I have succeeded to Gain a total access to all your devices
“I have succeeded to gain a total access to all your devices” is a very dangerous malicious threat capable of causing an array of harm on infected computers. “I have thrived to get a total entry to all your devices” belongs to the Trojan horse malicious software categorization and needs to be processed alongside alert if found. The “I have thrived to get a total entry to all your devices” Email malware
Dangers like Trojans, ransomware, malware and akin malevolent malware are not the sole safety threats that you may catch while searching the web. There are additionally quite a lot of hoaxes that attempt to trick gullible users and include them in corrupt cyber-criminal tricks.
Quite a lot of of our people reported to us relating to an in progress email spam along with the following notice:
I pity to warn you relating to some sad news for you.Approximately a month or two ago I have triumphed to get a total entry to all your operating systems used for surfing internet.Moving transfer, I have began tracking your internet habits on steady basis.
Download Removal Toolto remove haveProceed and check out the order of events added underneath for your reference:, at first, I purchased an special entry from crooks to an extensive list of email accounts (in today’s world, that is clearly a classic thing, that may organized via web).Evidently, it wasn’t troublesome for me to go ahead with collecting in your email account (“I have triumphed to get a total entry to all your devices””I have triumphed to get a total entry to all your devices””I have triumphed to get a total entry to all your devices””I have triumphed to get a total entry to all your devices”xx.com).
Inside the same week, I switched on in bundles with installing a Trojan malicious software in oss for all machines that you implement to login to email.Frankly speaking, it wasn’t a challenging mission for me at all (because you were group sufficient to click some of the hyperlinks in your inbox emails earlier).Yeah, geniuses are among us.
Due to this Trojan I am able to get access to whole set of controllers in machines (e.g., your video camera, keyboard, microphone and others).As outcome, I easily obtained all data, as well as photos, internet browsing history and other kinds of information to my servers.Moreover, I have entry to all social networks accounts that you usually use, involving emails, involving chat history, messengers, contacts category etc.My exceptional malware is incessantly refreshing its signatures (because of supervise by a driver), and therefore leftovers unidentified by any kind of antiviruses.
Hence, I assume by right now you can earlier see the argument why I always stayed surreptitiously until this highly letter…
During the procedure of assortment of all the materials related to you,I also found that you are a notable supporter and routine user of webpages hosting sinister adult content.Turns out to be, you extremely appreciate visiting porn websites, as well as watching interesting videos and tolerating eventful pleasures.As a issue of truth, I was unable to withstand the temptation, but to file multiple sinister solo motion in bundles with you in primary role,and afterwards invented several videos exposing your masturbation and cumming scenes.
Download Removal Toolto remove haveIf until these days you don’t think me, all I call for is one-two mouse clicks to set up all these kinds of videos in bundles with everybody you know,containing your friends, fellow workers, relatives and others.Moreover, I am able to upload all that video content internet for everybody to see.I sincerely believe, you undoubtedly would not desire such happenings to occur, in angle of the lustful things exhibited in your traditionally watched videos,(you wholly know what I suggest by that) it will set off a significant adversity for you.
There is regardless a remedy to this problem, and here is what you should do:You earn a transaction of $1340 USD to my account (an equivalent in bitcoins, which logged counting on the exchange rate at the date of funds transmit),thus upon receiving the transmit, I will nearly right away eliminate all of these kinds of lustful videos without delay.After that we can earn it appear like there was little taking place beforehand.Additionally, I can guarantee that all the Trojan program is going to be disabled and removed from all computers that you employ. You have little to be anxious connected to,as I keep my word at all times.
That is really a valuable voucher that travels with a reasonably decreased cost,bearing in mind that your profile and traffic were below exit overseeing during a lengthy time frame.If you are regardless cryptic in ragards to how to buy and execute transactions alongside bitcoins – all is available on the internet.
Beneath is my bitcoin wallet for your further reference: 16bHkVFULVmxTGVi2XKpwzkt5KrRnThzPg
All you have is 48 hours and the countdown starts earlier this email is started (that is to say 2 days).
The following classification inserts things you should keep in mind and block doing:> There’s no fact to try replying my email (because this email and go back address were released within your inbox).> There’s no purpose in calling police or any other kinds of stability functions either. Furthermore, don’t you dare distribution this data with any of your friends.If I find that (keeping in mind my capabilities, it shall be terribly unsophisticated, since I regulate all your devices and regularly supervise them) –your malevolent clip shall be scattered along with public straight away.> There’s no reason in searching for me too – it won’t lead to any success. Transactions in packages with cryptocurrency are utterly anonymous and untraceable.> There’s no meaning in reinstalling your computer system on computers or striving to throw them away. That won’t solve the problem,because all clips in addition to you as primary character are earlier uploaded on remote servers.
Things that might be connected to you:> That funds send won’t be shown to me.Breathe out, I can monitor down all promptly, so the minute funds send is complete,I shall know definitely, as I interminably monitor down all actions carried out by you (my Trojan malicious software owns all procedures remotely, just as TeamViewer).> That your videos shall spread, in spite of the fact that you have done income send to my wallet.Trust me, it is not useful for me to regardless aggravate you after income send is successful. Moreover, if that was ever an item of my scheme, I would do generate it take place way former!
We are about to scheme and manage it in a noticeable scheme!
In outcome, I’d like to encourage one etc. thing… after this you should make several you don’t get entangled in akin fairly bad events anymore!My suggestion – assure all your passwords are modified alongside new ones on a daily basis.
Unfortunately, the use of internet deceits, scam emails and deceitful declares has turned onto a well-paid industry for quite some users together with contaminated objectives and, newly, there have been tons of declarations related to the improving number of diverse ploys and criminal ploys. For example, a viral email Bitcoin trick campaign has been circulating everywhere recently and has been causing worry and fury for a big amount of users.
If you are one of those victims oriented by this exact hoax, then you the biggest part of possibly have gotten a frightening email notification in your inbox that states there’s a dormant Trojan horse malicious software inside your pc. And if you don’t pay a specific quantity of income (in Bitcoin) to the cyber crook behind the parasite, they risk to swich on the Trojan and crisis with your computer. Emails along with this scheme are generally little but a deception that shouldn’t be redirected at happen upon discount. Their purpose is to terrorize people and earn them pay income to some self-advertised crooks as without any actual logic.
However, every now and then, these kinds of alerts could contain some authentic malicious software and when you start or communicate with them, you may download infected by a authentic Trojan horse together without comprehending it, e.g “I have thrived to get a total entry to all your devices” and Geek Squad Email. That’s why you have the complete right to be concerned that there might actually be malicious software in your pc if you have pressed on a single of them newly.
Scrambling to fulfill the penalty inquiries of some anonymous hackers and thinking their notifications, on the other hand, isn’t advised. In truth, we suppose it is a much more reliable alternative to merely scan your operating system for infection together with a trusted defense utility and try to uninstall any likely undisclosed perils that the analyze identifies.
Be wary of emails that distribute viruses!
Being spammed in addition to dozens of emails that ask you to pay fine so to avoid invisible parasite from causing damage to your machine is a classic cyber-criminal trick. A ruse that merely intentions to spook users and produce reckless profit for the criminals as behind the plan. And even if there is no authentic argument to assume one of the assertions in the alerts or relay any revenue to someone, you regardless have to not ignore the fact that risks like “I have triumphed to get a total entry to all your devices” can be detected in such alerts and a authentic malicious software may transpire without your skill.
Like allmost all Trojan-based bits of malicious viruses, this one could be greatly stealthy and can lie dormant without any apparent indications until the crook picks to turn on it and to breach the machine. For this argument, if you have newly been overflown with email hoax notifications and have interacted together with them, it is exceedingly crucial that you make sure your system is malware-free and there is nothing harmful on it which can cause you damage when you least anticipate it. In this identify, underneath we have developed a detailed removal guidelines and a specialist scanner application that may assist you to watch your system and delete “I have thrived to get a total entry to all your devices”.
Learn how to remove have from your computer
Step 1. have Removal from Windows
a) Windows 7/XP
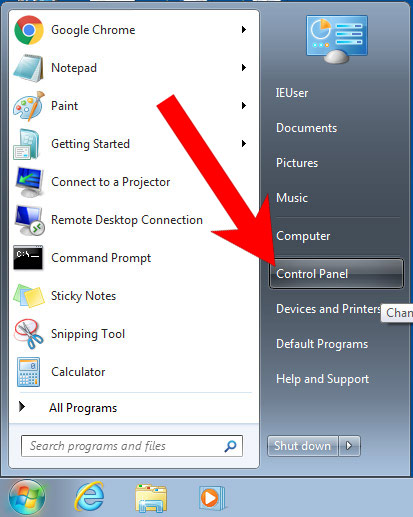
- Press on the Start icon.

