The Trojan horse malware are categorized as the most unfortunate of all infections shapes out there. They are highly stealthy and are able to start a full variety of contaminated processes earlier they land on a exhibited pc. Cve-2014-0543, particularly, can stay unidentified over drawn-out periods of time and control to wreck a device without the victim’s approval. Therefore, should you have this Trojan on your device, it has to be your first concern to appropriately detect and erase it former it might do more damage than it earlier has. But because getting rid of a Trojan is not a simple chore, we have created a exclusive removal guidelines that you can utilize for aid. You will discover it just below this report, accompanied by a trustworthy uninstallation utility for these kinds of of you who favor to not intervene in bundles with vital system files.
What complications can Cve-2014-0543 result in?
The Trojans are the the biggest number of adaptable elements of malicious program on the computer network. Representatives for example Cve-2014-0543 and Wup.exe, might be programmed to do varying corrupt movements and this is one of such primary reasons why these kinds of infections are so well-known and steady. That’s additionally why it’s generally very complex to locate what precisely a single Trojan could do by the time you identify it inside your computer.
Download Removal Toolto remove Cve-2014-0543For example, it is possible that such malicious software can be used to take some data from your device. In case the criminals who supervise it are curious about, say, some private details, sensitive correspondence, or some operate-akin data, alongside the Trojan’s assistance, they could access the stated numbers in addition toout your expertise. What is etc., an advanced Trojan for example Cve-2014-0543 can unidentified monitor your keystrokes and all you classification on the affected system. In that way, the criminals who steer behind it might acquire your passwords, login credentials, debit and credit card statistics , as well as other private data.
Another usual use of Trojan Horses is for tailing. Identical to the earlier-noted keystroke collecting procedure, such threat can share your screen with cyber crooks, generate screenshots, monitor your conversations, and even hack onto your webcam and mic to log videos and audios of your surroundings. In in this way, the culprits should be able to trail your whereabouts, shadow you, log your electronic communication, and employ the data accumulated for all sorts of criminal deeds that we don’t have to acquire onto. Another alarming of use of some Trojans is the one that authorizes criminals as to implant other viruses, e.g ransomware, worms, or other malware into oriented pcs together with a Trojan.
Therefore, if you don’t wish to end up with a pc packed with all kinds of viruses, it’s best to terminate Cve-2014-0543 promptly. We firmly recommend that you in addition carry out an entire pc investigate in addition to reputable security software or use the researcher deletion program on this page to fix the existing parasite.
Learn how to remove Cve-2014-0543 from your computer
Step 1. Cve-2014-0543 Removal from Windows
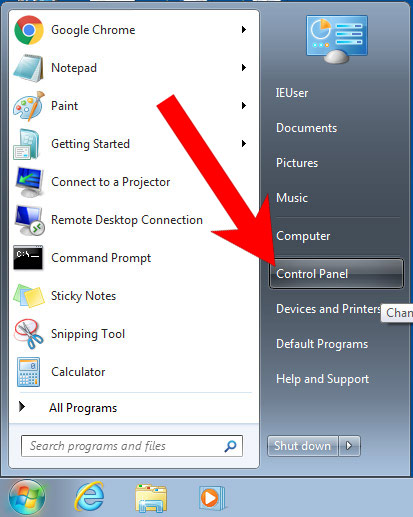
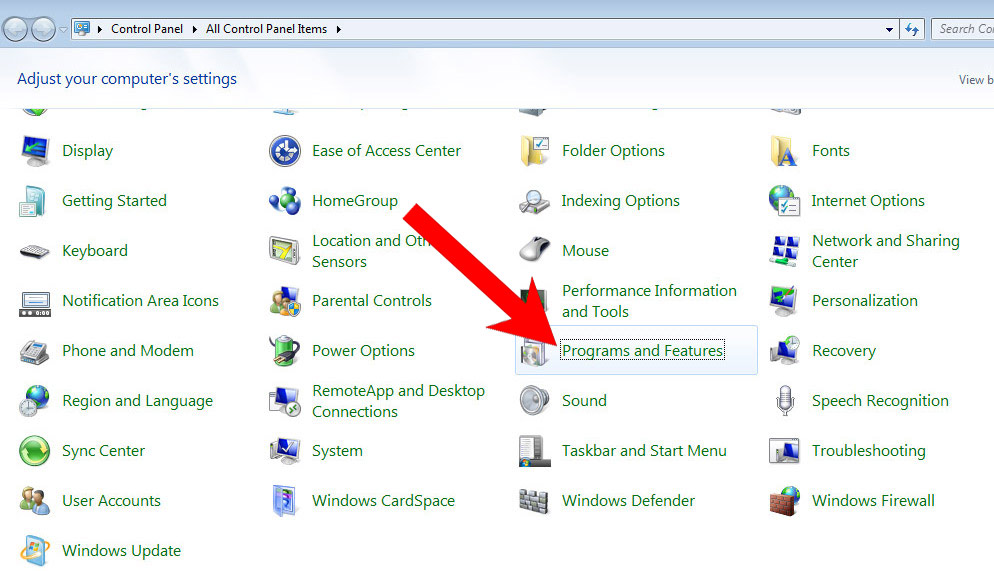
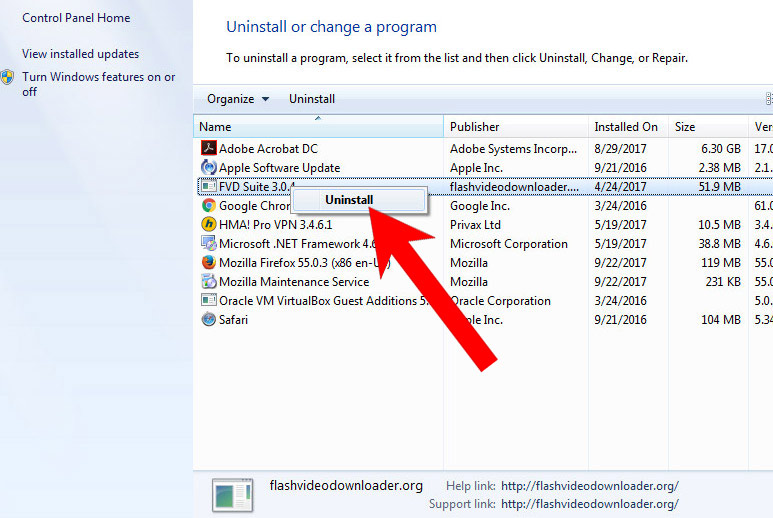
a) Windows 7/XP
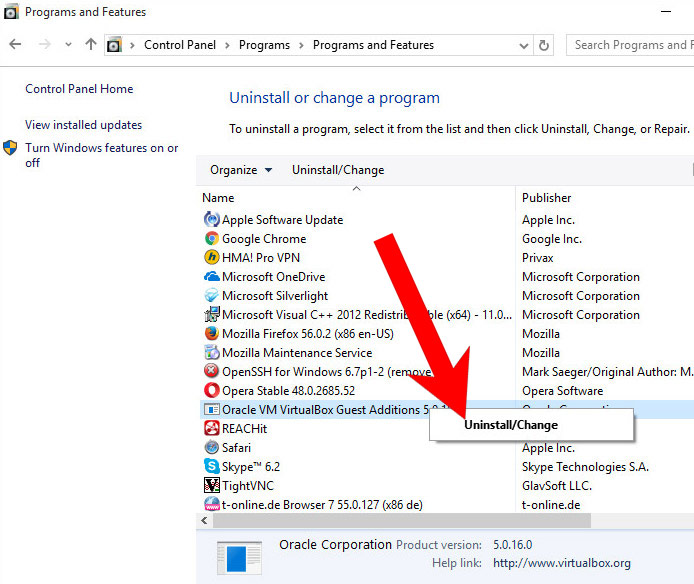
- Press on the Start icon.

