*Source of assert SH can erase it.
I hacked your device
“I hacked your device” is a piece of malware that is categorized by security specialists as a Trojan horse virus. “I hacked your device” has been contaminating a increasing portion of people freshly and it’s necessary that you scan your pc for this malicious software should you have reasoning to suppose you’ve been nasty, too.
Really surreptitious perils e.g ransomware, malware and Trojans are regularly concealed on varying web locations and a single wrong press can quickly arrive a serious virus on your system previous you even know it. That’s why one has to be greatly wary when interacting alongside web content and take additional measures to locate and terminate malware from their oss in time.
Tons of of our people reported to us related to an in progress email spam along with the following notification:
I hacked your device, since I transmitted you this note from your account.
Download Removal Toolto remove I hacked your deviceShould you have earlier reconfigured your password, my malicious software will be interrupts it each time.
You might not know me, and you are the biggest part of feasible guessing why you are receiving this email, right?
In truth, I posted a harmful program on adults (pornography) of some pages, and you note that you entered these portals to appreciate
(you realize what I suggest).
As long as you were watching video clips,
My trojan began functioning as a RDP (remote desktop) along with a keylogger that gave me entry to your screen because well as a webcam.
At once after this, my utility compiled all your contacts from messenger, social networks, and on top of that by e-mail.
What I’ve performed?
I designed a double screen video.
The at the start fragment advertises the video you watched (you have decent taste, yes … but odd for me and other regular users),
And the minute item displays the tracking of your webcam.
Well, I feel $671 (USD dollars) is a fair cost for our nothing sly.
You shall earn a bitcoin payment (if you don’t know, want “how to buy bitcoins” on Google).
BTC Address: 1GjZSJnpU4AfTS8vmre6rx7eQgeMUq8VYr
(This is CASE personal, please duplicate and paste it)
You have 2 days (48 hours) to pay. (I have a certain code, and at the second I note that you have read this email).
If I don’t get bitcoins, I shall relay your video to all your contacts, which include category members, fellow workers, etc.
However, if I am paid, I will almost instantly ruin the video, and my trojan shall be destruct someself.
If you wish to get evidence, reply “Yes!” and resend this letter to youself.
And I shall undoubtedly transmit your video to your any 19 contacts.
This is a non-negotiable suggestion, so please don’t waste my confidential and other people’s time by replying to this email.
Unfortunately, there are some greatly stealthy malware that use advanced schemes for example sending spam and scam Bitcoin deception e-mails to users so as to fool them and no issue how vigilant you are, there is always a risk of collecting threatened without having any notion connected to it.
Download Removal Toolto remove I hacked your deviceIn this post, we are about to discuss one such malware that goes under the tittle of “I hacked your device” and is a representative of the Trojan horse classification. As per data from safeguarding specialists, “I hacked your device” is an infection that generally implements spam emails to distribute around the web. That’s why it may be connected with a viral e-mail deception ploy that utilizes scam and deceiving spam alerts to blackmail its victims.
The victims of this Bitcoin trick generally acquire an email from a self-advertised cyber criminal who claims that their system has been attacked by a Trojan horse in other words lying dormant in the device and is hesitating for indications to wreck the full OS. The hacker inquiries that a penalty is paid to a particular Bitcoin wallet, aggressive that if no payment has been developed in a fleeting extent of time, they shall use the ulterior threat to carry out something bad to or together with the system or the facts that’s on it. The hazards in the note may range hundreds but the complete premise accompanies this necessary blackmailing agenda
What to perform should you have been oriented by this deception campaign
If you are on this site, you possibly have lately gotten an email along with akin information and you need to be guessing what to implement next. Thankfully, though, security analysts suggest that, in most situations, the e-mail Bitcoin deception notifications are little but a bluff utilized by users in addition to fraudulent agendas as a way of stealing hasty profits from the oriented web people. There is no valid argument to assume the declarations produced in such emails unless you desperately have malicious software inside your machine.
That being claimed, it is a excellent concept to watch your whole device along with a reliable malicious software elimination software (if you don’t have one, you can employ the software added to the instruction underneath) since, in certain cases, apart from cheating the web people onto paying the ransom money, such hoaxes could be employed as transmitters of perils like “I hacked your device”. That’s why, notably if you have engaged with the blackmailing alerts that have spammed your email inbox, it would be better to conduct a ultimate computer examine for potentially unfamiliar hijackers and uninstall anything that seems dubious.
If that the check identifies a malware called “I hacked your device” on your device, you need to know that you can employ the guide in the deletion instructions placed below to at once identify and delete this harmful Trojan horse former it takes care of to bring about any harm.
Learn how to remove I hacked your device from your computer
Step 1. I hacked your device Removal from Windows
a) Windows 7/XP
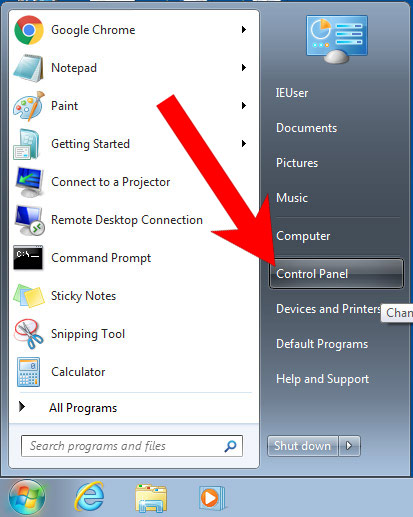
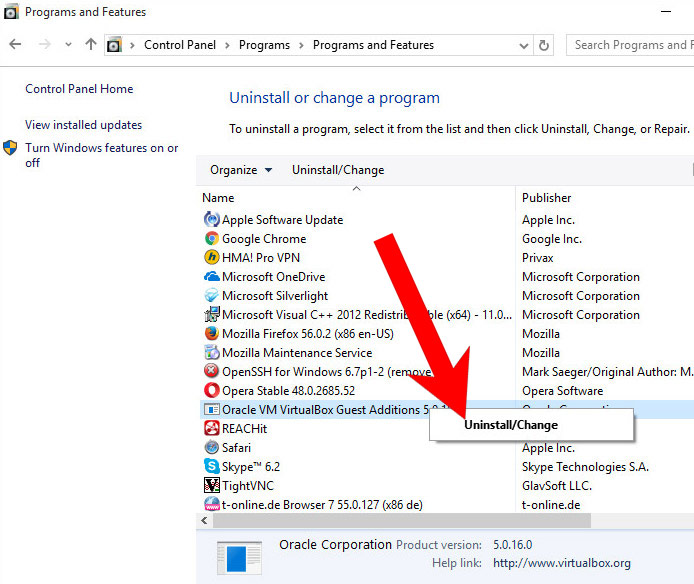
- Press on the Start icon.