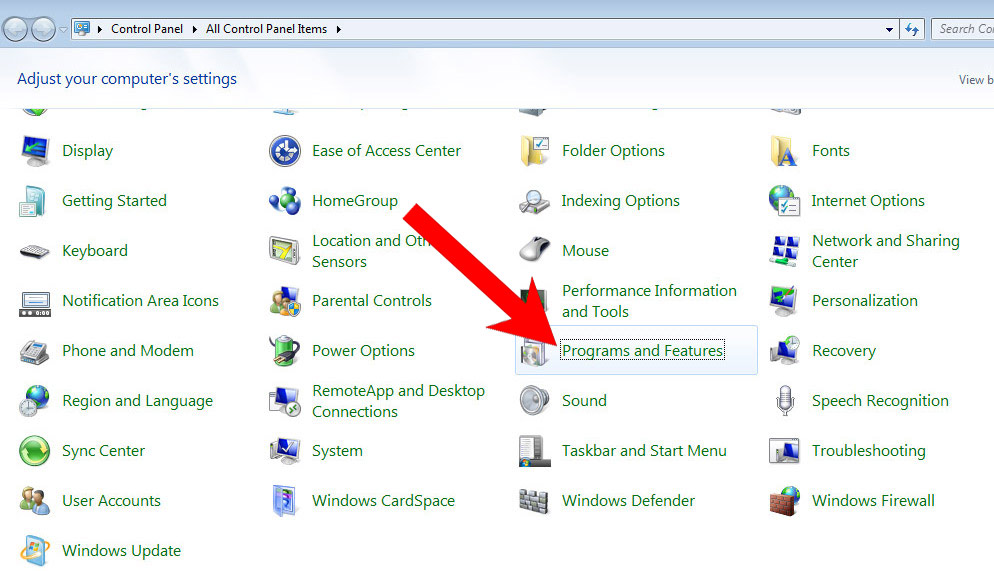
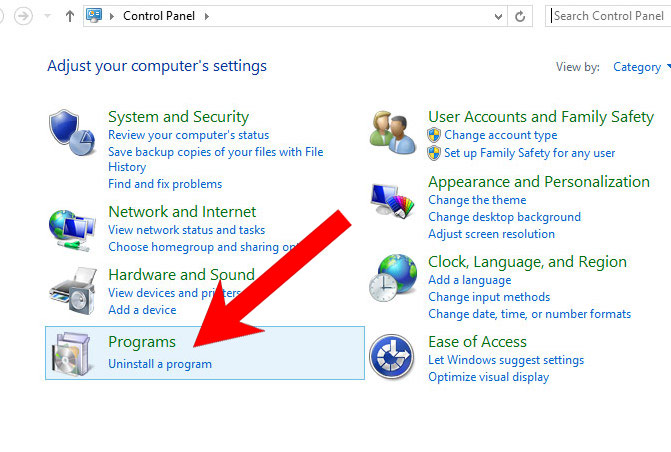
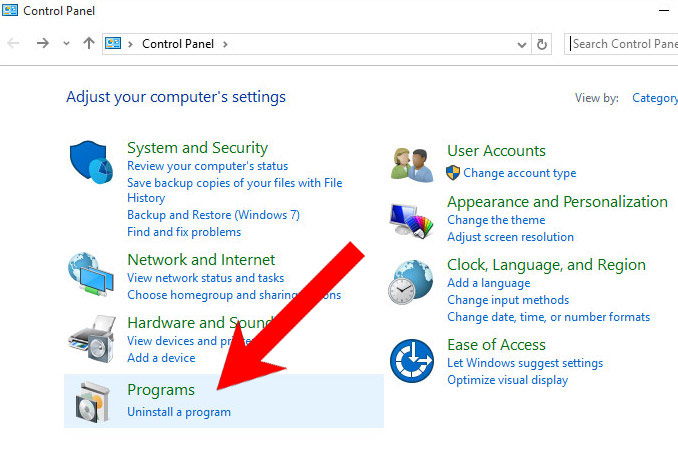
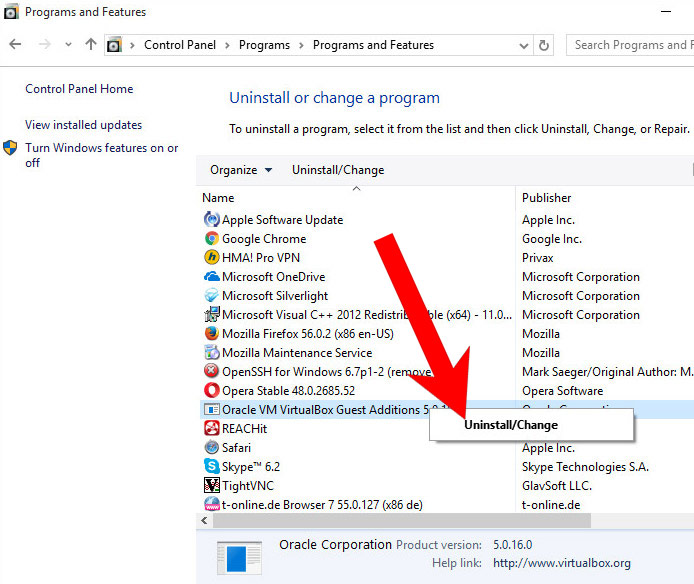
- Control Panel → Programs and Features.