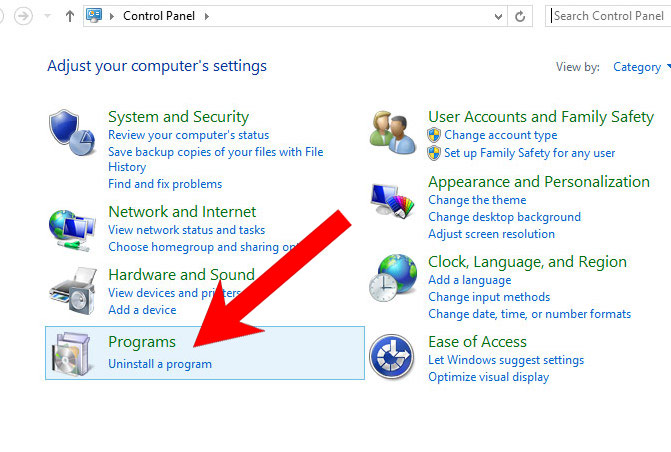
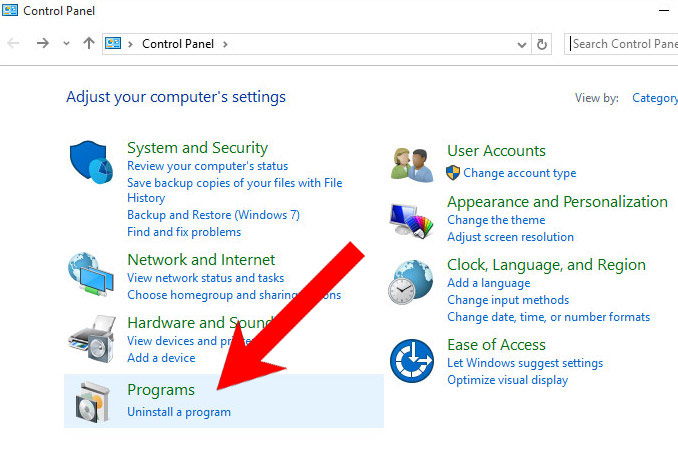
- Control Panel → Programs and Features.

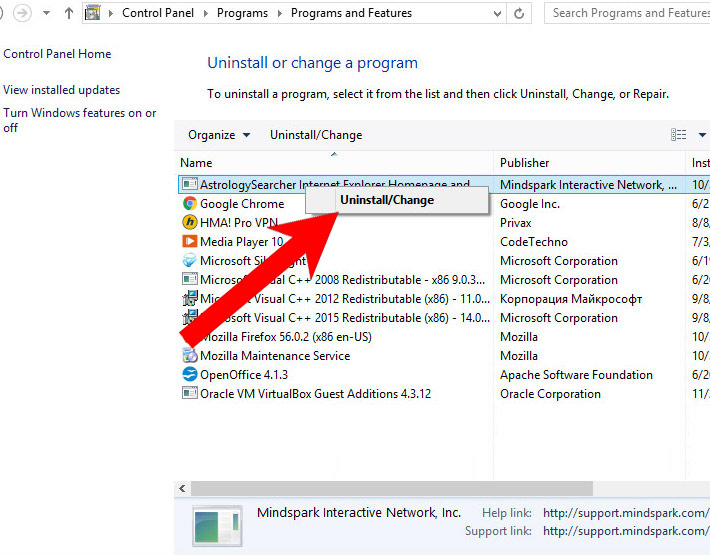
- Find the program you want to delete and press Uninstall.

