The intention of a exhibited Trojan horse malware relies on the position and on what the cyber criminals behind it are attemptinG to attain.
For example, a malware for instance “Payment from your account” can be used to accumulate sensitive confidential information from your computer by undetected watching on you until it makes data it may use against you. Counting on what sort of information the dangerous application saves from your pc, it may afterwards use it as blackmailing an advantage or, if the infection has purchased your credit/debit card quantities, it may straightaway use your monetary accounts and transfer the income to to cyber criminals.
Quite a lot of of our people reported to us relating to an in progress email spam along with the following notice:
Subject: Payment from your account. Greetings! I need to share bad news in bundles with you. Approximately few months ago I have gotten entry to your pcs, which you use for net surfing. After that, I have began observing your internet habits. Here is the order of events: Some time ago I have bought entry to email accounts from criminals (nowadays, it is rather not sophisticated to acquire such thing on the internet). Obviously, I have smoothly was able to log in to your email account (************). One week afterwards, I have earlier set up Trojan malware software to machines of all the computers that you implement to entry your email. In truth, it was not very difficult at all (because you were following the hyperlinks from your inbox emails). All brilliant is unsophisticated. =) this application presents me in bundles with entry to all the controllers of your computers (e.g., your microphone, video camera and keyboard). I have collected all your details, information, photos, internet browsing history to my servers. I get entry to all your messengers, social networks, emails, chat history and contacts classification. My malware frequently refreshes the signatures (it is driver-based), and thus traces hidden for anti-spyware utility applications. Likewise, I assume by now you realize why I have remained in a hidden manner until this letter… although collecting information about you, I have uncovered that you are a big fan of adult pages. You terribly appreciate visiting porn web pages and watching interesting videos, as long as tolerating a big amount of amusement. Well, I have was able to document a load of your dirty scenes and montaged several videos, which display the way you masturbate and come to orgasms. Should you have questions, I might develop a few clicks of my mouse and all your videos shall be circulated to your friends, fellow colleagues and relatives. I have additionally no problem at all to create them available for public entry. I assume, you highly don’t are keen that to occur, thinking about the specificity of the videos you like to watch, (you wholly know what I suggest) it will trigger a valid catastrophe for you. Let’s resolve it that way: You send $1500 USD to me (in bitcoin equivalent according to the exchange rate at the minute of funds transfer), and earlier the send is gotten, I will erase all this dirty stuff instantly. Afterwards we shall discard related to every other. I in addition to that vow to shut off and terminate all the harmful program from your systems. Faith me, I keep my word. This is a fair deal and the cost is reasonably low, taking into mind that I have been scanning out your profile and traffic for quite some time by now. In case, if you don’t know how to acquire and transmit the bitcoins – you can make use of any contemporary search engine. Here is my bitcoin wallet: 1GGZpqXsqKWSRnjJ1SHFaE5VPkMHHsKToX You have fewer than 48 hours from the minute you started this email (exactly 2 days). Things you should avoid from doing: *Do not answer me (I have composed this email into your inbox and created the go back address). *Do not seek to contact police and other defense functions. In addition, ignore relating to mentioning this to you friends. If I locate that (since you may see, it’s absolutely not so complex, taking into mind that I regulate all your computers) – your video shall be circulated to public immediately. *Don’t try to discover me – it is totally useless. All the cryptocurrency transactions are anonymous. *Don’t try to reinstall the device on your pcs or throw them away. It is useless and as well, because all the videos have earlier been saved at remote servers. Things you don’t need to be concerned about: *That I won’t have an opportunity to get your funds transmit. – Don’t be stressed, I will notice it straightaway, as soon as you perform the transmit, as I regularly observe all your movements (my trojan malicious software has got a remote-regulate trait, something like TeamViewer). *That I shall share your videos anyway after you carry out the funds transmit. – faith me, I have no truth to carry on developing disruptions in your life. If I very planned that, I would do it drawn-out time ago! All shall be conducted in a fair scheme! One etc. thing… Don’t get detected in connected somewhat instances anymore in future! My recommendations – keep switching all your passwords on a usual basis
Download Removal Toolto remove from your
The Payment from your account email
Another steady use of malware like the “Payment from your account” email is when they permit the cyber crooks behind them to remotely launch varying procedures on your machine without your consent or knowledge. Oftentimes, the procedures started on the affected machines are ones that force the operating system to mine cryptocurrency (for example bitcoins).
As long as this does not straightaway wreck the device or risk your privacy, it may earn the device almost useless as the resources spent on the cryptocurrency mining procedure have a tendency to close nothing to little for other functions. This would, in turn, generate the os hugely slow and likely to freezes and crashes. Until the malicious software is terminated, you won’t be able to forbid it from forcing your pc to use a majority of (if not all) of its free-of-charge RAM, CPU, and GPU for the mining procedure.
Trojans e.g “Payment from your account” should also be potent malicious software spread tools. In quite a great deal of instances, the major parasite that infiltrates the os won’t be the Trojan itself, but another malicious software that the Trojan brings to your os. This is generally the case alongside malicious software of the notorious Ransomware cryptovirus classification. These risks are generally shown to the pcs of their likely victims together with a Trojan horse infection that has earlier compromised the oriented device. In a lot of situations, the Trojan may also run as a rootkit (or download a rootkit) on the contaminated operating system. A rootkit is part of malicious programs that is capable of hidden its existence and the existence of other infections in the pc. The existence of a rootkit Trojan on the device might mean that the Ransomware (or any other parasite) would be free-of-charge to function without any endanger of it collecting detected by the user or the anti-malware utility existing on the system.
Download Removal Toolto remove from yourDeleting “Payment from your account”
If you suspect that your operating system may at the present moment be contaminated by “Payment from your account”, it is of amazing significance that you take instantaneous measure towards clearing your system from any item of information that might be connected to the Trojan. Our offer for you is act in accordance with the removal instructions by hand you will discover beneath. Finish every stage precisely as exhibited and, by the end of the instructions, you ought to have administered to fully uninstall the malicious Trojan malware.
Learn how to remove from your from your computer
Step 1. from your Removal from Windows
a) Windows 7/XP
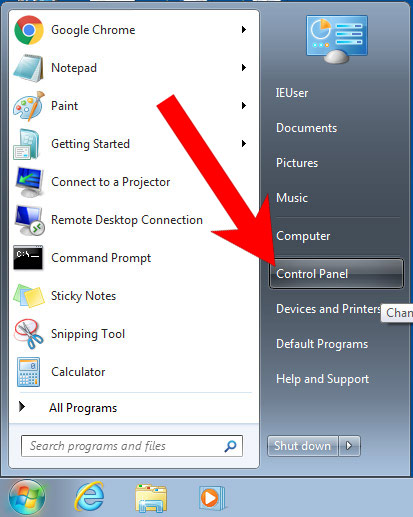
- Press on the Start icon.