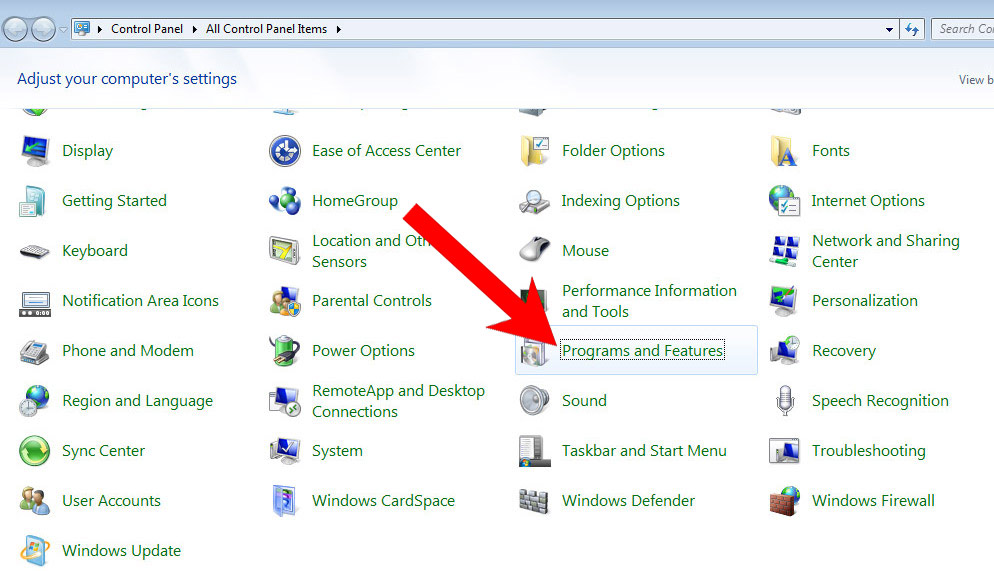
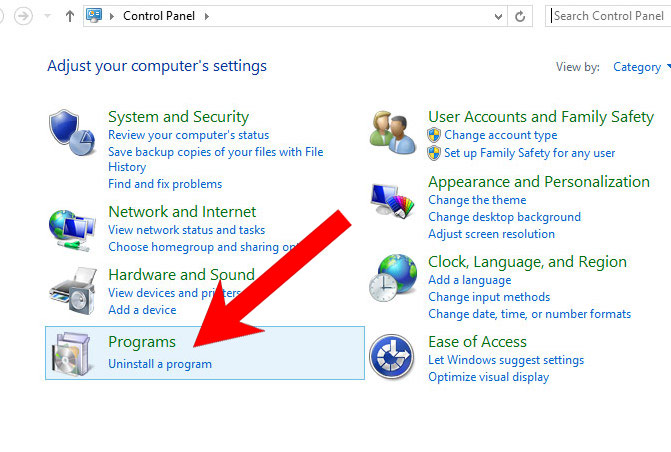
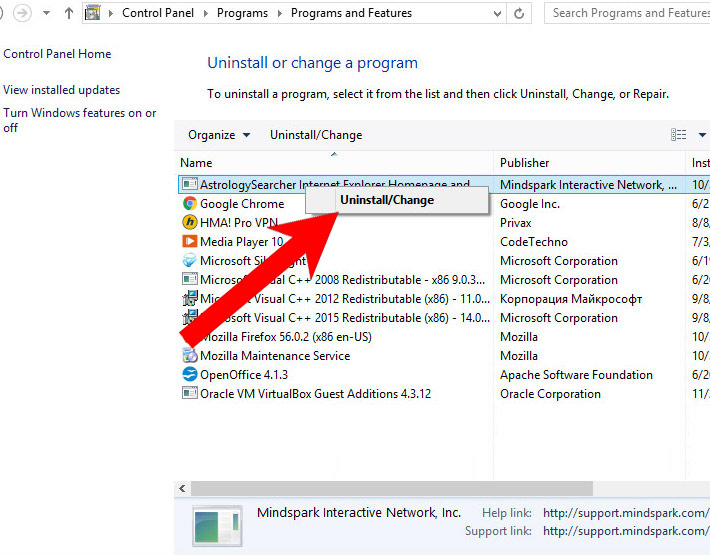
- Control Panel → Programs and Features.

