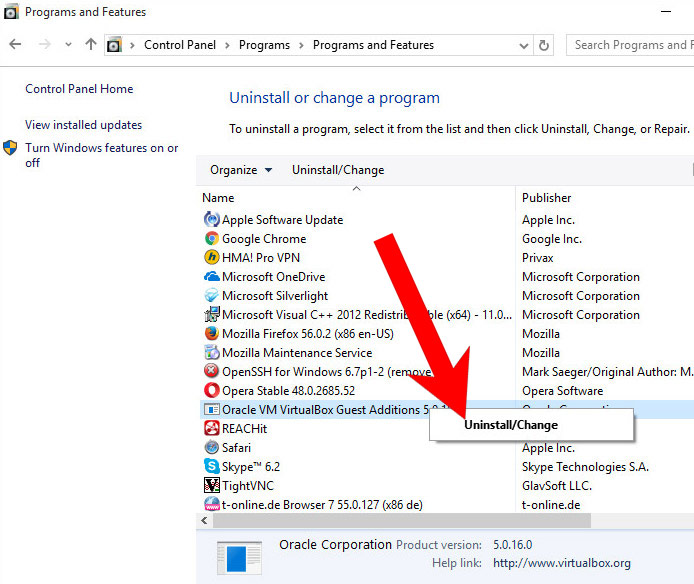
- Control Panel → Programs and Features.

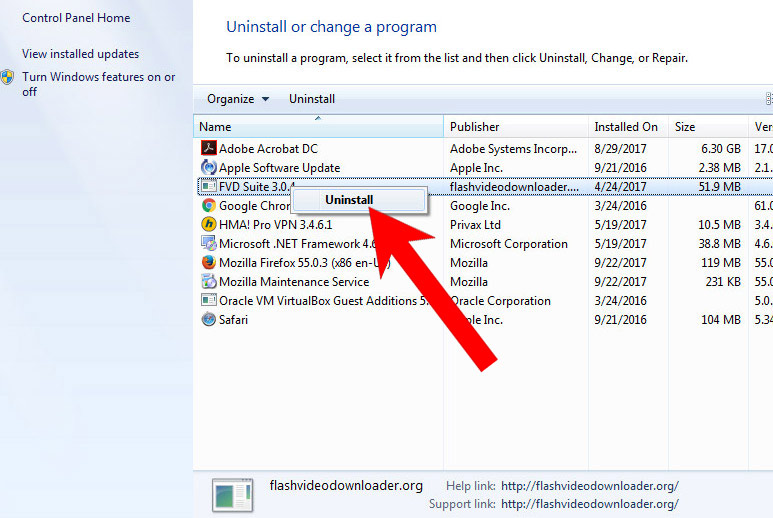
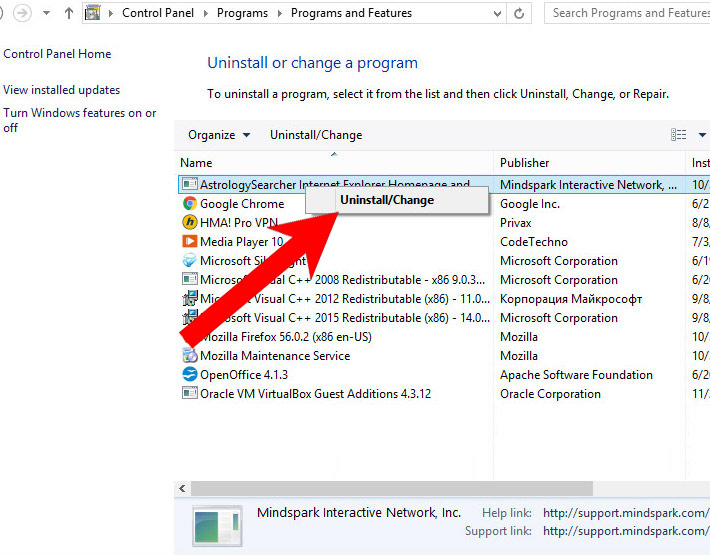
- Find the program you want to delete and press Uninstall.