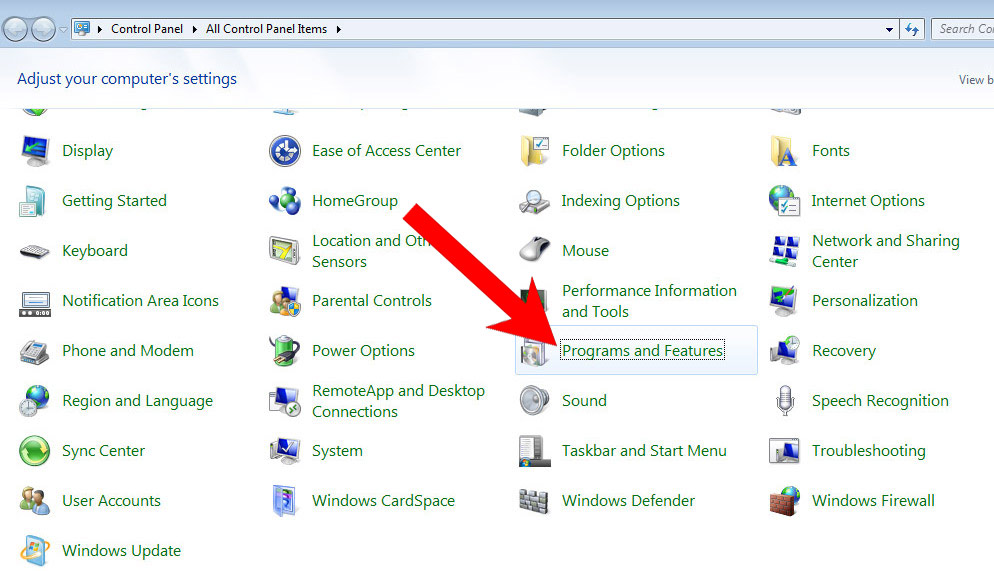
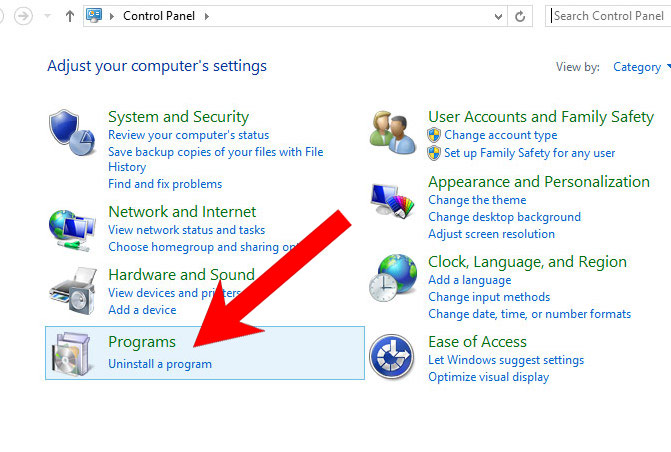
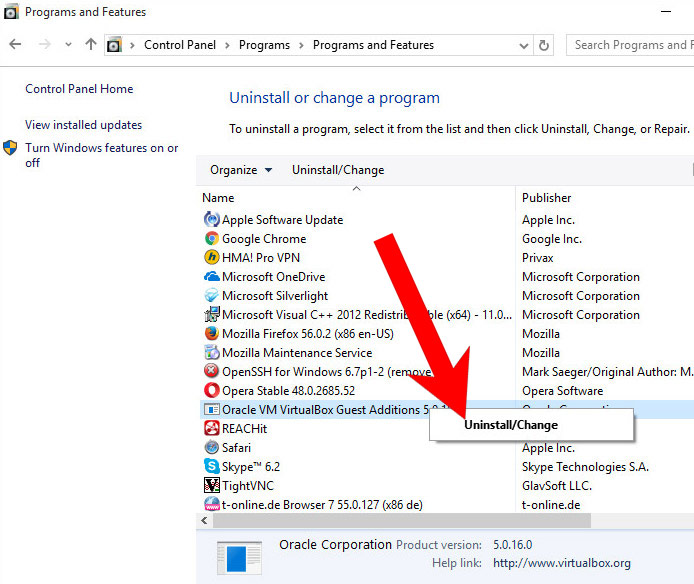
- Control Panel → Programs and Features.