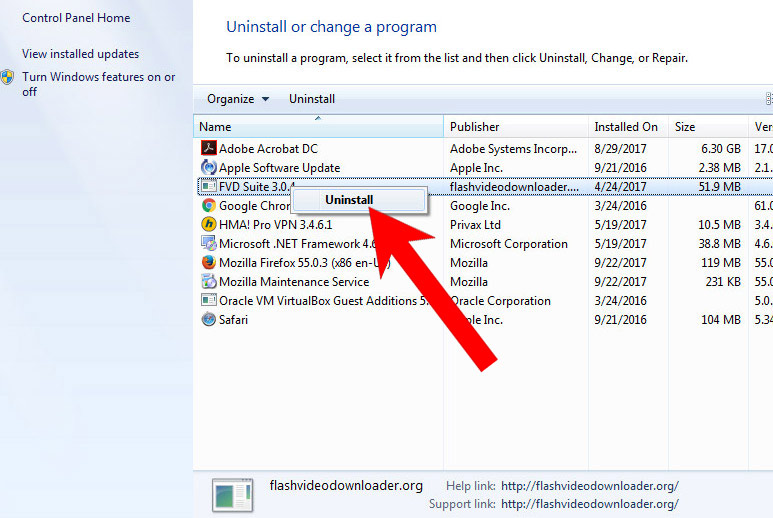
- Find the program you want to delete and press Uninstall.

b) Windows 8
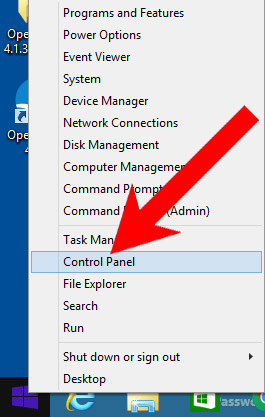
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

c) Windows 10
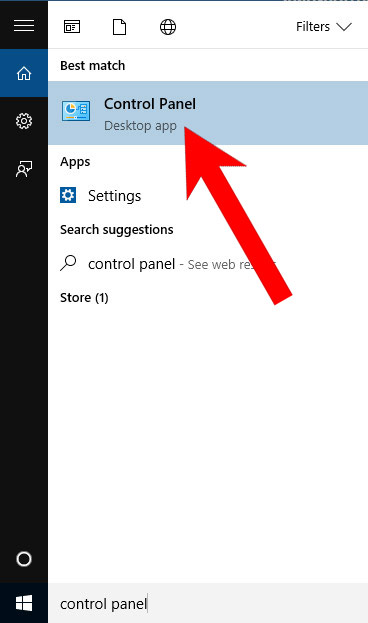
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

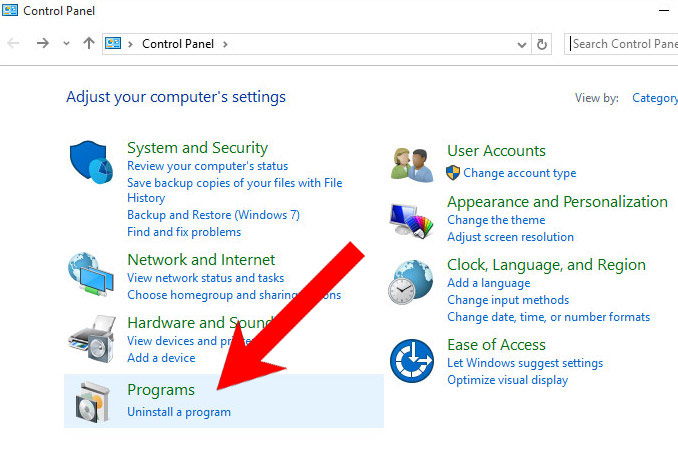
- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

d) Mac OS X
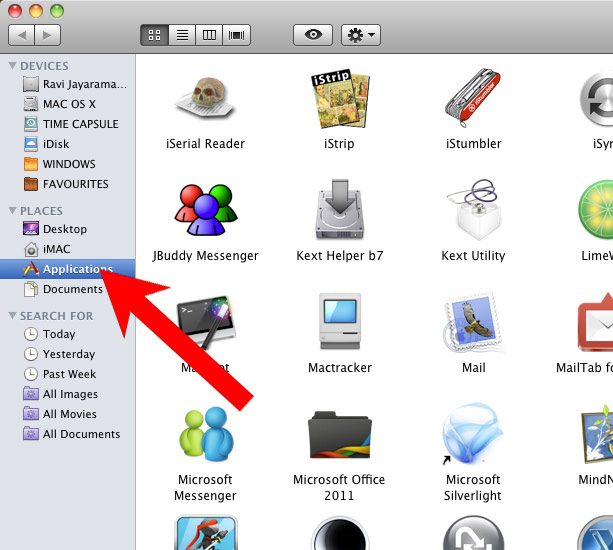
- Open Finder and press Applications.