b) Windows 8
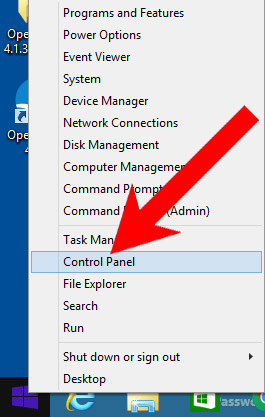
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

c) Windows 10
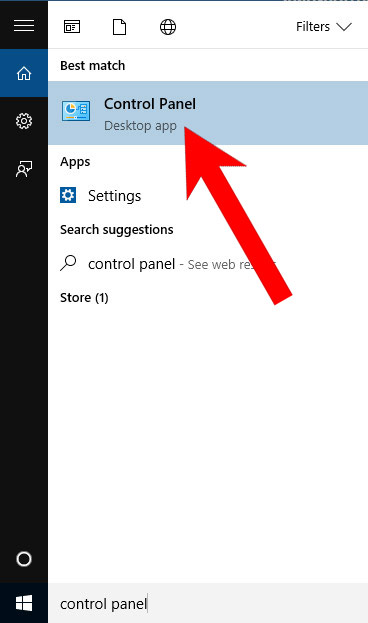
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

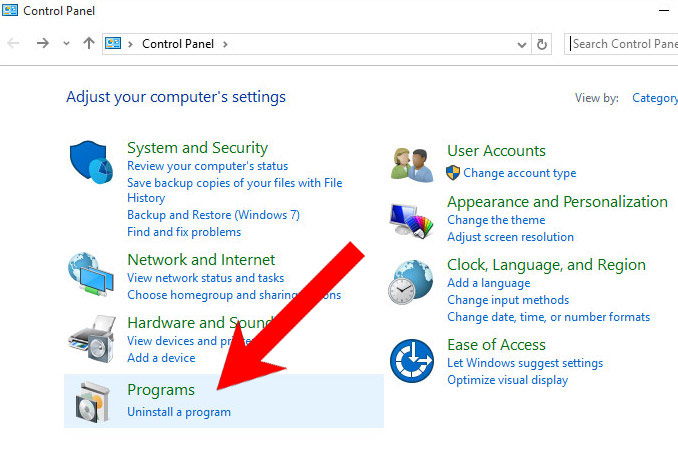
- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

d) Mac OS X
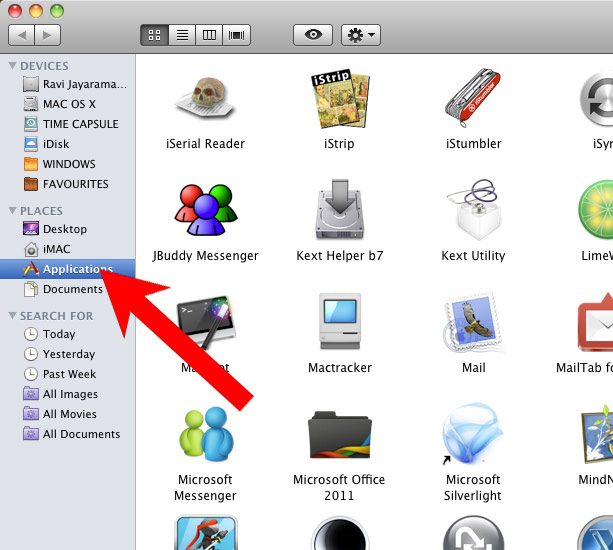
- Open Finder and press Applications.

- Check all suspicious programs you want to get rid of.
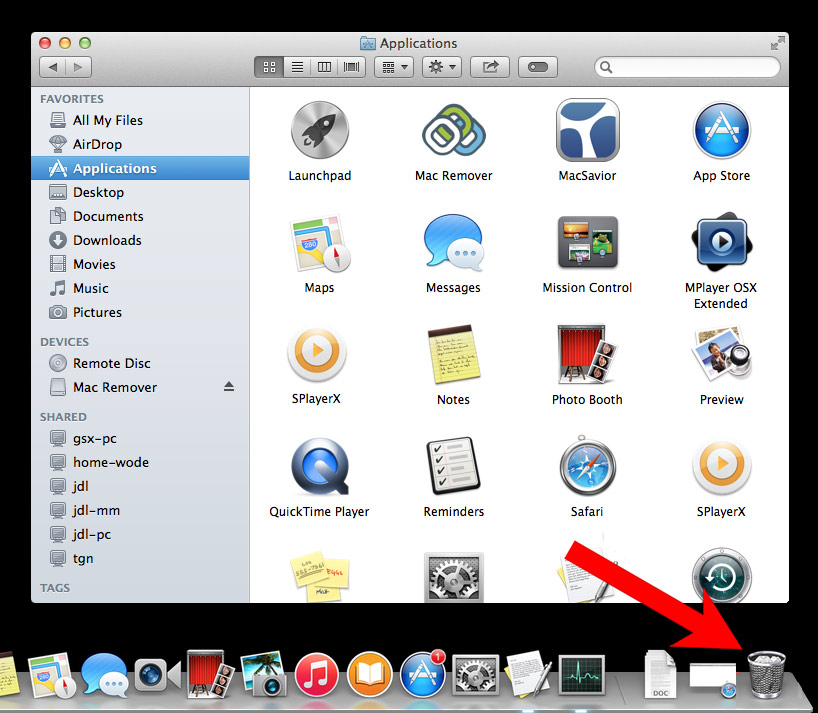
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete I monitored your device on the net from browsers
a) Remove I monitored your device on the net from Microsoft Edge
Reset Microsoft Edge (Method 1)
- Open Microsoft Edge.
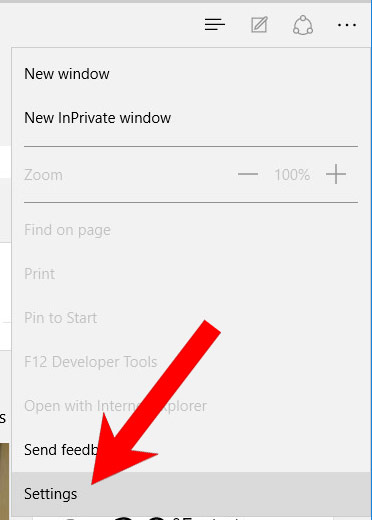
- Press More located at the top right corner of the screen (the three dots).