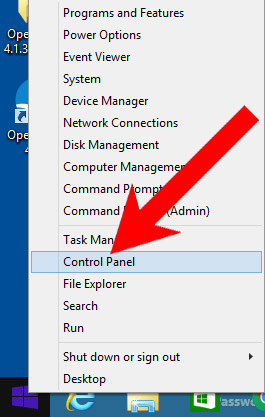
b) Windows 8
- Right-click on the start icon (lower left corner).

- Select Control Panel.

- Click Programs and Features.

- Find and remove all unwanted programs.

c) Windows 10
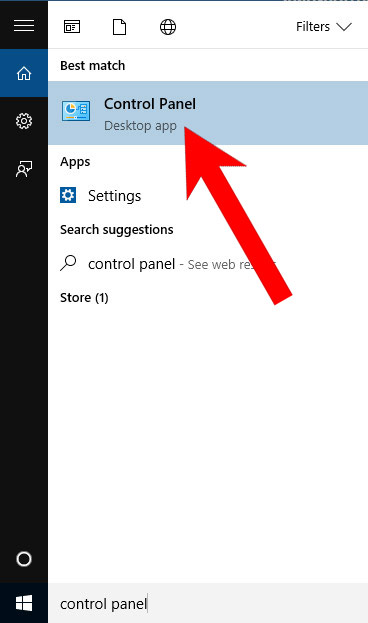
- Open Start menu and click on the magnifying glass (next to the shut down button).

- Type in Control Panel.

- Control Panel → Programs and Features.

- Find and remove all unwanted programs.

d) Mac OS X
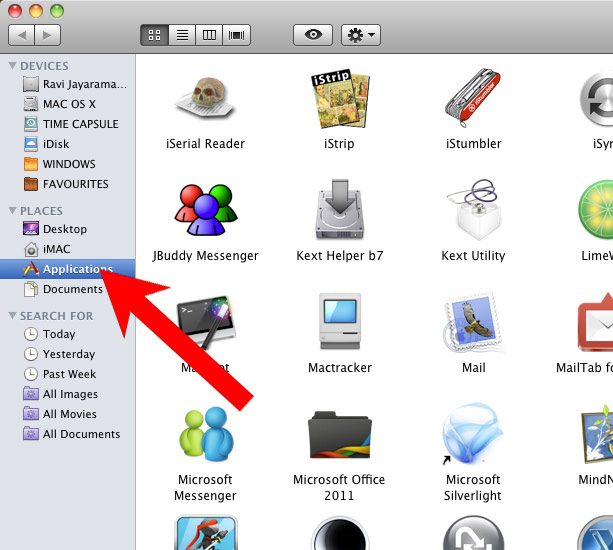
- Open Finder and press Applications.

- Check all suspicious programs you want to get rid of.
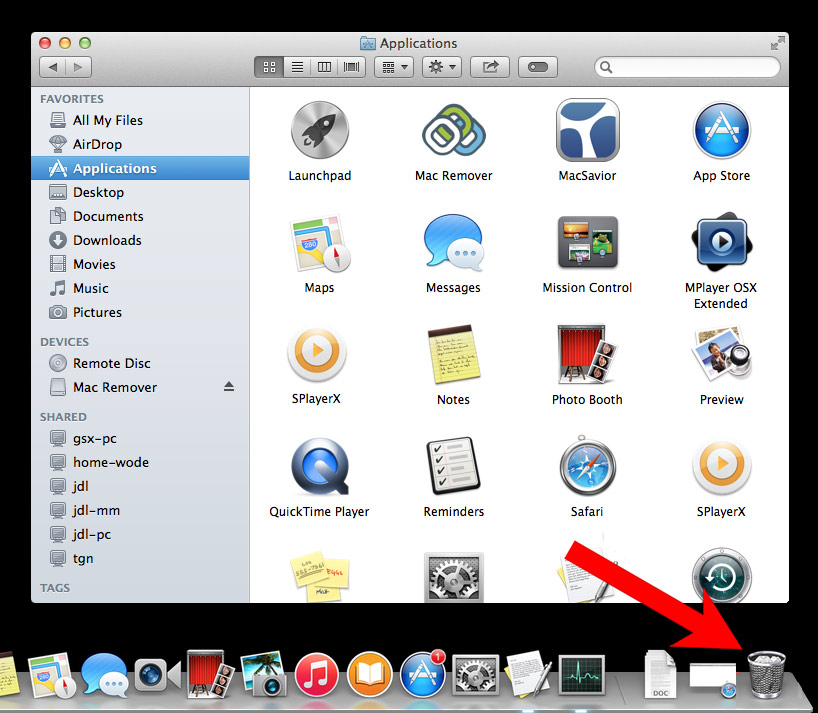
- Drag them to the trash icon in your dock (Alternatively, right-click on the program and press Move to Trash).

- After you move all the unwanted programs, right-click on the trash icon and select Empty Trash.
Step 2. Delete Cve-2014-0543 from browsers
a) Remove Cve-2014-0543 from Microsoft Edge
Reset Microsoft Edge (Method 1)
- Open Microsoft Edge.
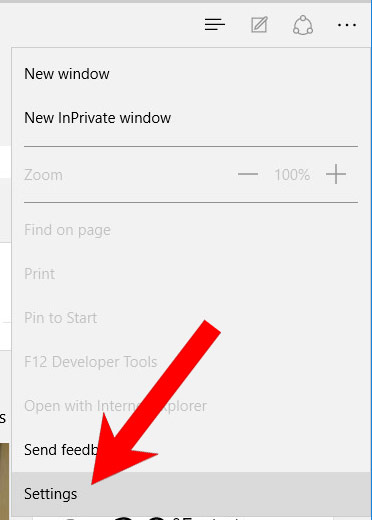
- Press More located at the top right corner of the screen (the three dots).