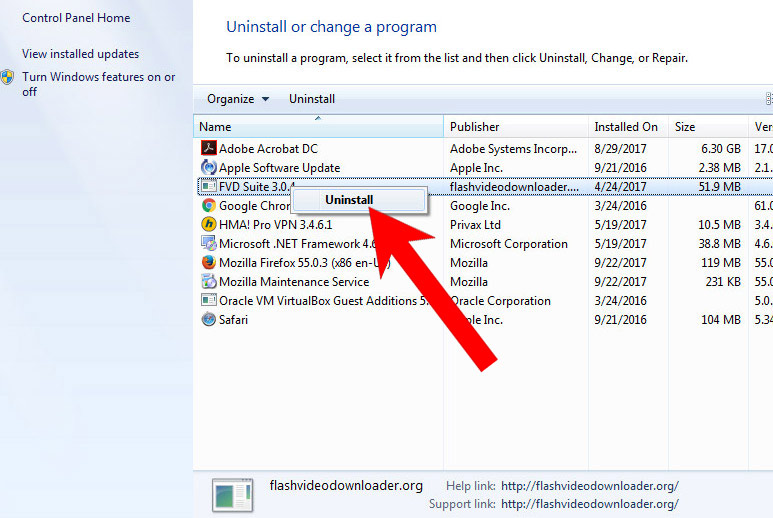
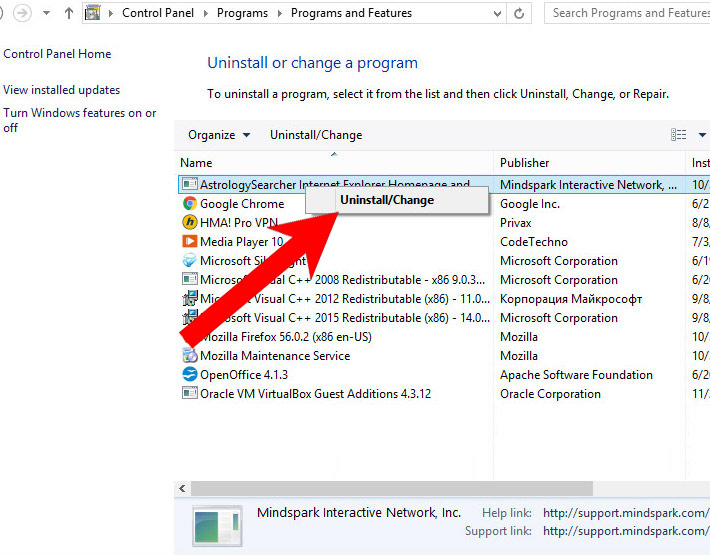
- Find the program you want to delete and press Uninstall.

b) Windows 8
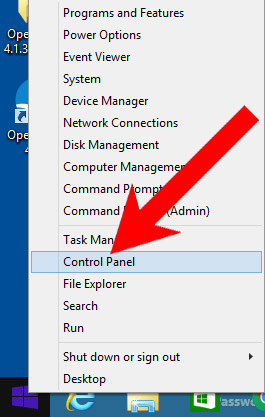
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

c) Windows 10
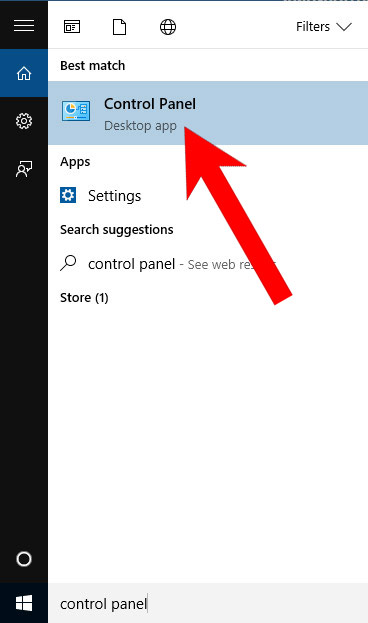
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