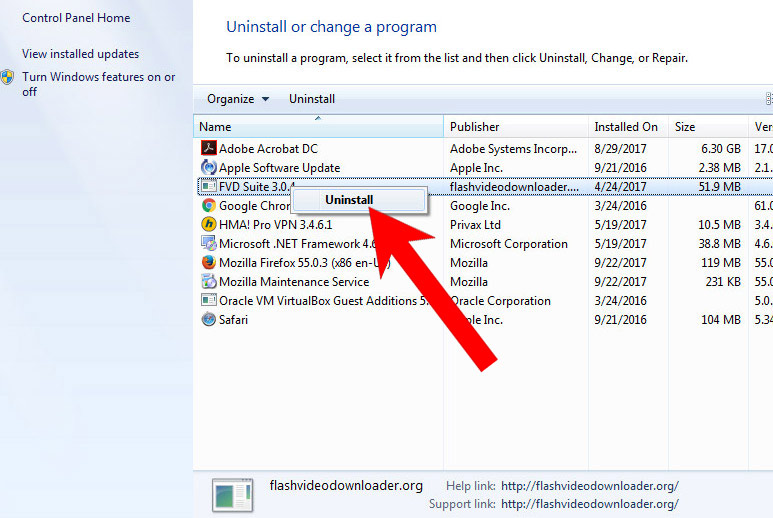
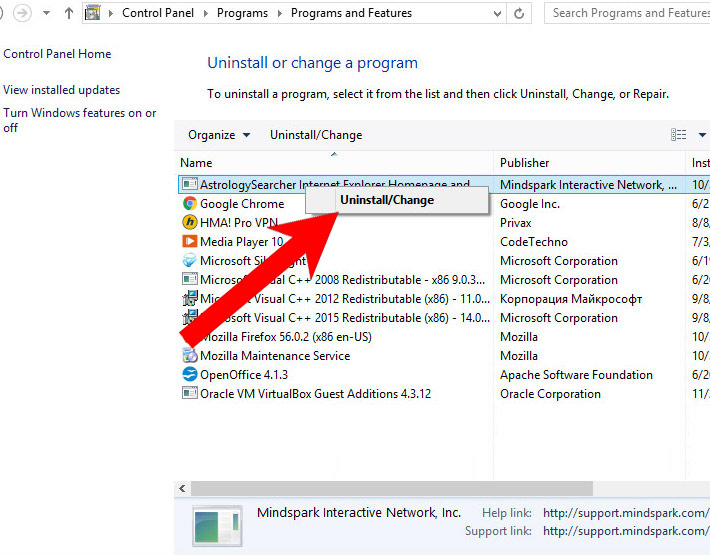
- Find the program you want to delete and press Uninstall.