- Check all suspicious programs you want to get rid of.
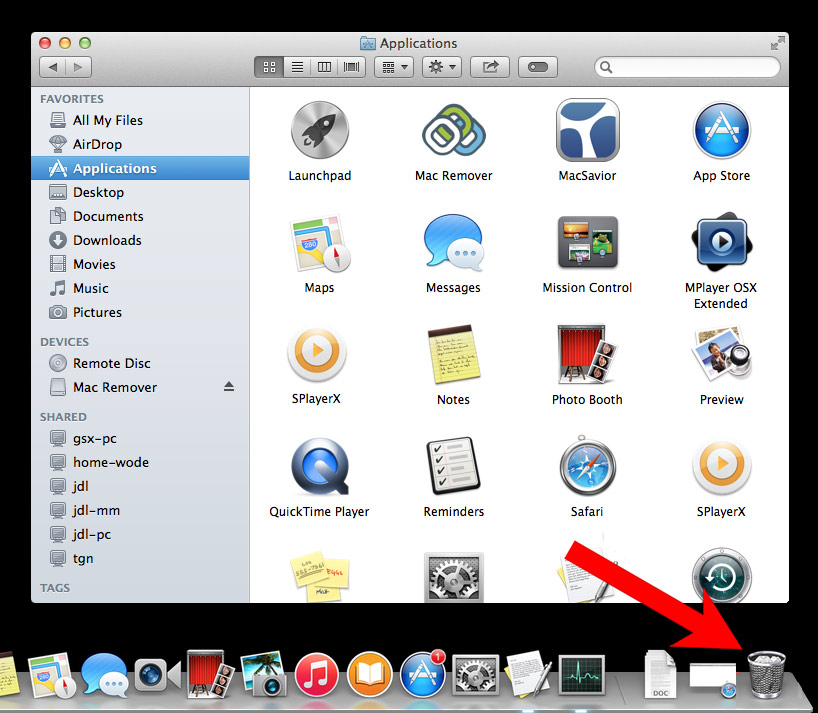
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete I hacked your device from browsers
a) Remove I hacked your device from Microsoft Edge
Reset Microsoft Edge (Method 1)
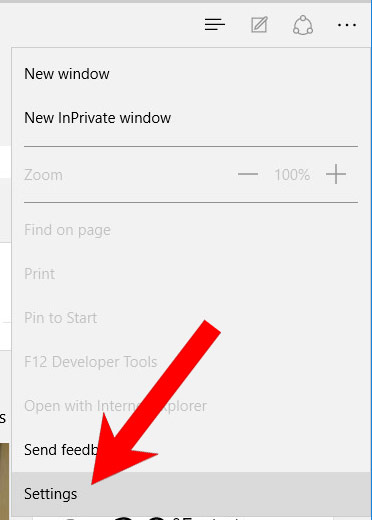
- Open Microsoft Edge.
- Press More located at the top right corner of the screen (the three dots).

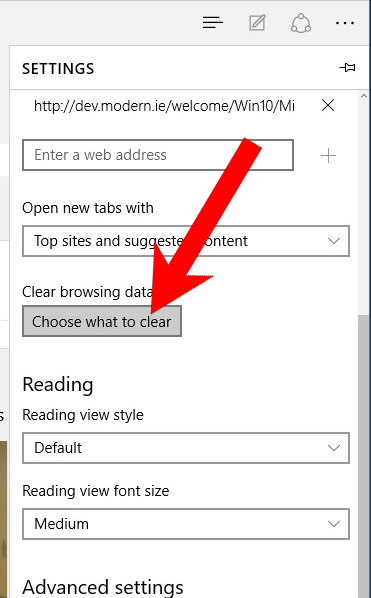
- Settings → Choose what to clear.

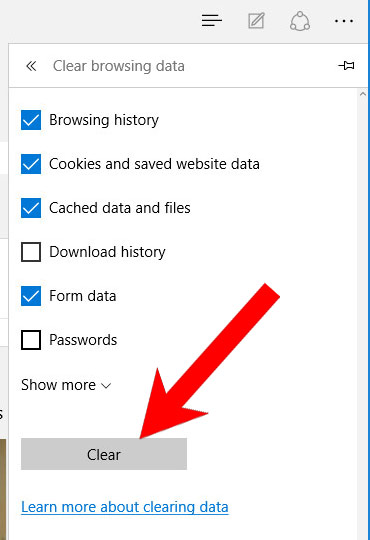
- Check the boxes of the items you want removed, and press Clear.

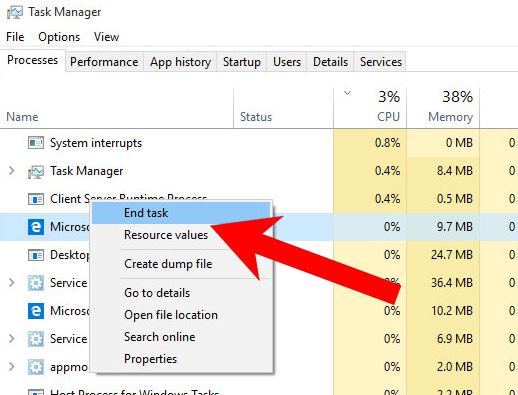
- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
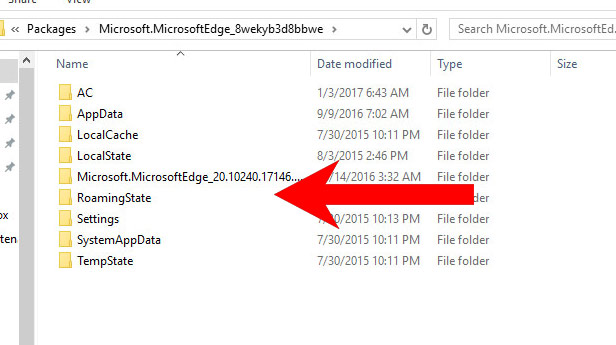
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