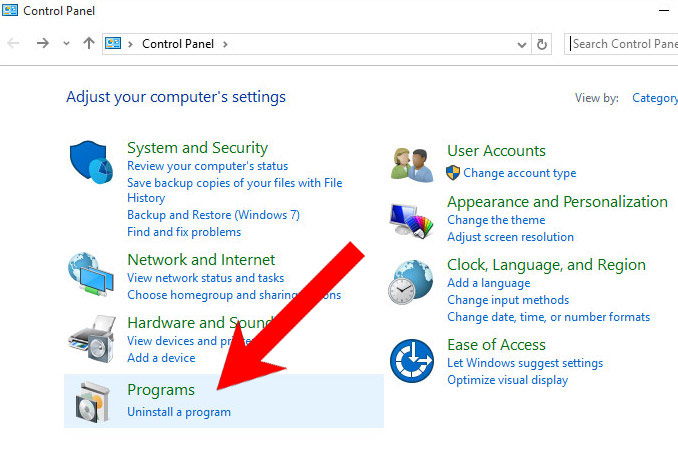
- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

d) Mac OS X
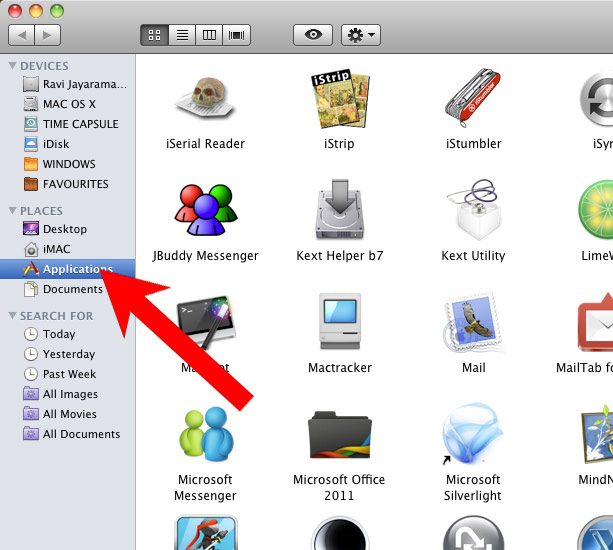
- Open Finder and press Applications.

- Check all suspicious programs you want to get rid of.
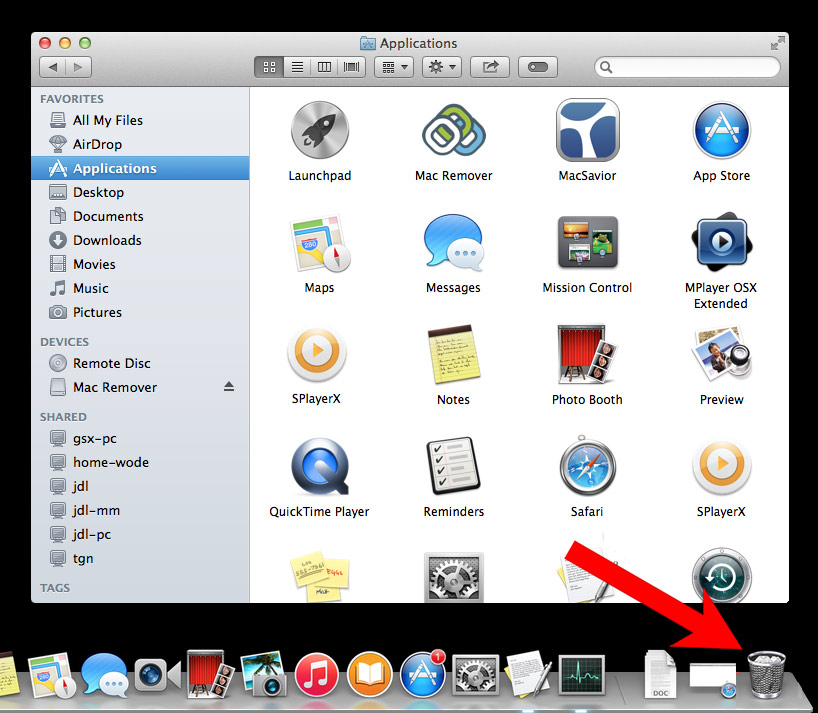
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete from your from browsers
a) Remove from your from Microsoft Edge
Reset Microsoft Edge (Method 1)
- Open Microsoft Edge.
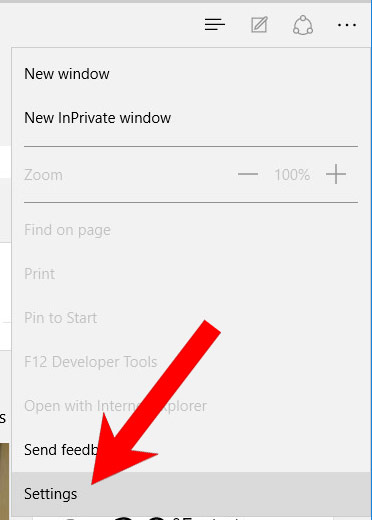
- Press More located at the top right corner of the screen (the three dots).