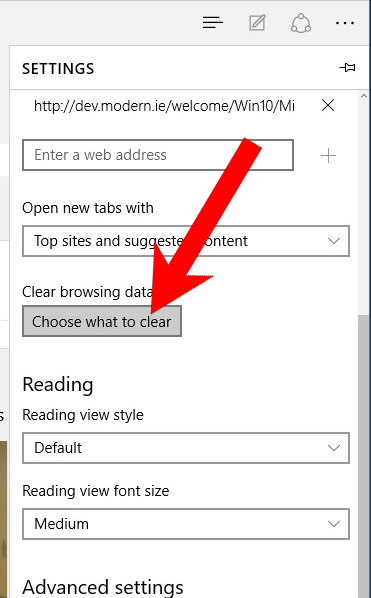
- Settings → Choose what to clear.

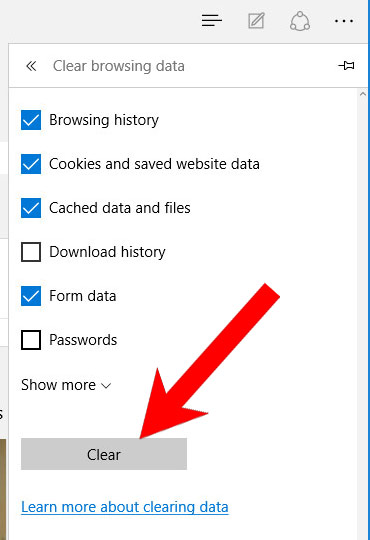
- Check the boxes of the items you want removed, and press Clear.

- Press Ctrl + Alt + Delete together.
- Choose Task Manager.
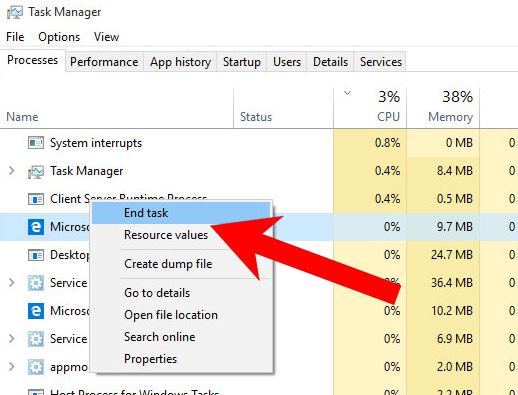
- In the Processes tab, find the Microsoft Edge process, right click on it, and press Go to details (or More details if Go to details is not available).

- Right-click on all Microsoft Edge processes, and choose End task.
(Method 2)
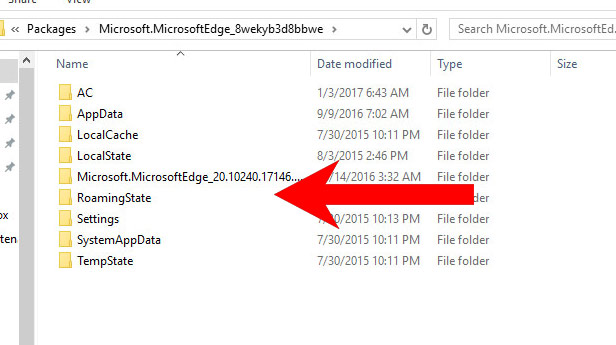
Before you proceed with this method, backup your data.- Go to C:\Users\%username%\AppData\Local\Packages\Microsoft.MicrosoftEdge_xxxxxxxxxx.
- Select all the folders, right-click on them and press Delete.

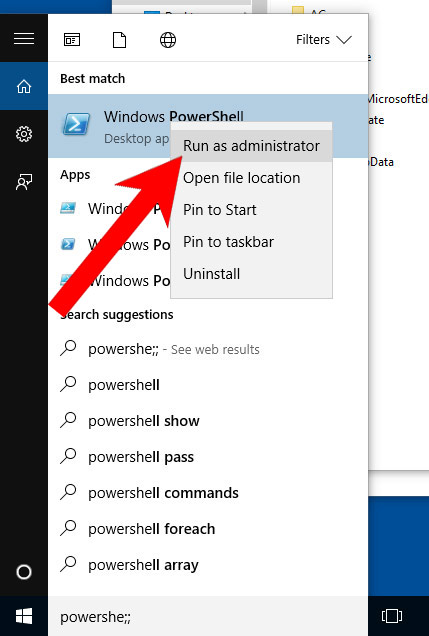
- Press the start button, and type in Windows PowerShell in the search box.
- Right-click on the result, and select Run as administrator.

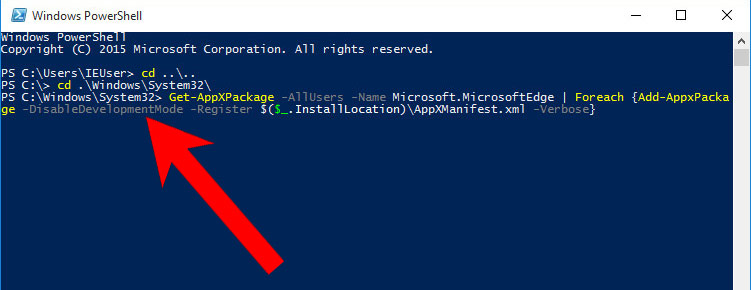
- In Administrator: Windows PowerShell, paste
Get-AppXPackage -AllUsers -Name Microsoft.MicrosoftEdge | Foreach {Add-AppxPackage -DisableDevelopmentMode -Register $($_.InstallLocation)\AppXManifest.xml -Verbose}
under PS C:\WINDOWS\system32> and tap Enter.

- The issue should be gone now.
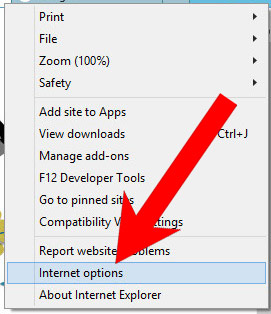
b) Remove Cve-2014-0543 from Internet Explorer
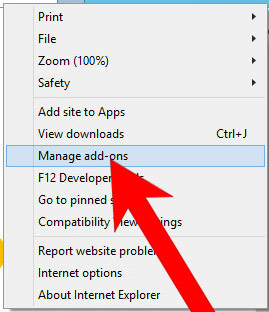
- Open Internet Explorer and press on the Gear icon.