b) Windows 8
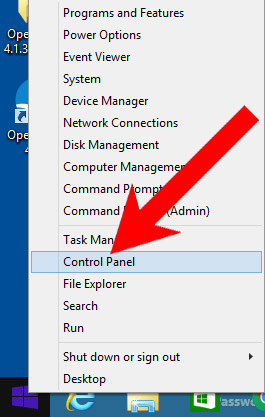
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

c) Windows 10
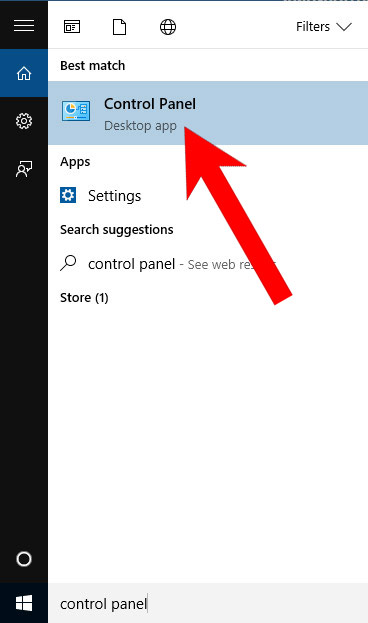
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

d) Mac OS X
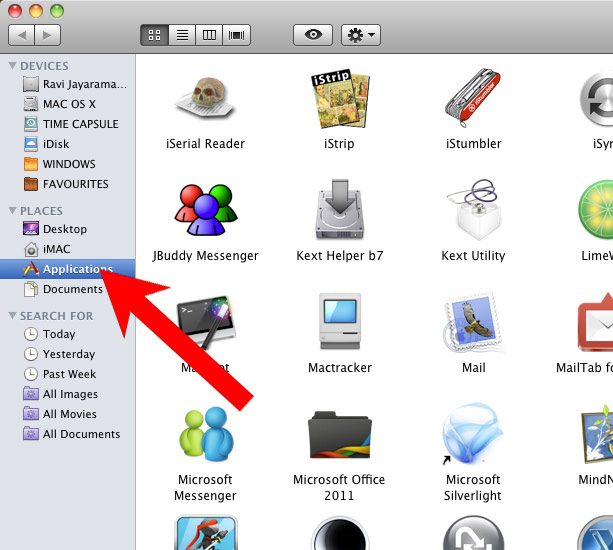
- Open Finder and press Applications.

- Check all suspicious programs you want to get rid of.
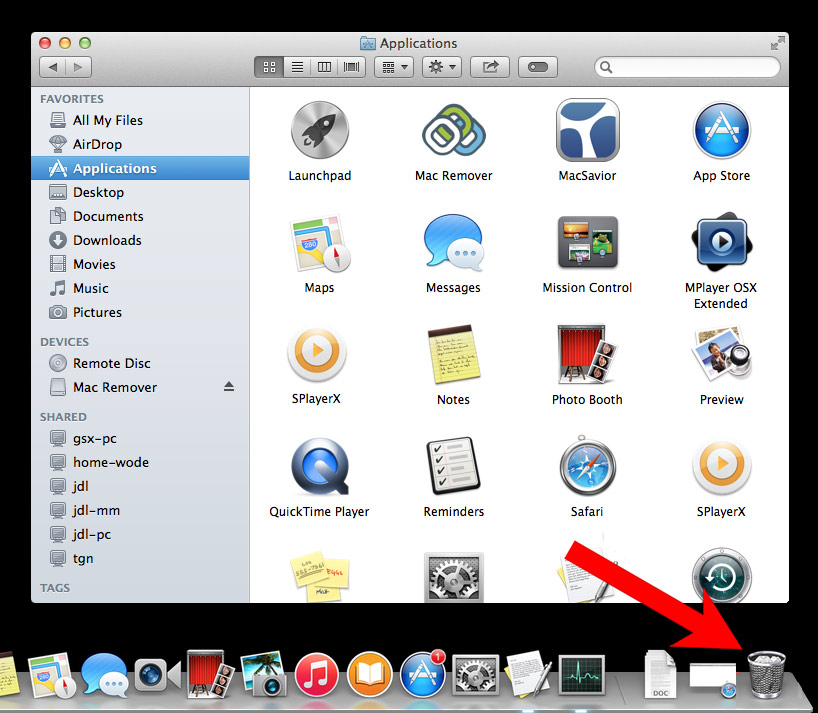
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete have from browsers
a) Remove have from Microsoft Edge
Reset Microsoft Edge (Method 1)
- Open Microsoft Edge.
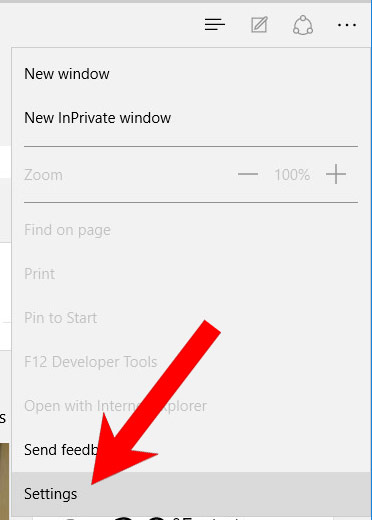
- Press More located at the top right corner of the screen (the three dots).

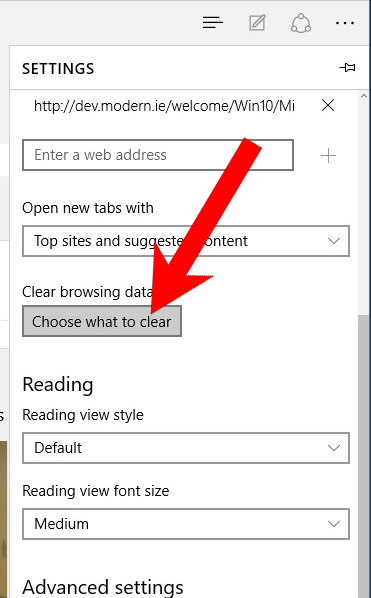
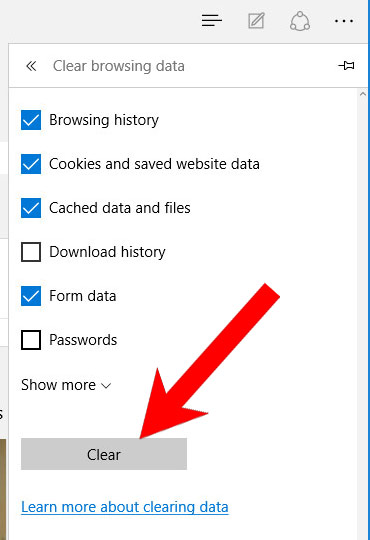
- Settings → Choose what to clear.