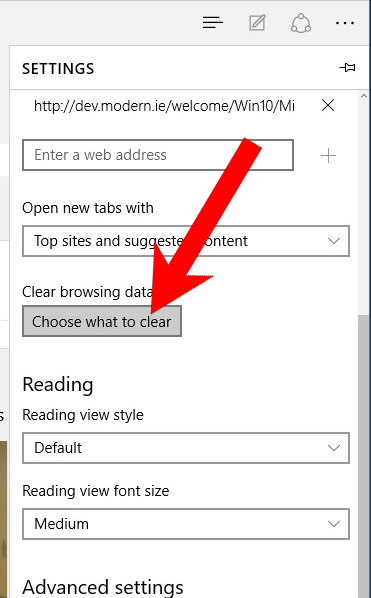
- Settings → Choose what to clear.

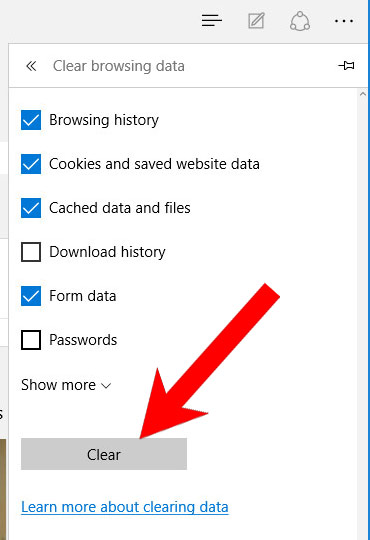
- Check the boxes of the items you want removed, and press Clear.

- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
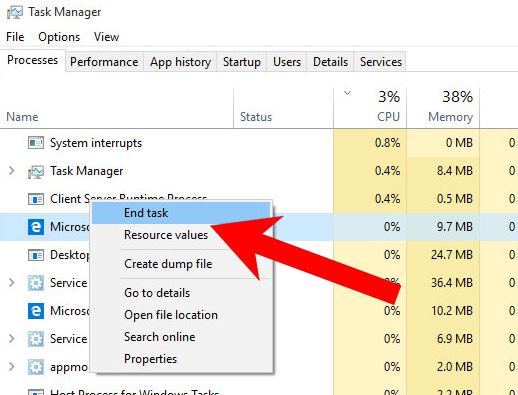
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
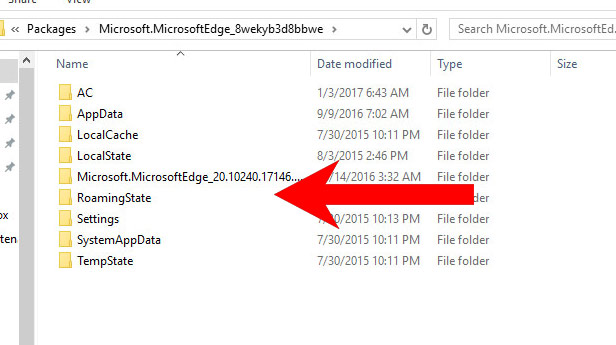
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