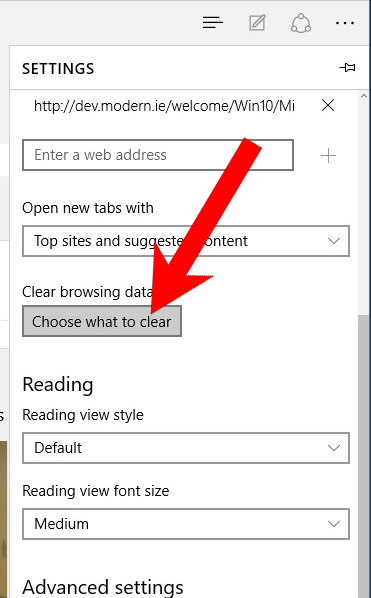
- Settings → Choose what to clear.

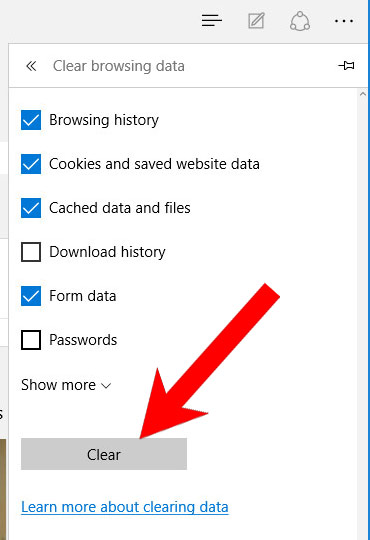
- Check the boxes of the items you want removed, and press Clear.

- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
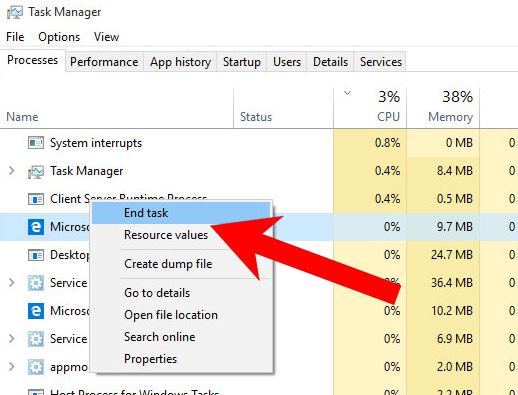
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
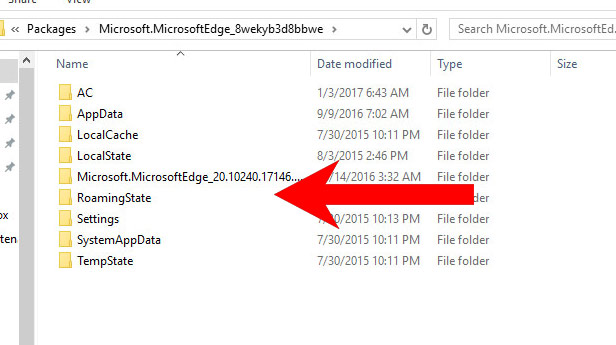
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

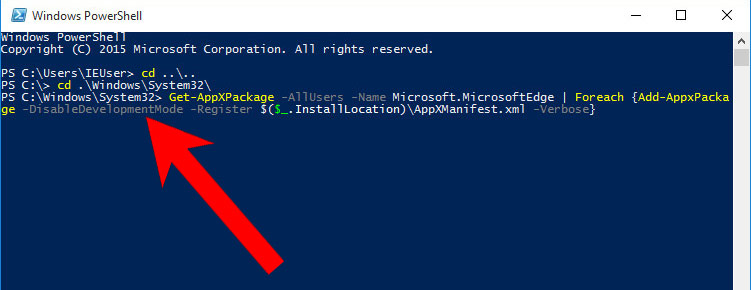
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
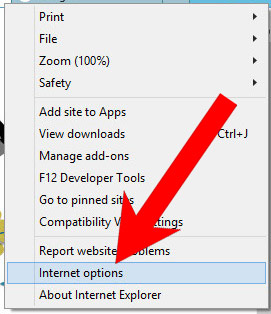
b) Remove from your from Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
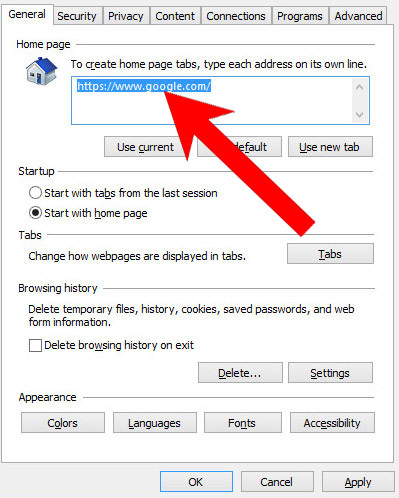
c) Restore your homepage on Internet Explorer
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
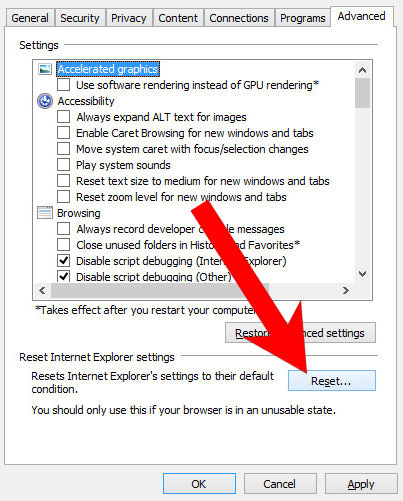
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