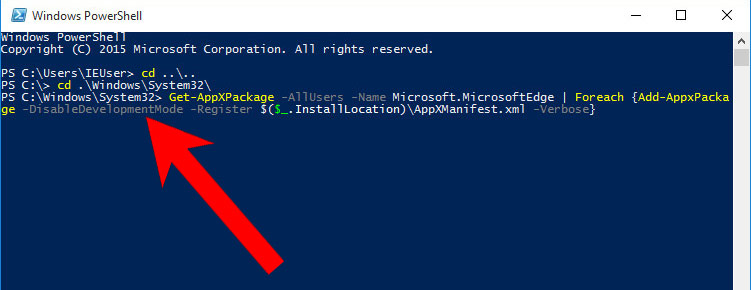
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
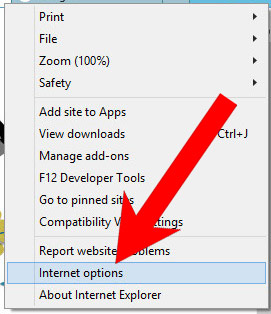
b) Remove I hacked your device from Internet Explorer
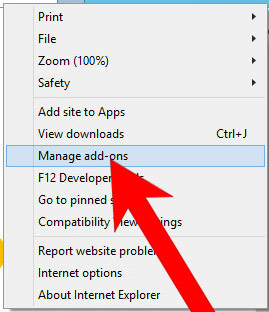
- Open Internet Explorer and press on the Gear icon.

- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
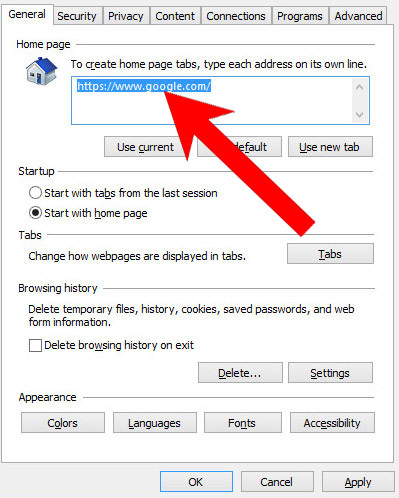
c) Restore your homepage on Internet Explorer
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
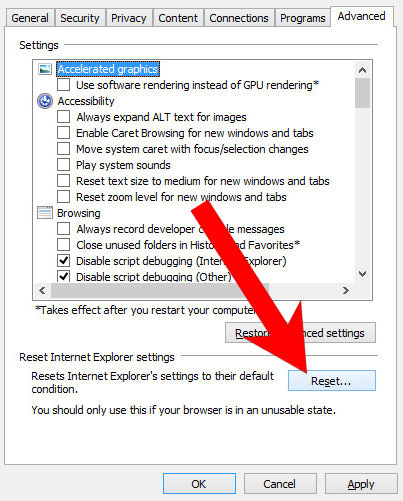
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

- At the bottom, you will see a Reset button. Press that.
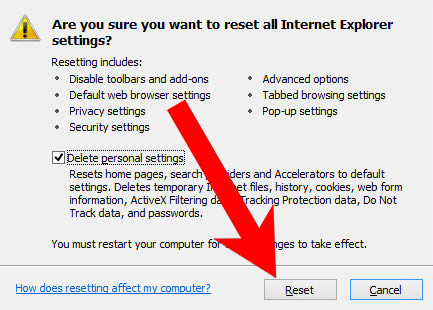
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
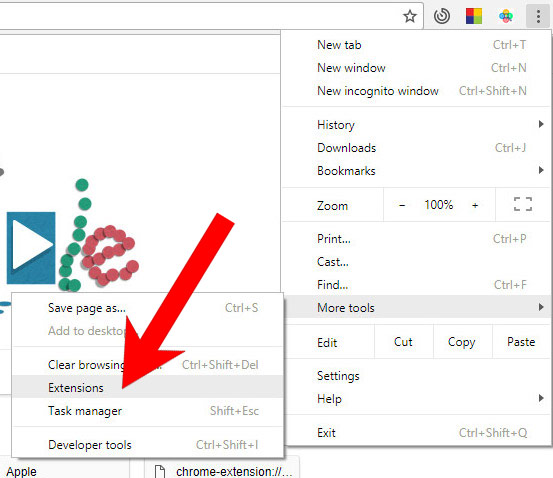
e) Remove I hacked your device from Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
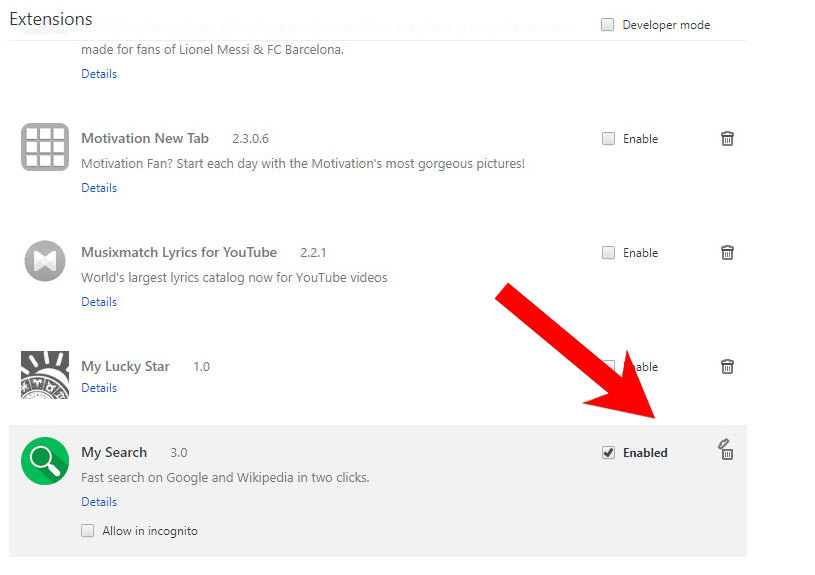
- Choose More tools and Extensions.

- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
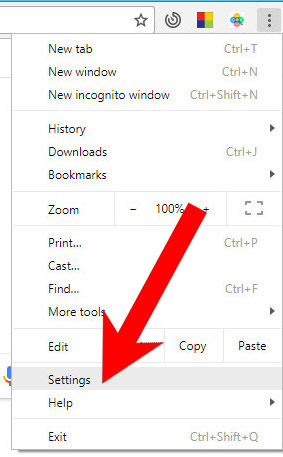
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

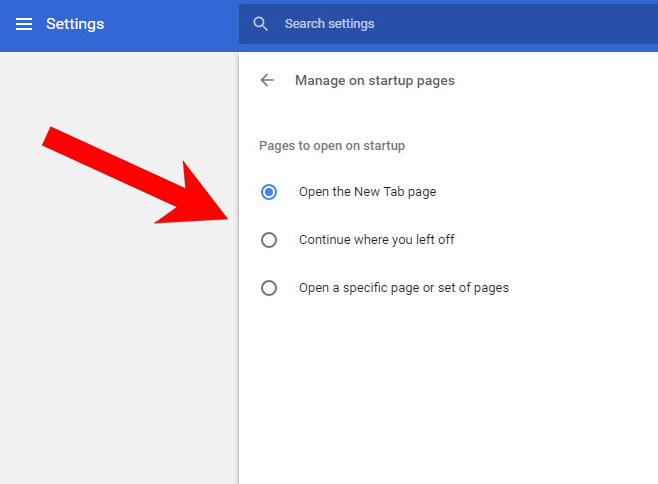
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

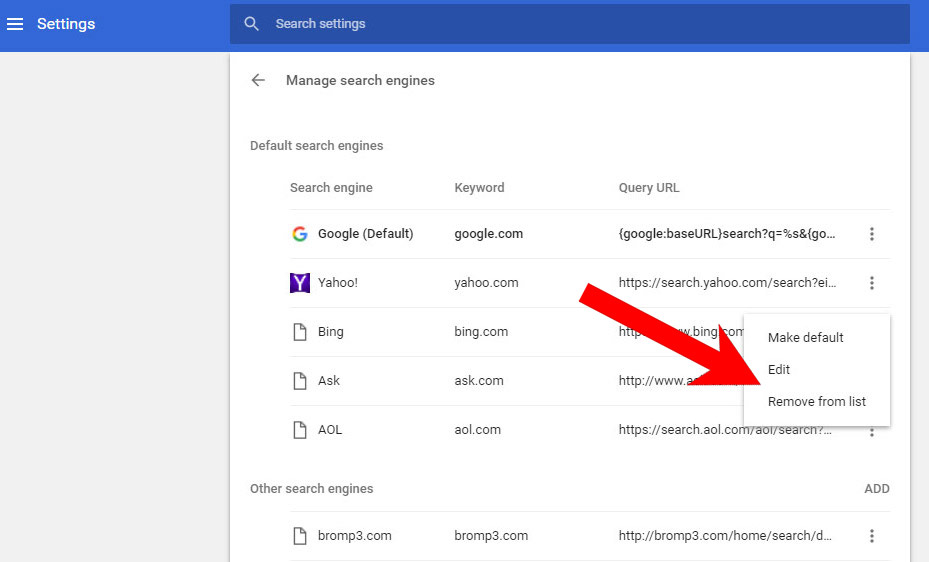
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
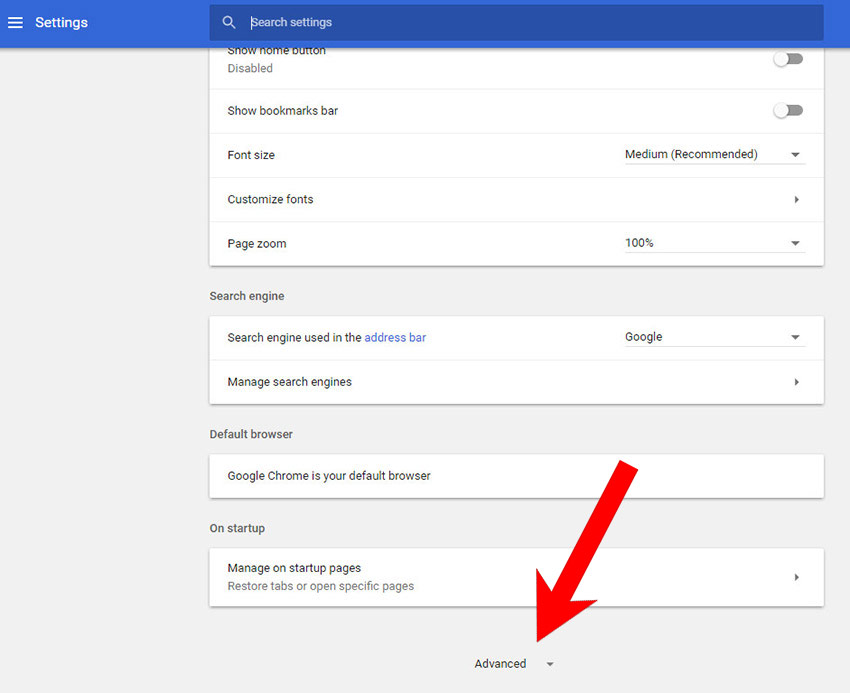
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