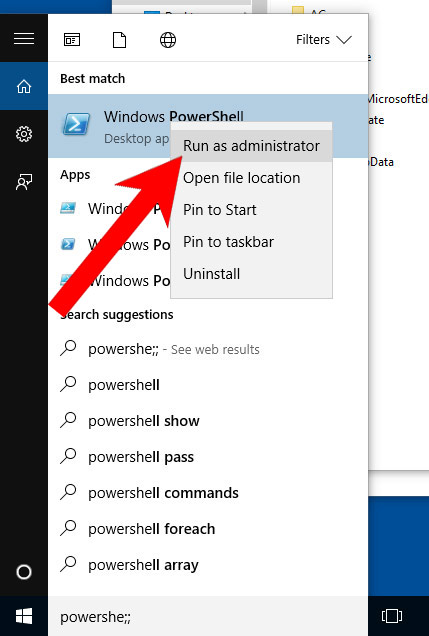
- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

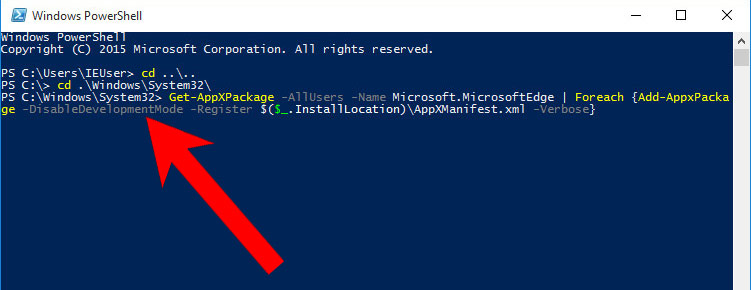
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
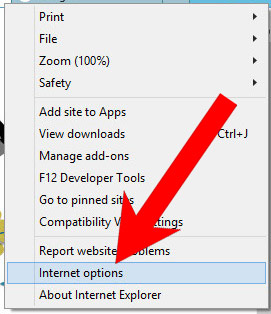
b) Remove I monitored your device on the net from Internet Explorer
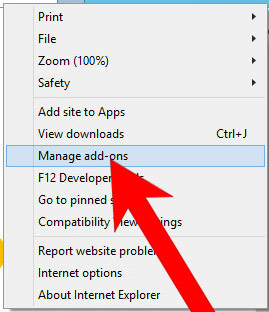
- Open Internet Explorer and press on the Gear icon.

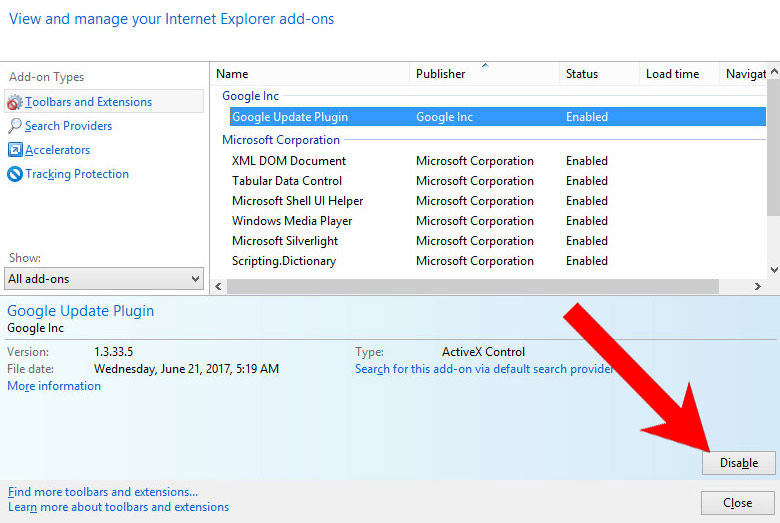
- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
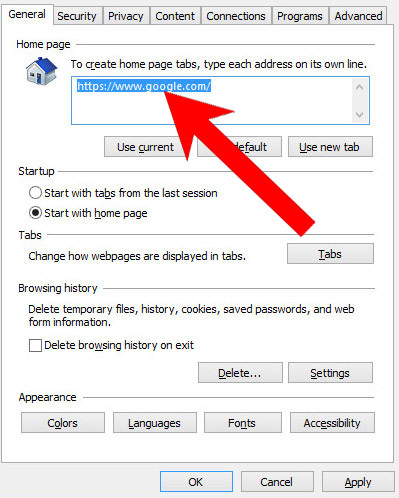
c) Restore your homepage on Internet Explorer
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
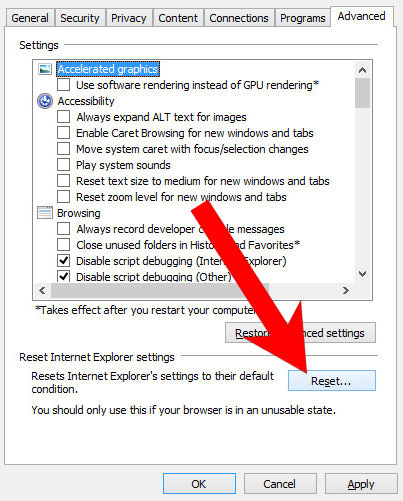
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