- Check the boxes of the items you want removed, and press Clear.

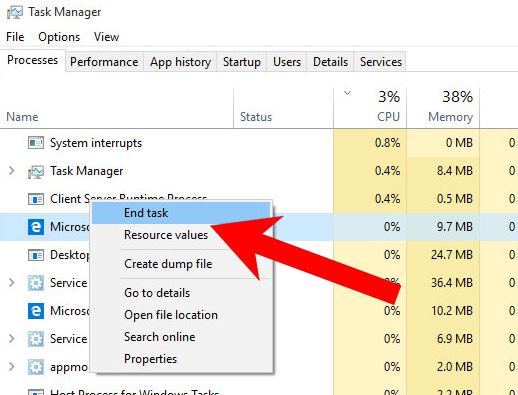
- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
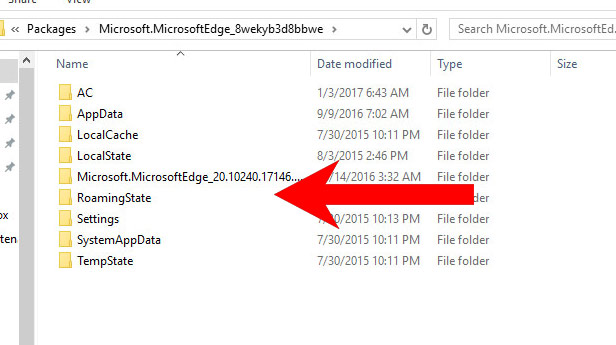
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

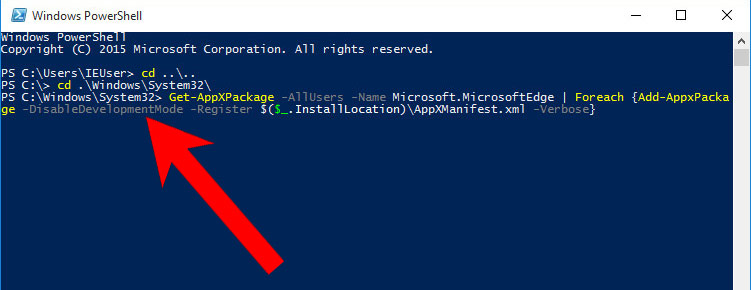
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
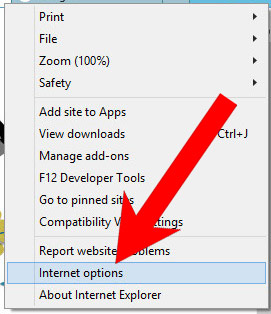
b) Remove have from Internet Explorer
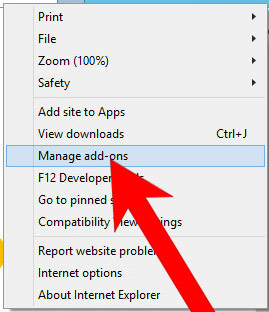
- Open Internet Explorer and press on the Gear icon.

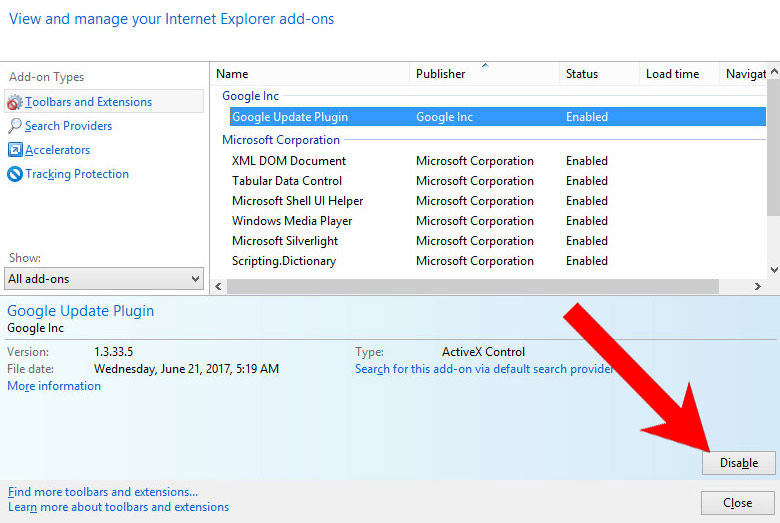
- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
c) Restore your homepage on Internet Explorer
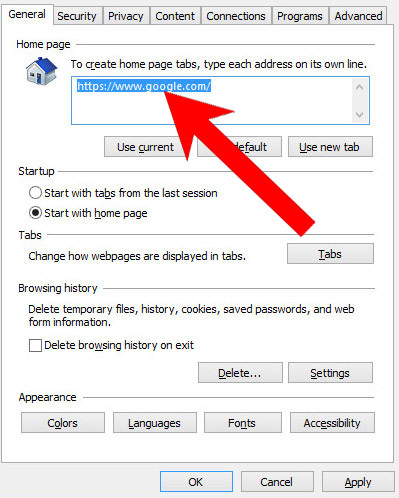
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
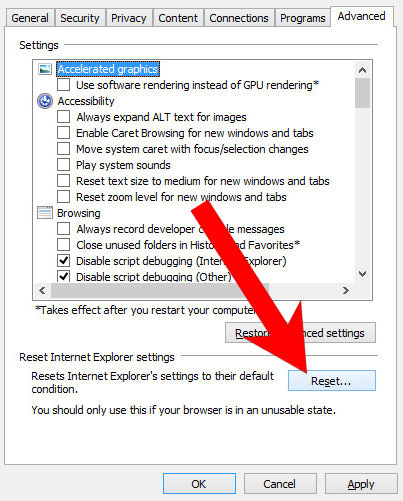
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