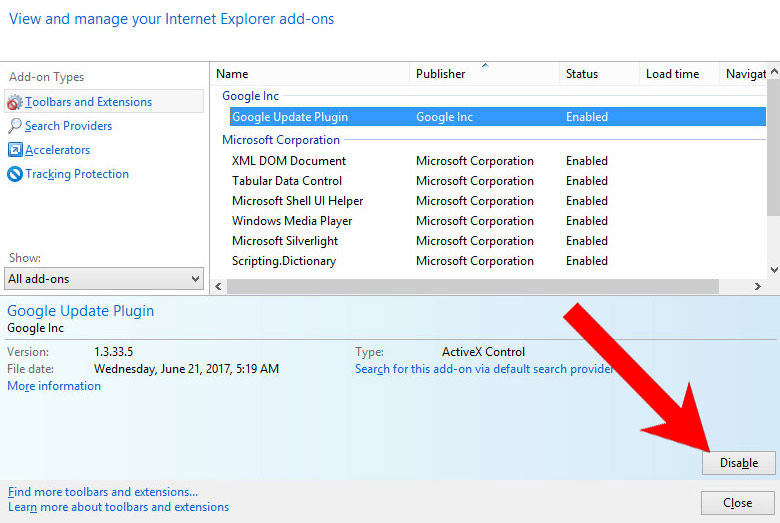
- Select Manage add-ons, and then Toolbars and Extensions.
- Find and disable all suspicious extensions.

- Close the window.
c) Restore your homepage on Internet Explorer
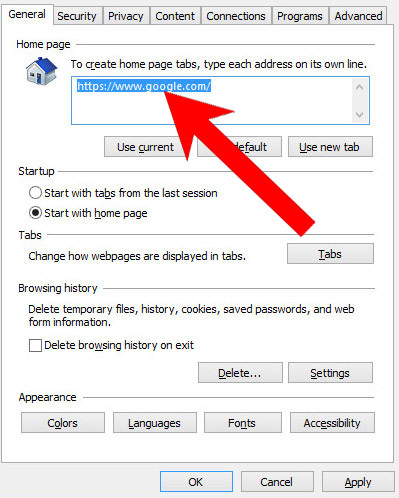
- Open Internet Explorer and press on the Gear icon.
- Internet Options → General tab. Delete the homepage URL and type in your preferred one.

- Press Apply.
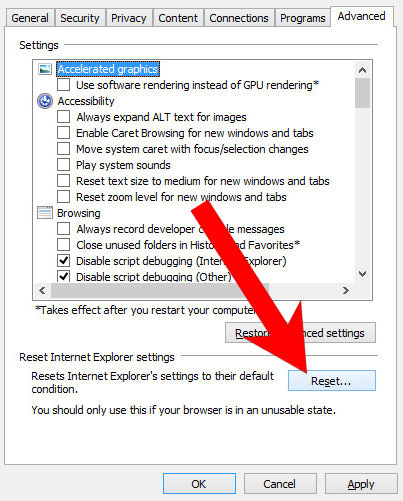
d) Reset Internet Explorer
- Open Internet Explorer and press on the Gear icon.

- Internet Options → Advanced tab.

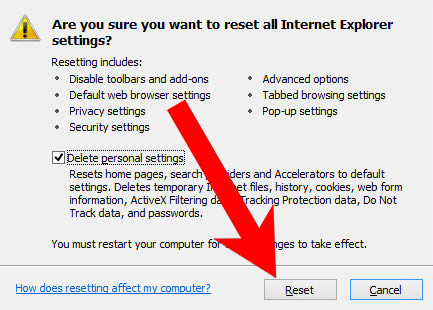
- At the bottom, you will see a Reset button. Press that.
- In the window that appears, check the box that says Delete personal settings.

- Press Reset.
- Click OK to exit the window.
- Restart your browser.
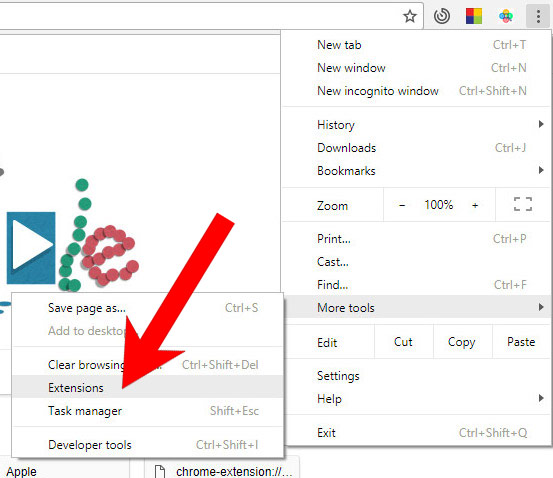
e) Remove Cve-2014-0543 from Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
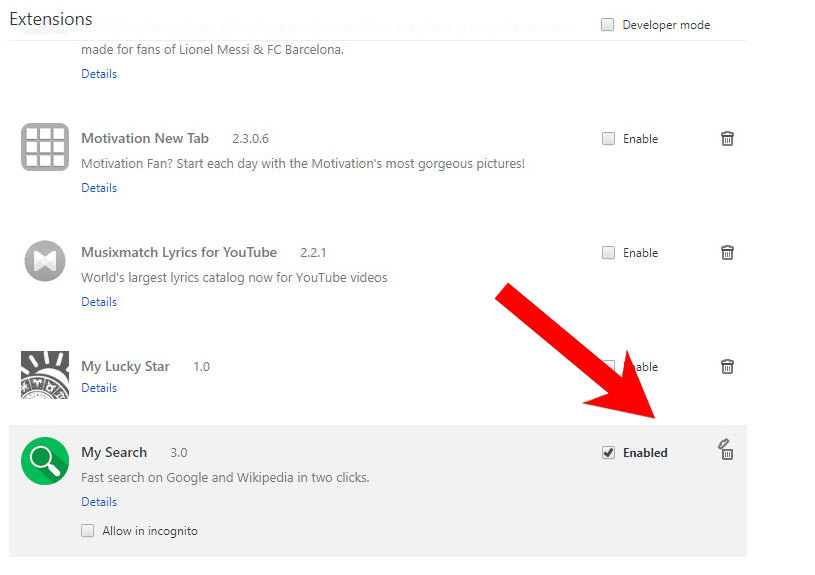
- Choose More tools and Extensions.