- At the bottom, you will see a Reset button. Press that.
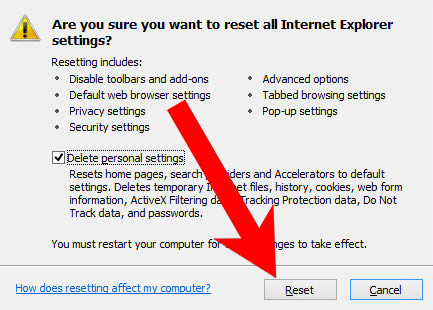
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
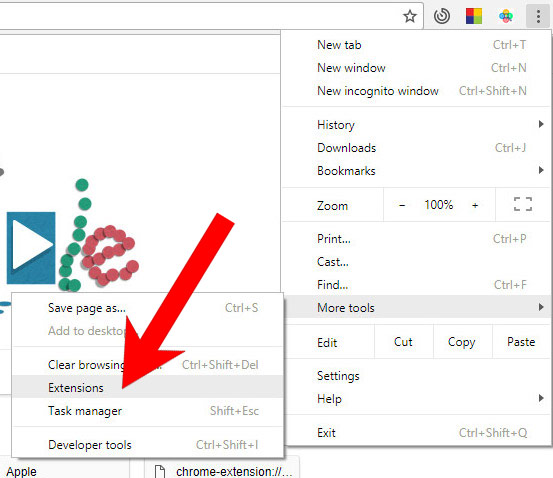
e) Remove I monitored your device on the net from Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose More tools and Extensions.

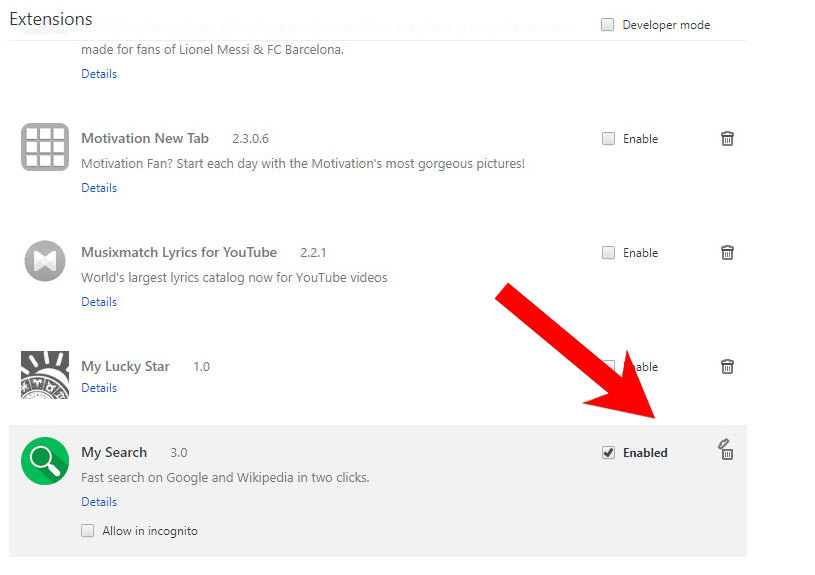
- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
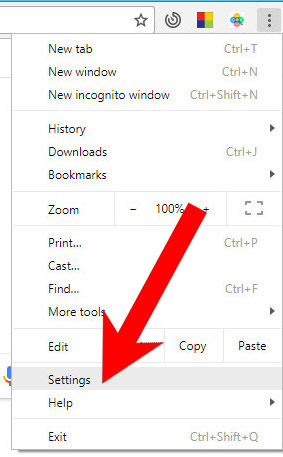
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

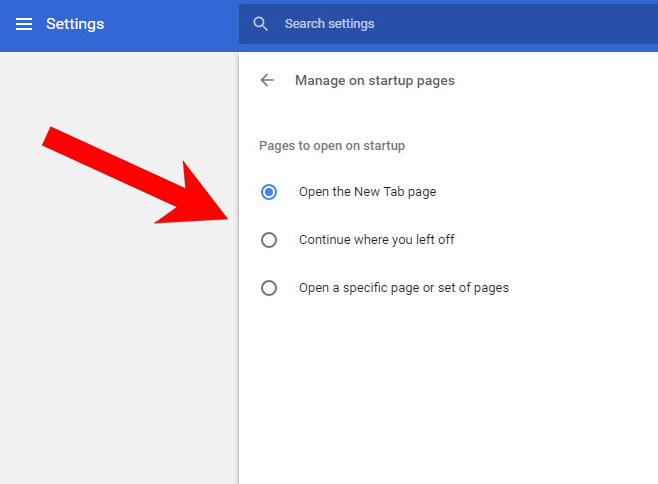
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