- At the bottom, you will see a Reset button. Press that.
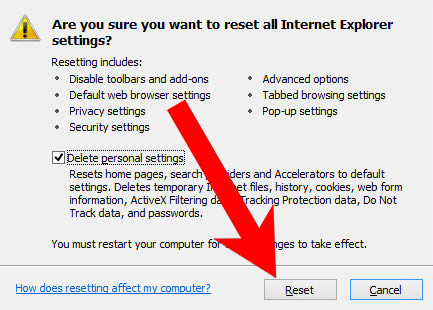
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
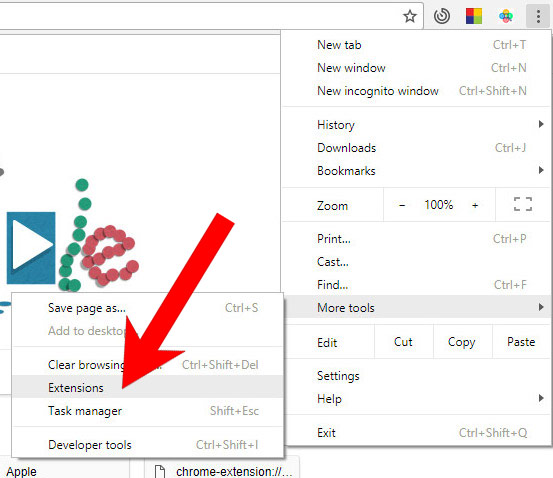
e) Remove from your from Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose More tools and Extensions.

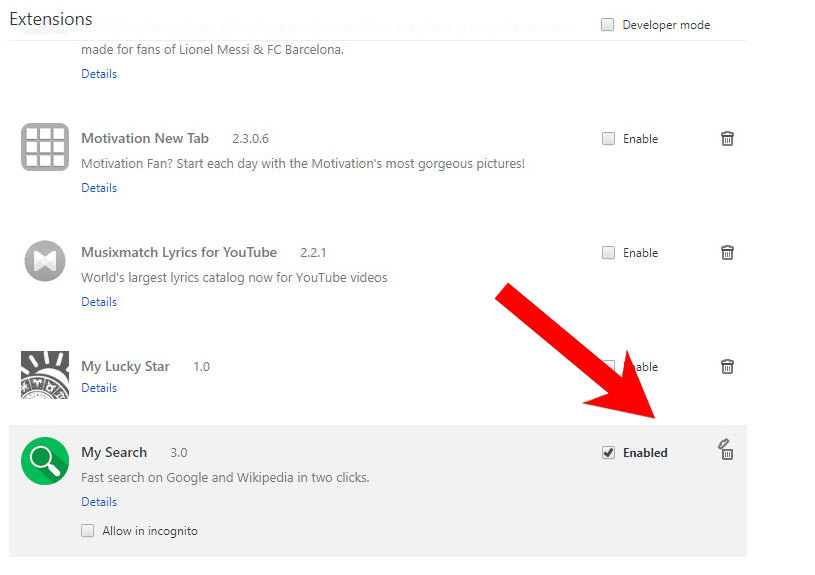
- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
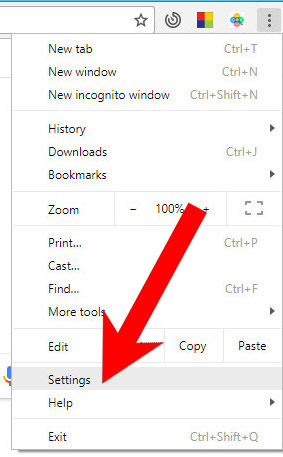
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

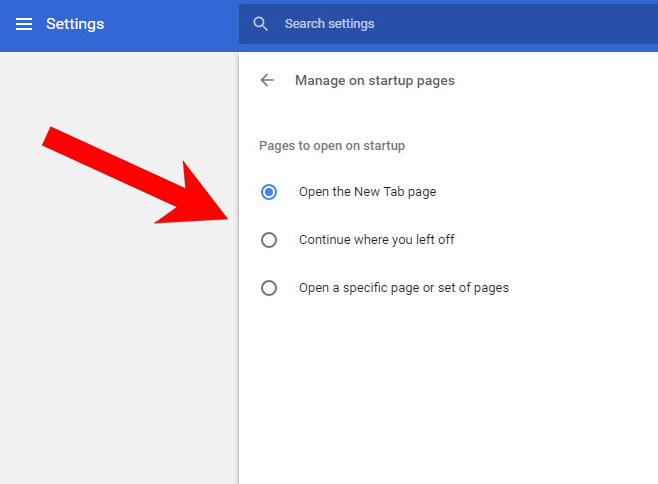
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