- At the bottom, you will see a Reset button. Press that.
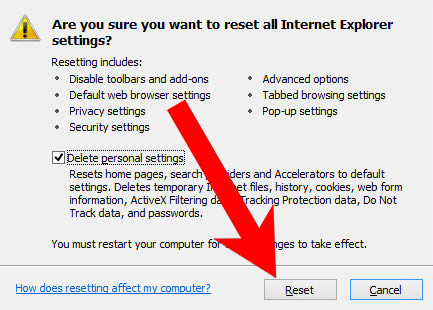
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
e) Remove have from Google Chrome
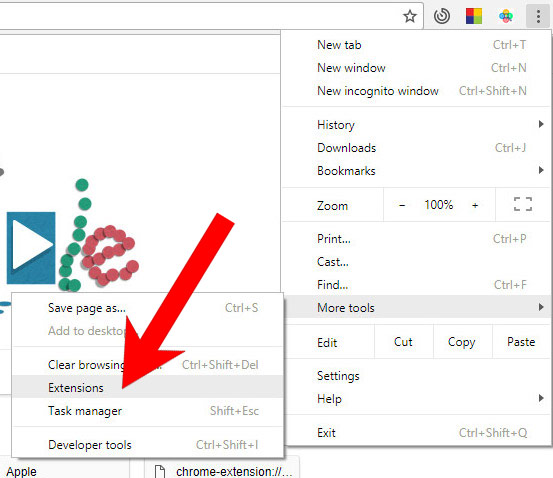
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose More tools and Extensions.

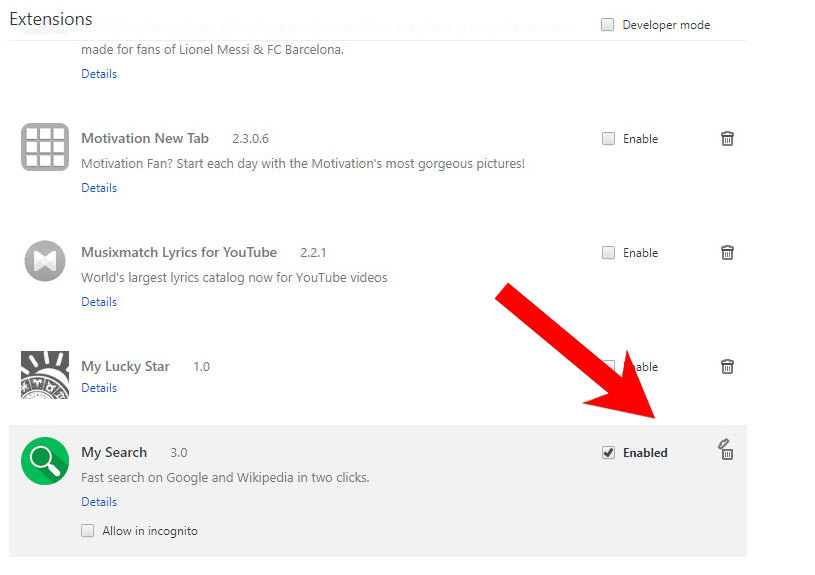
- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
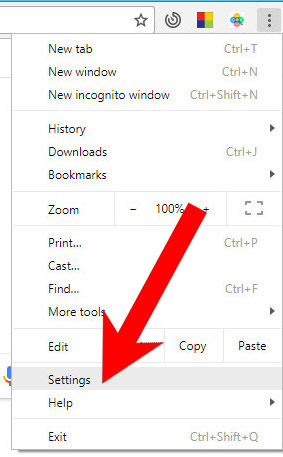
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

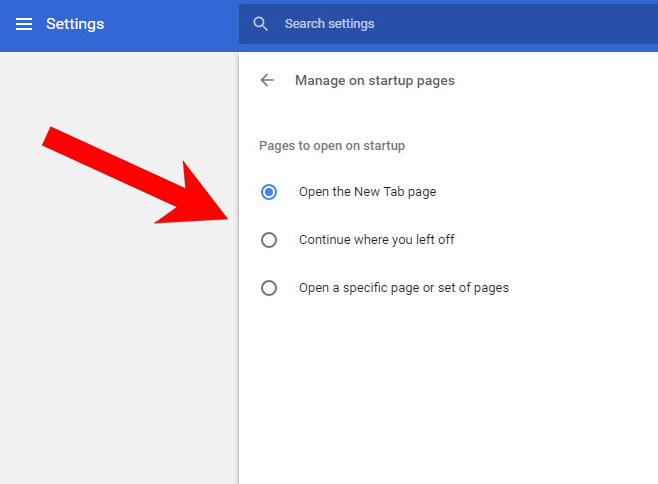
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