- Scroll down and press on Show advanced settings.

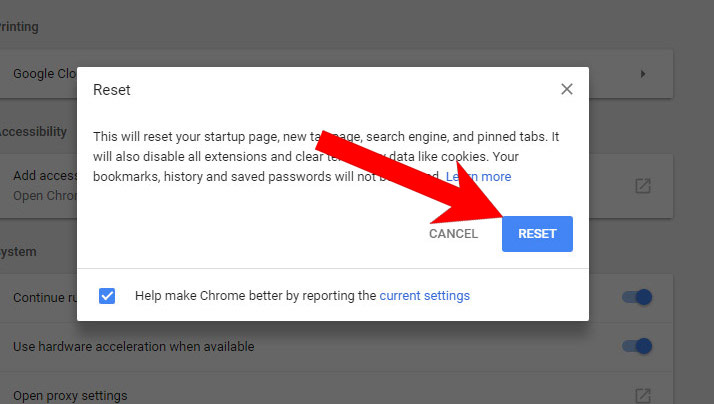
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
h) Remove I hacked your device from Mozilla Firefox
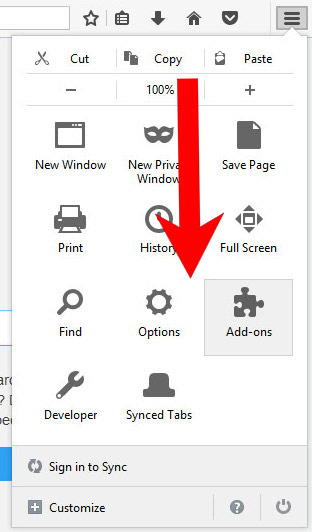
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
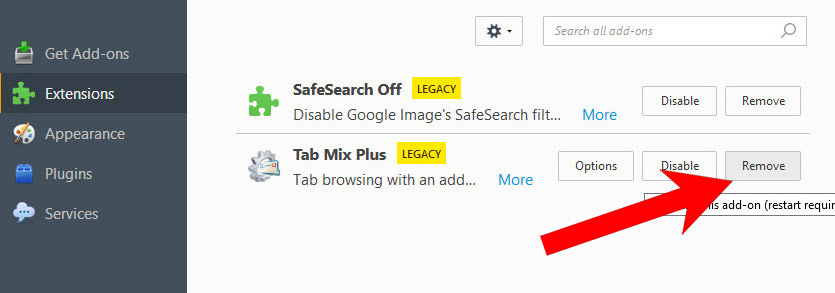
- Select Add-ons.

- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
i) Restore your homepage on Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
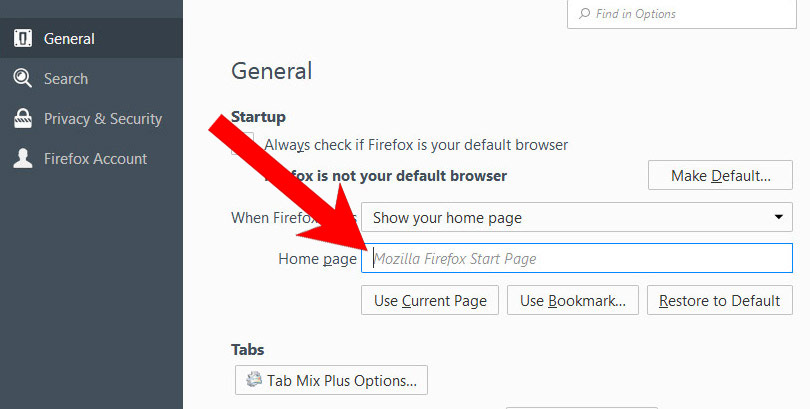
- Select Options.