- Remove suspicious extensions by clicking the Trash icon next to them.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
f) Restore your homepage on Google Chrome
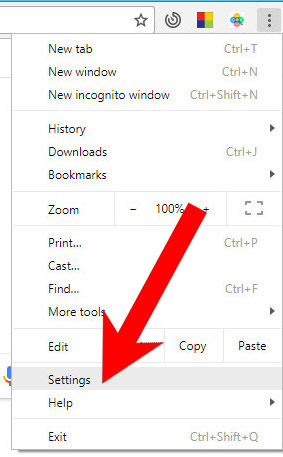
- Open Google Chrome and press the menu icon on the right, next to the URL field.
- Choose Settings.

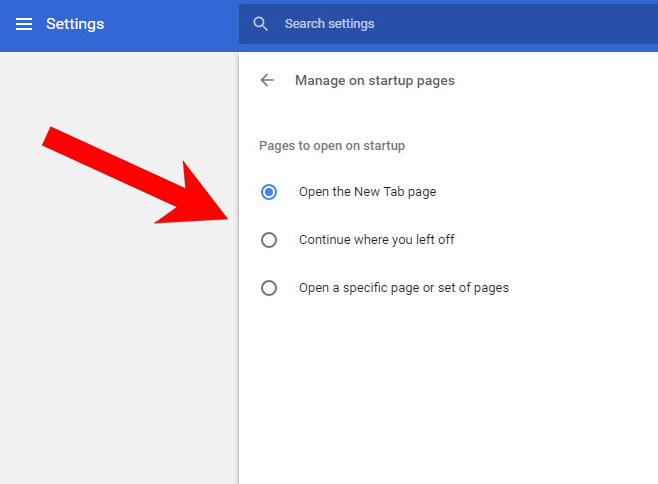
- In the window that appears, under On startup, there will be a Set pages option. Press on that.
- Remove the set website, and type in the one you prefer to be your homepage. Press OK.

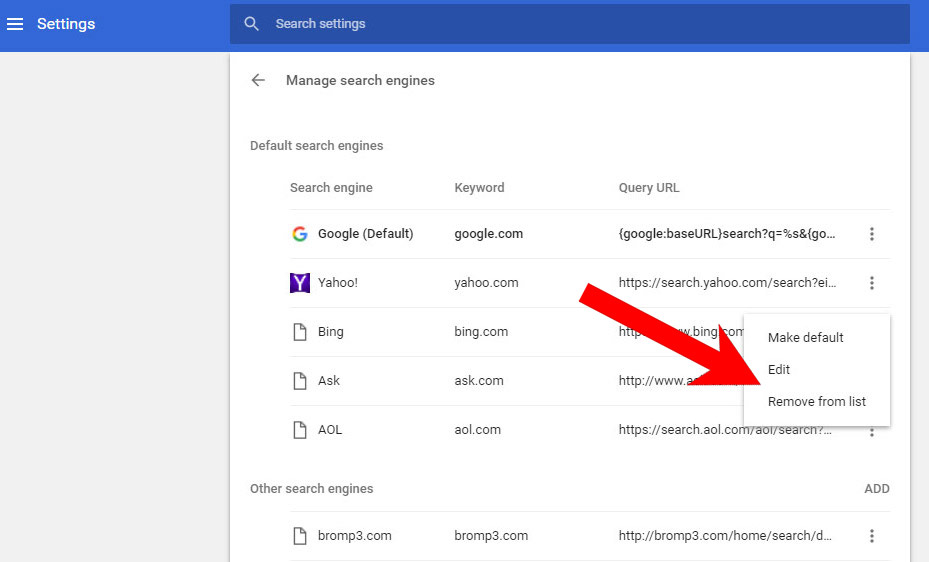
- In Settings, under Search, there is a Manage search engines option. Select that.

- Remove all search engines except the one you want to use. Click Done.
g) Reset Google Chrome
- Open Google Chrome and press the menu icon on the right, next to the URL field.
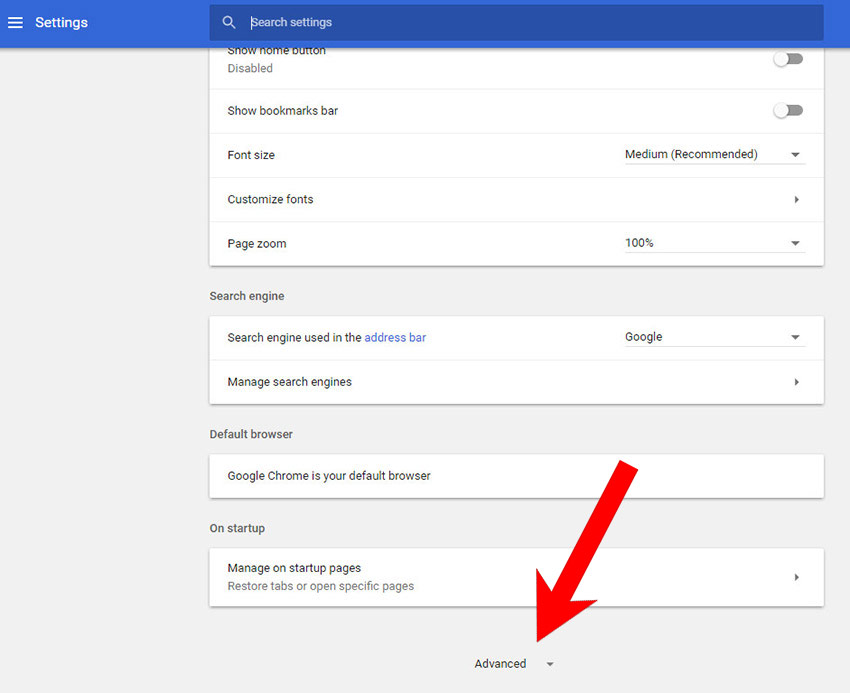
- Choose Settings.