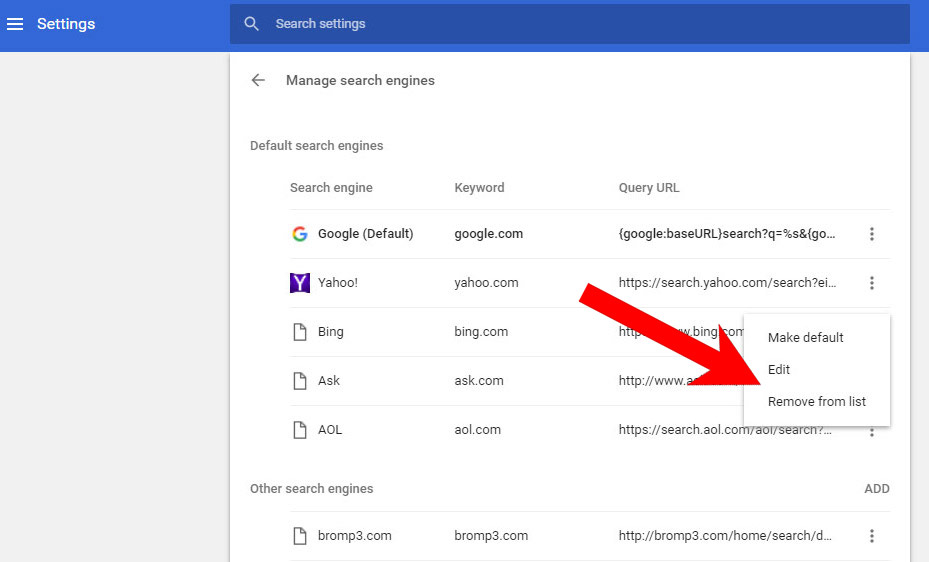
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
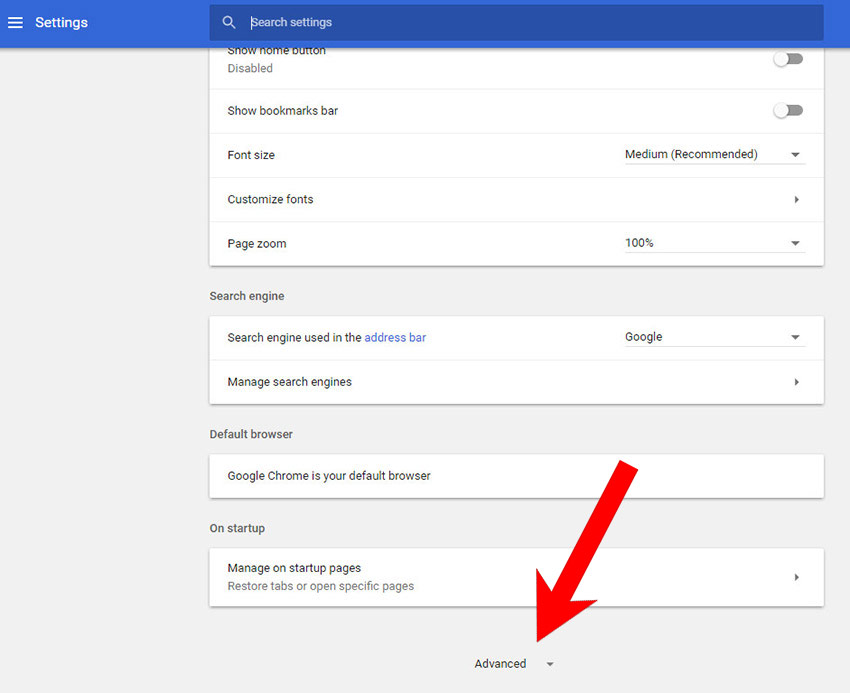
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

- Scroll down and press on Show advanced settings.