- In General, click Restore to Default below the Home Page field.

j) Reset Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
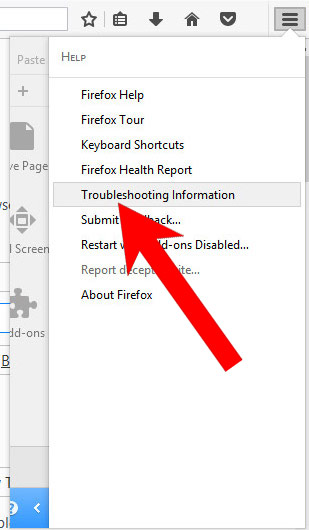
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

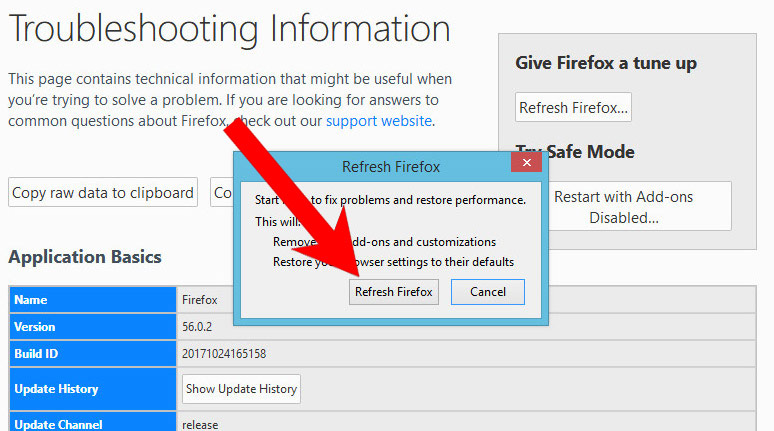
- Select the Refresh Firefox option.

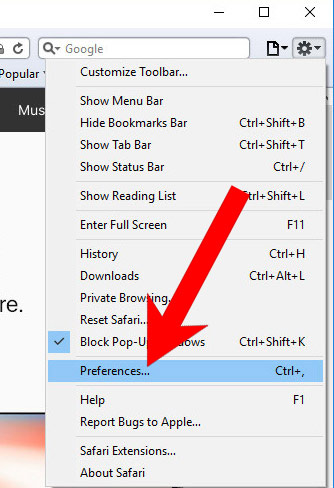
k) Remove I hacked your device from Safari (for Mac)
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

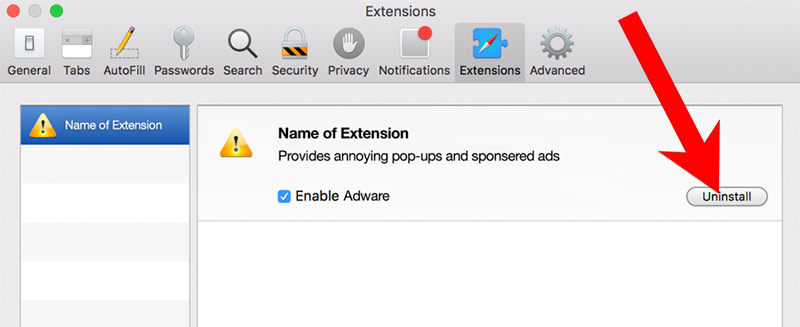
- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
l) Reset Safari
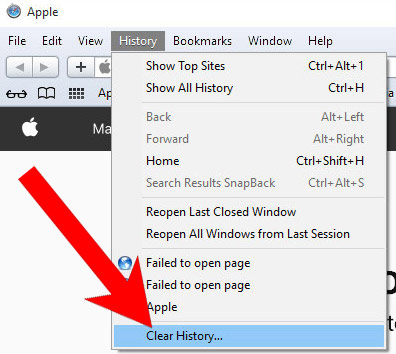
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

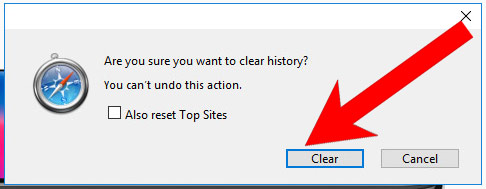
- Choose from what time you want the history deleted, and press Clear History.

- Press on Safari at the top of the screen and select Preferences.

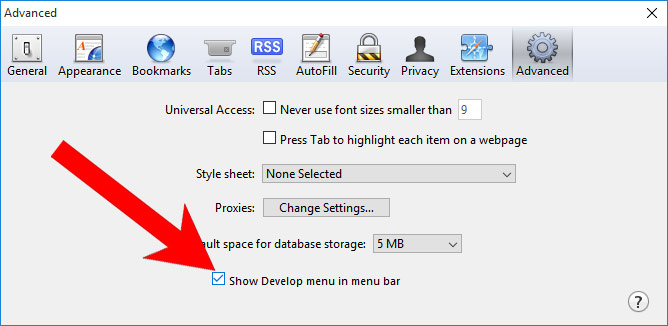
- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
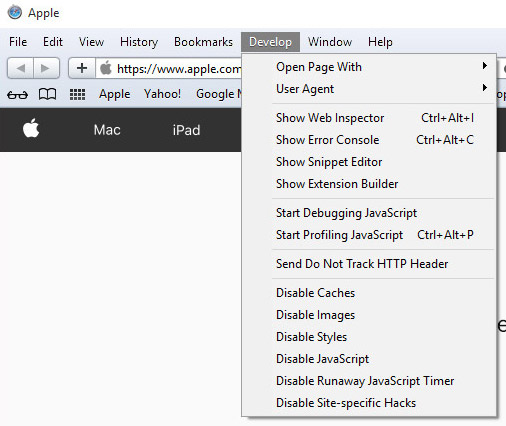
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.