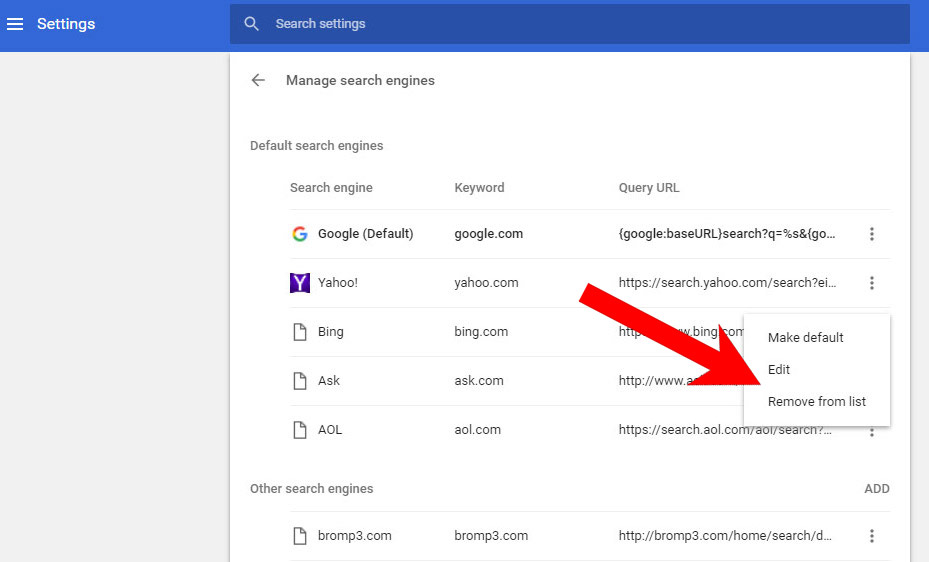
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
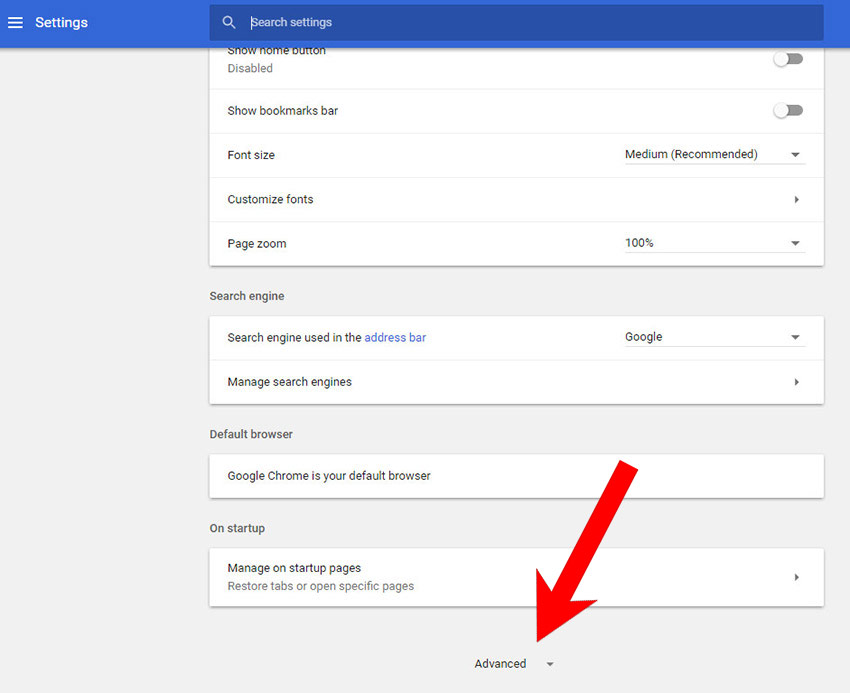
- Choose Settings.

- Scroll down and press on Show advanced settings.

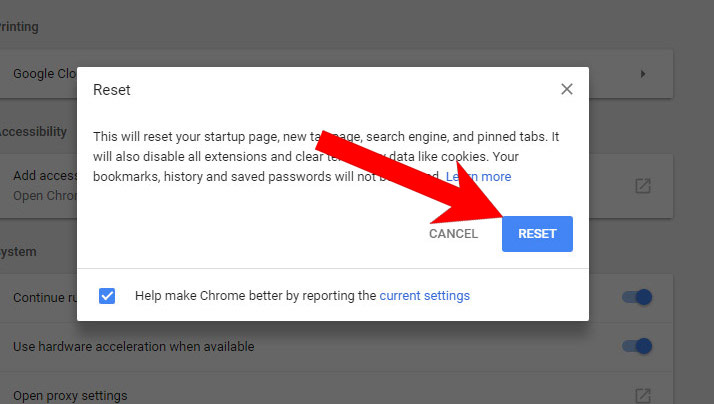
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
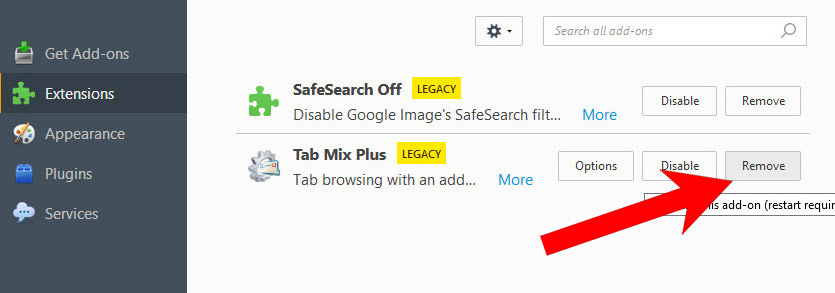
h) Remove have from Mozilla Firefox
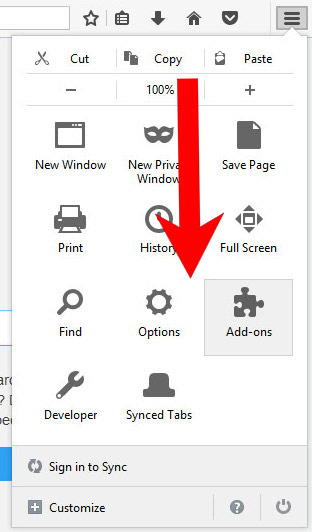
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Select Add-ons.

- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
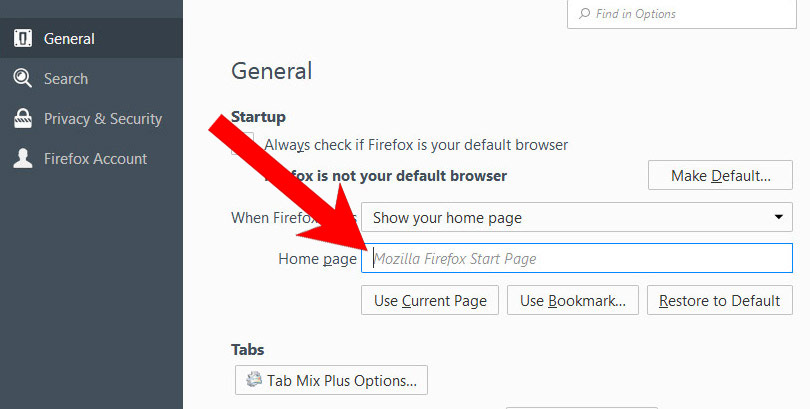
i) Restore your homepage on Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
- Select Options.