- Scroll down and press on Show advanced settings.

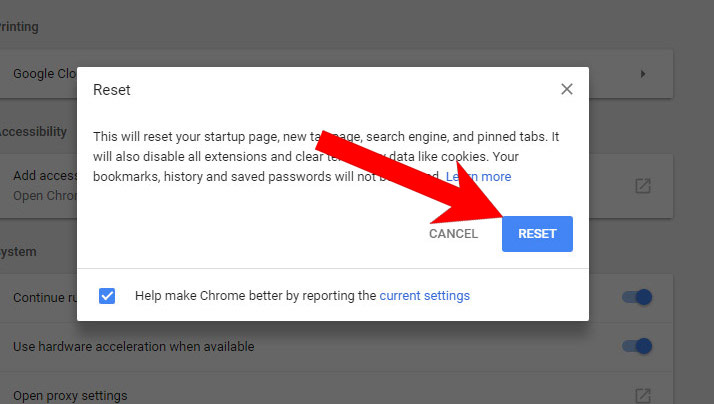
- Find and press the Reset button.

- In the confirmation window that appears, press Reset.
h) Remove Cve-2014-0543 from Mozilla Firefox
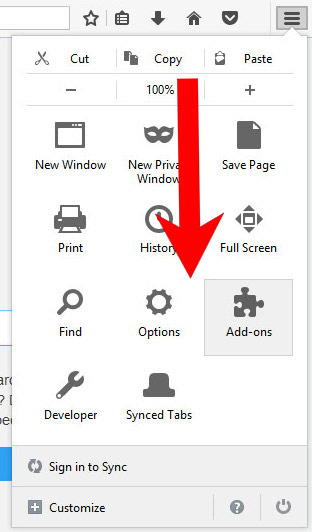
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
- Select Add-ons.

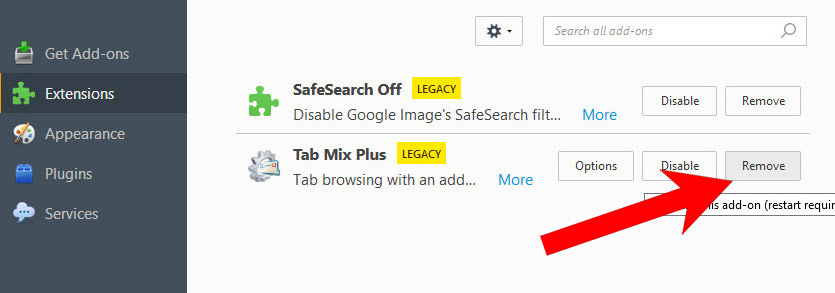
- Select the Extensions tab, and remove all questionable extensions.

- If you are not certain about an extension, you can disable it by clicking Disable. If you later decide to keep it, simply press Enable.
i) Restore your homepage on Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right side of the screen.
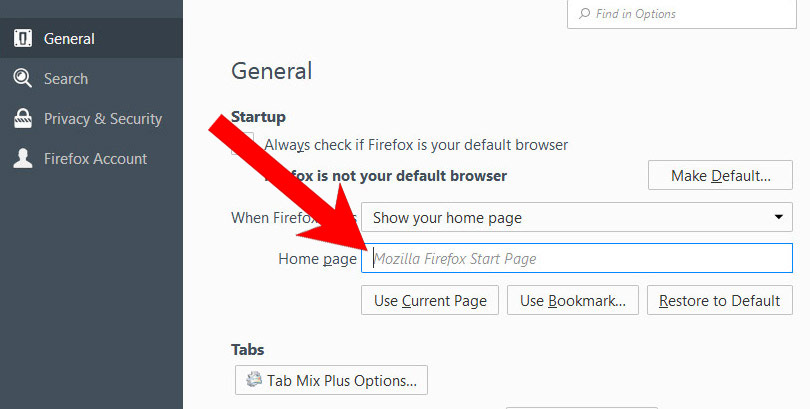
- Select Options.

- In General, click Restore to Default below the Home Page field.

j) Reset Mozilla Firefox
- Open Mozilla Firefox and access the menu by clicking on the three bars on the right of the screen.
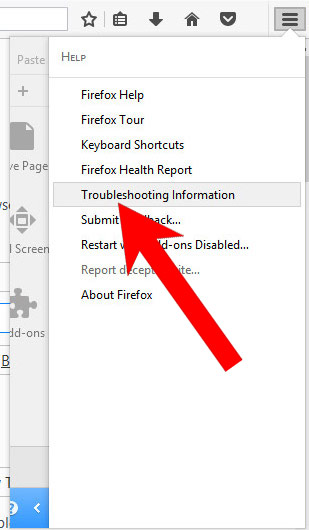
- Press the question mark at the bottom of the menu.
- Select Troubleshooting Information.