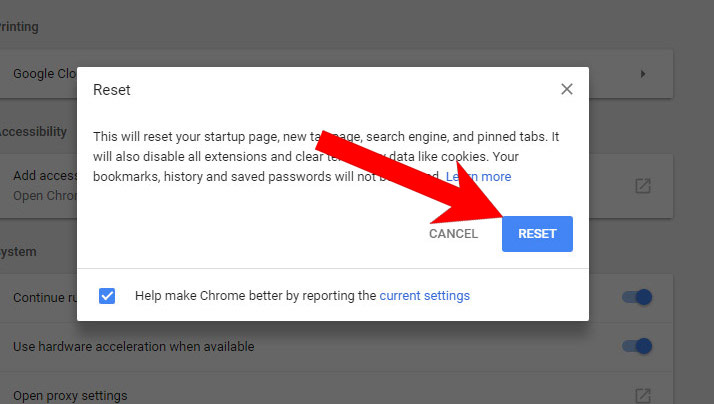
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
h) Remove I monitored your device on the net from Mozilla Firefox
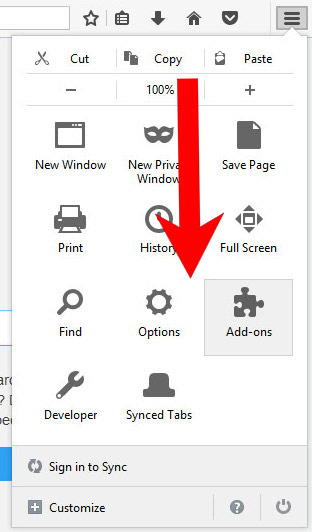
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Select Add-ons.

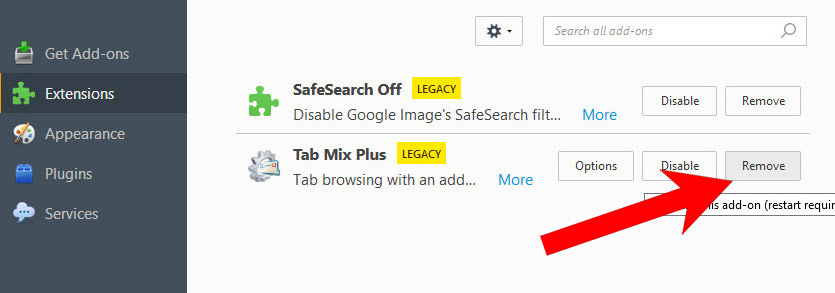
- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
i) Restore your homepage on Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
- Select Options.

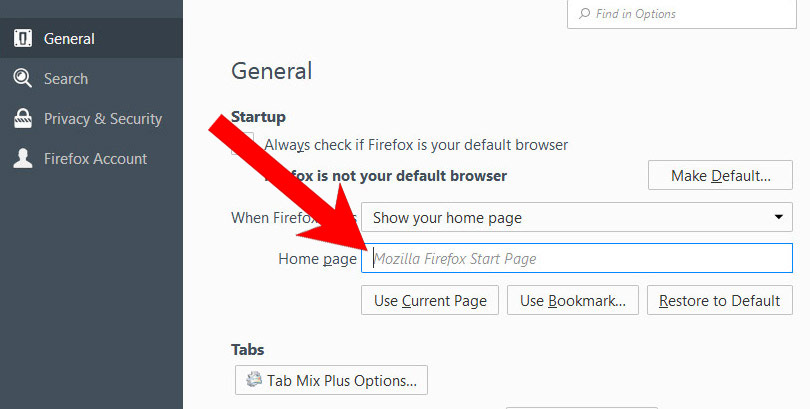
- In General, click Restore to Default below the Home Page field.

j) Reset Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
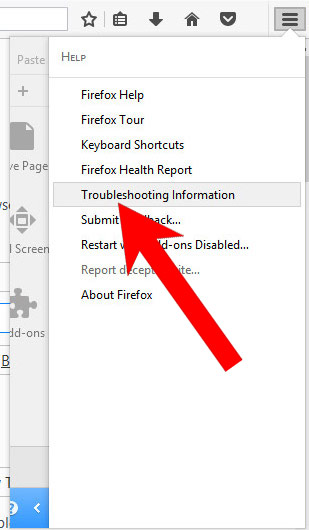
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

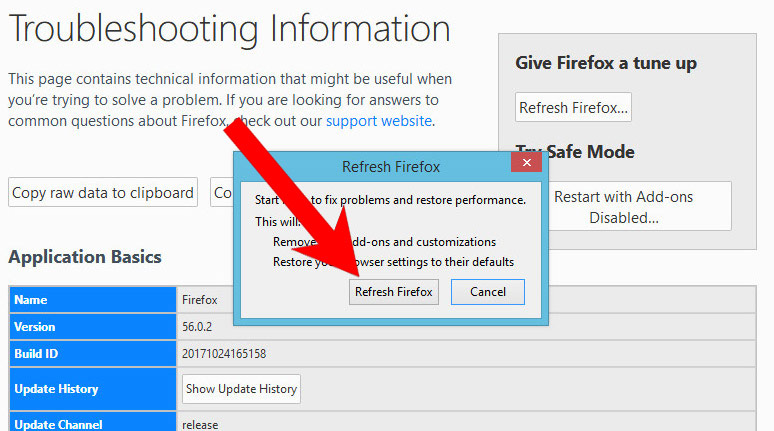
- Select the Refresh Firefox option.