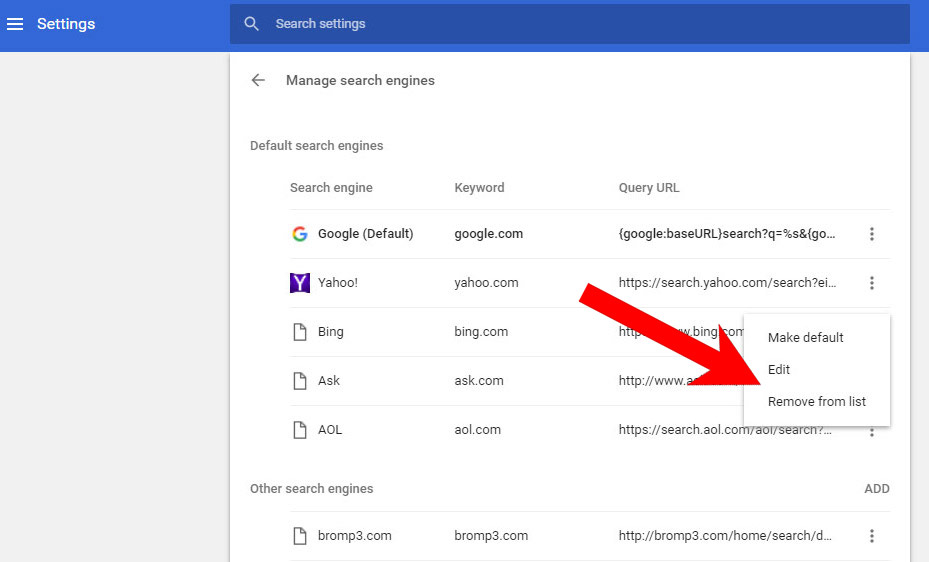
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
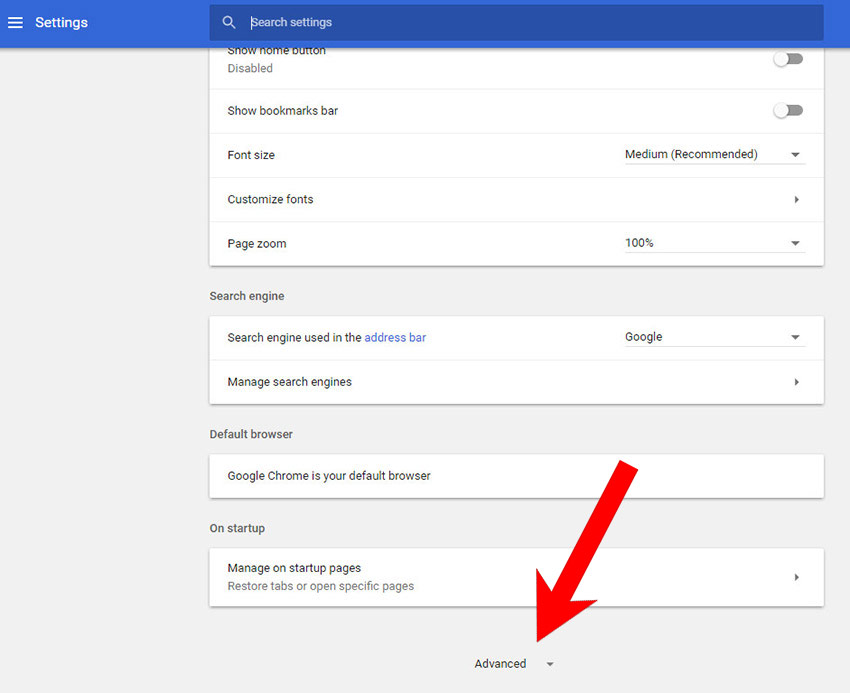
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

- Scroll down and press on Show advanced settings.