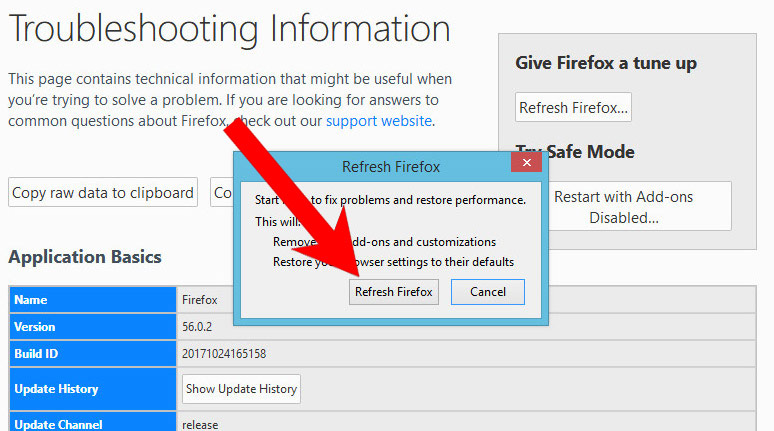
- Select the Refresh Firefox option.

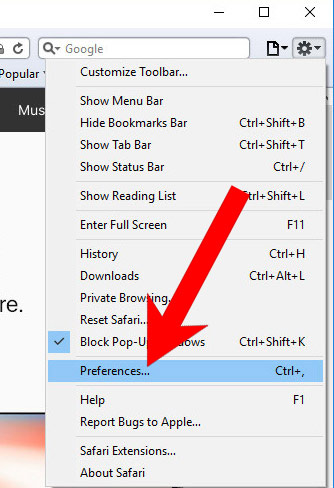
k) Remove Cve-2014-0543 from Safari (for Mac)
- Open Safari.
- Select Preferences (can be accesses by pressing on Safari at the top of your screen).

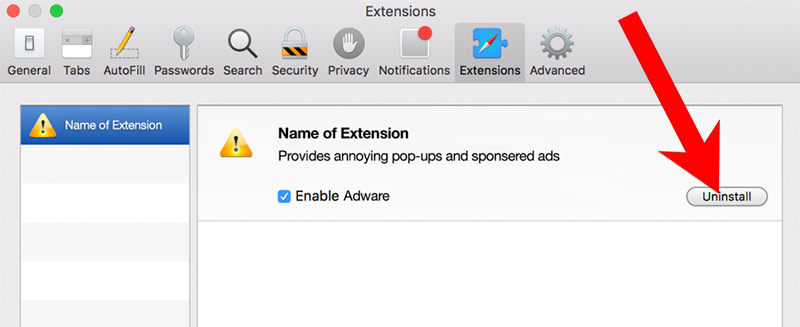
- Choose the Extensions tab.
- Uninstall all questionable extensions.

- If you are not certain about an extension, you can disable it by unchecking the box that says Enabled. If you later decide to keep it, simply check the box again.
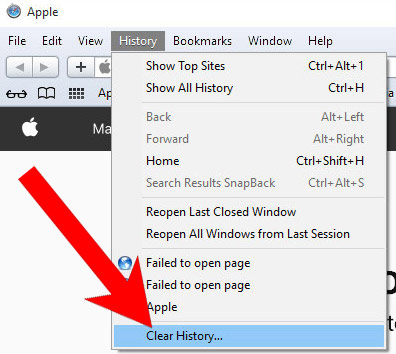
l) Reset Safari
If you are using the Yosemite, El Capitan or the Sierra versions, the option to reset Safari with one click is not available. Thus you will have to clear the history and empty the caches in separate steps.- Open Safari.
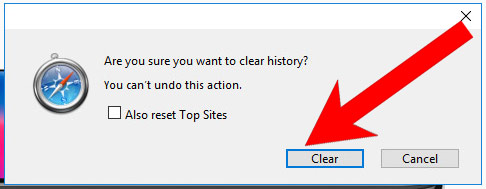
- Select Clear History (can be accesses by pressing on Safari at the top of your screen).

- Choose from what time you want the history deleted, and press Clear History.

- Press on Safari at the top of the screen and select Preferences.

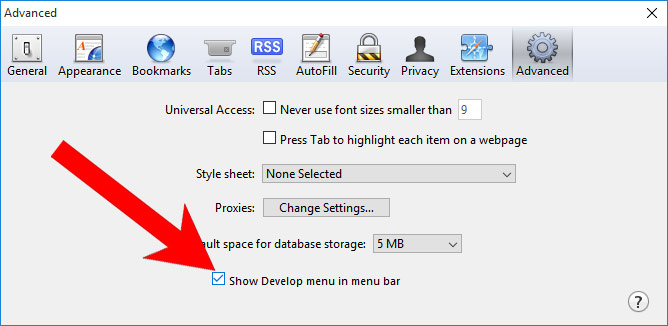
- Select the Advanced tab and check the box next to Show Develop menu in menu bar.
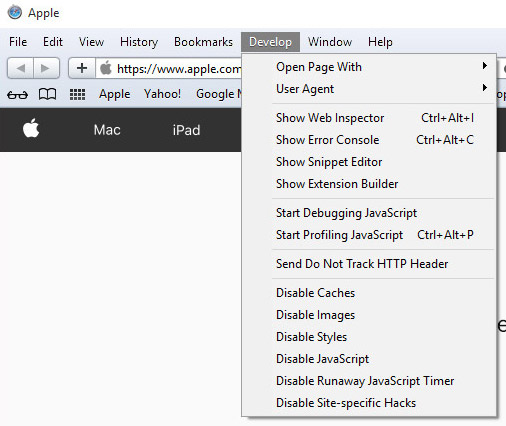
- Select Develop (from the menu bar at the top of the screen).

- Press Empty Caches.