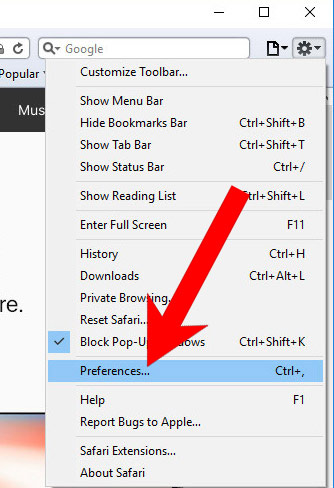
k) Remove I monitored your device on the net from Safari (for Mac)
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

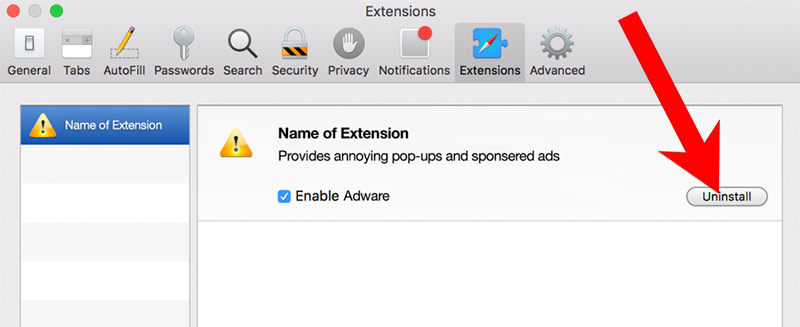
- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
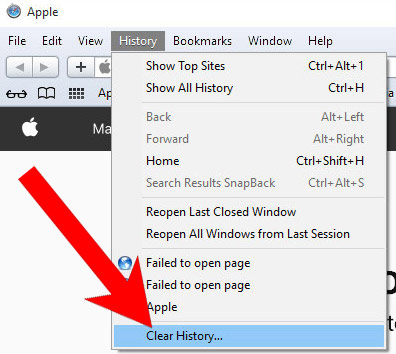
l) Reset Safari
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
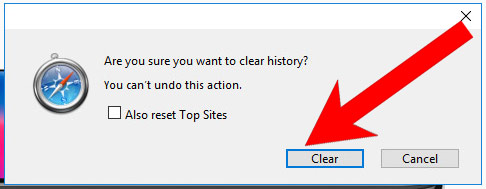
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

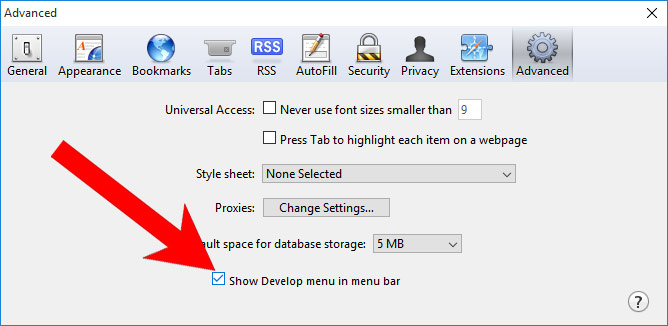
- Press on Safari at the top of the screen and select Preferences.

- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
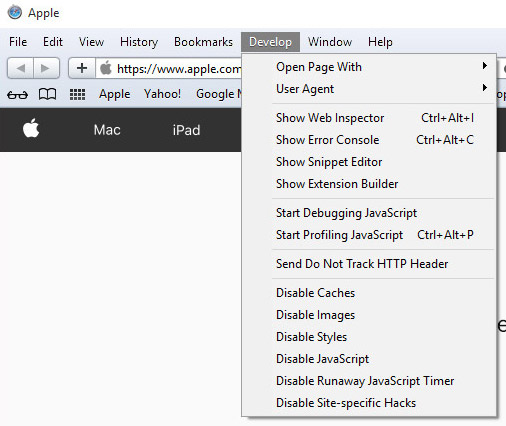
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.