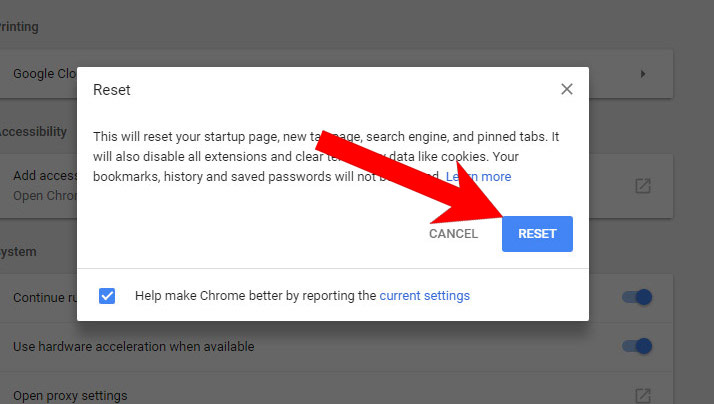
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
h) Remove from your from Mozilla Firefox
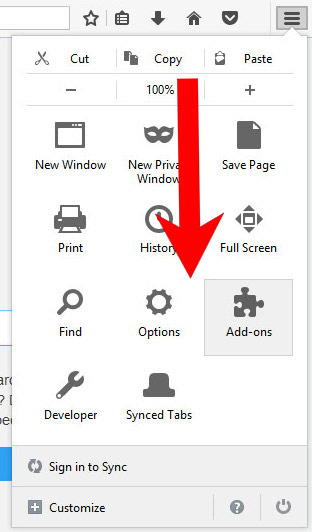
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Select Add-ons.

- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
i) Restore your homepage on Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
- Select Options.

- In General, click Restore to Default below the Home Page field.

j) Reset Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

- Select the Refresh Firefox option.

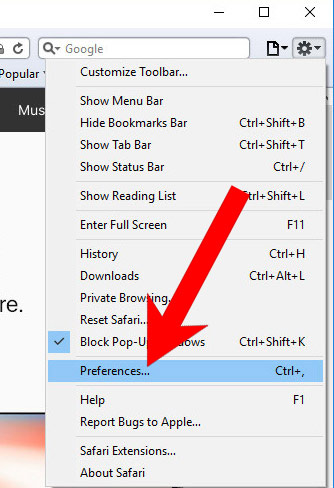
k) Remove from your from Safari (for Mac)
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

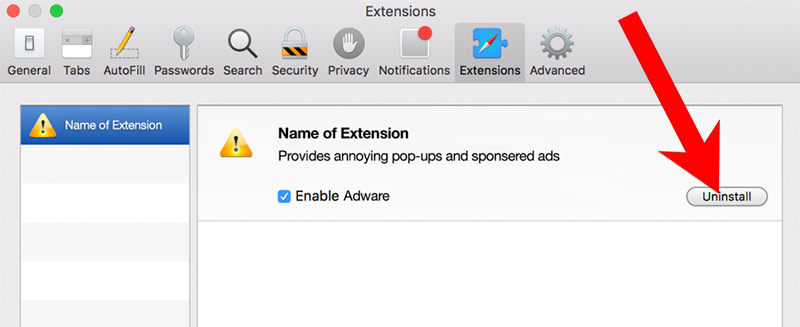
- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
l) Reset Safari
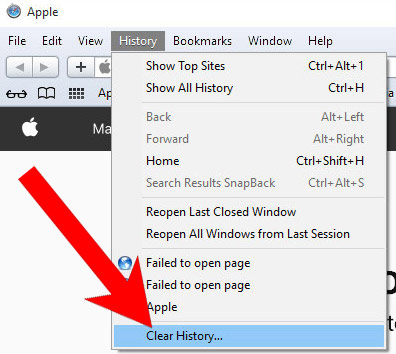
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
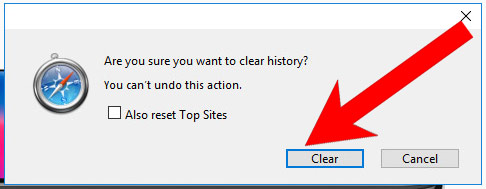
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

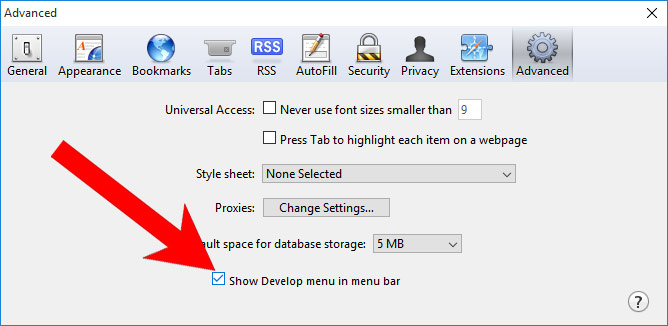
- Press on Safari at the top of the screen and select Preferences.

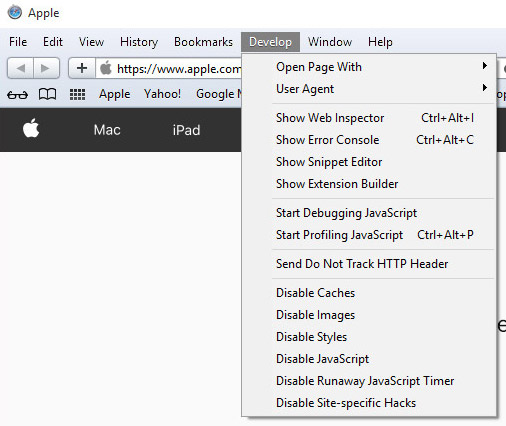
- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.