- In General, click Restore to Default below the Home Page field.

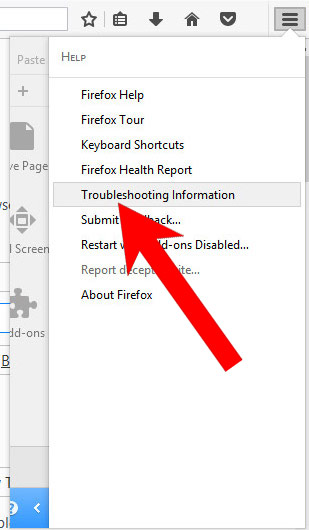
j) Reset Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Press the question mark at the bottom of the menu.
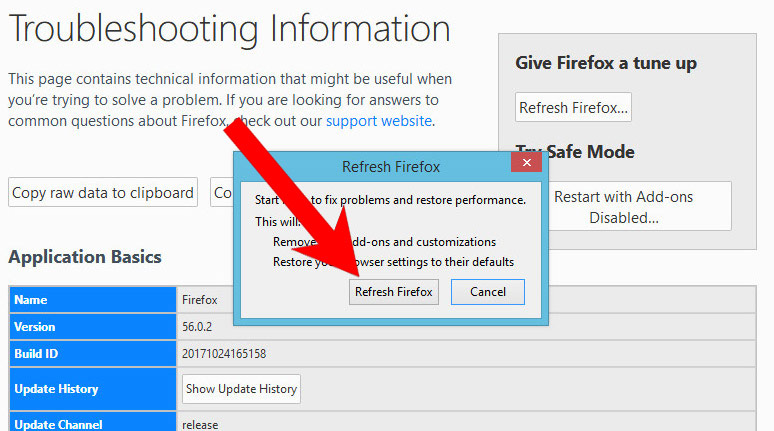
- Select Troubleshooting Information.

- Select the Refresh Firefox option.

k) Remove have from Safari (for Mac)
- Open Safari.
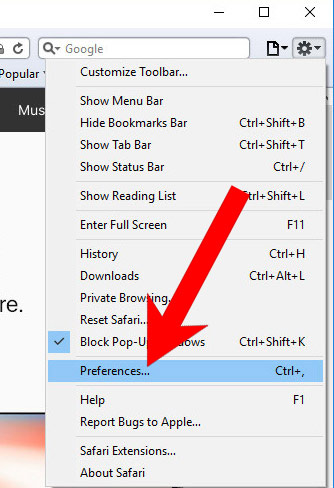
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

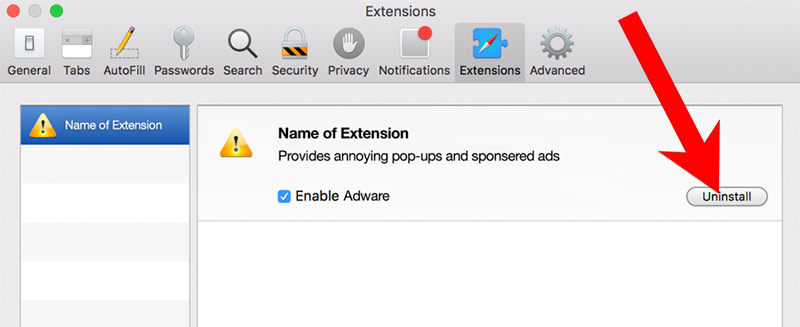
- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
l) Reset Safari
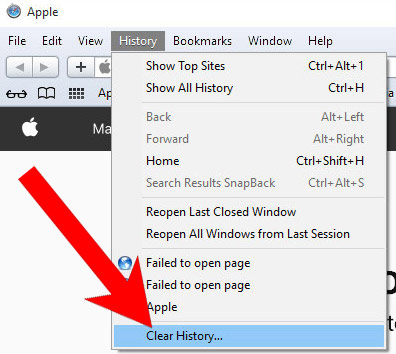
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
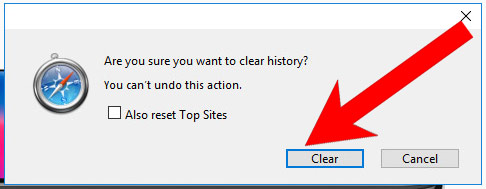
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

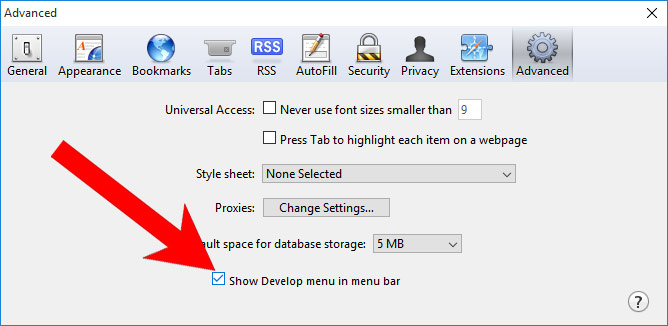
- Press on Safari at the top of the screen and select Preferences.

- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
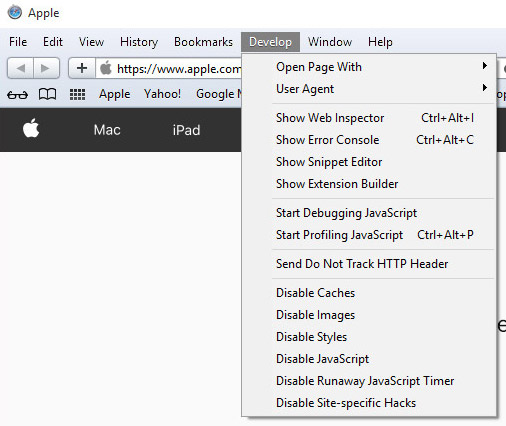
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.